An open question in the infosec community is how much user reporting of phishing messages benefits email security. Some customers tell us they’re all for it. Others are hesitant because they don’t have enough automation in place to manage the abuse mailbox successfully. That’s a valid concern, depending on the email security layers you have in place.
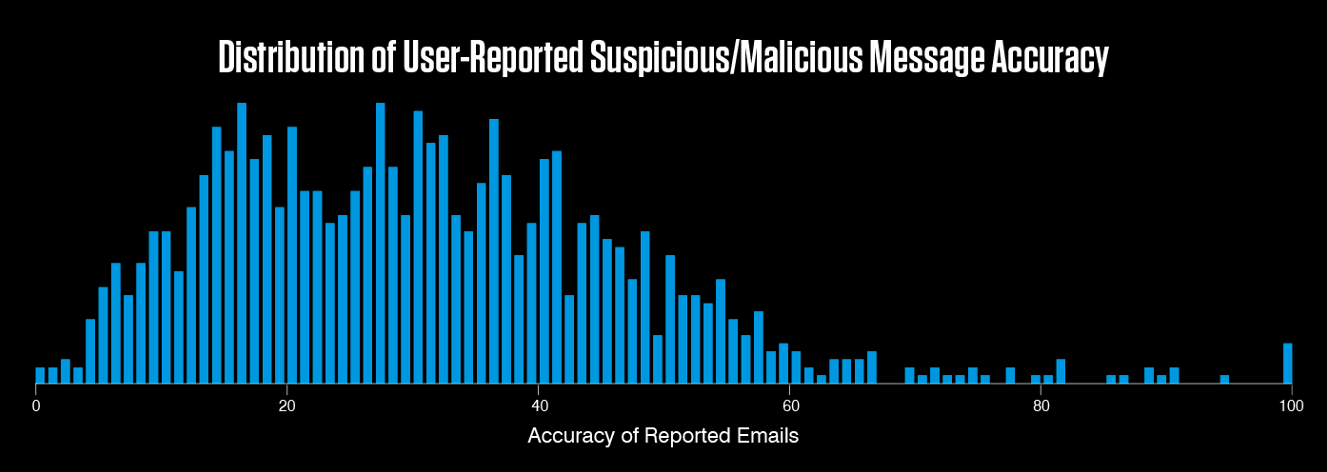
Figure 1. Research by Proofpoint of user-reported messages combined with our detection stack analysis found that, on average, 30% to 40% of what users were reporting was malicious or spam.
Phishing reporting add-ins: not perfect, and the data shows it
One recurring problem we’ve seen with phishing reporting relates to add-ins. Sometimes, collaboration suites make overnight updates that create issues with these add-ins, forcing teams scramble to update and re-rollout. Many times, when users encounter a phish, they are on a mobile device, with no access to a phishing reporting add-in. And sometimes, it takes too many clicks for users to report the phish easily.
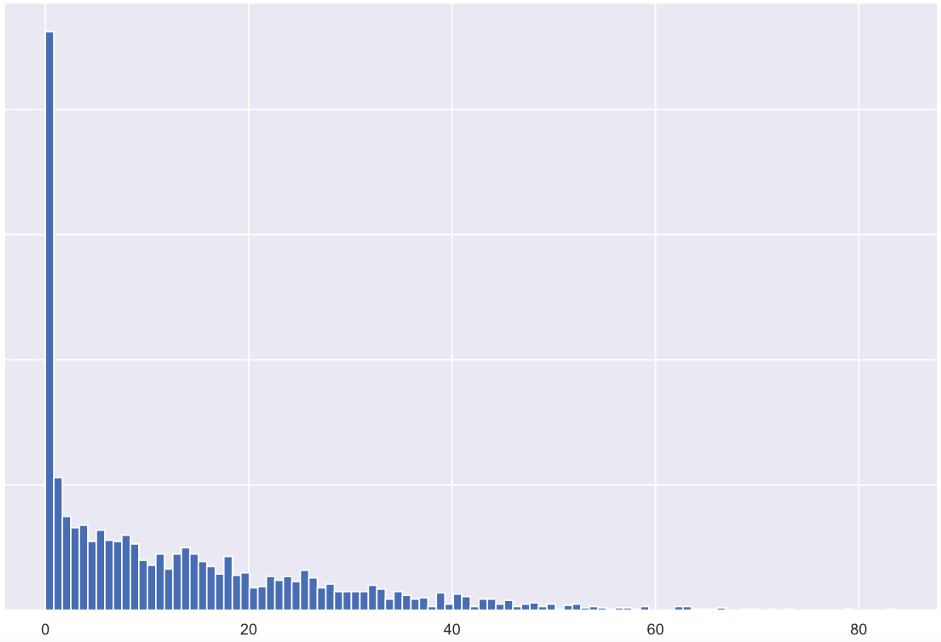
Figure 2. This graph shows that most customers fall into a low range of reporting rates because reporting add-ins have low awareness and aren’t always easy to access. (Y axis: number of customers, X axis: phishing reporting rate.)
