Cybercriminals are evolving their strategies to target your people, rather than your infrastructure—and that trend extends to business email compromise (BEC) attacks, which recently increased by 45%. Often highly-targeted, BEC attacks have cost organizations more than five billion dollars and aim to trick people into sending money or sensitive information on the fraudster’s behalf. These low volume email-based threats constantly shift in approach to successfully reach their mark – making them difficult to discern between normal business communications.
Below we have highlighted the top four “personalities” attackers assume to spur action including the authoritarian, the conversationalist, the fake chain of emails, and the false approver. BEC attack techniques span domain-spoofing, display name spoofing, lookalike domain spoofing, and partner spoofing. Targeted information and action also vary from wire transfer fraud to W-2 and intellectual property theft to brand defamation, and so on.
The Authoritarian
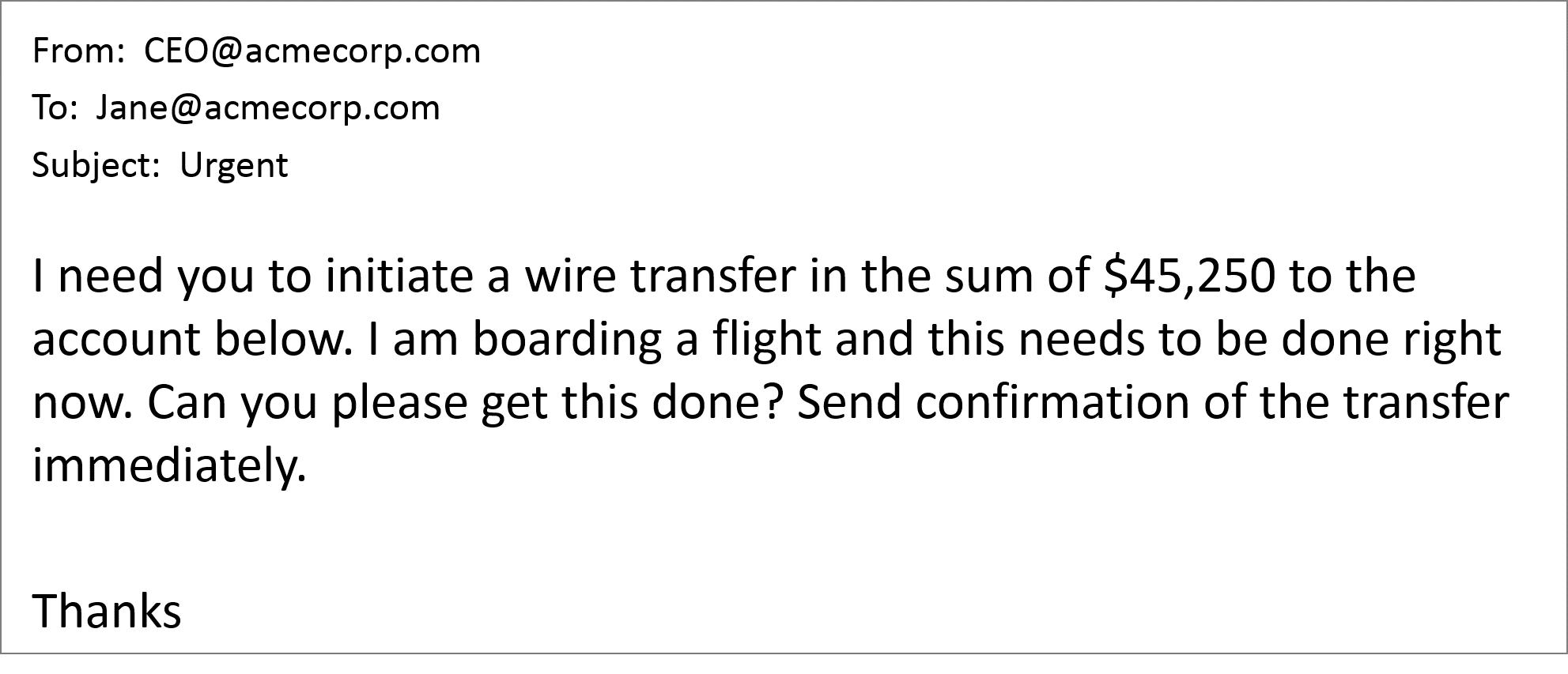
The authoritarian attacker may impersonate a high-ranking executive or business partner to target someone lower in the organizational hierarchy, such as accounts payable. This tactic is intended to intimidate the victim into sending money or data immediately and thwart the idea of asking any questions. The authoritarian will avoid dialogue by researching when the person being impersonated will be traveling, speaking, in meetings, etc. They may explicitly state, “I’m boarding a flight and won’t be able to respond.” BEC attacks using the authoritarian tactic can be finely tuned to be more credible from a timing and content perspective, tricking an unsuspecting employee into hastily making a costly mistake.
