Email is a critical part of your business operations and comes in many forms. Transactional emails are the focus of this blog post—including what they are, where they come from, why they’re so important and the best practices you should consider applying to help increase deliverability and customer satisfaction.
What are transactional emails?
When you place an order online and get an automated email confirming your order, that is an example of a transactional email. Other examples of transactional emails include invoices, appointment reminders, shipping notifications and password reset messages.
Transactional emails are one-to-one messages that typically contain high-value content, meaning they contain important information related to transactions a user is involved with.
Where do they come from?
There are three primary sources of transactional emails
- Internal on-premises applications
- Internal cloud-hosted applications
- Third-party software-as-a-service (SaaS) partners sending email on your domains’ behalf
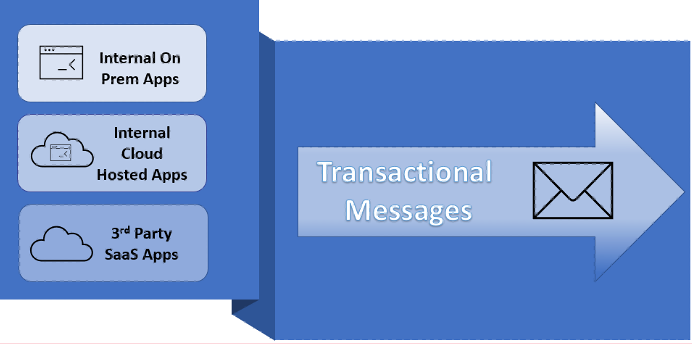
Figure 1. Three primary sources of transactional emails.
Internal applications provide automation and can be tremendous time- and cost-savers. Many legacy applications were deployed on-premises, but increasingly, companies are taking advantage of web applications and cloud hosting with platform-as-a-service (PaaS) tools such as Microsoft Azure.
A growing number of transactional messages are sent on a company’s behalf and come from third-party SaaS applications such as Salesforce, ServiceNow and Workday. Negative experiences from these applications can also impact a brand’s reputation. Adding third-party SaaS apps that use shared sending IPs into your SPF record introduces another layer of risk.
If an actor were to compromise an email service provider that leverages a shared IP, and that IP Address is in your SPF record, they could spoof your domain and send malicious emails that pass authentication.
Why are transactional emails so important?
Using the examples of transactional emails above, what would be your satisfaction level if you placed an order for something and received no confirmation email? Most likely, you would think the order wasn’t processed correctly—or, worse, that the company you just gave purchasing information to is fraudulent.
Delivery of transactional emails can greatly impact a customer’s overall satisfaction as well as a company’s brand reputation. When these emails are delivered properly, they can be an asset that builds trust and loyalty. When they’re not, they can become a liability.
Transactional emails aren’t user or marketing emails
Transactional emails are not one-to-many messages, like marketing emails. Marketing emails are a separate category and a topic for another day.
The takeaway here is that user emails, transactional emails and marketing emails all have very different purposes and characteristics, and each has its own best practices.
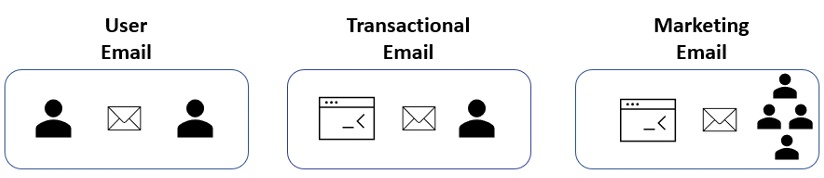
Figure 2. High-level overview of different email types: user email, transactional email and marketing email.
Best and worst practices for transactional email
Before we get to the “best practice” advice for transactional emails, I want to start with a “worst practice”. That’s mixing transactional emails with user-generated emails.
Transactional emails can occur in very high volumes and therefore could have a significant impact on overall sending performance. But more importantly, if any of the apps sending transactional messages were to cause your sending IP addresses to be blocklisted, it could compromise the deliverability of user email and bring business operations to a grinding halt.
Outbound transactional email, when managed correctly, can provide value not only to the messaging team for deliverability but also the security team, infrastructure team and app developers.
The key to success is having a separate but equally protected environment for sending transactional emails.
Recommended environment for transactional emails
Now, here’s a closer look at some best practices for managing transactional emails:
Centralised visibility and control—You want to have centralised visibility and control over both internal apps as well as third parties sending on your behalf. Sources should be approved and validated, and it’s highly recommended that you use a secure connection, such as SMTP authentication, between sources and your sending environment.
Allowing a very limited set of sending IP addresses in your SPF record will reduce the risk of others in a shared sending environment being able to impersonate your domains. Sending traffic from dedicated IP addresses reduces this risk even further.
Message scanning—Each message sent reflects on your company. Scanning messages for spam or viruses helps ensure only clean messages are sent. Having the ability to apply data loss prevention (DLP) rules or encryption are some advanced features to also consider, especially if you’re dealing with financial, healthcare or other personally identifiable information (PII).
Domain Keys Identified Mail (DKIM) signing—It’s a best practice to DKIM sign all outbound messages. If you’re using a third-party SaaS partner that lacks this capability, it’s important that your sending environment can intake these messages and add the DKIM signing before sending. DKIM and DMARC are critical components for brand reputation protection.
Resulting benefits
Having a separate and equally protected sending environment for transactional emails has multiple benefits, to multiple teams. For example, if you’re part of the:
- Messaging team—Deliverability is no longer put at risk by something completely outside your control, and application traffic won’t impact the reputation of your sending IPs. If an issue occurs with an app, it won’t affect user-generated or marketing emails. Also, brand reputation is isolated from third-party partners sending from your domains.
- Security team—You can reduce the risk associated with having an overly permissive SPF record and have centralised control to turn off applications, including third-party apps sending on your behalf, if they are suspect. This is especially important for third-party SaaS providers that use shared IP addresses and are ripe for abuse.
- Infrastructure team—Benefit from a reduced on-premises footprint by leveraging a cloud-based sending environment for transactional emails and providing a simple solution for app developers in your organisation who need email-sending capabilities.
Need help creating your transactional email sending environment?
Proofpoint is an industry leader when it comes to email and email security and has the resources, technology and skills to help you separate and protect your transactional emails. And the process is quicker and more cost-effective than you might have imagined. With our cloud-based Secure Email Relay technology, you’ll be up and running in no time.
Learn more about Proofpoint Secure Email Relay today!











