Proofpoint researchers analyzed activity from 2019 through August 2021 impacting entities in Germany to provide a comprehensive view of threat activity in the region and assess what types of threat activity might impact this region in the future. Researchers assessed over 400 campaigns impacting organizations in Germany and found a striking drop in message volume in 2021, but a significant change in the threat landscape as other threats appeared to dominate the landscape.
This analysis is based on email threat campaign data identified by Proofpoint researchers.
Proofpoint researchers took a proactive approach to identifying and analyzing threats to German organizations based on key assumptions regarding timely and relevant political, economic, and social factors in the German threat landscape. To guide our hunting and analysis efforts, analysts developed the following hypotheses:
- Emotet’s disappearance from the threat landscape will cause a significant drop in the cybercrime threat volume targeting the region.
- Emotet’s disappearance from the landscape will lead to a diversification of identified threats.
- Threat actors will leverage themes related to Germany’s upcoming federal elections on 26 September 2021 in spam and targeted campaigns.
- Germany’s economy is dominated by industrial and critical infrastructure businesses including in the automotive, mechanical engineering, chemical, and manufacturing. Proofpoint anticipates threats targeting the country’s businesses will frequently leverage industrial-themed lures.
- Threat actors conducting credential phishing attacks against German organizations will leverage themes common worldwide including banking, healthcare, and enterprise software lures.
- First-stage ransomware threats will likely not appear in 2021 data. That said, initial access facilitators will likely continue to be a vehicle to distribute ransomware.
Throughout our month-long investigation, Proofpoint researchers found that some of our hypotheses were supported by internal campaign data, while others were not.
Key Findings
- The international takedown of the Emotet botnet resulted in a significant dip in threat activity intended for German entities.
- Commodity malware threat types targeting German organizations include Remcos RAT and Formbook malware. Campaigns distributing malware frequently leverage German industrial control and engineering themes.
- Ransomware as a first stage payload is rare.
- Phishing activity accounts for most of the German language message volume in 2021, largely focused on obtaining banking credentials.
- Threat actors have not leveraged German election themes in widespread campaigns so far in 2021.
Threat Overview
Emotet's Impact
Hypothesis: Emotet’s disappearance from the threat landscape will cause a drop in the cybercrime threat volume targeting the region.
Finding: ✅
For the past few years, Emotet malware dominated the German cyber threat landscape, based on data gleaned from email threat campaigns identified by Proofpoint researchers. This is not surprising. The botnet was among the most prolific threats globally for years before it was disrupted in January 2021 by a coordinated global law enforcement effort. The Emotet campaigns impacting German entities were part of broader threat campaigns distributed by a group Proofpoint tracks as TA542 that targeted European and North American organizations and sent lures in multiple languages, including German. The disruption of the Emotet botnet was consistent with an observed steep decline in malicious messages observed by Proofpoint.
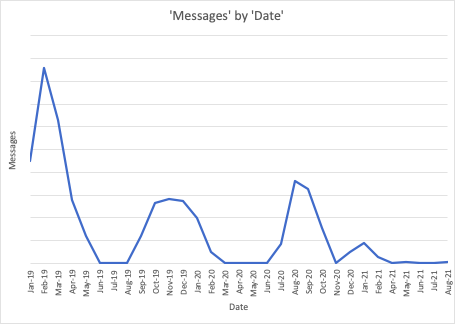
Figure 1: Message volume since January 2019. The spikes coincide with Emotet malware campaigns.
Hypothesis: Emotet’s disappearance from the landscape will lead to a diversification of identified threats.
