The Cybersecurity Stop of the Month blog series explores the ever-evolving tactics of today’s cybercriminals and how Proofpoint helps organizations better fortify their defenses to protect people against today’s emerging threats.
The scenario: a safe door to a dangerous room
It starts with an email that looks entirely routine. You receive a notification that appears to come from a trusted service—in this example, let’s say Dropbox. The email informs you that a colleague has shared a secure file, perhaps an invoice or a spreadsheet titled “Q3 financials,” and provides a link to view it. The link itself points to a legitimate Dropbox URL. There is no malware attached to the email. To any standard email security filter, this message looks clean.
When you click the link, you are directed to a Dropbox login page. You may have to first interact with a CAPTCHA form to prove you are human. Once logged into the application, you click on a pdf attachment that contains a malicious link within it.
This multilayered set of URLs is a tactic known as a URL-to-URL (U2U) authentication threat. It’s growing in popularity as it’s very hard for most security solutions to condemn. Let’s take a closer look at how this threat works and why it’s so difficult to block.
The end game: evasion and infection
Threat actors who use these multilayered attack techniques to hide a malicious payload deep within a well of URL clicks have two goals:
- Navigation difficulty. The several layers of gateways—including CAPTCHA and login screens—make it extremely challenging for security solutions get to the final payload.
- Malware delivery. Once the user authenticates, they are redirected to a second URL that delivers the malicious payload—often a weaponized document.
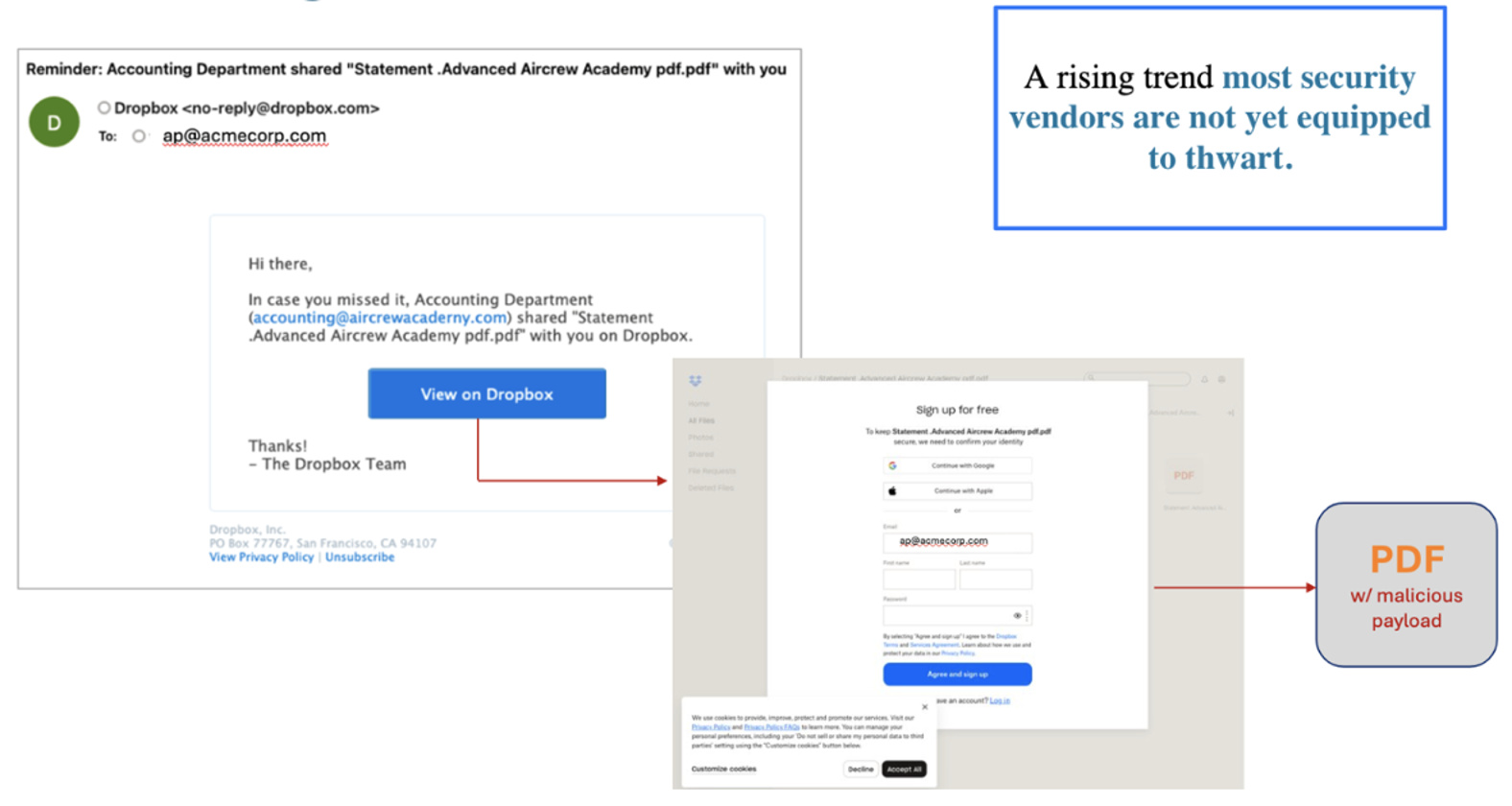
Figure 1. Example of a URL-to-URL threat.