This is reflected in how users engage with these add-ins. In Figure 2, you can see the difficulty many organisations have getting their users to actively use a phishing add-in for phishing simulations.
This small hurdle can be a big obstacle in building a strong, educated user base that can easily report suspicious messages that may slip by your technical controls.
The average reporting rate of phishing simulations is only 13%, with many organisations falling below that.
Average reporting rate of simulations by percentile:
|
Percentile |
Percentage of users reporting simulations |
|
25% |
1.4% |
|
50% |
8.5% |
|
75% |
19.9% |
|
Average |
13% |
|
Top-performing |
83.6% |
Thankfully, Proofpoint has an easier solution for phishing reporting for users and infosec teams.
Supplement PhishAlarm with our HTML-based email warning tags with “Report Suspicious”
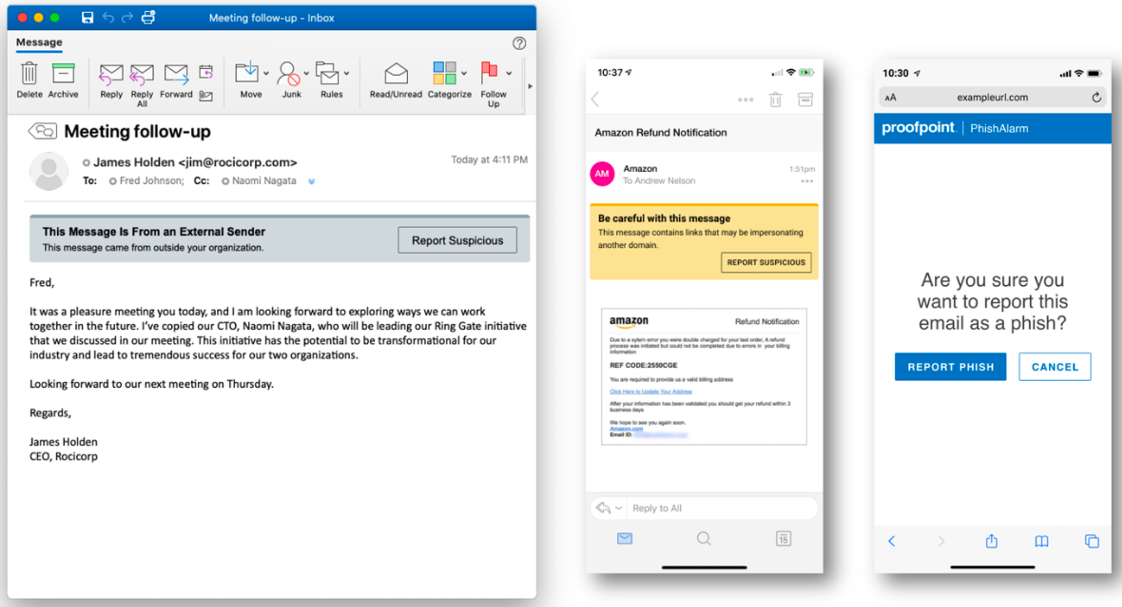
Figure 3. New HTML-based email warning tags from Proofpoint are device- and application-agnostic, and they make it easy for users to report potentially suspicious messages to infosec teams for automated scanning and remediation.
If you’re been using our PhishAlarm email add-in, there is a great way to supplement your existing investment and make phishing reporting and remediation even easier with this new capability. Both solutions live and operate seamlessly side-by-side to provide flexibility for your internal teams and users.
Our HTML-based email warning tags have been in use for some time now. And we’re happy to announce that all customers with the Proofpoint Email Security solution can now easily upgrade and add the “Report Suspicious” functionality. (All customers with PPS version 8.18 are eligible for this included functionality. Reach out to your account teams for setup guidance.)
The HTML-based email warning tags will appear on various types of messages. Administrators can choose from the following options:
Informational:
- External sender
- Email from new sender
Warning:
- Newly registered domain
- DMARC failure (identity could not be verified, potential impersonation)
- Mixed script domain (may contain links to a fake website)
- Impersonating sender (potential impostor or impersonation)
We’ll be using our full detection ensemble to refine and build new tags in the future.
The tags can be customised in 38 languages and include custom verbiage and colours. The best part for administrators, though, is that there is no installation or device support necessary for implementation. It is a true “set it and forget it” solution, saving teams time and headaches so they can focus on more important projects.
And what happens when users report suspicious messages from these tags? The same great automation for infosec teams and feedback from users that customers have come to love.
