The traditional security perimeter is no longer fit for purpose in a “work from anywhere” and cloud-first world. Today, most businesses are now defending a disparate attack surface that extends across locations, accounts and devices. When bad actors want to breach this vast network, all they need to compromise is one individual—not the defenses of an entire enterprise.
That’s why identity is the new attack surface—and your new perimeter.
In recent years, businesses have been investing heavily in tools like Privileged Access Management (PAM) and multi-factor authentication (MFA) to help combat these attacks. Yet, despite widespread adoption of these tools, our research shows that exploitable identity vulnerabilities are still present in one in six enterprise endpoints.
How are cyber criminals attacking identity?
Cyber criminals can bypass standard perimeter defenses with minimal effort or technical know-how by targeting unmanaged and misconfigured identities. Service accounts, local and shadow admins and cached credentials often slip through the net of privilege and password security tools.
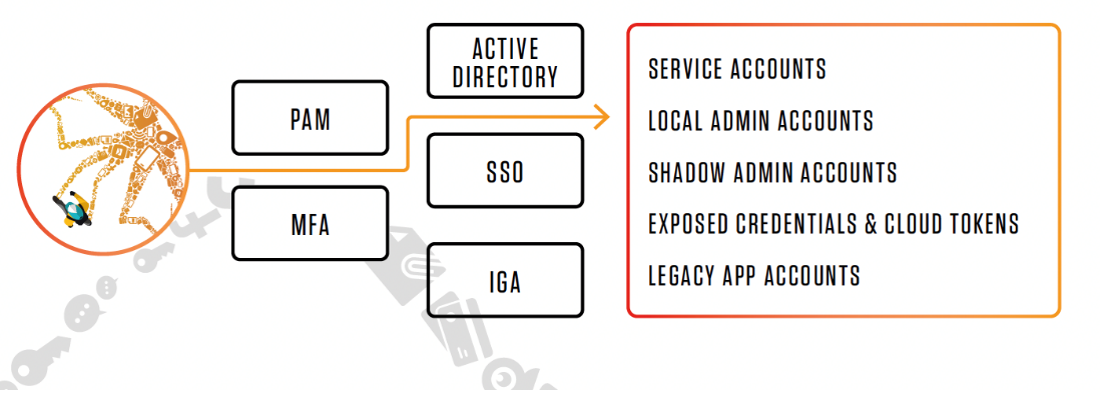
An overview of how cyber criminals attack identity.
Research from the Identity Defined Security Alliance found that 84% of organizations experienced an identity-related breach in the past year. And it’s easy to see why bad actors succeed with this attack strategy when you consider research from Proofpoint that found 87% of shadow admins aren’t enrolled in a PAM solution. On top of that, we learned that 40% of shadow admins can be exploited in just one step.

Findings from the 2022 Analyzing Identity Risks (AIR) Research Report from Proofpoint.
Once a threat actor exploits an identity vulnerability, they can move laterally through systems and networks to do even more damage. They can:
- Amass intelligence
- Distribute malicious payloads
- Exfiltrate data
The longer an attacker is free to move around, the more time and opportunity there is for them to traverse through identities. They can engage in privilege escalation, for example, and abuse Active Directory and cloud environments. And the consequences for companies can be dire.
Taking a new approach to countering identity threats
Proofpoint recognized the need for a new set of tools that is tailored to meet the challenge of identity threats. That was a key reason we recently acquired Illusive—a market leader in Identity Threat Detection and Response (ITDR).
Our Proofpoint Identity Threat Defense platform detects, remedies and defends identity vulnerabilities. This solution protects the imperative, middle section of the attack chain. It features the Proofpoint Spotlight™ and Proofpoint Shadow™ technologies, which help enterprises to:
- Detect and respond to identity threats
- Stop privilege escalation
- Prevent lateral network movement
Spotlight and Shadow: a closer look
Spotlight delivers unparalleled visibility into vulnerable identities by scanning:
- Directory structures
- PAM solutions
- Endpoint servers
- Services
It reveals the gaps between what your identity security policies are supposed to do and the reality of your environment. Learn more about Proofpoint Spotlight here.
Shadow is undefeated in over 150 red team exercises. It allows you to detect threats faster by identifying threats based on when an attacker interacts with deceptions, rather than probabilistic controls that are based on threat signatures or behaviours. Learn more about Proofpoint Shadow here.
Protect the new attack surface, break the attack chain
The term “people-centric” describes the modern threat landscape. It also describes the style of defence that’s required to meet the challenges this landscape presents. Bad actors use identity to further their aims, whether that’s to steal data or deploy ransomware. And as they go about doing this, they follow a pattern—an “attack chain.”
Threat actors start by targeting your people through attacks like credential phishing emails and by landing malware. Once they compromise an account—an identity—they’ve won. They’re inside your environment using that identity to move laterally and achieve their goals.
Proofpoint acquired Illusive to enhance our market-leading threat and information protection platforms. The added proactive identity risk discovery and remediation as well as a robust post-breach defence capability.
Identity Threat Defense is a unified solution that extends protection across the entire attack chain. It gives companies unprecedented insights into their privileged access attack surface. And it helps security teams to better protect those at the most risk of an attack.
Get your free copy of New Perimeters
To find out more about how Proofpoint Identity Threat Defense can help you to break the attack chain, see New Perimeters—Identity Is the New Attack Surface.











