Proofpoint researchers originally discovered the CryptFIle2 ransomware in March [1]. At the time, it was spreading via exploit kits (EKs); however, beginning on August 3, 2016, we detected the first large-scale email campaign distributing CryptFIle2, allowing a degree of targeting not generally possible with EKs. This ongoing campaign appears to be targeting primarily state and local government agencies and educational institutions in the United States.
Email campaign
Between August 3 and August 9, Proofpoint detected a large CryptFIle2 ransomware email campaign. Bucking the more common trend of attaching malicious documents to emails, this campaign used embedded malicious URLs that led recipients to download Microsoft Word documents. If opened, these documents employ a social engineering lure to entice the user to enable malicious macros. The macros, in turn, download the final ransomware payload.
The messages in this campaign used a convincing email body and had a variety of Subject lines referencing American Airlines, adding an air of legitimacy to the lures. These subjects included:
- AmericanAirlines discount
- AmericanAirlines free 100$
- Bonus from AmericanAirlines
- Free fly with AmericanAirlines
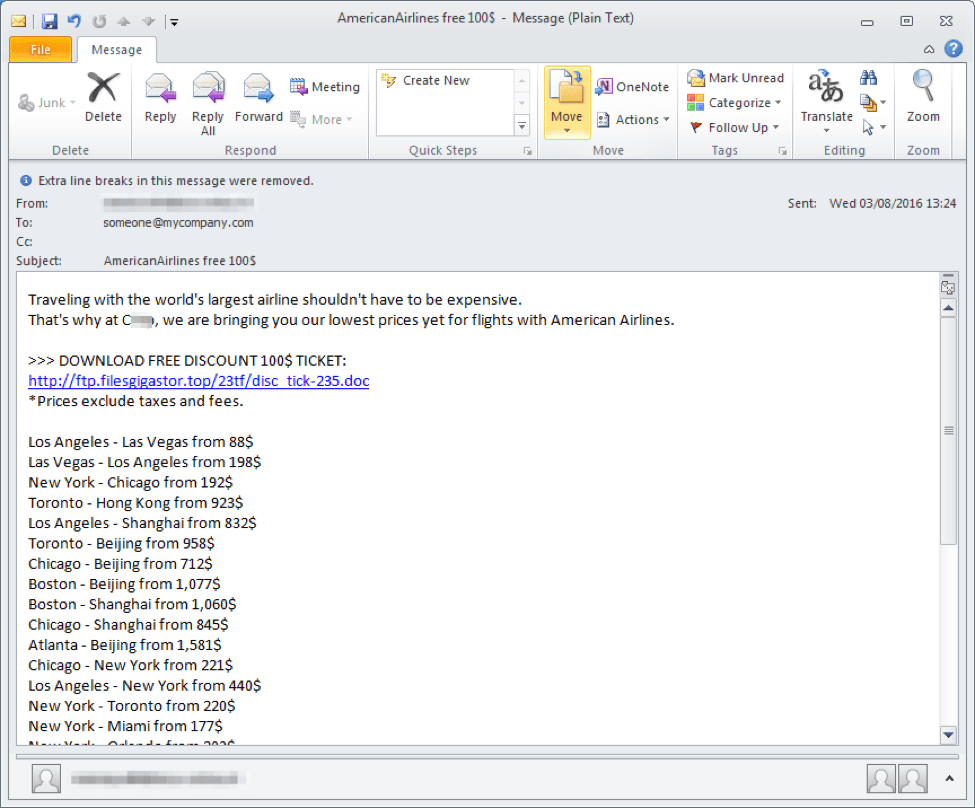
Figure 1: Email using a convincing lure and fraudulent branding to deliver the malicious URLs that eventually lead to ransomware
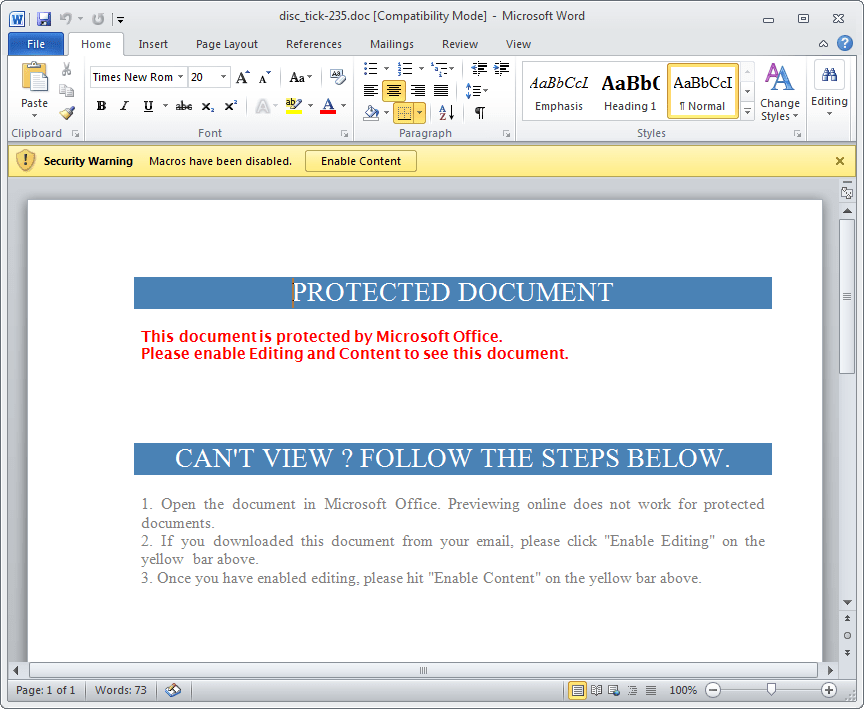
Figure 2: Document that uses macros and social engineering to download ransomware
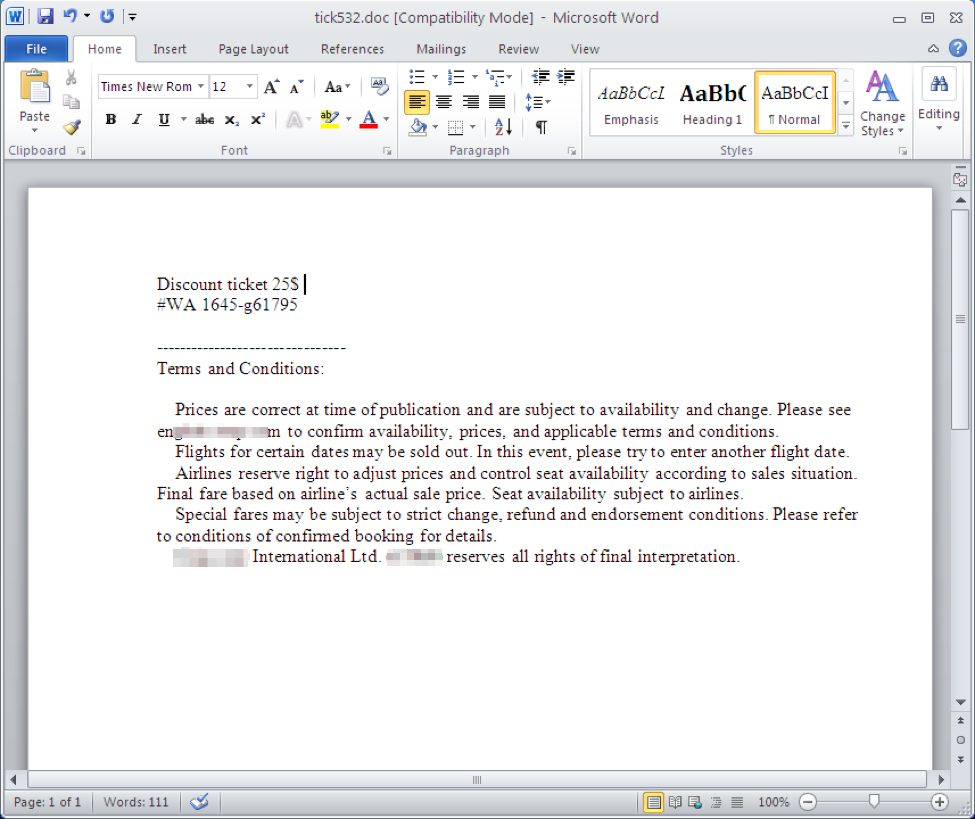
Figure 3: After enabling macros, a customized lure appears with an airline ticket offer similar to that in the original email message; this lure references a legitimate travel site (obscured here)
Targeting and Risk
Proofpoint researchers first discovered CryptFIle2 in March 2016 [1] spreading via Nuclear and Neutrino exploit kits. The current campaign is the first large email-borne campaign observed for the ransomware. This campaign began with hundreds of thousands of messages on August 3, and continued with a long tail of only several thousand messages each following day.
