(Updated 10/19/2020) Email isn't going anywhere anytime soon. In the work world, it is still the most common means to communicate and exchange information. Sometimes it’s an employee innocuously emailing an attachment to their personal email to work on it remotely, while at other times, it's a disgruntled or departing employee sending files to themselves or other external recipients. Regardless of intent, these actions may expose the organization to data exfiltration risks with their intellectual property (IP), sensitive data and employees’ personal data. Traditionally, security teams had to rely on email data loss prevention (DLP) and email security providers. During incident investigations, these solutions require significant manual analysis of email logs, yet they don't provide the critical user context. With Proofpoint, security teams can detect data exfiltration from email in real-time and investigate such alerts in minutes. This includes full context about the user, file and email activity during, before and after the email was sent or received.
Proofpoint Insider Threat Management now includes selective recording around triggered alerts, more control over fine-tuning alerts, and more capabilities for monitoring Mac endpoints. This is alongside detecting and responding to data exfiltration by email applications. In this post, we’ll take a deep dive into the new features and share how your organization can put them to work to intelligently manage insider threats.
Email Monitoring for Data Exfiltration
Email is a key exit and entry point of sensitive data within any organization. So it’s necessary to have visibility into user and file activity related to the email. With Proofpoint Insider Threat Management, organizations can now monitor the desktop Microsoft Outlook application on Windows and Mac. This includes the Mac Mail application, providing comprehensive visibility into users sending sensitive files over email and saving attachments received over email.
Organizations can detect, investigate and respond faster to email-related insider threat incidents by gaining full context into the email activity. We provide granular visibility into:
- Sender and recipients domains (including to, cc and bcc addresses)
- Subject line
- File Aatachments, capturing information on
- File names
- File size
- Number of attachments
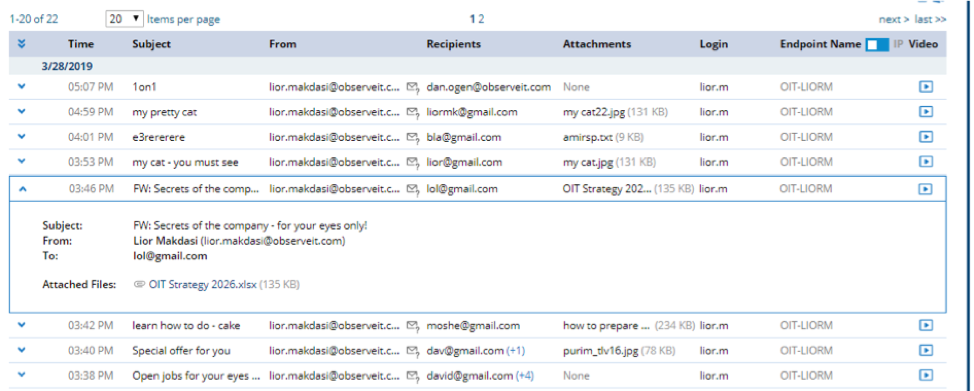
The rich metadata that we capture can be used to detect a wide variety of patterns of email data exfiltration. Some examples are:
- Sending and receiving sensitive data to and from unauthorized domains
- Unusually large file movement by users
- High-risk users exfiltrating sensitive data outside the organization
- Files downloaded or saved from corporate emails and exfiltrated through other channels
- Users downloading or saving files from known bad domains (e.g., phishing and malware originating domains)
Proofpoint provides the whole context of the user’s activity before and after the email exfiltration activity. Our Timeline view provides a chronological view of a user’s email actions, along with other user activity before and after the email event.
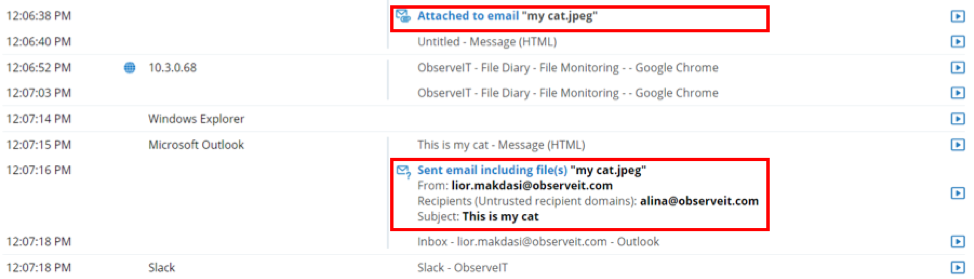
Email Diary showcases all email metadata in a dedicated view and email attachments are linked to the File Diary view.
