If a user avoids clicking on simulated phishing attacks – does it mean they’re less risky? On the surface, yes, it should mean that. But it isn’t the full picture.
The reality is what’s actually happening in your company’s environment matters more to your risk profile than simulations. Users could be engaging with real phishing messages – just avoiding simulated ones. Attackers could be laser-focused on exploiting a user who isn’t considered risky through the lens of your security awareness training program. So there’s a mismatch of security awareness risk and real risk. Until today.
Today Proofpoint released an industry-first innovation to make security awareness real. Our new Targeted Attack Protection Guided Training integration takes Proofpoint’s leading advanced email security product and ties its rich people-centric and threat landscape data to Proofpoint Security Awareness Training. Let’s dive into what this means for driving better behavior change at your organization.
See Risk Through a Brand New Lens
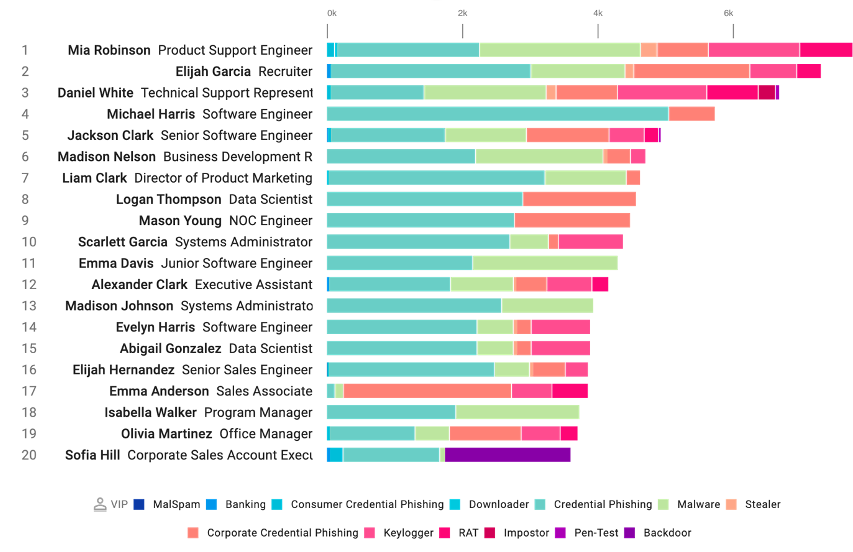
Sample data from a Very Attacked Persons (VAP) report in Proofpoint Targeted Attack Protection advanced email security dashboard
Your risk insights just got an upgrade. Now, in addition to results of simulated attacks and knowledge assessments, you’ll be able to see risk in your real environment.
Top Clickers from Proofpoint’s Targeted Attack Protection advanced email security dashboard.
You’ll see users who are engaging with real malicious content (Top Clickers) – even if the click was blocked or rewritten by the email gateway solution. In addition, you’ll be able to see your Very Attacked People (or VAPs) – users who are being targeted by attackers. We’ve found with customers these VAPs can be 4-10x (or more!) attacked than the average user at the organization. It isn’t just volume measured of messages trying to get through, but the severity and targeted nature of the attacks those users are getting sent.
By focusing your education initiatives on both of these types of users, you can be more focused and prescriptive about reducing risk while efficiently using employee time. This visibility also highlights potential blind spots, like employees that are VAPs or Top Clickers but haven’t been involved in your organization’s security awareness program previously.
Apply Smarter Adaptive Controls with Relevant Education
Let’s see how you can put this insight into action with more impactful educational experiences for users.
