One-size-fits-all is never fashionable, especially when it comes to education. Consider two employees who work for the same company: Martina and Mike. They’re roughly the same age, but Martina grew up with a computer in her home, and Mike only used a computer when he was at school. Martina was one of the first to get on the web, and she even created her own webpage. Mike, on the other hand, only used the internet when he needed to look up something for an assignment.
Now, say you’re an administrator who needs to educate Martina and Mike on the intricacies of cybersecurity and safe online behaviors. These two individuals have vastly different experiences and proficiencies when it comes to using a computer. Do you start them on the same training module? Or do you advance Martina to a higher level and give Mike a more basic introduction?
This isn’t merely an academic question. Taking time out of the workday for training is typically the largest expense when it comes to security awareness and training programs. Ideally, an organization wants the highest possible levels of safety with the lowest amount of investment. But how do we get there? Is that even possible?
To answer these questions, let’s look back through the history of educational research for a potential answer.
In the zone
In the early 1930s, a Soviet psychologist named Lev Vygotsky coined the term “zone of proximal development” (ZPD). It referred to the tasks a learner could accomplish with the assistance of a more capable partner. In other words, the learner might not be able to complete the task autonomously, but if they had a partner that could guide them or answer questions, then they could be successful. (See Figure 1.)
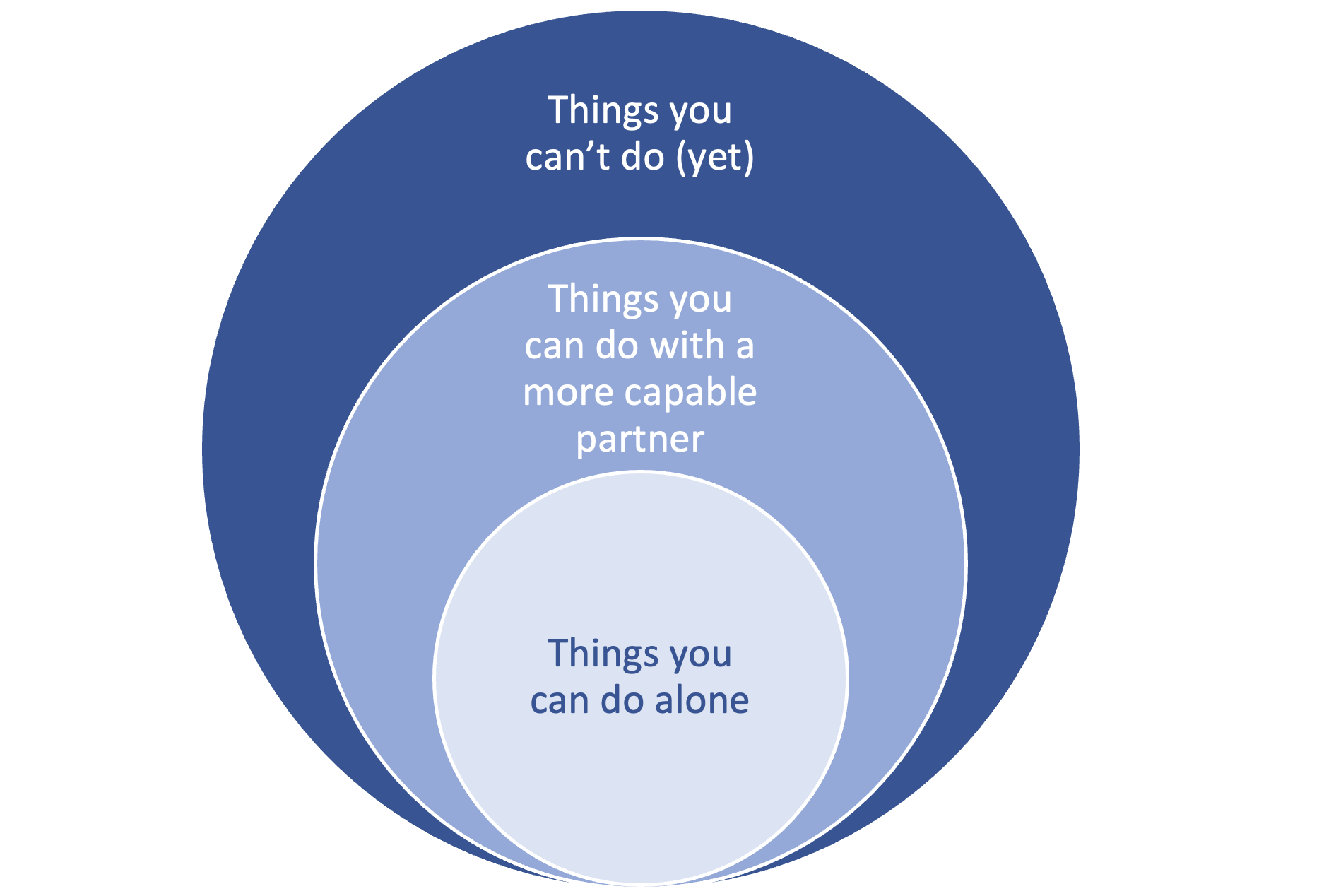
Figure 1. The three developmental zones, according to Vygotsky’s ZPD theory.
ZPD was a powerful idea because it recognized that one’s development exists on a continuum between “the things you can do alone” and “the things you can’t do (yet).” The “more capable partner” could be a teacher, tutor, coach or mentor.
