Welcome back to the Proofpoint Cybersecurity Stop of the Month blog series. In this series, we explore the ever-evolving tactics of today’s cyber criminals. We also focus on the critical first steps in the attack chain—reconnaissance and initial compromise—particularly in the context of email threats.
The aim of this series is to help you understand how to fortify your defenses, so you can be more effective at protecting your business against the emerging threats in today’s dynamic digital world.
So far in this series, we have covered supplier compromise, EvilProxy and SocGholish attacks. In this post, we look at a recent email signature (e-signature) phishing threat that Proofpoint detected. The threat was hosted on a well-known software-as-a-service (SaaS) provider’s website.
The scenario
Proofpoint detected a credential harvesting threat hosted on Amazon’s Amplify SaaS application; the app was being used by our customer, an automotive company with 2,000 employees. We blocked the threat prior to delivery, breaking the attack chain.
A bad actor had crafted a phishing lure purporting to be a sensitive document—an updated contract requiring review and countersign. The target was an employee who works with company contracts and has other fiduciary responsibilities. This employee often communicates with board members, customers and suppliers in the course of their work. So, they would expect to receive this type of request.
If the target clicked the malicious URL, they would then see a login screen that was designed to look like other legitimate login screens. The attacker’s goal was to trick the employee into handing over their credentials.
Applications like Amazon’s Amplify and other SaaS services such as DocuSign, Adobe Sign and OneSpan Sign provide bad actors with easy avenues to distribute malicious content under the guise of a legitimate reputation. Why does this matter? In the scenario above, the URL domain is over five years old. And the IP address belongs to Amazon, which would likely result in a clean verdict.
In June 2023, Proofpoint detected more than 75,000 different threats just like this one, which were behind 19 different email security vendors. That group of vendors includes some who claim to use advanced artificial intelligence (AI) and machine learning to detect these types of threats.
The threat: How did the attack happen?
Here is a closer look at how the recent attack at the automotive company unfolded:
1. The deceptive message: Our customer received an email inviting the employee to view and sign an updated contract.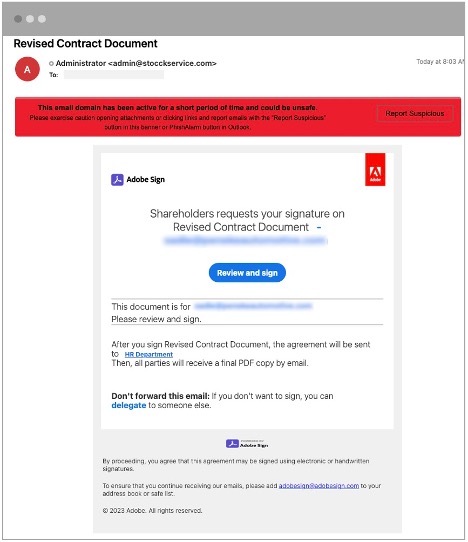
An image of the malicious email.
2. The malicious URL: If the user clicked on the URL in the email, they were asked for their credentials to view and take the requested action.
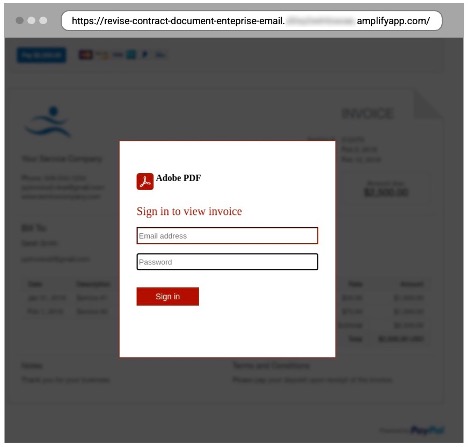
An image of the fake login page hosted on amplifyapp.com.
Detection: How did Proofpoint detect the attack?
Most email security vendors can detect commodity credential phishing attacks. However, the SaaS provider’s trusted domain adds a layer of complexity to most detection engines.
Proofpoint's behavioral AI engine leverages multiple message-level signals that allow Proofpoint to detect and block not only text-based threats (i.e., BEC and TOAD), but also other forms of threats including ransomware, Remote Access Trojans, but also credential harvesting threats such as in this scenario.