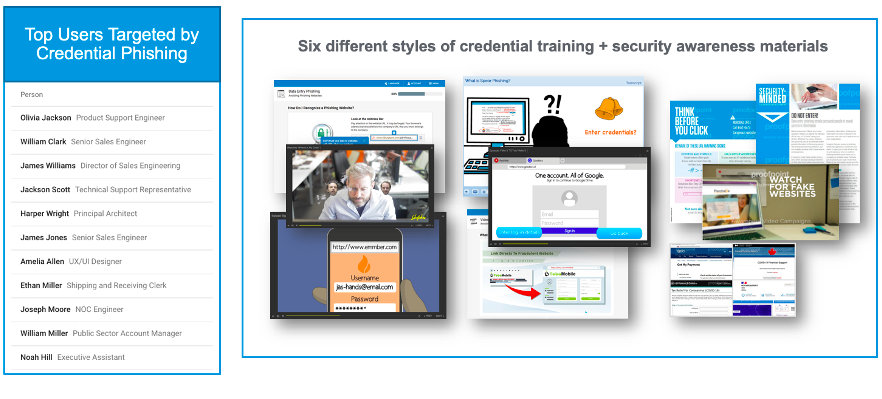
Look at the Risk from a People-Centric Perspective
As the security administrator, you are reviewing the Very Attacked People (VAP) data and you notice that credential phishing is currently the predominant threat type being sent to your users. Since these users could be high risk, you decide to set up a phishing simulation.
Make the Simulation Relevant to Your Threat Landscape
There has been a large volume of OneDrive credential phish impacting your environment. During your simulated phishing campaign creation choose VAPs being targeted by credential phish and use some of Proofpoint’s templates from real attacks to simulate the threats seen in your environment.
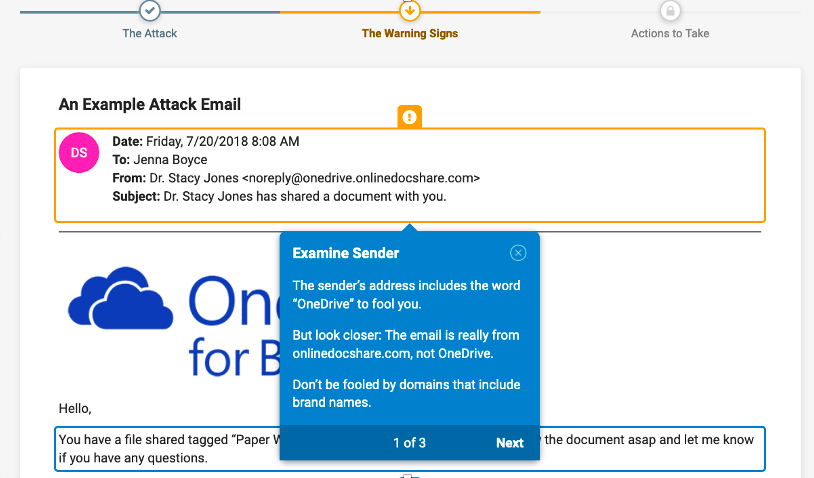
Create an Impactful Educational Experience with a Call-to-Action
Finally, for users who fall for one of the simulations, you automatically assign one of our Attack Spotlights, a short 3-5 minute education module based on real threats. To make it even more personalized, you customize the module to tailor it to your users. At the end of the module you ensure users know your abuse mailbox address, or to user their email reporting add-in to report the message.
This new visibility into risk combined with our leading content library means not only a variety of ways to engage users, but that education delivered to users is more impactful in the ultimate goal of behavior change.
Align Your Teams Towards a Common Goal
Security awareness training is not an island. And with competing priorities and distributed workforces, it’s more important than ever that security awareness teams work collaboratively with others in security and in the organization. Connecting with HR, Incident Response, Email Security, and other internal teams about the program brings stakeholders to the table, helps get buy-in, and shows your program is aligned to business needs and other team’s goals.
More specifically, the Very Attacked People and Top Clicker data is information email security teams leveraging Proofpoint’s advanced email security solution will have previously had exposure to. So, it’s a great way to start the conversation. Then both teams can have different conversations with management about risky and very attacked users.
With this exclusive integration, we recommend working with the email security team to understand the threat landscape, discuss with teams the “Why” behind the data, and align on how adaptive controls like security awareness, web isolation, and others can focus on reducing risk and provide benefit to your organization. Since these two data points can change frequently, having an ongoing sync is the best way to stay aligned on the ultimate goal of reducing end-user risk.