This campaign is primarily aimed at state and local government agencies, followed by K-12 education. Messages came through in smaller numbers for healthcare, post-secondary education, and several other verticals.
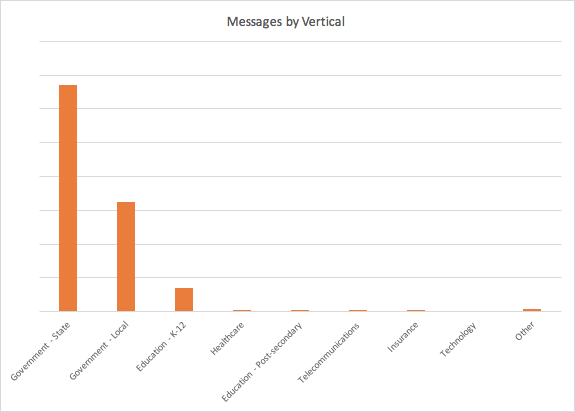
Figure 4: Vertical targeting by indexed message volume
Analysis
Compared to our last analysis, the files dropped on the file system to alert the victim that they are infected have changed slightly:
- HELP_DECRYPT_YOUR_FILES.TXT
- HELP_DECRYPT_YOUR_FILES.HTML
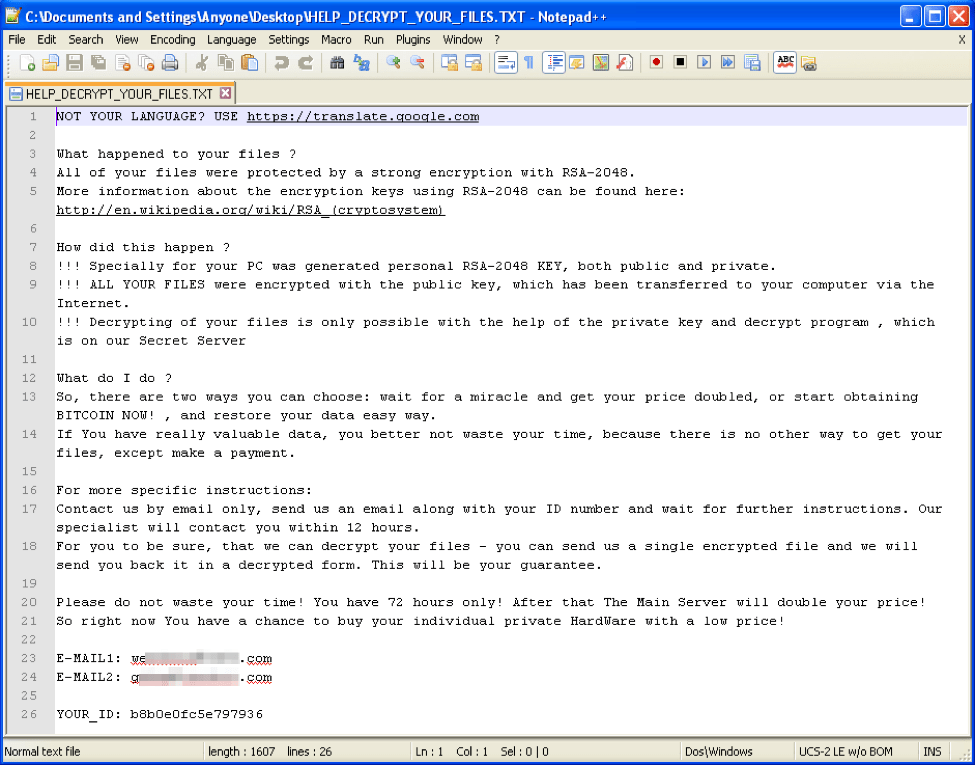
Figure 5: New CryptFile2 text file ransom note
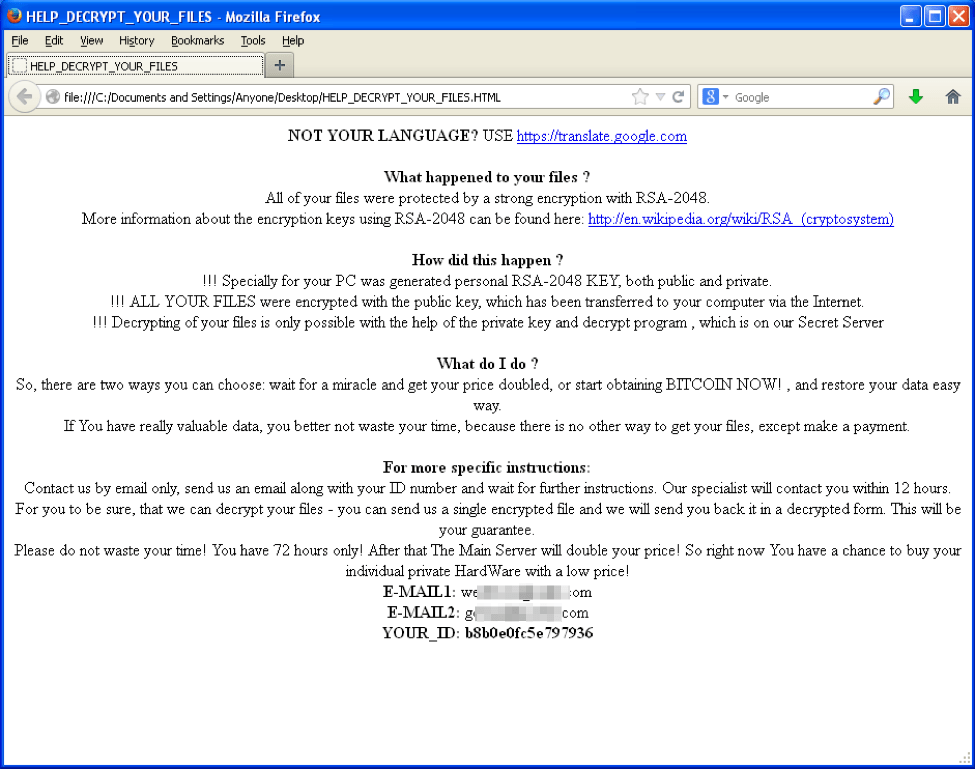
Figure 6: New CryptFile2 HTML file ransom note
However the encrypted files are still renamed to contain the original file name, followed by the “.id_[personalid]_[ransomemail].scl” extension. In this new file name, the “personalid” is a 16-character string consisting of lower-case letters and numbers. The “ransomemail” is the email with which the infected user is supposed to communicate to get their files decrypted. Examples of renamed files appear below:
- user.bmp.id_b8b0e0fc5e797936_email_go[redacted]it.com_.scl
- tulips.jpg.id_b8b0e0fc5e797936_email_go[redacted]it.com_.scl
The network communication protocol also remains the same and can be detected with ET signature 2022683 “ET TROJAN Win32/CryptFile2 Ransomware Checkin”. In addition to the standard command and control (C&C) request, the malware first requests a “default.jpg” file from the server, to which the server replied with “default” in our case. This functionality may allow threat actors to customize the skin of ransom message.
