Last Thursday, we welcomed attendees from around the globe at our annual Wisdom conference to explore how to elevate security awareness programs. Here are five highlights from the virtual conference. To view these sessions and more on-demand, enter your information here.
1. Threat data drives successful security awareness programs
On a customer panel featuring Mike Manrod, CISO of Grand Canyon Education and Deanna Bennigsdorf, GRC Lead of Corteva Agriscience, participants shared how they use threat intelligence to enhance their security awareness programs. Here are some key takeaways from the group:
- Develop collaborative relationships across the security organization (e.g. threat intelligence, SOC, incident response) to customize phishing templates and content based on real-world activity
- Communicate regularly with these groups using corporate messaging apps and regular stand-up meetings
- Curate broad threat data via PhishAlarm, abuse mailbox, threat intel feeds like Proofpoint Emerging Threats, ISACs (Information Sharing and Analysis Center) and local threat information groups to build campaigns, messaging and security awareness programs.
- Make security awareness programs more relevant for users by sharing data with the entire organization to boost user knowledge and engagement about the threats the organization is targeted with.
- Understand which users are more at-risk and tailor outreach, content and communications for them.
2. Measure the success of their security awareness programs
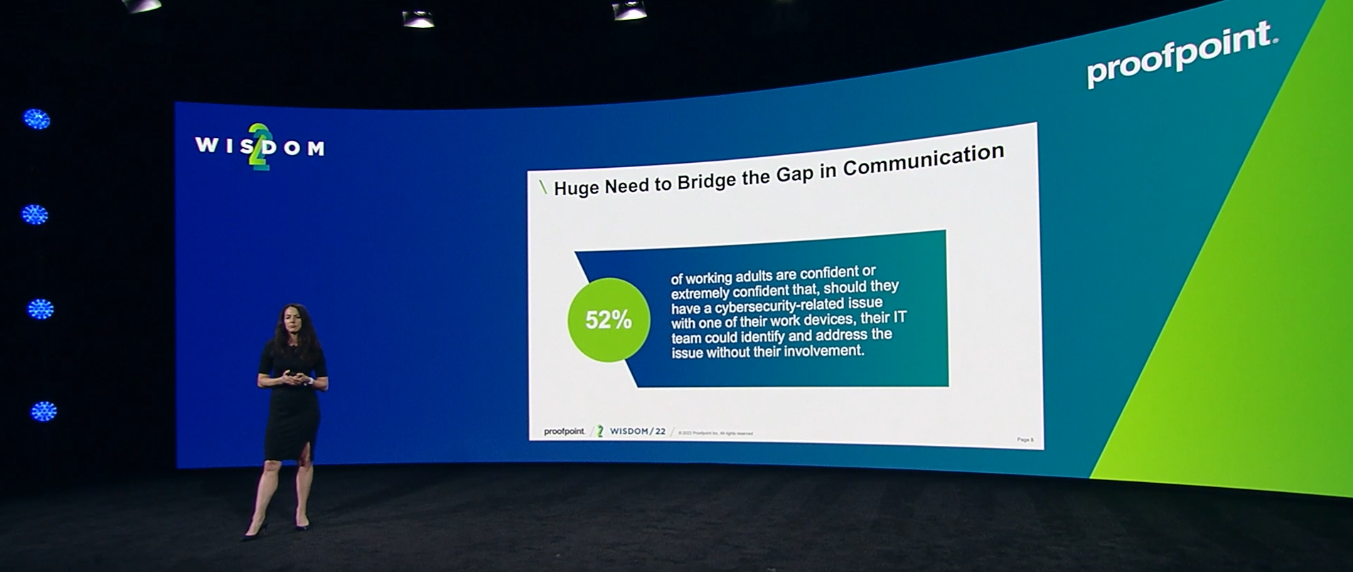
Customers including Princess Young of Southwest Airlines and Katie Whitt of Nationwide Children’s Hospital shared how essential success metrics are for garnering executive support of security awareness programs.
While phishing simulation click rate is a great metric to track there are so many more that can give you valuable information about your program, including reporting rates, non-response rates, and click rate of the educational content included in simulations. There are also qualitative metrics to take into account including user engagement and motivation.
Qualitative feedback helps your leadership team understand what you did to impact a metric overtime. What metrics you track should be dependent on how you and your leadership team define success. And you don’t need to tackle everything at once—you can build over time as your program continues to mature.

3. Getting Buy-In from End Users and Leadership
Customers from Trust Financial and SMBC Bank shared best practices to engage users and get buy-in from executive leadership.
Changing user behavior, when it comes to security awareness, relies on tactics that work for any other kind of behavior change:
- Stay positive. No one is motivated by criticism. Create a community of educated digital citizens by focusing on the opportunity for security awareness.
- Be personal. Security awareness shouldn’t be relegated to the professional sphere.
- Promote storytelling. People resonate with human stories, not lists of facts. Develop compelling narratives with heroes who identify and stop email attacks.
- Use language that’s succinct, relevant and digestible.
- Be consistent in your communications so secure habits stay top of mind for your users who will start to build muscle memory for the best practices you’re promoting.
Of course no program, no matter how well-orchestrate, will be successful without buy-in from leadership. To get it, identify people who can be your program champions and build strong relationships with them. And base your case in data—use industry reports that prove cybersecurity incidents often involve human error to justify the spend of your security awareness program.
4. The vision and roadmap for Proofpoint Security Awareness Training
Karen Letain, VP of Product, Security Awareness, highlighted innovations from Proofpoint that will help organizations advance the security awareness at their own organization in the following ways:
- A culture assessment which will help companies assess their security culture.
- An adaptive learning framework with a variety of content styles and learning modules, including micro-learning, in over 40 languages.
- Email warning tags with “Report Suspicious” which provides contextual nudges to change use behavior
- A Repeat Offenders Report which will empower you to understand which users need extra intervention based on how many times they repeatedly click and fail phishing simulations.
Read more about these product innovations and many more in our press release here.
5. Guest speaker BJ Fogg discussed how to use behavior design to advance programs from awareness to behavior change
Andy Rose, Proofpoint Resident CISO, discussed how to model and influence behavior change with BJ Fogg, our guest speaker. They explored the different factors that influence behavior change and BJ shared his tips for creating lasting change by tapping into the sources of human motivation: competition, cooperation and recognition.
Speakers shared so many more *wise* insights and best practices throughout the conference. But what makes Wisdom so special is the community it gathers. Thank you to all of our participants and customers for another great year. Again, if you’d like to view the sessions on demand, please click here. We hope to see you next year!