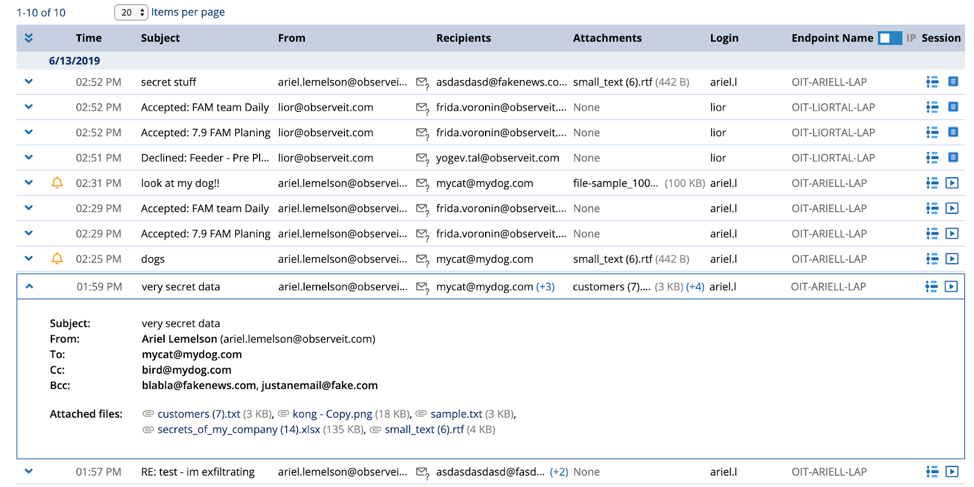
Each of these views indicates user actions that caused email alerts to be triggered. And it offers flexible searching and cross-referencing with the other diaries for easier investigations. These new features are for both Microsoft Outlook and Mac Mail clients.
Screenshot of the File Diary view. Emails filtered by sender or receiver.
Activity Replay for Selective Recording
Traditionally, incident investigations have been time-consuming. And even then, user attribution is very difficult. Recording user actions when they are engaged in high-risk activity is the clearest evidence of intent and action. This provides irrefutable proof of harmful intent or establishes the innocent nature of actions. Yet, it’s often untenable to record all activity all the time, as this can significantly drive up storage requirements (and costs) and doesn’t follow the latest regional privacy standards.
For these reasons, our Activity Replay feature gives you the ability to selectively capture screenshots just before and after a policy violation. This way, teams have access to replay user activity without the privacy concerns and overhead of a no-strings-attached, full session recording.
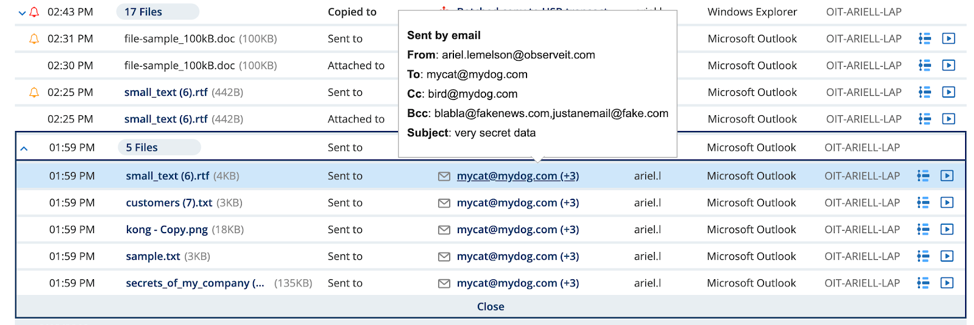
Here’s a visualization of how this works:
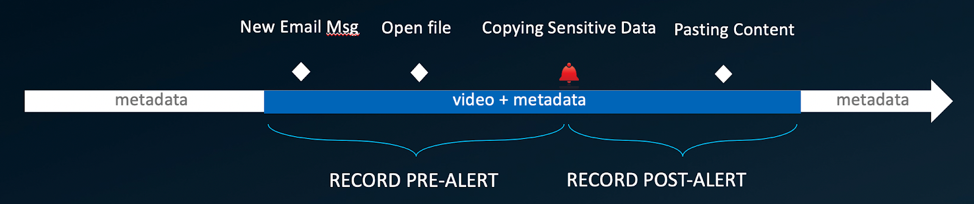 Activity Replay provides improved context before and after suspicious user and data activity. As you can see above, Proofpoint Insider Threat Management continually records metadata. But when an alert is triggered, the platform also records video from before, during and after the event.
Activity Replay provides improved context before and after suspicious user and data activity. As you can see above, Proofpoint Insider Threat Management continually records metadata. But when an alert is triggered, the platform also records video from before, during and after the event.
We also empower your teams with a flexible session recording policy that they can fine-tune to meet their exact requirements. This includes upholding specific privacy laws, maintaining internal corporate norms and reducing costs. We specifically enable organizations to exclude monitoring of any private employee activity (e.g., the use of a personal financial account or social media) should you so choose. With these features, organizations can save up to 80% in storage per day per agent (assuming average user and alert activity). This, in turn, can lead to significant cost savings.
