This blog is the first in a series where we explore attack path management. We’ll explain what you need to know and give you the tools you need to help you better protect the middle of the attack chain.
A big reason that successful cyberattacks are on the rise is that threat actors are shifting their tactics to identity-based attacks. Last year, 84% of businesses fell victim to an identity-related breach.
When attackers land on a host, it is rarely their end target. Instead, they look to escalate privilege and move laterally across an environment. Their next step is to exploit more privileged credentials, and they often do this by using shadow admin vulnerabilities.
It can be a challenge to stop them. To do so, you need to quickly discover, prioritize and remediate identity vulnerabilities. But first, you need to know what you’re up against.
In this blog post, we explore the multitude of identity vulnerability challenges, and we explain why an attack path management (APM) view is so important. We also specify which identity-centric attack vectors are likely to exist in your environment.
Key terms
Before we dive into this topic further, let’s define some key terms that are central to this area of security:
- Attack path management. This refers to the process of identifying, analyzing, understanding and remediating attack paths within a business. Identities and other system resources are typically spread across multiple on-premises and cloud identity stores. These include Microsoft Active Directory (AD), Entra ID (formerly Azure AD), AWS and Okta.
- Attack path. Threat actors follow a sequence of steps as they compromise security, which is called an attack path. The typical end result is the compromise of a tier-zero asset (TZA)—or what is generally referred to as a bad breach.
- TZAs. Tier-zero assets are often referred to as the “crown jewels.” They are a company’s most critical and sensitive assets. They can include systems, data or other resources (databases, web gateways) that are essential to its operation, reputation and overall resilience. In certain scenarios, AD domain controllers or authentication systems can be considered TZAs given the broad scope of damage that can arise with their breach.
The risks of TZA compromise
Compromising a tier-zero asset is a high-value objective for attackers because it allows them to achieve their financial or other malicious goals. Here are some common objectives:
Data exfiltration
TZAs may store or have access to critical and sensitive data or intellectual property. Or they might be critical system resources that, if compromised, could result in a service outage. Attackers aim to steal this information for financial gain, espionage or extortion. Data exfiltration clearly impacts the confidentiality part of the CIA triad.
Data manipulation
Attackers may alter or manipulate data within TZAs to achieve their goals. For instance, they could modify user account settings, insert malicious code or encrypt data as a step toward operational disruption. Data manipulation impacts the integrity part of the CIA triad.
Denial of service (DoS) or disruption
Attackers may use compromised tier-zero assets to launch DoS attacks against critical operational services in an enterprise. This can disrupt services and cause operational or financial harm to the business. This exposure category is about impacting the availability portion of the CIA triad.
Ransomware
Attackers may use their control over TZAs to deploy ransomware across a network. By encrypting critical systems and data, they can demand substantial ransom payments in exchange for the decryption keys. Ultimately ransomware attackers are focused on financial gain. One of their main tactics for extracting a ransom is threatening to directly impact system availability. (See this 2021 breach as an example.)
Lateral movement to more TZAs
Once attackers compromise a tier-zero asset, they can use it as a launch pad to move laterally to other TZAs.