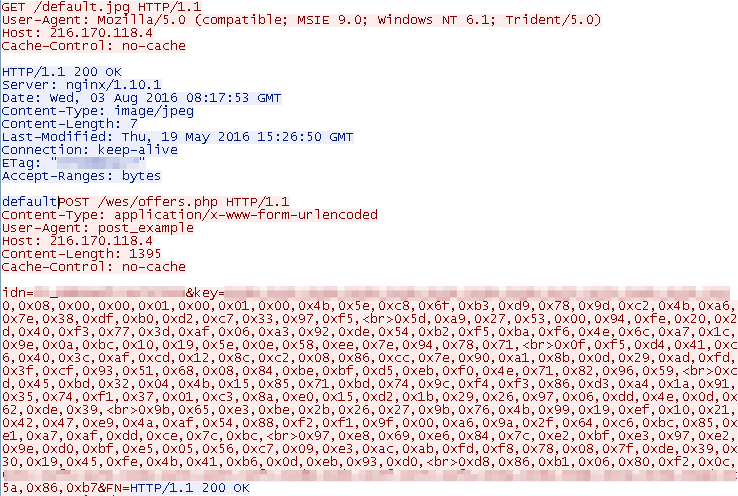
Figure 7: Network traffic generated by ransomware
As mentioned in our previous analysis, it is likely that this ransomware is another one in the series of CrypBoss clones, which already include HydraCrypt and UmbreCrypt.
Conclusion
The number of ransomware instances in the wild continues to increase, with new variants appearing regularly. As this campaign and others like it demonstrate, sheer numbers of variants are not the only risk for users. Rather, shifting vectors and changing delivery methods require organizations to employ comprehensive protection solutions across both gateways and endpoints to avoid infection. In particular, the targeting in this campaign made possible through email distribution, brings increased risks to public sector organizations that may be less equipped to detect and mitigate these kinds of threats. Organizations that do not update defenses to detect and stop this latest generation of ransomware threats may find themselves in the difficult position of having to pay the ransom, which carries its own set of risks.
References
Indicators of Compromise (IOC’s)
| IOC | IOC Type | Description |
| hxxp://www.filesgigastor[.]top/cvd/ticket_454.doc | URL | URL leading to Macro document |
| hxxp://pub.filesgigastor[.]top/ghef/tick532.doc | URL | URL leading to Macro document |
| hxxp://www.dataupllinks[.]top/skfn/tick-09w1.doc | URL | URL leading to Macro document |
| hxxp://ftp.filesgigastor[.]top/23tf/disc_tick-235.doc | URL | URL leading to Macro document |
| hxxp://pub.dataupllinks[.]top/gdl/tick974.doc | URL | URL leading to Macro document |
| a5e14eecf6beb956732790b05df001ce4fe0f001022f75dd1952d529d2eb9c11 | SHA256 | tick532.doc |
| hxxp://216.170.126[.]3/wfil/file.exe | URL | CryptFIle2 payload location |
| hxxp://216.170.118[.]4/default.jpg | URL | CryptFIle2 C2 |
| hxxp://216.170.118[.]4/wes/offers.php | URL | CryptFIle2 C2 |
Select ET Signatures that would fire on such traffic:
2022683 || ET TROJAN Win32/CryptFile2 Ransomware Checkin
2812515 || ETPRO USER_AGENTS Suspicious User-Agent (post_example)