Here’s a screenshot that shows how to create a new recording policy:
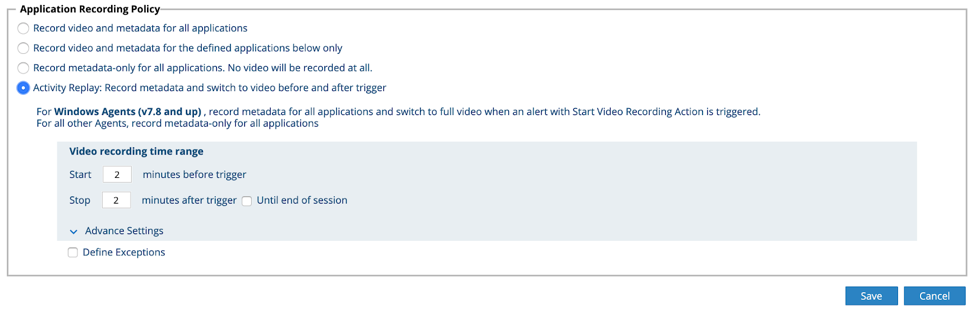
With this flexible recording policy, teams can make exceptions to the policy based on certain applications, websites or types of web category. Activity Replay can also be triggered alongside user education or blocking, so that you can not only gather the information you need for investigations and response, but also immediately neutralize risky user activities.
Note: This is currently a Windows-only feature.
Alert Tuning for Improved Detection
For security teams familiar with the problem of too many alerts, we provide you with tools to fine-tune all types of alerts from a single screen in eight easy steps. Alert Tuning can be used to clean up false positives from the past, reduce noise and make alerts more accurate for the future, as depicted below:
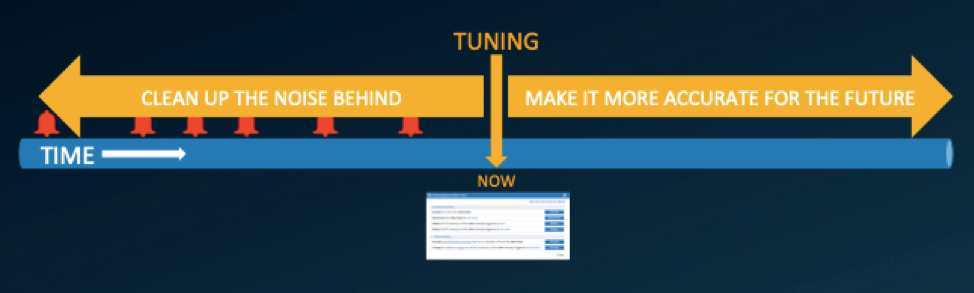 Your ecurity analysts are able to execute their tasks with more efficiency using a single alerts screen to fine-tune all of their insider threat alerts within Proofpoint Insider Threat Management.
Your ecurity analysts are able to execute their tasks with more efficiency using a single alerts screen to fine-tune all of their insider threat alerts within Proofpoint Insider Threat Management.
For future alerts, analysts can choose to:
- Exclude users
- Exclude active directory groups
- Deactivate
- Delete
For previous alerts, analysts can choose to:
- Delete
- Change status
These features enable Proofpoint users to leverage the power of the platform without being bogged down by extraneous alerts. This is one more step in the right direction when it comes to reducing alert fatigue for analysts.
Other Features and Benefits
In addition to the major updates above, Proofpoint Insider Threat Management includes:
Enhanced Mac support
- New Mac Endpoints group
- New Mac Recording Policy Type with Mac-related fields only
- Search by OS type (=Mac)
- Recapture only the window in focus
- Monitor Firefox and TOR browsers on Mac endpoints
File Activity Monitoring (FAM) Usability Improvements
- Faster investigations with improved usability in File Diary
- Batched events grouped
- File size information available
- Easier navigation
Insider Threat Library Updates
- Five new alert rules on email activity
- Only the top 60 valuable alert rules are active by default
Timestamp Display
- Switch timestamp display to make local time of user clearer
- Toggle activity timestamps between server or endpoint local time zones
- Switch is available in all diaries, alerts, search
- New Reports fields allow users to view timing in endpoint local time zone
You can find the full product update documentation here, should you require more details.
Less Noise, More Signal
When it comes to insider threat protection, less is often more. In other words, fewer and higher-fidelity alerts are often the key to catching threats quickly. We're excited to provide access to these email-based data exfiltration features, Activity Replay, Alert Tuning, and other new additions to the platform that will make defenders more productive and effective against insider threats.
Ready to try it for yourself?











