Home Networks Are Left in a Highly Vulnerable State
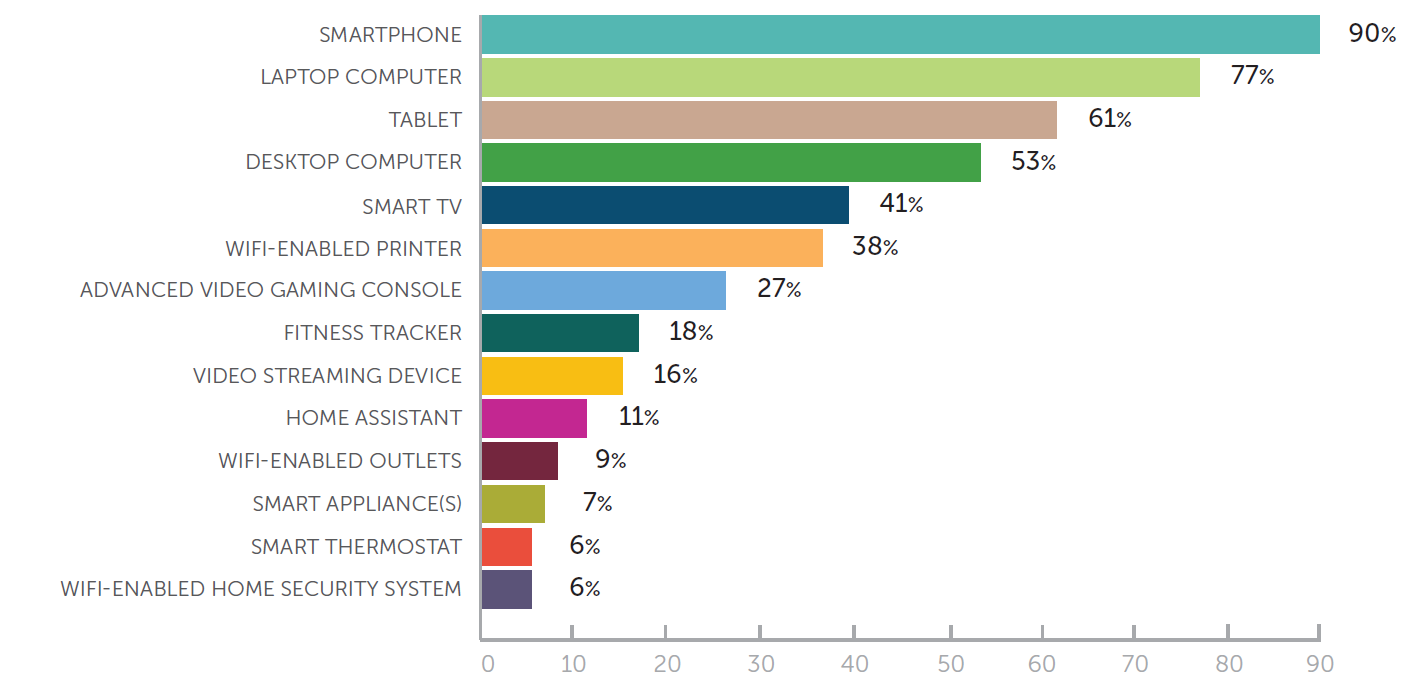
We wanted to look beyond working adults’ use of public WiFi this year and, as such, our 2018 survey included several questions related to home WiFi use. We found that more than 90% of users said they have a home WiFi network, and that a wide variety of devices are connected to these networks (see the graphic below). Half of respondents said they have 3 to 5 devices in use in their households, 27% said they use 1 to 2 devices, and 18% put the mark at between 6 and 10 devices. Interestingly, respondents were more likely to have 11 or more devices in use than they were to have no devices at all (3% vs 2%).

