The growing sophistication of cyber threats and the fact that working remotely increases attack surfaces means that legacy solutions designed for an office-based corporate environment are no longer effective. Your people are still the target of attackers, and securing a remote workforce requires a strong layered defense approach.
Proofpoint and CrowdStrike have now been partnering for over a year which has brought tremendous value to customers with the integrations offered today.
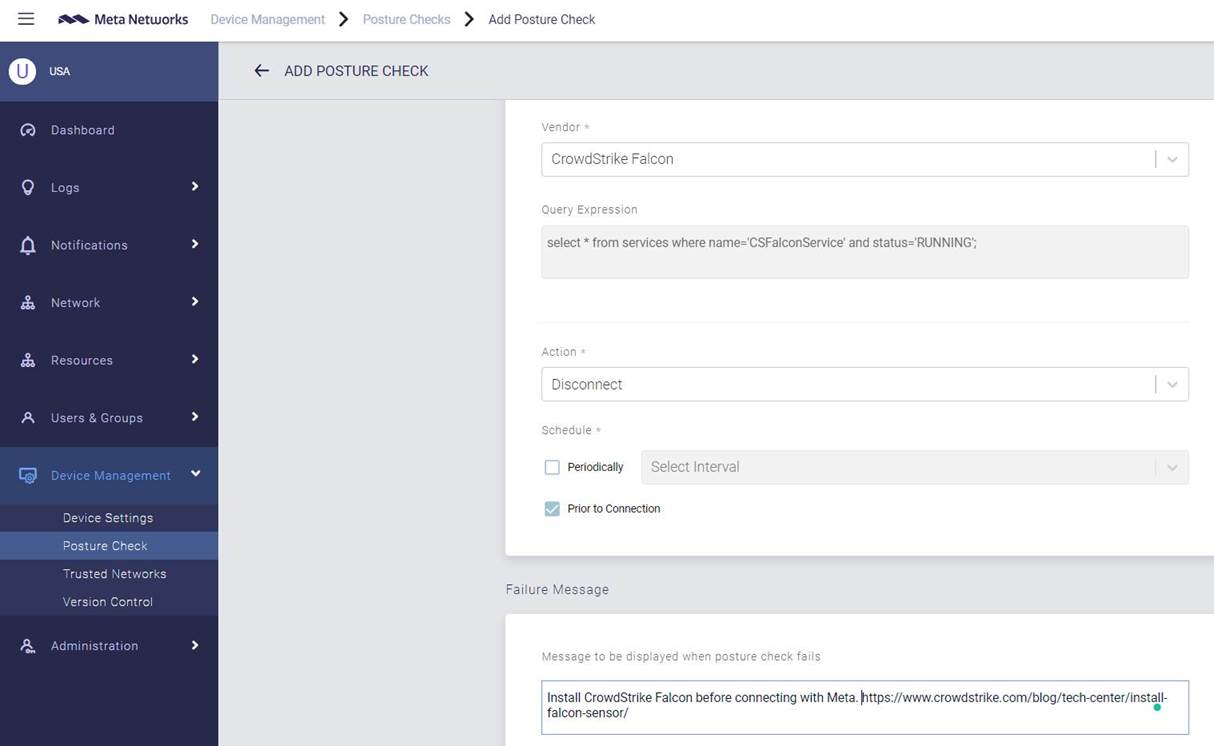
Posture Checking for Enhanced Zero Trust Security
In today’s work environment and as more customers have employees working remotely, it’s critical to ensure they have secure access to company resources. Proofpoint Meta provides for Zero Trust secure access to all company resources regardless of the device or network they connect from. It is fully cloud-based with a global network of PoP’s for seamless and easy user access.
Proofpoint and CrowdStrike are both focused on ensuring the highest level of security for users. We are excited to announce the latest integration with CrowdStrike where we can use Posture Checking for enhanced zero trust security. This seamless integration allows the Meta agent to check and see if the CrowdStrike agent has been properly installed. If not, the Meta agent can carry out several actions such as disconnecting the user from the network resource. In addition, administrators can easily set a message letting the user know why they have failed the posture check. This helps strengthen our Zero Trust security approach by ensuring the highest level of compliance for users before being able to access company resources.
Multi-layered Protection Through Threat Intelligence Sharing
As your people remain the top target for attackers, it is imperative to have a multi-layered defense to stop targeted attacks. Our existing integration that leverages Proofpoint TAP and CrowdStrike provides both pre-delivery and post-delivery protection through threat intelligence sharing.
Pre-delivery Email Protection: When an email that contains a file is sent to a customer, Proofpoint TAP will begin its sandbox analysis to determine if it is malicious. At the same time, Proofpoint TAP will query the CrowdStrike Intelligence for file reputation. If CrowdStrike knows the file to be malicious, it will inform Proofpoint TAP. From there, the message and file will be condemned and blocked from ever reaching the end-user. Hundreds of our joint customers are benefiting from this shared intelligence by leveraging two best-of-breed solutions and protecting over 3 million end-users.
Post-delivery Protection: For multi-layered protection, Proofpoint TAP shares threat information with the CrowdStrike Falcon platform. This provides more enhanced security for you to protect your people, both through email and the device itself. When TAP detects that a malicious file has been delivered via email, it can alert Proofpoint Threat Response Auto-Pull to quarantine any of those delivered messages as well as query CrowdStrike Falcon X, the threat intelligence module, to determine if it’s known. If the malicious content is known, no action is taken because the device will be protected. If it’s unknown, the malicious hash information is added to the CrowdStrike list of custom indicators of compromise (IOCs). And an alert is created if the malicious content tries to execute on the device.
In the last three months alone, Proofpoint TAP has added over 4,800 unique file hashes to CrowdStrike’s Custom loC lists for our joint customers. This shared intelligence has helped organizations to proactively defend against any similar future attacks seen across endpoints in their organization.
All these integrations are simple to implement and can be enabled at no-cost for joint Proofpoint and CrowdStrike customers.
To learn more, visit the webpage here.











