Security teams have been playing catch-up since the start of the COVID-19 pandemic and applying new security controls to their global, remote workforce. Meanwhile, their time, headcount and tools haven’t adapted at the same rate to address the new challenges their business faces. Also, many chief information security officers (CISOs) have growing security concerns around business email compromise (BEC), cloud account compromise, ransomware, and insider threats.
Nearly two-thirds (64%) of CISOs believe their organization will suffer a material cyber attack in the next year, with 20% of these security executives rating that risk as very high. And more than half (57%) of CISOs reported that the expectations placed on their role are “excessive.” These findings are just some of the insights gained from a recent Proofpoint survey of 1,400 global security leaders, which we summarize in our 2021 Voice of the CISO Report.
Our survey also found that 66% of all CISOs are concerned about their ability to cope with attacks and the reduced visibility their teams have into user activity. They’re also facing growing pressure to deliver results and protect their organizations from a breach, while facing resource constraints.
There’s a direct correlation between budget, resources and risk reduction — and not all organizations have added margin in these areas. Security teams must figure out how to reduce risk with existing resources, while advocating for greater budget and spend for security projects by justifying their prior success in mitigating risks.
CISOs’ top concerns are all people-centric—and people are the primary source of risk
While all attacks are of utmost concern to security teams, the Voice of the CISO Report reflects that the biggest perceived threats in the next year are BEC (34%), cloud account compromise (33%), insider threats (31%), and ransomware (27%).
What do these threats have in common? They’re all focused on people, or they require human interaction to activate.
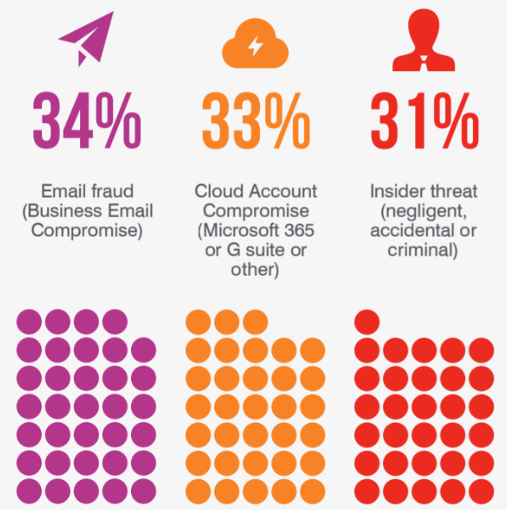
Figure 1. Shaded circles represent the percentage of CISOs concerned with the three biggest perceived threats described in the 2021 Voice of the CISO Report
While organizations can deploy secure email gateways, virtual private network (VPN) access, and multi-factor authentication for cloud accounts, security teams can’t stop 100% of attacks because malicious actors are constantly adapting their social engineering tactics to exploit human vulnerabilities. And remote work only adds to the challenge of keeping the organization and its critical assets secure.
With over 90% of breaches involving human interaction, security teams must think outside the box and consider how to implement solutions with a risk-based, people-centric approach to keep their organizations safe.

Figure 2. Quote from Krishnan Chellakarai, CISO, Gilead
Using security awareness training in a people-centric context to uncover sources of risk
Over half (58%) of the CISOs Proofpoint surveyed for our 2021 report said they believe employees understand their role in protecting against cyber threats – yet users also pose the biggest risk. The challenge lies in the fact that human error is an organization’s biggest liability, and while end users might intend to avoid threats, they might lack the appropriate skills and preparation to do so.
A common approach organizations take to counter that challenge is to deploy security awareness training. While this is a great step toward mitigating risk by changing user behavior, protecting users requires a combination of people-centric security awareness training and an understanding of the additional variables that influence risk.
For example, users can be vulnerable to clicking on attachments or URLs they believe come from someone they trust—when, in fact, they could be falling for email account compromise (EAC). They can also have personal and financial information or systems privileges based on their job function, which means if they’re compromised, the impact on the organization is that much greater. These data points can then be accounted for when deciding which security awareness training modules to administer to certain users.
Because risk has different origins, Proofpoint defines risk as the intersection between vulnerability, attack and privilege. So, to reduce risk, security teams need to complement their security awareness training program with robust technical controls to account for people-centric risks.
A people-centric, risk-based cybersecurity strategy can help you optimize resources
Nexus People Risk Explorer from Proofpoint helps CISOs and security teams mitigate people risk more effectively by helping them prioritize controls and scope projects based on risk severity associated with users, departments or custom groups. By segmenting users based on similar risk profiles, Proofpoint identifies the most critical users who, if compromised, could put the broader organization at significant risk.
Not only does Proofpoint help security teams identify those users who present the highest risk, but we also provide granular details surrounding the vulnerabilities and privileges that might make them prime targets for attackers. By better understanding the factors contributing to people risk, security teams can make informed decisions on which security projects to deploy to selected groups of users and which projects to prioritize.
