
Gain adaptive controls for high-risk users and credential phishing protection
Today’s cyber attacks target people. To stop them, you need a people‑centric understanding of how attackers work, who they target, and what they might be after.
Download the Solution BriefThe Challenge
- Phishing and stolen credentials are the two leading tactics in data breaches.
- Attacks are always evolving and target the weakest point in your attack surface—your users.
- Conventional security and one-size-fit-all access controls can get in users’ way and make them less productive.
- Old approaches preventing and resolving stolen credential attacks simply don’t work. They are often siloed, fragmented or incomplete.
The Solution:
- Proofpoint and Okta combine leading email security, cloud security, and identity solutions to safeguard the tools you rely on: Microsoft 365, Google Workspace, all Okta-federated apps, and your broader IT environment.
- Email is today’s No. 1 threat vector. Protect it with today’s only people-centric defense.
- Protect crucial information in cloud accounts with the first and only CASB solution in the market to protect your 7000+ Okta-federated cloud apps from account takeover.
- Protect all your users. Apply extra controls to your Very Attacked People™ (VAPs). Adaptive controls can focus extra security layers where they are needed most.
- Orchestrate response and remediation efforts to contain attacks. Automatically enforce step-up authentication for compromised users.
Strengthen your defenses with people-centric security
As traditional network boundaries fade, cyber attackers are focusing on people. That’s why you must evolve your approach to protect your “people perimeter.” Proofpoint Targeted Attack Protection (TAP) and Okta Identity Cloud make identity-driven security easy and effective.
Combine our world-class email protection with Okta’s market leading identity management to secure Microsoft 365, Google Workspace and your whole IT environment. Our joint solution gives you a powerful defense against phishing and credential-based attacks. With Proofpoint and Okta, you get:
- Unmatched visibility across today’s threat landscape
- Granular adaptive controls for proactive security
- Powerful tools to automate threat response and remediation
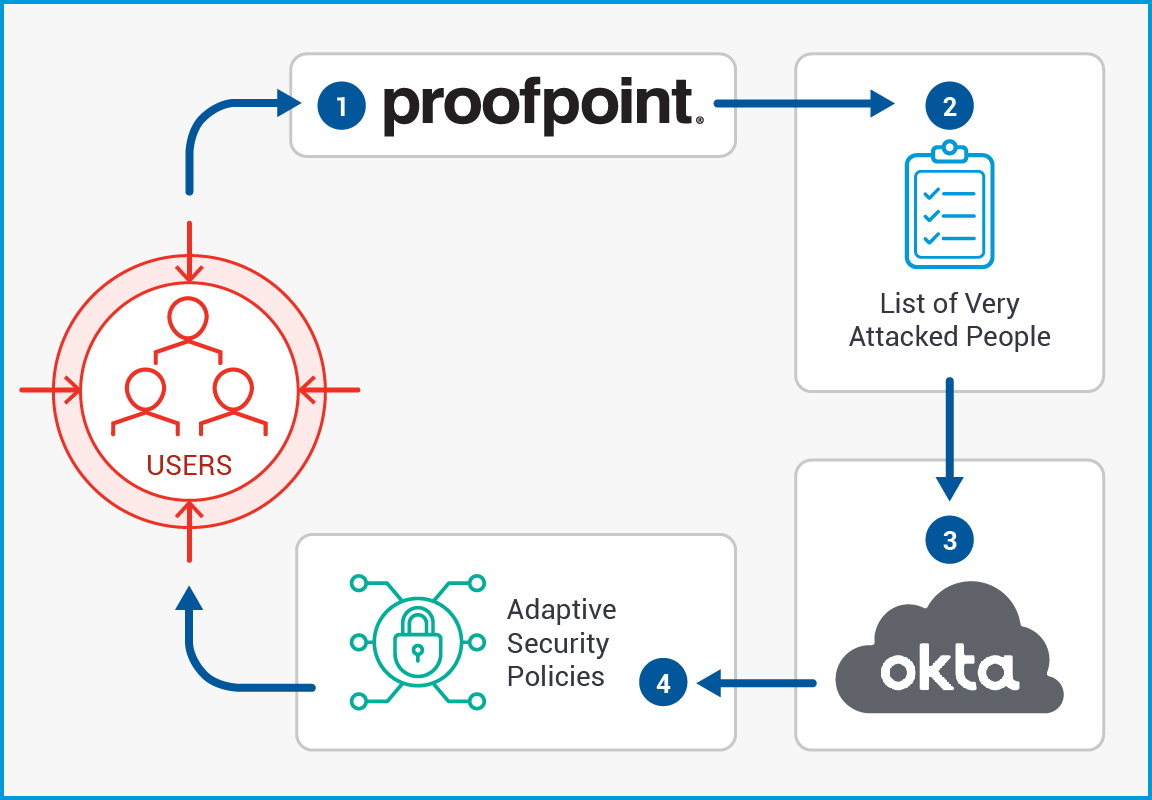
Adaptive Security Controls for VAPs
Proofpoint TAP identifies your VAPs and shares that insight with Okta Identity Cloud. You can automatically apply adaptive controls to secure those users’ accounts. These include authentication policies such as:
- Password policy
- Factor enrollment
- Application access
- Application sign-on
- User roles/entitlements
Another way you can use this unique VAP insight is through the Proofpoint and Okta Workflow Connector. This lets your team easily program and activate automated workflows that dramatically improve your enterprise security. It improves your response time, enhances visibility and automates definitive responses to email, mobile and other threats. Your team can also apply decision logic, such as branching, flow control, and data manipulation. And with our pre-built app connectors and API connections, it brings your entire tech stack to bear.