The challenge: why security vendors miss it
Identifying these threats is notoriously difficult because they are engineered to exploit the architecture of traditional secure email gateways (SEGs).
- Clean entry. Scanners typically inspect the first URL in an email. Since the attack starts with a legitimate file share link, such as Dropbox or SharePoint, it passes reputation checks with flying colors.
- Proof of human. There is often a CAPTCHA layer inserted before reaching the login page to prove the user is a human. These techniques are easy for a person to solve but difficult for automated systems to pass.
- The “scanner trap.” Automated sandboxes are designed to follow links, but they often cannot log in. When the scanner hits the authentication page, it stops because it lacks credentials to proceed. It assumes the page is a secure portal and clears the email, leaving the malicious payload hidden behind the gate.
- Malicious payload. The final payload is sitting on the vendor’s server and did not come through via email. Traditional security filters struggle to analyze and identify malicious links or attachments that have not passed directly through their own gateway or API.
How Proofpoint Nexus blocks URL-to-URL threats
While traditional gateways are fooled by the legitimate entry point, Proofpoint excels at identifying and blocking multilayered attacks like these. Our detection stack, Proofpoint Nexus®, uses an ensemble of AI-powered engines to analyze the context, behavior, and intent of the attack, identifying the threat even when the initial URL looks safe.
Here is how Nexus dissects and blocks URL-to-URL authentication attacks:
1: Detecting intent with the Nexus LM™ (Language Model)
The attack relies on social engineering to lure the victim into taking some action, such as clicking a link. Our Language Model analyzes the psychology of the message to identify:
- Urgency and reminder language. It flags messages that use language to create a false sense of urgency, or reminder or pressure the user into clicking the link.
- File sharing intent. It recognizes the specific intent of file sharing in the email body, correlating it with the link to verify that it aligns with normal business communication patterns.
2: Spotting anomalies with the Nexus RG™ (Relationship Graph)
Nexus understands that a trusted link doesn't mean a trusted sender. Our Relationship Graph analyzes the broader context to find:
- Uncommon senders. It flags a message if there is no previously established relationship between the sender and the recipient, making a sudden file share highly suspicious.
- Campaign patterns. It identifies whether the same links or files have been shared with multiple other recipients simultaneously—a clear indicator of a mass campaign rather than a legitimate 1:1 file share.
3: Connecting the dots with Nexus ML™ (Machine Learning)
Our Machine Learning engine provides historical context to the immediate threat. It determines:
- Evidence of past suspect activity. It checks if the sender or the pattern matches previous suspect activity seen across our massive threat ecosystem.
- Malicious file associations. It analyzes whether similar known files have been associated with malicious intent in other attacks, linking the current “clean” link to known bad actors.
4: Detonating the trap with Nexus TI™ (Threat Intelligence)
Finally, the Threat Intelligence engine does not take the URL at face value.
- Sandboxing detonation. It triggers advanced sandboxing techniques to follow the URL chain to its end, effectively detonating the final malicious payload in a safe environment to reveal the hidden destination.
- Future-proofing. It identifies the new malicious webpage at the end of the chain and remembers these malicious sites for the future, instantly protecting all other Proofpoint customers from the same attack.
The Proofpoint Nexus advantage
Attackers use URL-to-URL chains to hide behind the reputation of trusted brands like Dropbox. Proofpoint Nexus looks beyond the brand to see the behavior. By combining language analysis, relationship context, real-time threat intelligence and advanced analysis techniques, Nexus ensures that even the most convincing URL-to-URL authentication threat does not trick your users and wreak havoc on your organization.
To learn more about how we can help your organization protect your people and your data from the next generation of AI-driven threats, schedule a demo.
Contact us to learn more about how Prime Threat Protection can help defend against subscription bombing and other emerging cybersecurity risks.
Read our Cybersecurity Stop of the Month series
To learn how Proofpoint Nexus stops advanced attacks, check out some of our recent blogs in this series:
- Hiding real attacks with subscription bombing (November 2025)
- Weaponizing AI Assistants with Indirect Prompt Injection (October 2025)
- BEC Attacks Targeting Government Agencies (September 2025)
You can find a full list of our Cybersecurity Stop of the Month blogs here.











