Active Directory is a centralized and standardized “directory service” that eases network management of user data, security and distributed resources, enabling straightforward interoperation with other systems and directories. Active Directory was introduced by Microsoft as part of Windows 2000 (actually, the concept of “directory services” was introduced even before that, with the Microsoft Exchange mail server). Ever since then, Active Directory has been an integral and important part of the Windows operating system architecture, and is now the world’s most-used directory services system. According to Microsoft, 95% of Fortune 1000 companies use Active Directory, and the market share is not much different when looking at smaller organizations.
So, it makes sense that many organizations use their Active Directory database to create, manage and control authentication and authorization of users to resources such as workstations and servers.
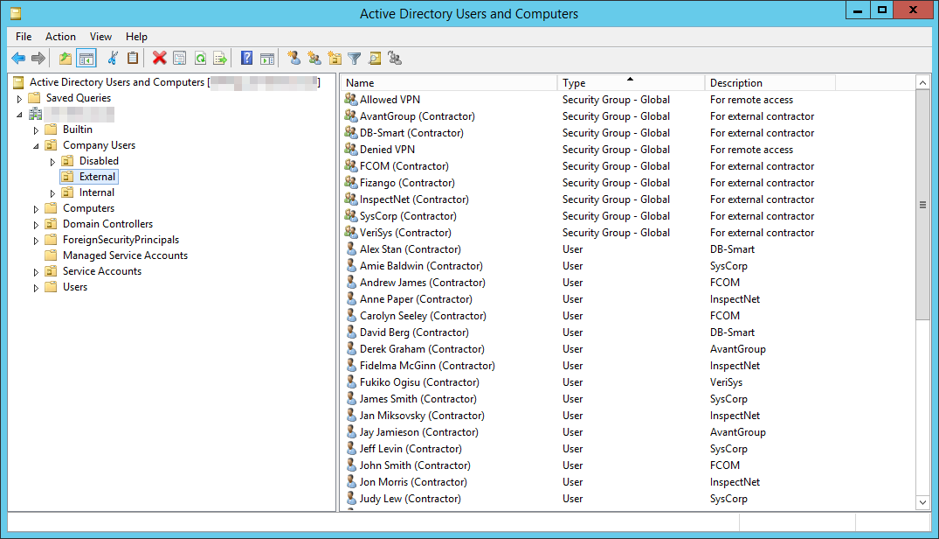
A typical Active Directory management window
Taking Advantage of Active Directory for User Activity Monitoring
One of Proofpoint ITM’s main User Activity Monitoring use cases is monitoring and auditing the activity of privileged users on company computers. These users include system administrators, database administrators, help desk users, DBAs, programmers and so forth. Because these users are given extensive access to sensitive data and systems across the organization, they are the most important people to monitor—both because of the risk they pose to the organization and because industry regulations (such as PCI, HIPPA and SOX) may mandate it.
Proofpoint helps organizations quickly enhance their security and achieve (and maintain) regulatory compliance by enabling the targeted monitoring and recording of specific users (and groups). This monitoring is usually applied to those users that represent the most risk to the organization. For example, system administrators with extensive IT permissions, business users with access to sensitive customer data, outside vendors who log in to the company via Remote Desktop or Citrix servers, and so forth.
For organizations already using Active Directory, Proofpoint ITM makes it very fast and easy to deploy selective User Activity Monitoring for privileged/risky users and groups. Proofpoint ITM is tightly integrated with Active Directory, allowing the auditor or security officer to configure recording policies that will only record specific users/groups. These recording policies can also be limited to selected Active Directory groups of machines.
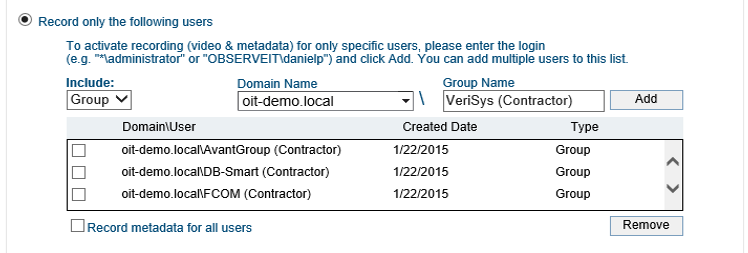
Recording policies can specify which users/groups to record using Active Directory.
Auditing the Use of Shared Accounts
Another challenge faced by many organizations face is controlling and auditing the use of shared accounts, such as “administrator” in Windows and “root” in Unix/Linux. Access to the accounts is frequently provided to internal privileged users and outsourced contractors in order for them to do their jobs. However, having only the generic login name to track the actions performed on sensitive machines makes it difficult to determine, at a later time, who was the actual person who did those actions.