Unfortunately, these types of educators do not scale well. It is extremely expensive to hire a tutor to teach each individual child all the subjects they need to learn. As a society, we solved that scaling problem with the advent of formal schooling. Now, we have about 30 students for every teacher.
While that solves the scaling problem, it creates a new problem: Because teachers have limited time, they are unable to tailor their instruction to the capabilities and background knowledge of each learner. Instead, they must teach to the average student and then provide remediation (or enrichment) when possible.
The advent of the student model
To simultaneously solve the scaling and customized-learning problem, educational psychologists began collaborating with computer scientists to develop computerized teaching systems. The first generation of Computer Aided Instruction (CAI) fell short of the mark because each student was given the same set of tasks.
However, those early efforts helped pave the way toward Intelligent Tutoring Systems (ITS). This second generation of teaching machines could adapt instruction to the individual student by creating a student model. In other words, the system attempted to diagnose what the learner knew, or didn’t know, about each lesson or topic.
For example, a physics tutoring system gives a problem to an individual to diagnose if they understand how to properly apply Newton’s second law of motion. If the student correctly applies the law to a problem, then the system increases its probabilistic estimate that the student knows that skill. It then continues to repeat the same process across the many different skills needed to solve physics problems, each time updating the student model for that particular student.
Cybersecurity isn’t rocket science (nor is it physics)
If an ITS can be built for physics, then why don’t we take the same approach for cybersecurity awareness training?
In 2021, Proofpoint developed the Adaptive Learning Framework, which mapped specific pieces of content to a single control domain (for example, email and social engineering, mobile devices, insider threats, etc.).
Those pieces of content were also associated with a targeted level of understanding—for example, basic, beginner, intermediate and advanced. (See Figure 2.)