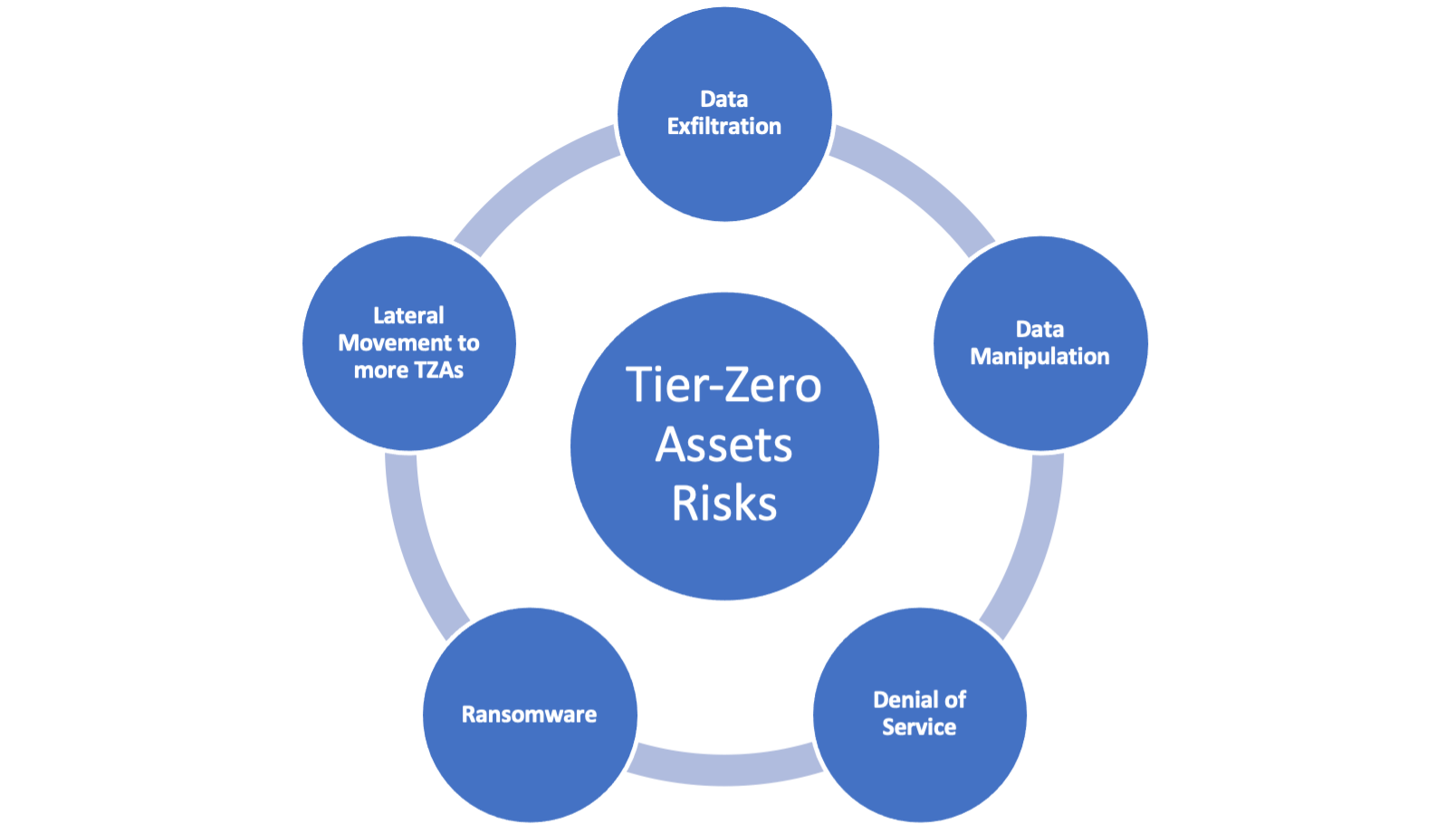
Figure 1. Tier-zero assets that attackers typically target.
Why an attack path assessment is so important
It is vital to assess your business from an attack path perspective—and to do so regularly, ideally continuously. That’s where an attack path assessment comes in. It can:
- Demonstrate how a sophisticated attacker would likely traverse through your systems and associated defenses
- Map how vulnerabilities might be chained together (using two or more hops) to compromise critical assets
- Estimate your actual risk as well as the exact location where mitigation would be most effective
Let’s look at the attack path posture demonstrated in Figure 2 below. The attack path, highlighted in red, shows that 102 identities can control one or more of the TZAs (on the tree root) using the “Owns” AD ACL. That said, it likely would be challenging for an attacker to compromise these highly privileged users.
