Increasingly, companies are monitoring and recording the activities of their employees on company computers, to help protect critical business and customer data from unauthorized access and theft, as well as to comply with industry requirements (e.g., PCI‐DSS, HIPAA, SOX, ISO 27001). Not surprisingly, this has been met with concern on the part of employees, who fear that this monitoring may limit their privacy in the workplace.
However, a combination of logical controls and transparency can bridge these two seemingly diametric positions. After all, if an employer seeks to meet regulatory compliance requirements and/or to protect customer and employee data from theft – and do so without infringing on employee rights – then both sides will benefit from greater efficiency and security.
Let’s take a look at the three main ways in which our User Activity Monitoring solution respects and protects employee privacy.
Control What is Recorded
The first step in protecting the privacy of employees is to limit the monitoring and recording of their activities to what is actually necessary. For example, companies focusing on the protection of their sensitive data and systems have little reason to monitor what employees do in their personal email or social media accounts. Thus, it is important that recording policies be granular enough to include only the applications, websites or operating system areas that present risk. Alternatively, recording policies can be defined to record everything except particular applications or websites.
For example, a recording policy could be configured to record everything except when users are in Gmail and Facebook, as shown here:
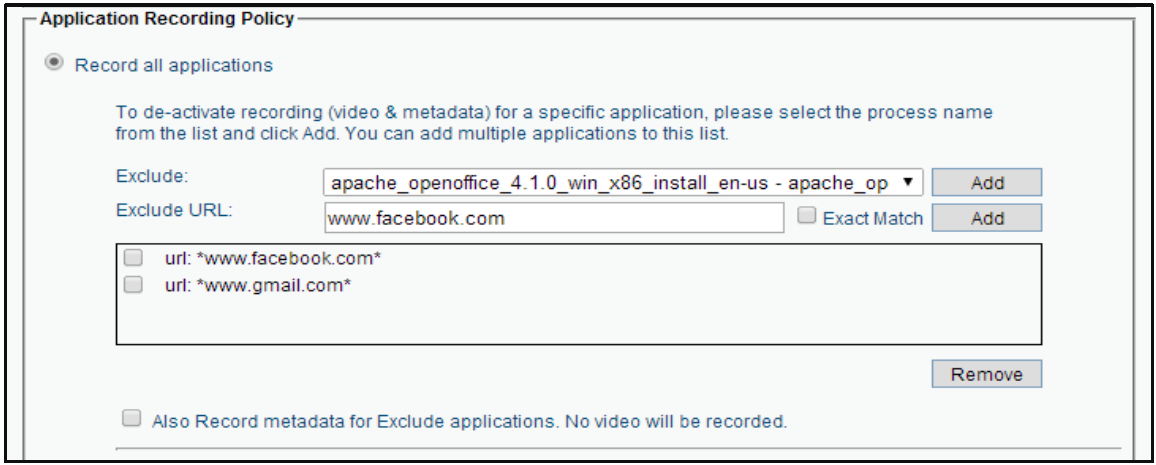
Note the checkbox at the bottom that allows the policy to log user activity – without screen video – so that administrators will be able to see the fact that a user was in Gmail or Facebook (and for how long), without seeing what the user was actually doing on those sites.
A second avenue of controlling what is recorded is based on particular users. It might make sense for a company to be very selective about who it is recording. For example, if only particular business users and administrators have access to regulated data, then it may not be necessary to record any other employees. Likewise, it might be inappropriate to record the activities of particular types of employees, such as top management.
It is important that a company have the ability to define numerous different recording policies, which can be applied selectively to particular computers and/or users. For example, it is reasonable that all activities performed by privileged administrators on sensitive servers be recorded, while significantly limiting what activities are recorded on employee desktops. This approach provides the ideal balance between business needs and employee privacy.
Control Who Can View Recordings
Perhaps even more important than controlling which activities and users are recorded, is the need to control access to the recordings themselves. It is easy to understand the impact on employee privacy that would result if unauthorized or unwarranted viewings of their activities were possible. To this end, Proofpoint provides the following protections of recorded user activity logs and screen video recordings:
- Different administrator permission levels – Just because an administrator is privileged to have access to the ITM console in order to configure the system, modify policies or run reports does not mean that the administrator should also have permission to view recorded user activity data. Therefore, the system provides different levels of admin accounts, separating between those individuals with the rights to configure the system and those who can access user activity data.
- Dual-password session playback privacy – To protect employee privacy, Proofpoint ITM can be configured to require a second set of credentials in order to view any recorded session video. Thus, with this option invoked, even an authorized administrator will not be able to play back user activity videos without the approval of a second individual. These additional credentials are typically held by legal counsel or an employee union representative, ensuring that employee privacy is protected to the maximum degree possible.
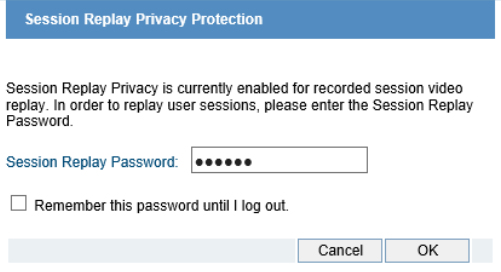
- Audit log of all session views – Proofpoint ITM generates an audit log of every time a user activity video was played or exported, and by whom. This allows employee representatives to conduct periodic audits to ensure that no unjustified invasions into employee privacy were conducted.
- Encrypted screen recording data – Of course, if system administrators were able to access the screen recording data outside the ITM system (e.g., by directly accessing the database), none of the above protection levels would ensure employee privacy. Thus, all user screen recordings are encrypted, making it impossible to view them except using the ITM console, subject to the above-described protection mechanisms.
- Hashed keylogging data – Finally, even the user’s keylogging data (i.e., all text typed, pasted, auto-completed, etc.) is stored in a hashed format, leaving it available for searching, but useless for reviewing. This ensures that sensitive keystrokes, such as passwords, can never be found by anyone with access to the Proofpoint ITM database.
Inform Employees of Monitoring Policy
Transparency is a critical element of employee activity monitoring. Whether because management wants to ensure open communication and mutual trust with their employees, or because local laws mandate it, informing employees that their digital activities are being monitored or recorded is a key element in the successful (and, sometimes, legal) deployment of an Employee Monitoring solution.
To this end, Proofpoint ITM provides a Login Message feature that serves two important purposes:
- The login message informs the user that all (or specific) activities on the computer will be monitored and/or recorded.
- The pop-up message may optionally be configured to require the user’s agreement before proceeding. Without checking this checkbox, the user will be unable to log in to the computer. Because the click on the agreement checkbox is recorded as part of the session video, it can serve as legal proof that users knew they were being recorded (e.g., in the event that employees try to deny that the monitoring was disclosed to them).
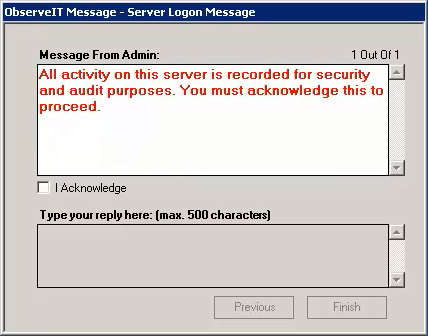
Because each recording policy can display a different login message, the specific details of the policies in effect at each login can be displayed (e.g., which users/applications/websites are or are not recorded). This level of transparency and communication between employer and employee fosters open communication and mutual trust.
To learn more about how User Activity Monitoring improves the secur
ity of business-critical applications, join us for a customer webcast: How Xerox Leverages User Activity Monitoring.