Automated abuse mailbox: same back end, easier reporting for users
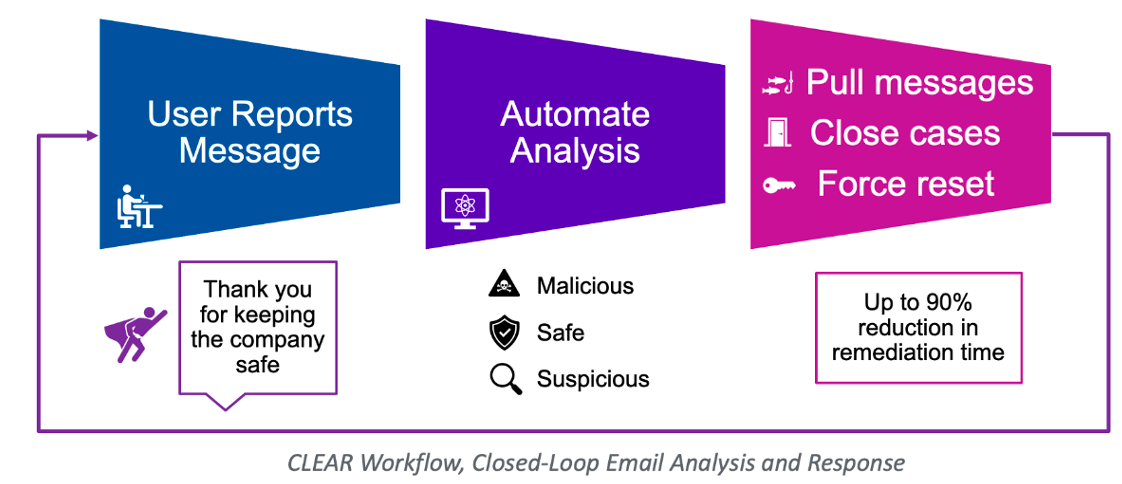
Figure 4. CLEAR, the automated abuse mailbox solution from Proofpoint, helps reduce remediation time by more than 90% for infosec teams and provides feedback to users who report messages.
When Proofpoint launched our automated abuse mailbox solution, Closed-Loop Email Analysis and Response (CLEAR), it was a pioneering technology, and the customer feedback was powerful:
“Time savings and automation have been huge. Can’t imagine going back to our old process.”
“Peace of mind that reported messages can be automatically and effectively removed without having to engage in a complicated process.”
We’re thrilled that thousands of customers use CLEAR today. And now, with email warning tags and the “Report Suspicious” functionality, we’ll make phishing reporting and remediation even easier for users, with the ability to spot and report potentially dangerous messages on any device. For existing CLEAR customers, no updates are needed when “Report Suspicious” is enabled, and the workflow will be normal.
In-depth behavioural and threat insights
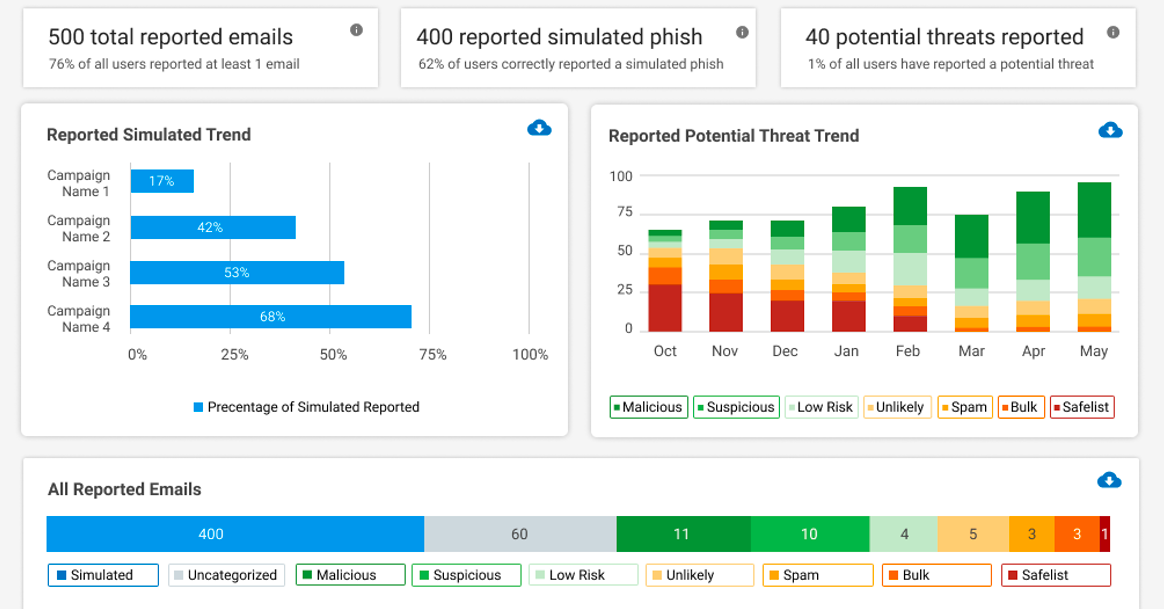
Figure 5. Proofpoint provides details about employee reporting accuracy—and even benchmarks performance against other customers.
We provide in-depth reporting in our security awareness platform and our CISO Dashboard to help you understand user reporting behaviour—and if it’s getting better. You can also use the insight to tailor your security awareness program and measurably demonstrate the impact of users protecting your organisation. (We highly recommend rewarding and recognising users who are helping to protect the organisation—maybe in a newsletter or contest.)
If you’re interested in comprehensive and impactful threat protection, read the “2021 Gartner Market Guide for Email Security” to make sure you’re covering all key use cases and getting the necessary efficacy to protect your organisation.