Finding: ❌
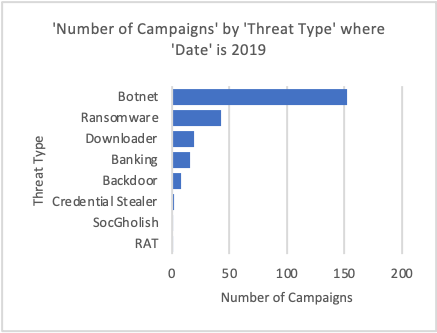
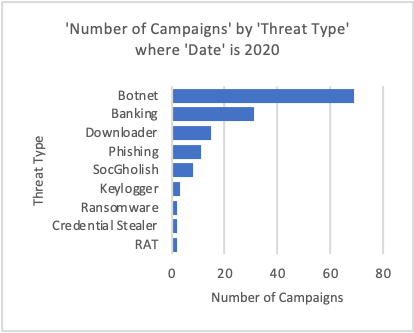
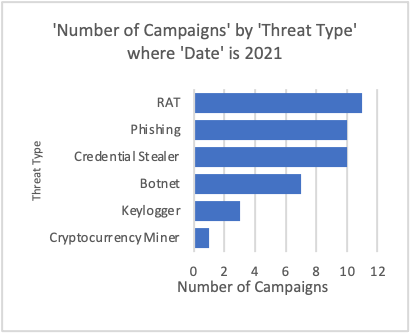
Figure 2-4: Most frequently observed threat types per year with targets including German entities.
Proofpoint researchers observed that Emotet’s disappearance from the threat landscape in January 2021 resulted in different malware and threat actors filling the gap left behind – but not in greater numbers. Emotet campaigns accounted for millions of messages and included broad, indiscriminate targeting.
In 2021, the number of total campaigns has decreased significantly, and the number of identified threat types has also decreased. For example, Proofpoint researchers identified nine significant threat types in 2020, versus just six in 2021. Proofpoint researchers observed more commodity malware including remote access trojans (RATs), credential stealers, and keylogger campaigns impacting German organizations than other threats in 2021. Between 2019 and 2021, the number of campaigns distributing data stealing malware impacting German entities has increased dramatically. This is driven by an increase in the number of observed campaigns distributing FormBook malware and various remote access trojans (RATs) via German-language lures.
RATs became the most frequently observed threat type in identified campaigns in 2021, after being the least frequently observed threat type the previous two years. Credential phishing also leapfrogged in popularity to become the second most frequently observed threat type based on several campaigns with targets including German organizations.
Although the number of identified campaigns decreased significantly in 2021, they are more evenly spread across RATs, stealers, and keyloggers. So far, no single threat type dominates the German threat landscape in 2021.
Commodity Malware
Hypothesis: Germany’s economy is dominated by industrial and critical infrastructure organizations including in the automotive, mechanical engineering, chemical, and manufacturing. Proofpoint assesses threats targeting the country’s businesses will frequently leverage industrial-themed lures.
Finding: ✅
Frequently, the lures used by malware actors distributing RATs, keyloggers, etc. impersonated German and other European industrial and engineering companies. Organizations such as those in metalworking, manufacturing, and mechanical engineering are frequently leveraged as lures. In recent months, a majority of the German language malware campaigns observed by Proofpoint have almost exclusively used industrial and engineering themes.
Example: Formbook
Proofpoint researchers have observed ongoing German language FormBook campaigns targeting German organizations and others in Europe and North America throughout 2021. Observed targets included many entities supporting critical infrastructure. FormBook is a commodity browser form stealer/keylogger. It is actively developed and can be purchased online for a low one-time fee. It is used by many cybercrime threat actors.
In the observed campaigns, the threat actor spoofed German industrial and engineering companies including some of Germany’s largest industrial equipment providers. The emails were written in German and English and purported to be business requests, machine information, or payment requests.