Making Security Awareness Even More Real
With this new visibility, you’ll get more insight into how to run a more effective program that aligns security awareness to risk in your environment. But that’s just one component of the program. Ultimately you need users to become, “part of the security team” as one of our customers succinctly put it. The best way to do that – empower them to report suspicious messages to an abuse mailbox.
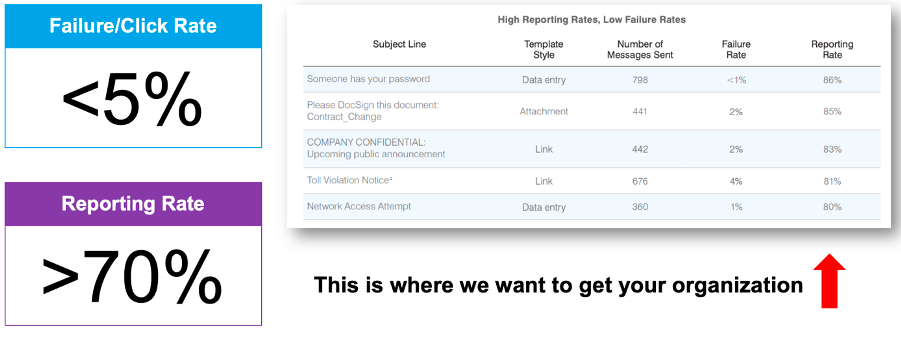
In our 2020 State of the Phish report we found that organizations using our email reporting add-in had users reporting on average 10-20% of simulated phishing messages sent to them. But more importantly, customers with ongoing, impactful programs were able to get that number to 70% plus, or even more as shown above. The “70/5” rule (>70% reporting rate and <5% click rate), as we like to call it, is important because the click rate reduces vulnerability but the reporting rate proves users know what to do when faced with a real threat and ultimately can reduce exposure even more.
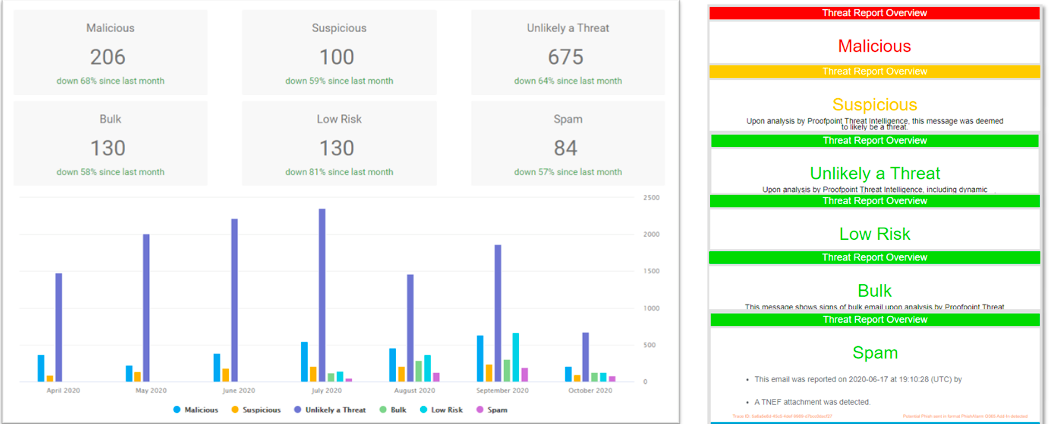
To take it a step further, using our leading Nexus threat intelligence and sandboxing technology, we’ll show you what kind of real messages your users are reporting and if they’re getting better at reporting malicious/suspicious messages instead of spam or safe messages. Our reports will demonstrate the impact of your security awareness efforts.
See Targeted Attack Protection (TAP) Guided Training in a customized demo of our security awareness solution and see how we’re making security awareness more real for organizations worldwide.












