TikTok, the popular social media video sharing application, continues to make headlines due to cybersecurity concerns and the trend doesn’t appear to be slowing down. Just recently the U.S. Army and Navy banned its use on government phones following a Defense Department warning regarding potential risks due to its information gathering policies. And this week TikTok confirmed it patched multiple vulnerabilities that potentially exposed accounts, user information, and videos.
To help users understand TikTok’s real privacy impact, the Proofpoint research team has examined TikTok’s app permissions and its behaviour. Below are details on the information TikTok gathers, sends, and stores.
What is TikTok?
TikTok enables users to create short, fifteen-second videos on their phones and post the content to a public platform. Videos are enhanced with music and visual elements, such as filters and stickers, and can also be co-created with other users through a split screen “duet” feature.
TikTok’s youthful target demographic and the nature of the content people create and share on the platform have put the app’s permissions and privacy aspects in the spotlight in recent months. Also, questions about where TikTok data is stored has led people to raise questions about who might have access to that data.
Our researchers looked at TikTok’s privacy statement, the permissions the app required on Android and iOS, the information the Android app sends to servers, as well as the app’s privacy controls for uploaded content. This analysis is meant to help you better evaluate what TikTok has access to and how it handles privacy. In turn, you can decide whether you, your organisation, or others you are responsible for should use it.
What you need to know about TikTok security
The most important thing to understand is that while TikTok shares audio and video you post and allows you to restrict who can see that content, it does request a number of permissions on your device. Most notably, it accesses your location and device information. While our researchers found nothing to indicate malicious activity or that TikTok is violating their privacy policy, people should exercise caution, especially in terms of the content they record and post.
TikTok app permissions include personal information and device control
First, our researchers examined TikTok’s permissions and requirements on Android and iOS devices following installation. While some of the app’s permissions detailed below are to be expected, all of this is consistent with TikTok’s written privacy policy. However, when you see all that TikTok gathers it can still be of concern. In summary, these permissions allow TikTok to:
- Access the camera (and take pictures/video), the microphone (and record sound), the device’s WIFI connection, and the full contact list on the device
- Determine if the internet is available and access it
- Keep the device turned on and automatically start itself when the device restarts