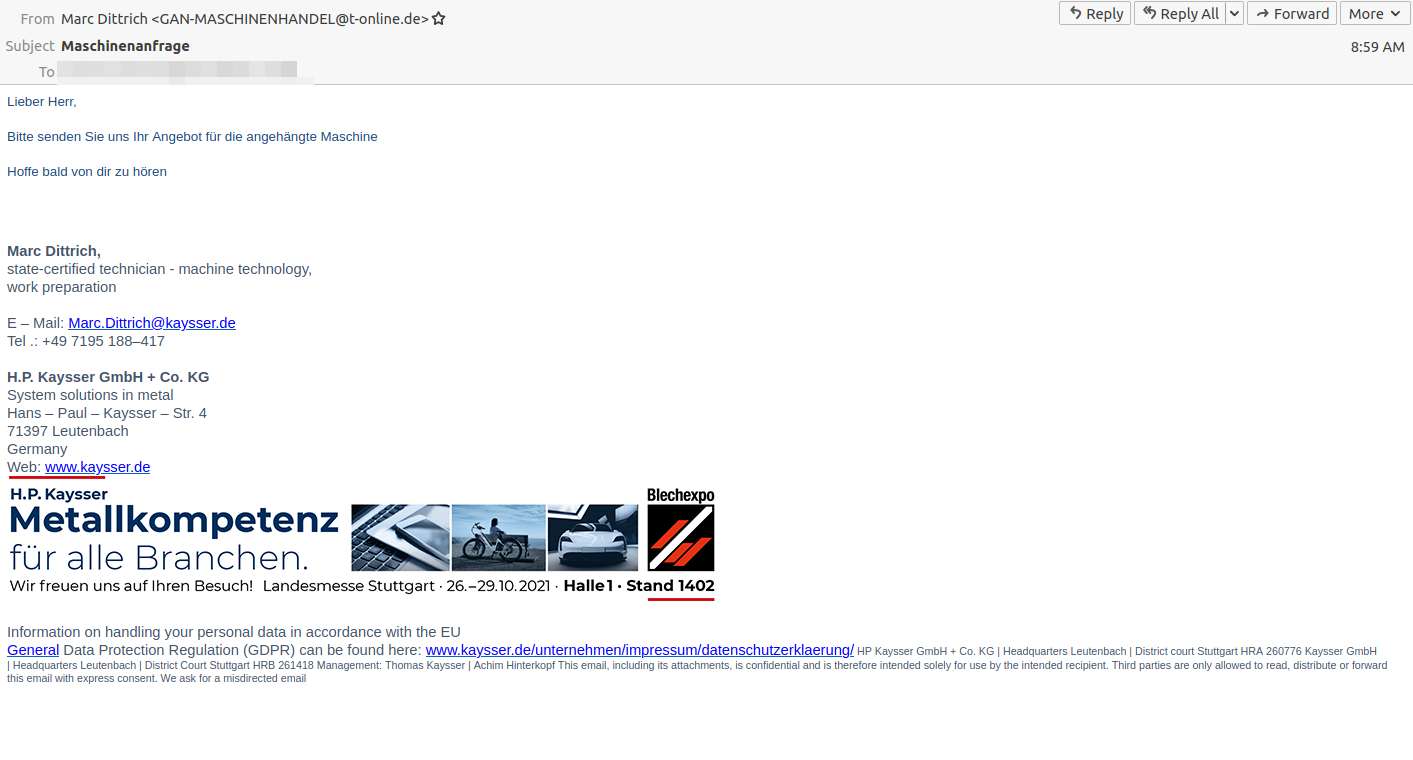
Figure 5: Phishing email requesting an offer/proposal for industrial equipment and related specifications.
The messages contain either an attached compressed executable or a malicious URL leading to a downloaded executable of a similar filename and theme. The malicious link is a Sendspace URL that leads to the download of a compressed executable (e.g. angebotsdokument.cab) that installs FormBook. Sendspace is a free file hosting service that is often used by threat actors to host malware. Proofpoint does not attribute this activity to a known threat actor.
Example: Remcos RAT
Beginning in mid-August 2021, Proofpoint researchers identified thousands of emails masquerading as request for quotes, payment requests, or business proposals targeting organizations in multiple industries worldwide and distributing the Remcos remote access tool. The emails masqueraded as industrial related organizations including German mechanical engineering company Kronen, Dutch manufacturing company Holmatro, and Spanish chemicals firm Quality Chemicals. The emails were written in German and Spanish.
The messages impacted over 700 customers globally including manufacturing, pharmaceutical, technology, and industrial organizations among others. Geographic targeting focused mostly on North America and Europe. The email senders masqueraded as industrial company representatives.
