Pop quiz: What do the following have in common?
- A tiny Florida city
- Japan's largest media conglomerate
- A national museum in the Netherlands
- A host of cable TV's "Shark Tank"
Answer: They've all recently fallen victim to business email compromise (BEC) or email account compromise (EAC).
BEC and EAC attacks come in many forms. But they all follow a similar playbook: the attacker, posing as someone the victim trusts, tricks the victim over email into wiring money or sending sensitive data.
And no one is immune to them. Victims can be as small as the 60,000-population city of Ocala, Fla. (which lost $740,000) or as big as Japanese publishing giant Nikkei (which lost $29 million). They can be as obscure as the Dutch museum Rijksmuseum Twenthe (which lost $3.1 million) or as famous as "Shark Tank" TV host Barbara Corcoran (who lost $400,000).
And those are just a handful of cases. BEC and EAC attacks have caused more than $26 billion in losses since 2016—and nearly $1.7 billion last year alone. And each one is unique, deploying countless ploys and phycological tricks limited only by attackers' guile.
Unfortunately, that means there's no one technological silver bullet for stopping all of them.
How they're similar
While BEC and EAC attacks have generated a lot of press coverage in recent months, that attention has also generated a lot of confusion.
On one hand, the two are similar enough that the FBI tracks them together. Both target people, usually someone chosen because of their job function or access. Both rely on social engineering, not technical vulnerabilities. And in both types of attacks, the attacker is after money. That's either directly through a fraudulent wire transfer or as sensitive information or data that can be sold on the black market.
Because they are so narrowly targeted, BEC and EAC attacks don't set off the usual cybersecurity triggers. And because they don't involve a malware payload or an unsafe URL, they're invisible to many security tools.
How they're different
Still, BEC and EAC have some key differences.
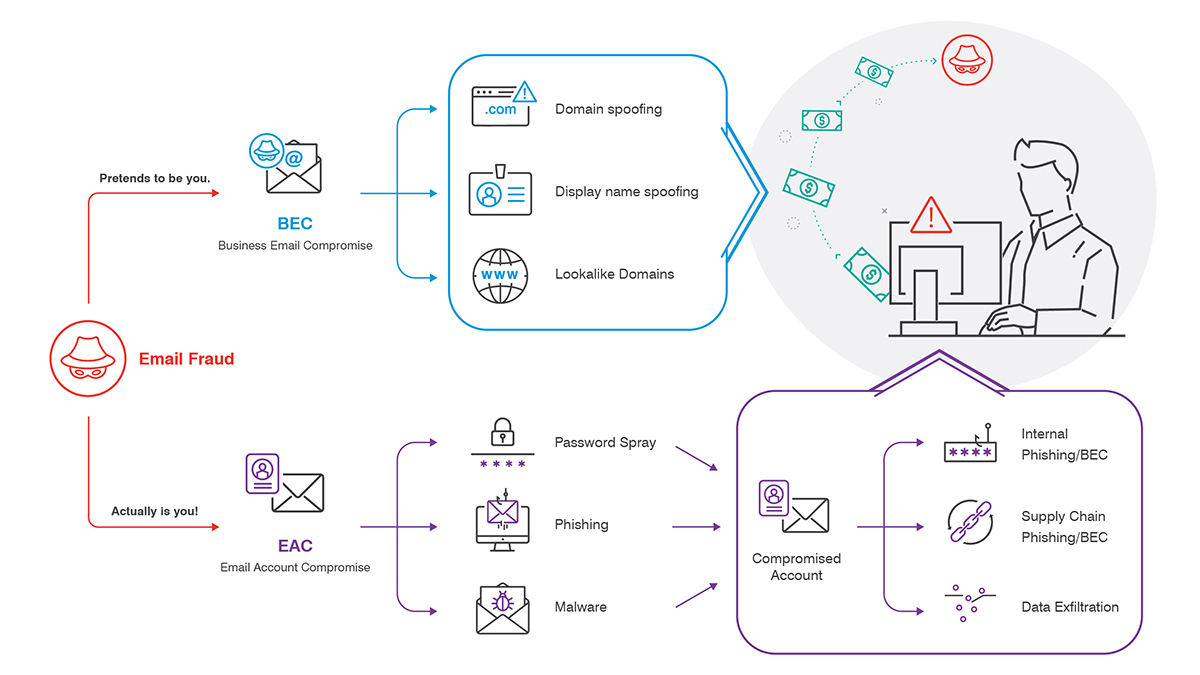
In BEC attacks, the attacker disguises their email address to look like someone the victim trusts. Common tactics include:
- Domain spoofing
- Display-name spoofing
- Lookalike domains
In EAC attacks, the attacker takes over the actual email account of someone the victim trusts—in essence, becoming that trusted person. Common account-takeover techniques include password spraying and getting account credentials through phishing, malware or earlier data breaches.
By taking over a legitimate email account—especially one within the same internet domain as the victim' s—the attacker can launch a number of attacks, including:
- BEC-style attacks against other people in the same organization
- Phishing emails to colleagues
- Supply-chain attacks that trick business partners into rerouting payments
Most email security tools just aren't designed to detect threats from within the organization.
Whack-a-mole—on steroids
BEC and EAC tactics are complex, multifaceted and ever-changing. An email defense built to stop one kind of attack—or even a handful—may leave you exposed to other BEC/EAC threats.
Consider the following scenarios:
|
You do this |
Attackers do that |
|
You protect corporate email. |
Attackers target users’ personal email (which people often access within the corporate environment on company-owned systems). |
|
You detect and block impostor email at the gateway. |
Cyber criminals take over users’ email accounts and attack from the inside. |
|
You protect your users from account compromise and takeovers. |
Attackers compromise the accounts of your supply-chain partners or impersonate someone from your organization in attacks against them. |
Next steps
In our research, nearly 90% of organizations faced business email compromise and spear phishing attacks in 2019.
To keep your people and data secure, you need to secure every avenue that BEC and EAC attacks might take. That effort requires a comprehensive, end-to-end solution. It should include all of these features working together:
- Security awareness education.
- Email authentication to stop domain abuse.
- Visibility and control over cloud apps and what they access.
- Web access and isolation controls.
- Detection of unsafe attachments and URLs at the gateway.
- Content classification to identify BEC.
- Internal email defenses to stop EAC.
- Visibility into and adaptive controls for your most attacked people. We call these Very Attacked People™ or VAPs.
- Automated remediation when something gets through
No single technology, working alone, can stop all BEC and EAC threats. But people-centric approach that uses multiple lines of defense holistically can help you anticipate—and block—all the ways an attacker might target your users. To learn more about how Proofpoint can help you manage BEC and EAC threats, take a quick BEC/EAC readiness assessment on the BEC/EAC solution page.