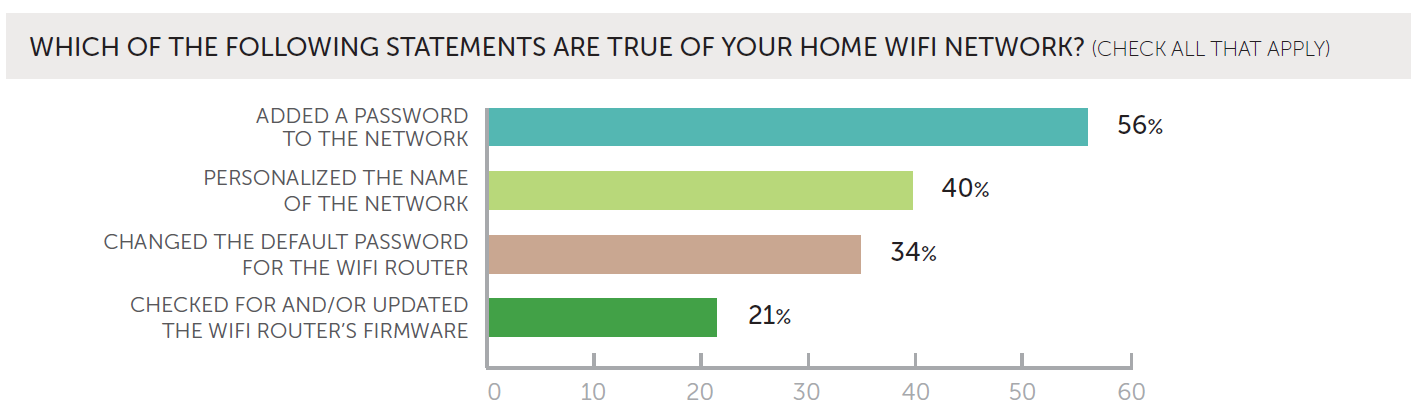
Knowing these responses, it should set off alarm bells that 44% of global respondents said they have not added a password to their home WiFi networks. In addition, despite widespread FBI warnings earlier this year about router vulnerabilities, 66% of users have not changed their router’s default password, and 79% have not updated firmware.
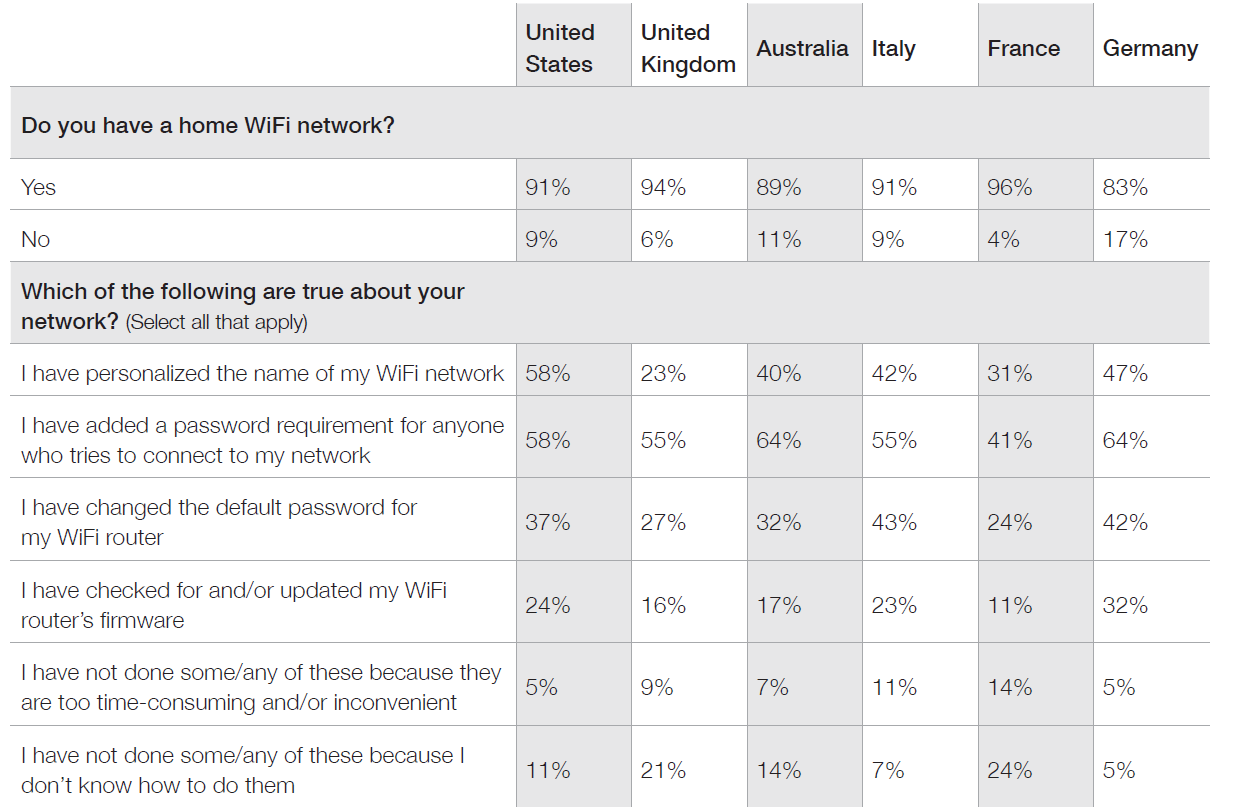
We did see some interesting variations across regions, as you’ll note in the chart below. Working adults in Germany, though least likely to have home WiFi in comparison to their global counterparts, are most likely to implement key safeguards on their networks. On the opposite spectrum, French users — the most likely to have a home WiFi network at 96% of respondents — are much less likely than working adults in other countries to take important security precautions, and nearly a quarter of those said they haven’t taken the steps because they don’t know how to.
Advice for Turning the Tide
If your organization does not allow BYOD access to corporate systems … and none of your end users travel for business … and nobody in your organization works remotely … well, our User Risk Report findings are not likely to spark much concern. But we’re guessing that’s not the case.
The question is, what to do about it?