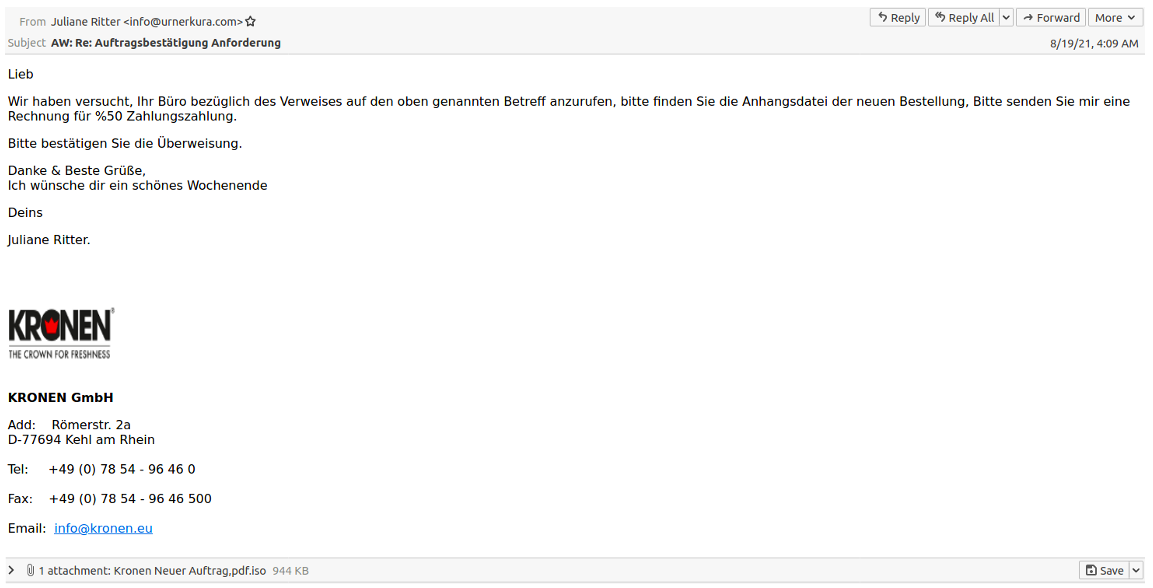
Figure 6: Email sample purporting to be an order confirmation request from Kronen.
The message translates to:
We tried to call your office regarding the reference to the above subject, please find the attachment file of the new order, please send me an invoice for% 50 payment.
Please confirm the transfer.
These messages contain ISO attachments ultimately leading to the installation of the Remcos remote access tool (RAT). The threat actors leverage DBatLoader (also called ModiLoader) as the initial loader for the final RAT payload.
Remcos is a RAT available for purchase online, and can be used for legitimate remote management. It is also used by many cybercrime threat actors. DBatLoader is frequently seen distributing Remcos; it is a loader written in the Delphi programming language that uses cloud services to download the stager component, which the actual payload is embedded in. In the observed campaign, threat actors leveraged One Drive cloud hosting services.
Proofpoint does not attribute this activity to a known threat actor. In both FormBook and Remcos campaigns, the targeting appears opportunistic. Despite the industrial control themes and targeting, Proofpoint assesses with high confidence this is a commodity cybercrime threat and not an industrial control system (ICS)-specific disruptive or destructive campaign.
Example: STRRAT/vjw0rm
Proofpoint researchers recently observed a targeted industrial-themed campaign distributing STRRAT and vjw0rm. The German-language email targeted a handful of manufacturing entities with operations in Germany.