By clustering message-level tells, Proofpoint can detect novel phishing threats earlier in the attack chain and block threats prior to delivery.
We conducted a multilayered, deep analysis of the user’s profile and found an uncommon sender/recipient based on historical communication patterns. We found that the sender rarely communicates with the recipient or anyone else at the automotive company.
Using behavioral AI and machine learning techniques, Proofpoint conducted an in-depth analysis of the contextual nature of the URL. That analysis included the URL’s relevance based on previous historical data points and other anomalous activity. Across the entire company’s sending patterns, the URL had never been seen before—not by the recipient or anyone else within the company.
Proofpoint also detected the use of a legitimate and well-known SaaS provider’s domain. At other companies we help to protect, we have detected attackers abusing this same domain and using it to distribute malicious content.
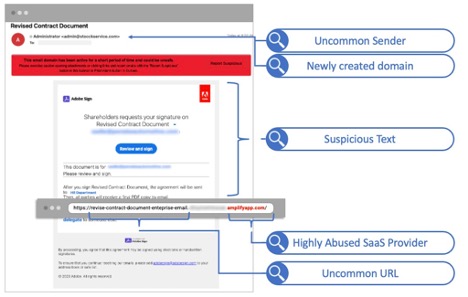
A summary of observations by Proofpoint about the e-signature email, which led to condemnation of the email.
Proofpoint blocked this threat before it was delivered because we detected:
- Uncommon elements in the URL
- The URL domain, which has been used in other attacks[AD4]
- Suspicious text within the body of the message
With additional, message-level behavioral inspection, Proofpoint can be more effective and efficient at blocking novel threats from reaching end users.
Remediation: What are the lessons learned?
To safeguard against threats like e-signature phishing and other URL threats that abuse reputable SaaS infrastructure, it is crucial to implement proactive measures like:
- User education. Your employees and customers are your first line of defense. Make sure they receive security awareness training that helps them learn about all types of phishing attacks, including deceptive emails and fake login pages. This training can help to reduce their chances of becoming the victims of phishing attacks.
- Cloud security. A good cloud security platform can identify account takeover (ATO) attacks and prevent unauthorized access to sensitive cloud resources. Such a solution covers both initial- and post-compromise activities. It also lets your security team get a closer look into which services and apps attackers are abusing. Look for a platform that automates remediation, as well. It helps to reduce attackers’ dwell time and keep damages to a minimum.
- Supply chain protection. Defend your supply chain from attacks that come from email. Proofpoint Supplier Threat Protection uses advanced AI and the latest threat intelligence to detect compromised supplier accounts and prioritize which accounts to investigate.
- Multi-factor authentication (MFA). Strong authentication measures like MFA can provide a big boost to your company’s security posture. But keep in mind that traditional MFA solutions can be ineffective at times. The scenario in this post is a case in point. That is why it is important to use cloud ATO automated tools to remediate these types of incidents fast.
- Preemptive email security. Preventing and blocking messages is the only sure way to keep users safe. Look for a solution—such as the threat detection platform from Proofpoint—that uses a combination of machine learning algorithms and advanced threat detection to identify and stop email threats. Other solutions claim to detect these threats. But they do so later in the attack, after the threat is in users’ inboxes. Users are then at risk until those threats are remediated.
Proofpoint helps to break the attack chain
In today’s sophisticated threat landscape, companies must be vigilant and proactive about protecting themselves and their customers. By using integrated technologies and collaborating with trusted cybersecurity partners, your business can stay ahead of evolving threats.
We invite you to stay tuned to this blog series as we continue to share information about the latest threats, our detection methodologies and more. And by shining a light on the attack chain, we hope to empower businesses to take proactive steps to defend against emerging threats.
Together, we can enhance threat visibility, improve efficacy detection and increase operational efficiencies to make the digital world safer for everyone.
Stay informed, protected and ahead of the game
To learn how to protect against threats like SaaS app phishing, download our e-book, The Definitive Email Cybersecurity Strategy Guide.