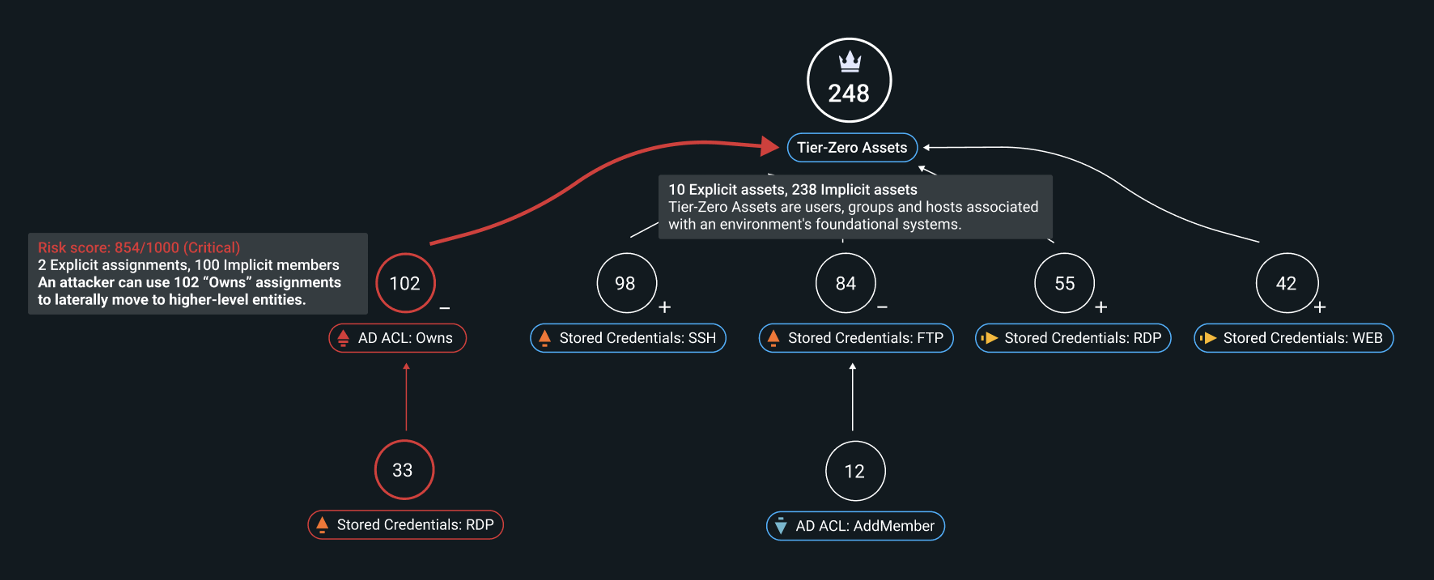
Figure 2. Example visualization of an attack path assessment.
Look deeper into the path outlined above and you can see that there are 33 hosts with exposed credentials. These hosts would allow an attacker to connect to any of the 102 identities using an RDP session. Stale RDP sessions are much easier for a threat actor to find and use. Fortunately, they are also easy for defenders to remove.
Additional considerations
Here are other ways an accurate and detailed attack path assessment can create value for a business.
Realistic risk assessment
Attack path assessments are typically visualized using a tree graph. This approach provides a clear and easy way to get an overall view of a company’s vulnerability landscape.
Prioritization
Intelligent APM systems give you a prioritized view of your attack paths, which enables you to start remediating the prioritized vulnerable paths immediately.
Proactive risk mitigation
Once potential attacks have been identified and prioritized, proactive steps can be taken to mitigate risks before malicious actors can exploit them. At that point, the business may decide that it needs to:
- Improve access controls
- Clean exposed credentials or sessions from hosts
- Increase monitoring
- Reconfigure security controls
Intelligent response by blast radius
The blast radius refers to the lateral movement opportunities for a compromised identity. When a company understands its unique blast radius, its security teams can act on these findings and isolate all lateral movement opportunities with speed and accuracy.
Compliance and regulation
Many industry-specific regulations, compliance standards and frameworks require that companies conduct risk assessments from an attack path perspective. The NIST Cybersecurity Framework (NIST-CSF), for instance, encourages businesses to assess cybersecurity risks by identifying:
- Assets
- Threats
- Vulnerabilities
- Potential attack paths
Stay tuned to learn more
If you take away one thing from this post, it should be this: Don’t focus exclusively on point vulnerabilities in isolation. Attack path management assessments can help you see the big picture of all your identity vulnerabilities and how they interrelate. It’s only when you take proactive steps to eliminate your key attack paths that you can stop attackers in their tracks.
In the weeks ahead, keep your eye out for more posts in this series. We’ll cover topics such as cleaning up the vulnerabilities you discover with attack path management and advanced attack vectors like the paths between AD identities to Entra ID resources in the cloud.
Meanwhile, learn more about your company’s attack path risk and how you can mitigate it. Sign up for a free Identity Threat Assessment from Proofpoint here. We can help you learn how attackers can move laterally in your environment—before they do.