The email contains the following subject:
"ANGEBOT: Interesse an Metallbearbeitungsmaschinen" (Translates to: OFFER: Interest in metalworking machines)
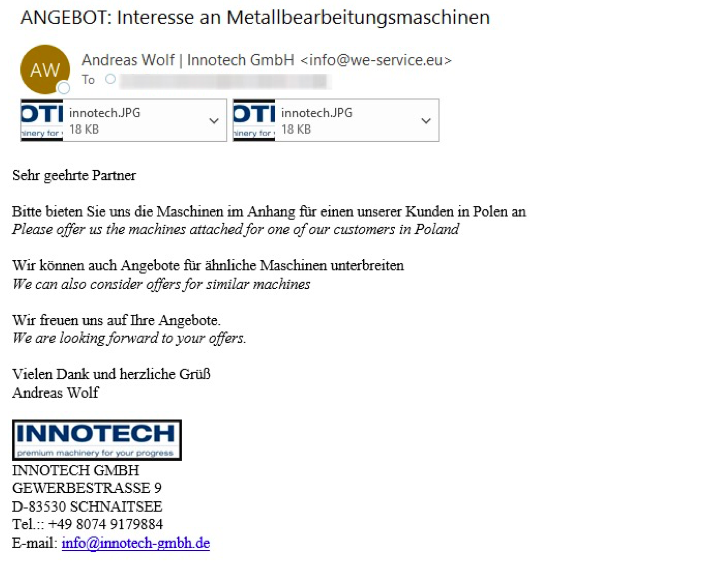
Figure 7: Industrial themed lure distributing STRRAT and vjw0rm malware.
These messages contain an executable file which contains two JAR files (AGB_INNO.JAR and MACHINE_.JAR). If executed, it will load vjw0rm and STRRAT. STRRAT a remote access trojan with a focus on stealing credentials of browsers, email clients, and passwords via keylogging. Vjw0rm is the JavaScript version of vw0rm (a VBS worm) with USB spreading functionality. The use of a USB-targeting malware impacting industrial organizations is interesting as it may be used to bridge the gap between the information technology (IT) network and the operations technology (OT) network in organizations supporting ICS. However, Proofpoint has no evidence that suggests this was an ICS-specific campaign targeting OT environments.
Ransomware
Hypothesis: First-stage ransomware threats will likely not appear in 2021 data. That said, initial access facilitators will likely continue to be a vehicle to distribute ransomware.
Finding: ✅
The number of campaigns impacting German organizations in which ransomware was a first stage payload plummeted dramatically from over 40 to nearly zero between 2019 and 2021. This mirrors the overall ransomware threat landscape. Historically, threat actors targeted entities in Germany with first-stage ransomware payloads at a higher rate than other regions. According to Proofpoint data, ransomware accounted for 2% of the overall threat landscape in 2019, while ransomware made up nearly 18% of the German threat landscape based on campaign data that year.
Now, ransomware threat actors have largely shifted from direct email threats to indirect threats where email is only part of the attack chain. Ransomware threat actors often leverage cybercriminal enterprises – largely banking trojan distributors – for malware deployment. While Proofpoint continues to observe high volume campaigns of malware that can act as initial access facilitators for follow on ransomware payload, such as BazaLoader, Dridex, or IcedID, Proofpoint does not frequently observe such malware specifically targeting German entities.
Example: Philadelphia ransomware (June 2020)
However, Proofpoint occasionally still sees ransomware as a first stage payload. In 2020, ransomware cybercriminals – like many other threat actors – took advantage of concerns surrounding the global COVID-19 pandemic in their campaigns. In June 2020, Proofpoint researchers identified a Philadelphia ransomware campaign masquerading as the German federal government. Philadelphia ransomware is an uncommon ransomware strain that first appeared in 2016.
The threat actors sent messages with the following characteristics:
From: Federal Germany Government <information@germany-government.eu> Subject: Die Entscheidung, Ihr Unternehmen aufgrund von Covid-19 zu schließen
In English, the subject translates to “The decision to close your business due to Covid-19”.