- Secure detailed information on the user’s location using GPS and other apps that are running
- Read and write to the device’s storage, install/remove shortcuts, access the flashlight (turn it off and on), request additional installation packages
Our researchers found that TikTok permissions give them full access to the audio, video, and address book on the device, which isn’t surprising given that TikTok is an audio-visual app by design.
However, the GPS tracking is surprising, especially as TikTok videos don’t obviously display location information. TikTok’s collection of location information gathering is called out in their privacy policy. In it, they state that you have control over this: “You can switch off GPS location information functionality on your mobile device if you do not wish to share GPS information.”
On Android, the app has the ability to access other apps running at the same time, which can give the app with that permission the ability to access data in another app like a banking app. However, our researchers see no evidence that TikTok abuses this ability.
In Figure 1 you can see the TikTok permissions require as shown in the Android interface.
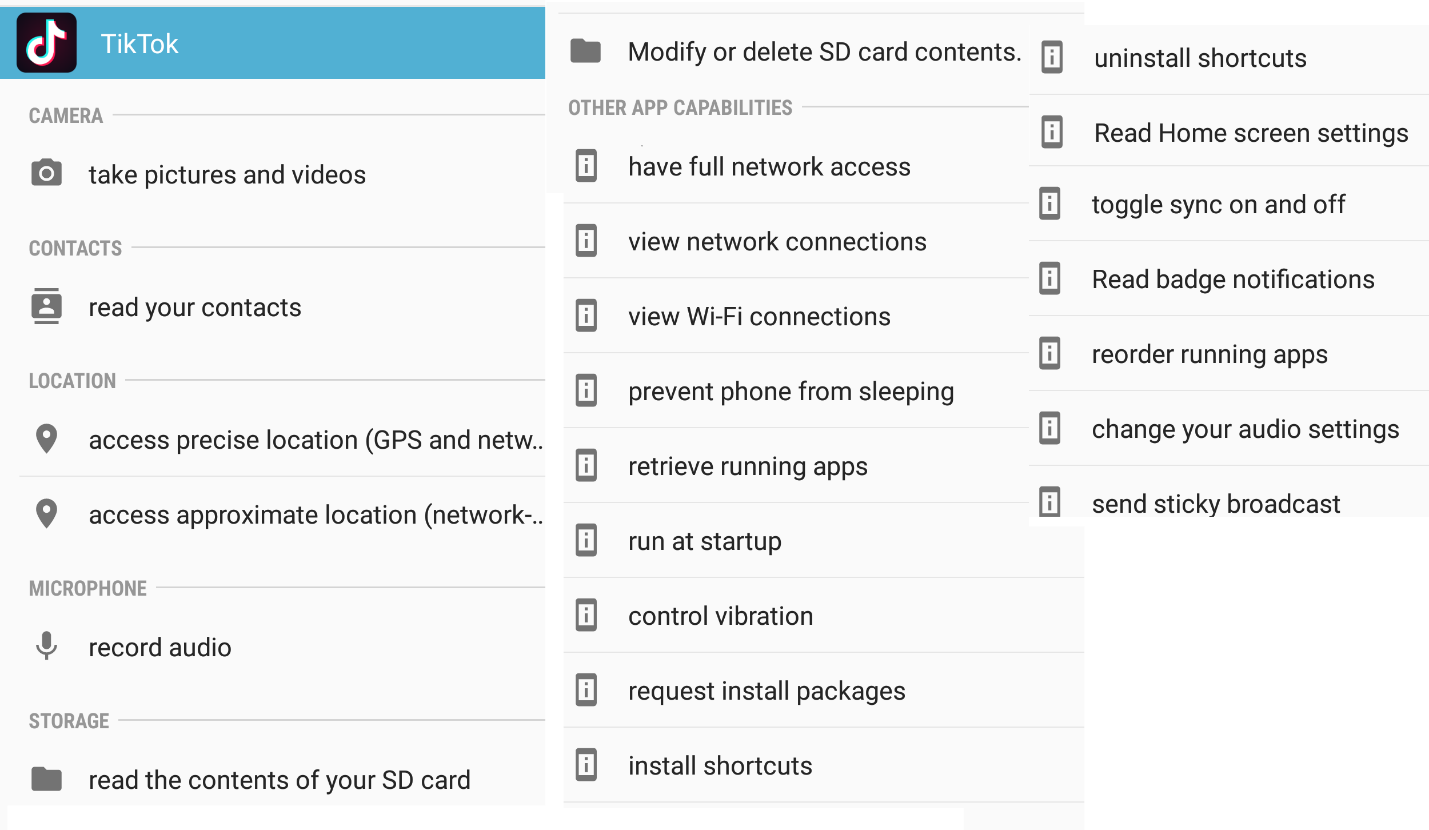
Figure 1 TikTok Permissions as shown in Android
In Figure 2 you can see the permissions it requires on iOS.
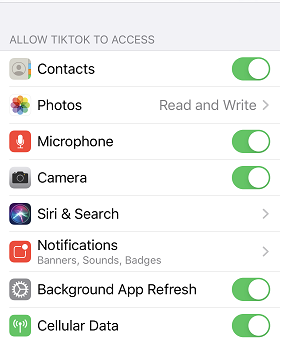
Figure 2 Figure 1 TikTok Permissions as shown in iOS
Our researchers also examined the information that is actually sent across the network from the Android TikTok app. We found it is consistent with their privacy policy and the permissions requested. Our researchers found the following information was being sent:
- Geolocation data, including: longitude, latitude, and time zone
- Device information, including: Android ID, International Mobile Equipment Identity (IMEI), Address Book Access, Device carrier region, Device region, Device type, Device OS version, Device language, Device connection type, and Mobile network code
- App information, including: App name
This information is sent to TikTok’s servers and based on their privacy policy, should be presumed to be stored there.
Content Privacy Controls
TikTok’s privacy model and controls are similar to and consistent with other social media platforms like Facebook. Users have the ability to restrict their content visibility. The controls are simple: users can choose between “Everyone”, “Friends”, and “Only me”. It’s important to note that these are social media visibility controls and they only control what other users can see regarding content posted. These do not have a bearing on the information that’s actually stored on TikTok’s server infrastructure. TikTok is like many mobile device-cloud paired services: the total privacy picture includes the privacy controls for content you store in the cloud.
In Figure 3, you can see the app permissions that control content privacy (once it’s uploaded).