One approach to this challenge is the deployment of a “password vault” solution that provides specific users with temporary passwords to access shared accounts, thus adding accountability for who used the shared credentials for each login. Unfortunately, password vault systems are complex and expensive to deploy, they force users to change how they work and they introduce a new single point of failure which could prevent logins at inopportune times. (Read more about these limitations here: Enterprise Password Vaults are Not Enough.)
The good news is that Proofpoint ITM can leverage an existing Active Directory infrastructure to immediately provide individual-name-auditing of the specific people logging in to servers using shared accounts. Proofpoint ITM does this without the need for any additional infrastructure, without a new central point of failure and without the need to change how users work. To do this, the organization’s administrators or security auditors can simply enable Proofpoint ITM's “secondary identification” feature for the shared accounts and/or specific servers they want to audit.
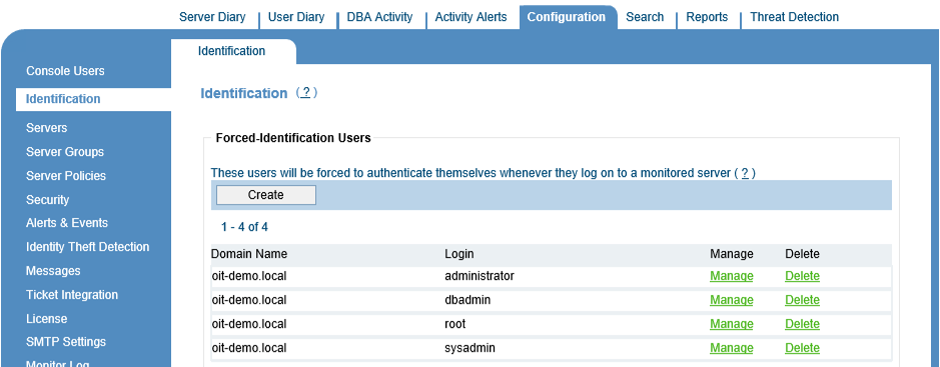
Specification of shared accounts that will require secondary login credentials
This causes a prompt to appear immediately after a user logs in using one of the designated shared-account credentials. At this prompt, the user must provide an authorized personal account login and password in order to access the computer.
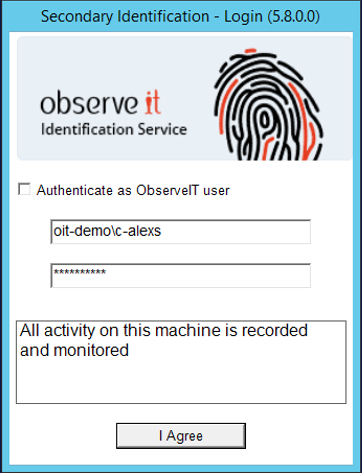
The Secondary Identification prompt that appears when logging in using a shared account
Proofpoint ITM validates these secondary credentials against the list of approved users/groups in Active Directory and will not allow the login process to proceed without valid credentials. Thus, with no more effort than assigning the appropriate Active Directory users/groups to specific shared accounts and/or designated computers, the shared account conundrum is eliminated.
At a later time, administrators and auditors can review the session records to see which particular user logged in using shared credentials. The views are either per login account or per server, with additional filtering options to make it easy to zero in on whatever is sought. Likewise, the system can generate reports with this information. Additionally, alerts can be defined to alert administrators any time a particular combination of server, shared account and secondary ID are used.
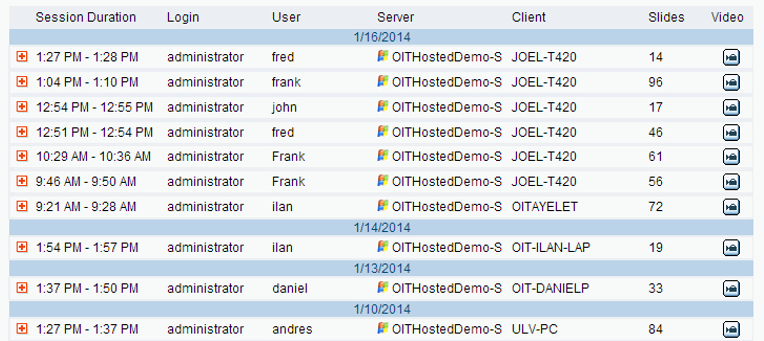
The server session list shows the actual User who logged in using each shared Login account.
Try it Yourself!
There is nothing like experiencing the value of User Activity Monitoring in your own environment. Get a free 15-day trial of the full-featured Proofpoint ITM, and see how easy it is to leverage your existing Active Directory infrastructure to monitor and audit your users. After your trial, purchase the solution or keep Proofpoint ITM Lite, free forever.