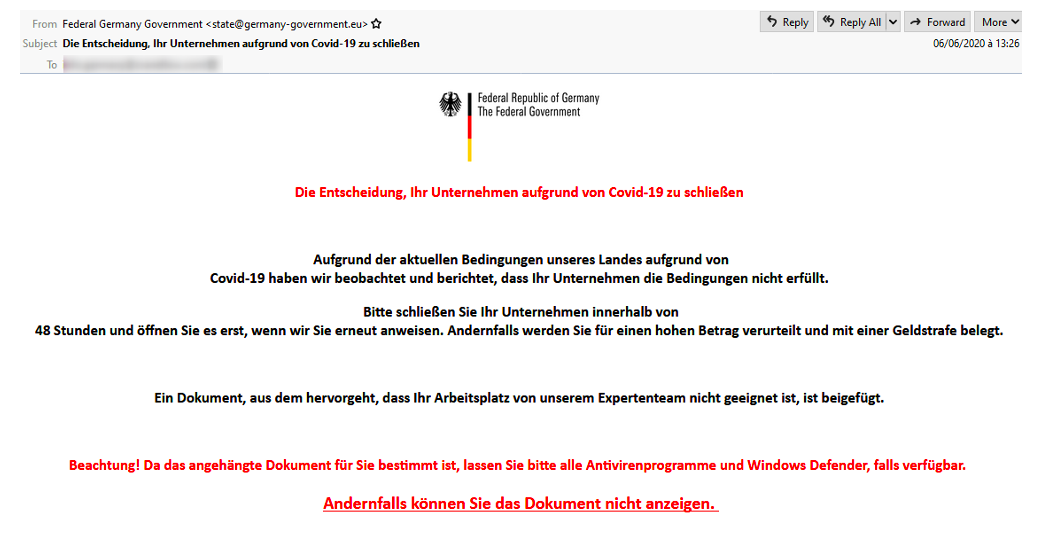

Figure 8: Sample of the German government themed Philadelphia ransomware email lure
These messages contain One Drive-themed links leading to a compressed executable, Philadelphia Ransomware.
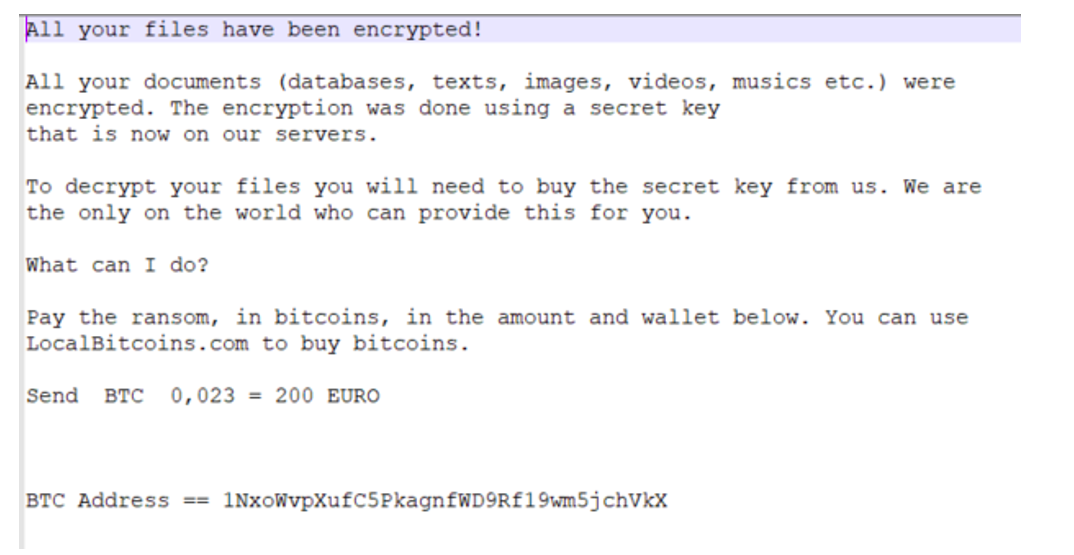
Figure 9: Philadelphia ransomware note
Despite occasionally appearing in email threat data, Proofpoint assesses that ransomware threat actors will continue to bypass direct email distribution of threats and instead rely on initial access facilitators and external or remote access vectors to distribute ransomware.
Credential Phishing
Hypothesis: Threat actors conducting credential phishing attacks against German organizations will leverage themes common worldwide including banking, healthcare, and enterprise software lures.
Finding: ✅
In terms of message volume, credential phishing is the second most high-volume threat impacting German entities in 2021, following Emotet. Proofpoint identified nearly one million credential theft campaigns specifically targeting entities in Germany. The messages attempted to steal banking or corporate credentials.