First, we recommend you start by recognizing that the actions your employees are taking outside of business hours are impacting your organization’s internal security posture. Second, instead of getting angry about it — or maybe in addition to getting angry about it — we suggest getting proactive about advice and guidance. Here are two simple (and not terribly time consuming) steps you can take to start closing the knowledge gap (and the resulting security holes):
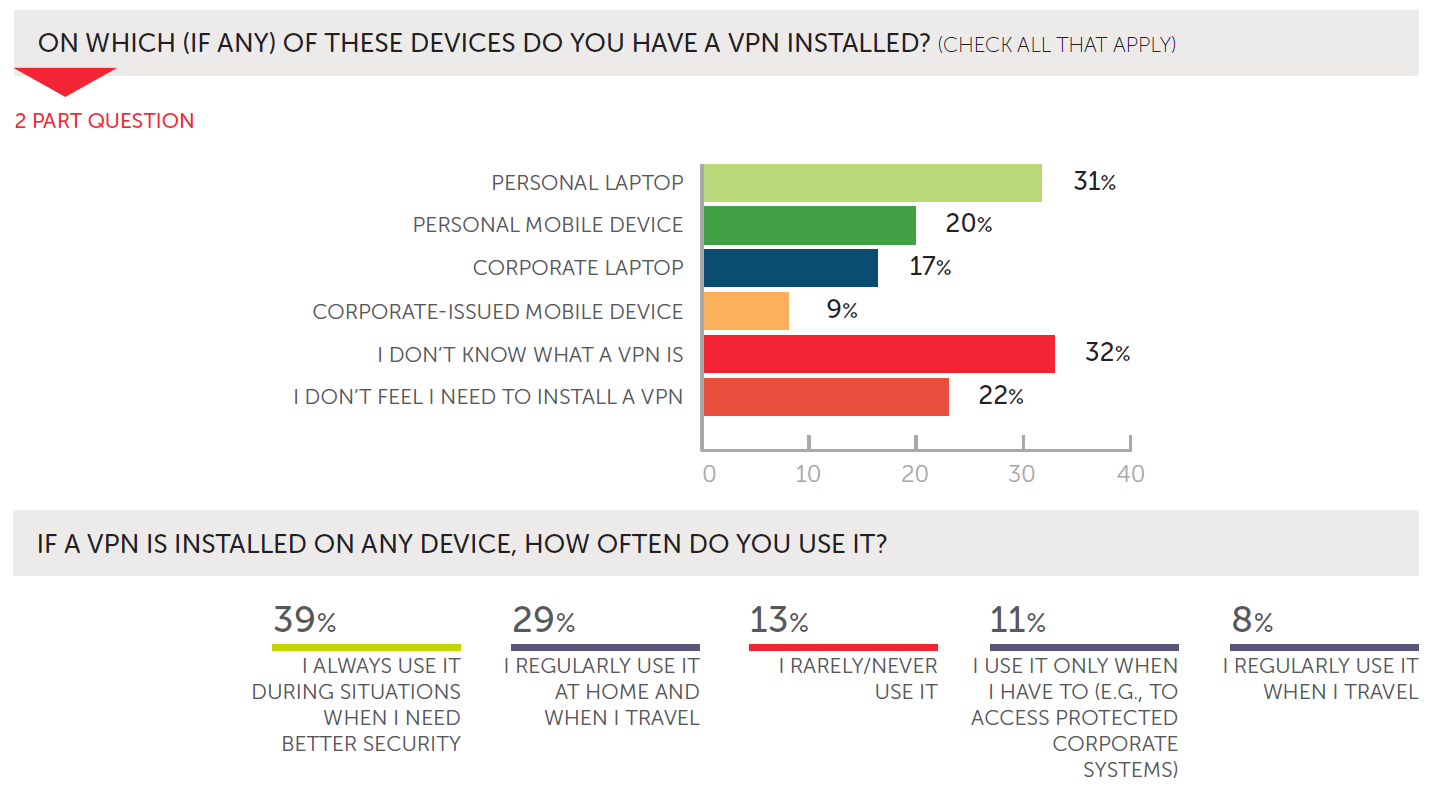
- Recommend VPNs your employees can use on personal devices – With all the options available in all the app stores, technology users are likely to feel uncertain about which VPN to choose even if they do take it upon themselves to install one. Your end users trust your IT expertise, and you can help to raise VPN adoption rates by sharing your recommendations for different devices. You don’t have to endorse any particular VPN over another, but making some suggestions can give clarity and confidence to employees who are interested in better device security. You’re not likely to influence everyone, but every bit helps.
- Provide a security checklist for home WiFi users to follow – Rather than assuming your end users are taking the precautions they should be taking on their home networks, give them some help in getting the work done by providing an actionable checklist. If you're concerned about the number of questions that will come from your full employee base, focus your initial attention on remote workers and frequent travelers, who are most likely to connect to corporate systems from outside the office. Even sharing some third-party advice (like our blog post about this very topic) is a step in the right direction.











 We also advise technology users not to confuse trusted locations with trusted WiFi — again, with good reason. As noted in the graphic, nearly 40% of respondents to our global User Risk Report survey believe that they can rely on the security of a free WiFi network if they’re in a location they trust (like a local coffee shop or international airport). In locations like France and Italy, there’s an even bigger disconnect, with 45% and 59% of users putting their (misguided) trust in this technology, respectively.
We also advise technology users not to confuse trusted locations with trusted WiFi — again, with good reason. As noted in the graphic, nearly 40% of respondents to our global User Risk Report survey believe that they can rely on the security of a free WiFi network if they’re in a location they trust (like a local coffee shop or international airport). In locations like France and Italy, there’s an even bigger disconnect, with 45% and 59% of users putting their (misguided) trust in this technology, respectively.