The Conversationalist
In contrast to the authoritarian, the conversationalist technique looks to earn the trust of the victim by building a dialogue. The fraudster will perhaps open with something seemingly innocuous such as, “are you at your desk” or “are you in the office?” Then, once the victim responds and has engaged in conversation, the attacker will request for a wire transfer or sensitive information to be sent. They will also send follow-up communications or request a confirmation to ensure the crime has been committed and to keep the victim in the dark.

The Fake Chain of Emails
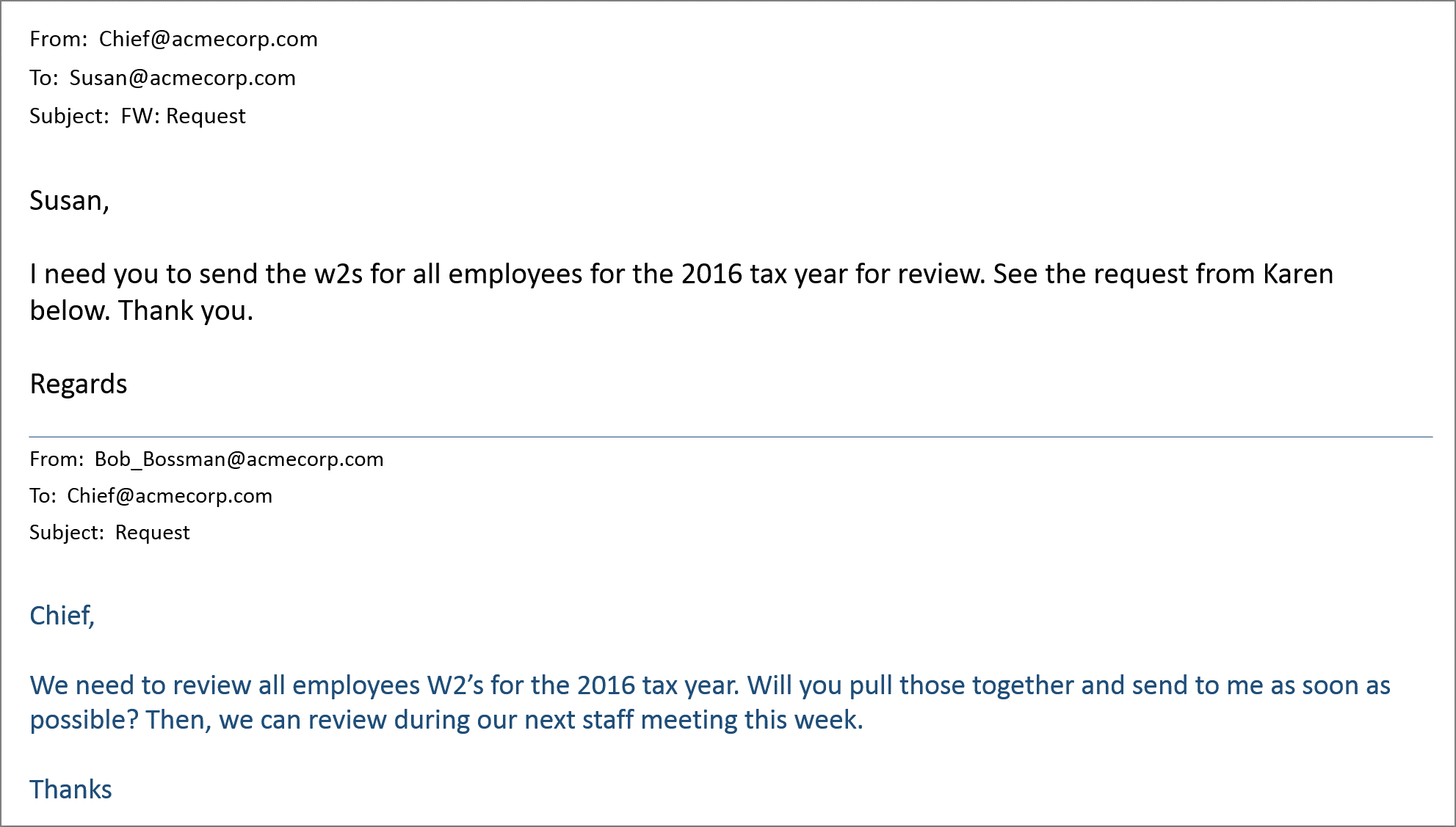
Some BEC criminals will also use a fake chain of emails to trick a victim by adding the illusion of credibility. The fraudster can point to a faux history with realistic interactions for a request to send on their behalf. For example, “per our CFO’s instructions below, please transfer the money to this account…” This scam elicits an emotional response and motivates the victim to follow through.