Threats don’t always originate externally. Users can be negligent and fall for an attack that leads to the loss of company data due to their click-happy nature and access to sensitive data. This is especially relevant with multi-stage ransomware campaigns requiring several clicks to activate – security teams might not detect a threat so users must know how to identify malicious content and avoid falling for them. Nexus People Risk Explorer can surface these behaviors and privileges ahead of time to help security teams proactively identify potential sources of future compromise. Using control recommendations in Nexus People Risk Explorer, security teams can administer additional security awareness training modules or limit users’ access to certain systems to reduce their risk score.
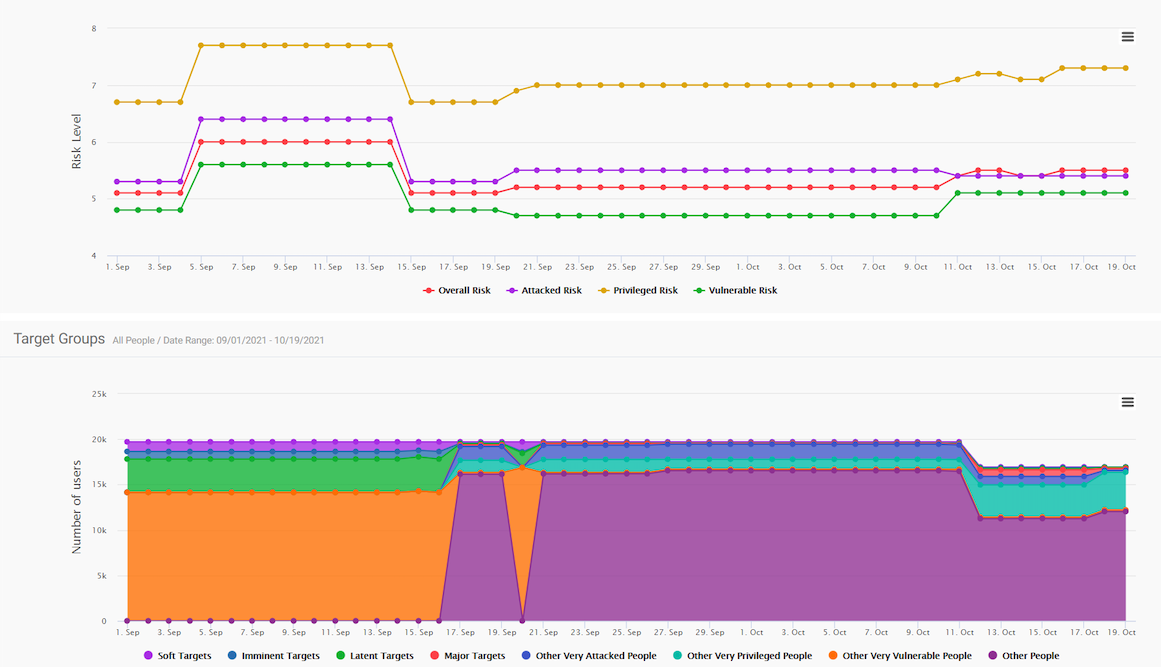
Figure 3. An example of the trending visualizations provided by the Nexus People Risk Explorer dashboard
Proofpoint recommends security controls and provides the associated risk-reduction scores, which helps security teams identify and apply the controls with the most impact on risk mitigation. Deploying the right security controls and looking at risk trends over time equips security teams with actionable data and lets them make appropriate changes to security controls. Better yet, these visualizations in Nexus People Risk Explorer are easy to understand and can be downloaded for use in comprehensive reports shared with executives and the board.
Here’s an example of how training plus controls can enhance security: A healthcare organization that was previously using another vendor’s security awareness training solution with limited engagement and low impact switched to Proofpoint Security Awareness Training. Before their campaign was over, their security teams used the trending capabilities in Nexus People Risk Explorer to discover a reduction in almost 50% of their vulnerability risk scores. This is prime data they can use to justify future security projects with their executives.
Get started by gaining visibility into and an understanding of people-centric risk
Keeping organizations safe is the top priority for CISOs and security teams. This is a challenging, time-consuming task, with attackers constantly adapting and taking advantage of people vulnerabilities to accelerate their nefarious activities.
Security teams have a never-ending list of projects to tackle and limited time and resources. But Proofpoint can provide them with a unique perspective on prioritizing security controls and projects, so they can maximize risk reduction by surfacing vulnerabilities and privileges that attackers could exploit. We equip CISOs with the actionable data insights they need to make more informed decisions on their security spend and project priorities.
Read our Global Resident CISO’s take on the top three CISO concerns in 2021. Also, refer to the Voice of the CISO Report to learn about the old and new pressures your security teams should be aware of to stay ahead of cyber attackers.
To learn how Nexus People Risk Explorer can positively impact your security journey, read the Nexus data sheet.