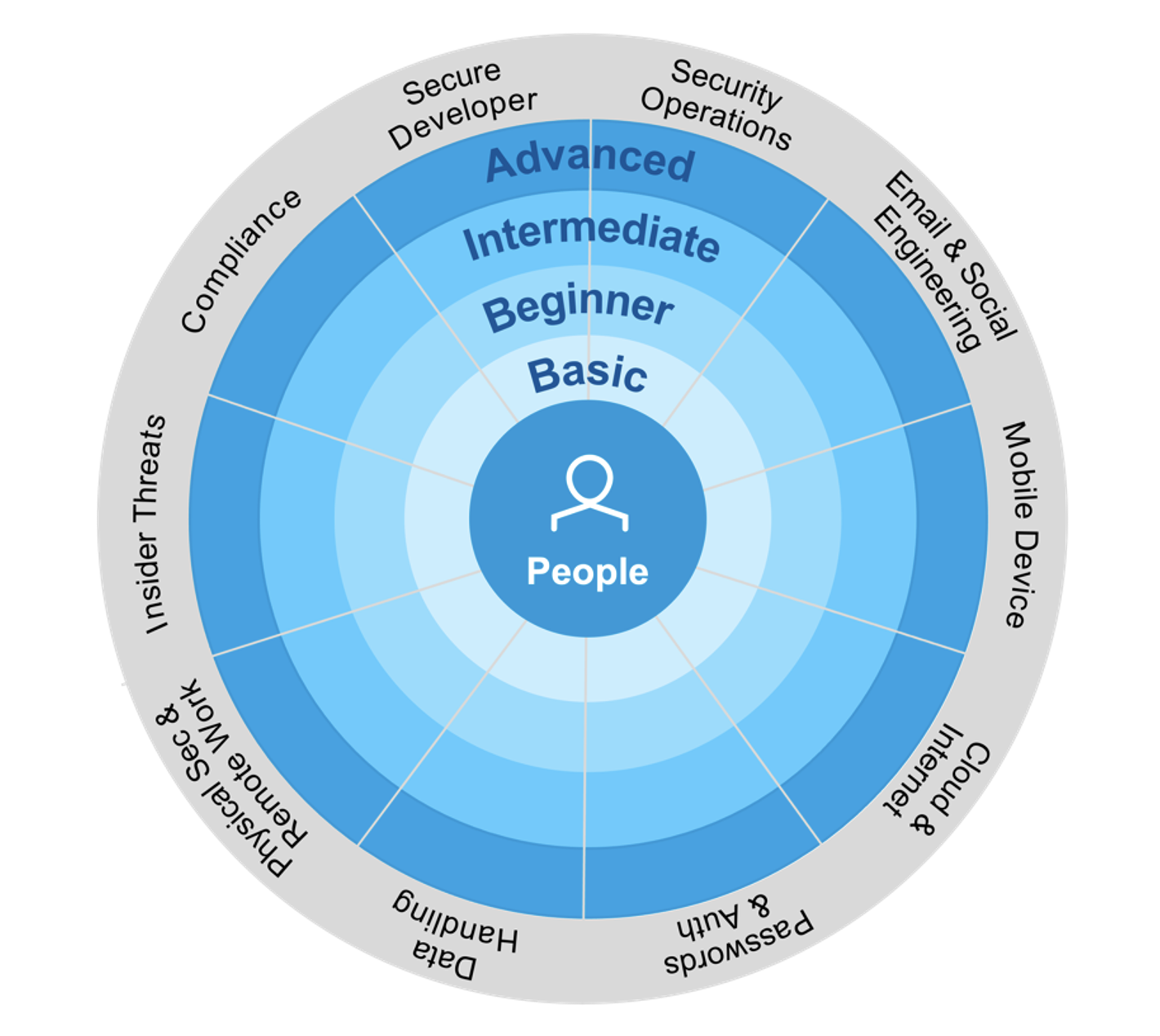
Figure 2. The 10 control domains and four knowledge levels of the Adaptive Learning Framework.
The goal of the Adaptive Learning Framework is to deliver the right content to the specific level of understanding of the learner. In so doing, Proofpoint Security Awareness Training minimizes the time wasted on lessons that employees already know.
As administrators, we’re going to treat Martina and Mike as individuals. And they, in turn, will get up to speed on cybersecurity in a way that suits them best—with an adaptive learning program.
To learn more about how you can use the Adaptive Learning Framework as the foundation to shape user behavior and empower security culture, check out our blog post, “Drive Behavior Change and Engage Users with an Adaptive Learning,” and watch our on-demand webinar, “How to Shape Security Behavior and Build Sustainable Habits.”