The False Approver
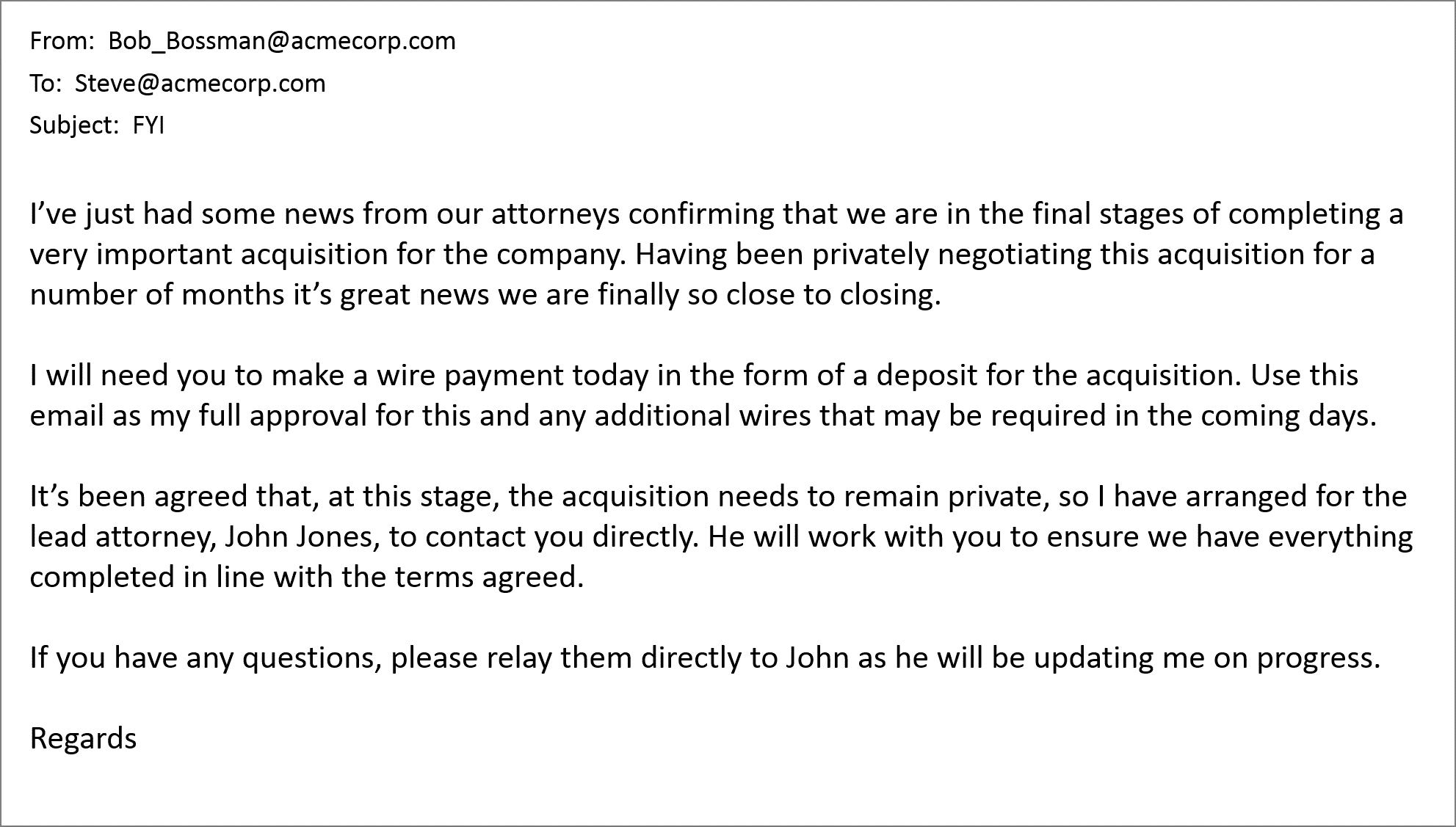
Similar to the fake chain of emails tactic, the false approver seeks to add trustworthiness to their con. This BEC tactic introduces additional email threads or even additional communication channels, such as a telephone call for believability. For example, the malicious message might say, “you will hear from our lawyer with payment details” and the victim could then receive a follow-up telephone call from that “lawyer.” This perceived credibility makes it even more difficult to decipher between a business email compromise or legitimate message - and much harder for your security/messaging teams to stop.
Stop These BEC Actors in Their Tracks
With ever-evolving techniques and the constant shift in approach that BEC attackers use to trick people into delivering money and data outside of the organization, you need a multi-pronged approach to put a stop to these threats. For more information on how to combat BEC attacks, check out our post on Imposter Email Threats and download our infographic to learn how to stop and identify.
Our survival guide is also available here: https://www.proofpoint.com/us/resources/white-papers/bec-survival-guide