Example: Sparkasse Bank
Two of the most high-volume phishing campaigns observed in 2021 attempted to steal banking credentials for Sparkasse bank. For example, a May 2021 campaign included hundreds of thousands of messages with the subject “Wichtige Nachricht" which translates to “Important Message.”
These messages contain links that lead to a spoofed Sparkasse website. It is designed to steal banking credentials including usernames and passwords.
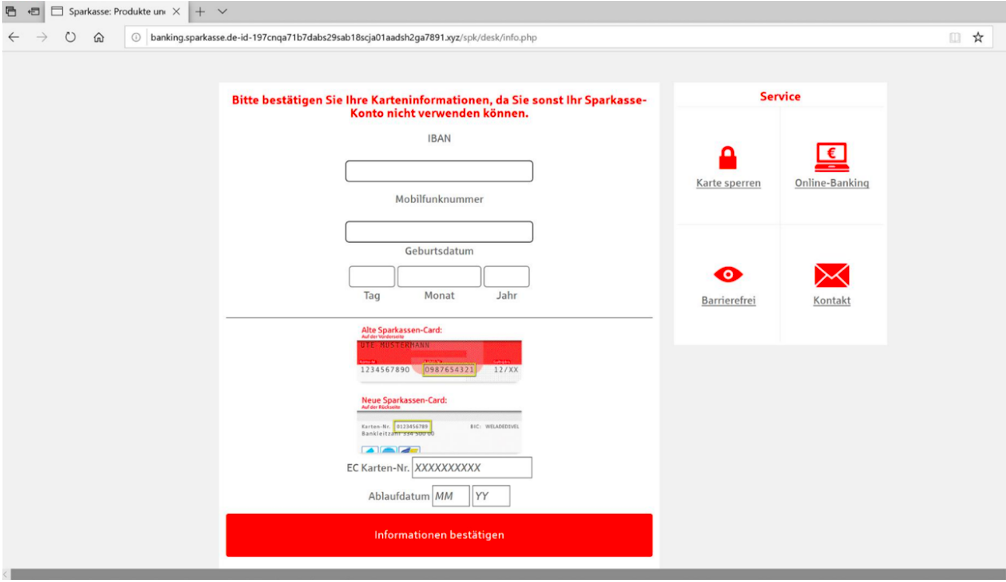
Figure 10: Sparkasse credential capture page
Proofpoint researchers observed additional phishing campaigns leveraging lures such as Volksbank and generic Microsoft Office themes, among others.
German Elections
Hypothesis: Threat actors will leverage themes related to Germany’s federal elections on 26 September 2021 in spam campaigns.
Finding: ❌
As Germany prepared for its parliamentary elections on 26 September 2021, officials and security practitioners anticipated attempts by cyber threat actors to disrupt or interfere with election efforts. Generally, these types of activities will be conducted by state-sponsored actors, as we’ve previously observed in multiple countries. Such activities include credential capture, disinformation campaigns, and hack and leak efforts. Third-parties identified threat activity associated with the Ghostwriter threat group targeting German politicians leading up to the elections. Proofpoint tracks Ghostwriter as TA445. When Proofpoint has historically observed Ghostwriter activity, threat campaigns have been successfully discarded.
Cybercrime threat actors have historically used election-themed lures to distribute spam campaigns during election season as well. In 2017, Proofpoint researchers found spammers began using election-themed lures in earnest in May, over three months before the official election.
While analysts anticipated threat actors would begin leveraging election themes at the same rate as prior years, Proofpoint data does not support this assumption. So far in 2021, Proofpoint has not observed significant email threat activity related to Bundestag election.
Conclusion
With the departure of Emotet, the German threat landscape looks much different in 2021 than previous years. Although researchers anticipated a diversification of threats to this region, the number of campaigns and identified threat types decreased this year. Of the observed malware including RATs and keyloggers targeting organizations in Germany, many leveraged themes such as engineering or manufacturing business proposals. This theme is expected due to industrial and related organizations making up a large portion of the German economy.