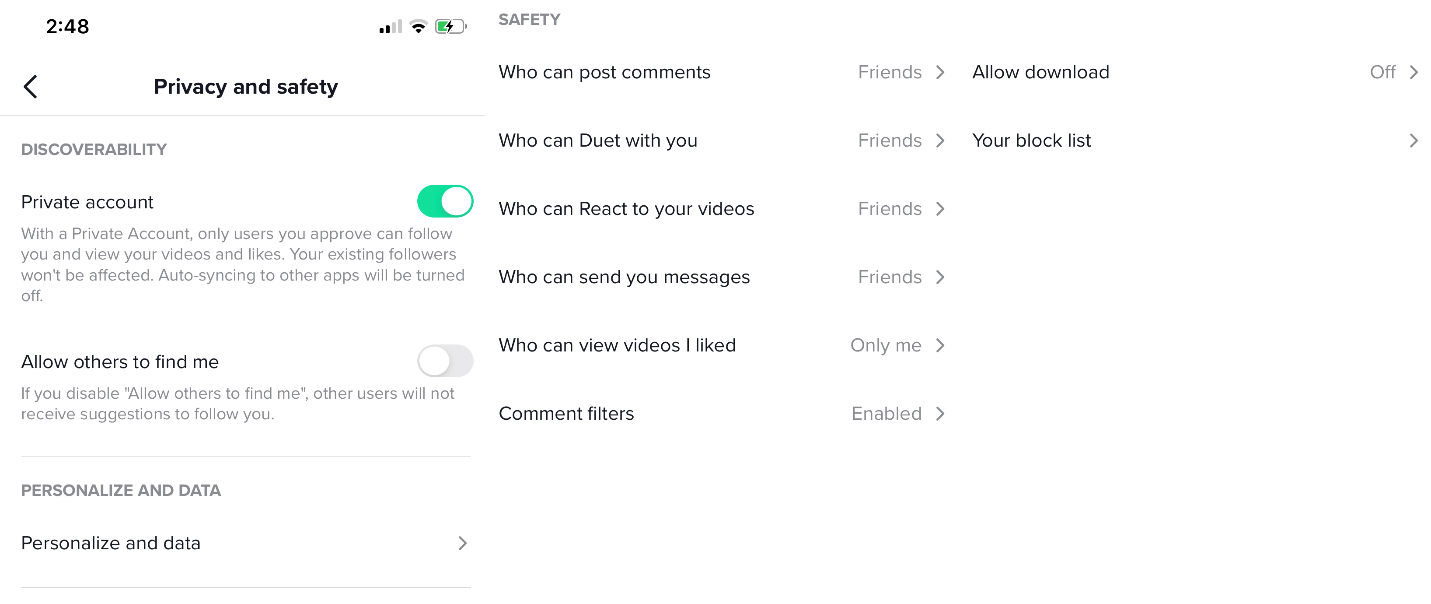
Figure 3 TikTok Permissions as shown within the app
Data Storage Location and Security Concerns
One of the biggest concerns surrounding TikTok’s information gathering is where user information is stored. The TikTok website states: “We store all TikTok US user data in the United States, with backup redundancy in Singapore. Our data centers are located entirely outside of China, and none of our data is subject to Chinese law.”
Their EU privacy policy includes as a question “Where we store your personal data” which says “The personal data that we collect from you will be transferred to, and stored at, a destination outside of the European Economic Area (“EEA”).” There is no other specific information on the TikTok website regarding where user data is stored.
Related to this, TikTok has just published their first ever “Transparency Report” which details “legal requests for user information”, “government requests for content removal”, “copyrighted content take-down notices”. It’s notable that India, the United States and Japan were the top three countries respectively where user information was requested. The United States was the number one country with fulfilled request with 86% and the number one country in terms of number of accounts specified in the requests, 255. China is not listed which means TikTok did not receive any requests for user information in China.
Conclusion
The TikTok app requests several permissions that are obvious for a social media app focused on audio and video; however, outside of U.S. users, it does not provide specific information on where the data is stored. It provides standard social media privacy controls which can be used to restrict access to content but does require user interaction to lock it down tightly.
All in all, TikTok should be treated like any social media app: one that can be used with relative safety if you’re aware of the information it gathers and what it does with the data. This is where review of their privacy policy is useful, as well as taking time to review all the information available around the app, the service, and data storage. And finally remember that what you record, others will see.
Is your organisation protected from potential personal information risk? Learn about Information Protection.