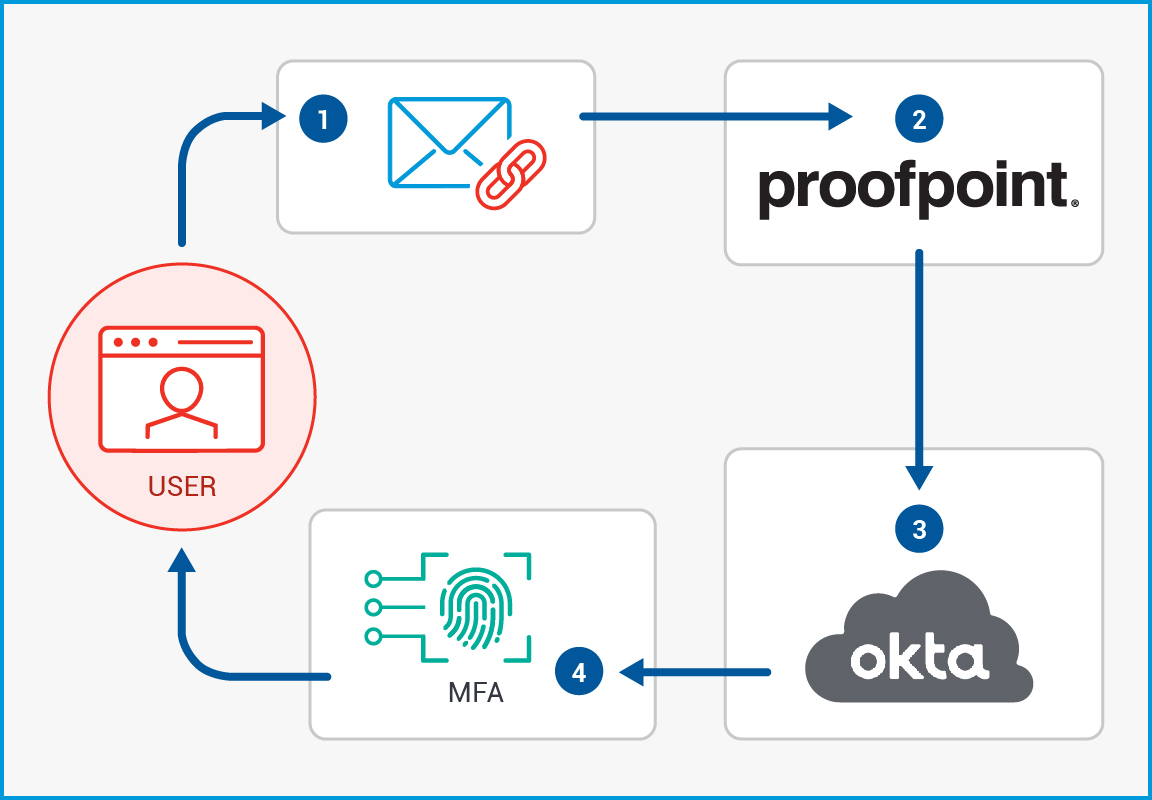
Close the Security Loop: Email
When users click a phishing link in an email, Proofpoint Threat Response Auto-Pull (TRAP) removes it from their inbox. From there, TRAP alerts Okta. And Okta adds those users to a group subject to stricter multi-factor authentication.
Close the Security Loop: Cloud
Proofpoint detects and remediates suspicious logins to cloud applications via Proofpoint Threat Intelligence, TAP, and CASB behavior analytics. We then alert Okta who then applies Proofpoint policies to those user accounts.

Real-time insight to help prioritize threats and act on them
Email threats are constantly evolving. TAP evolves with them to detect and resolve new threats as they arise.
