Tax-themed email phishing campaigns are a mainstay for threat actors worldwide as they often pursue tax season to siphon funds and personal information. As a follow-up to our recent tax-related overview of US and UK-focused attacks, below is a sample of a recent campaign that focused on organisations in Australia.
While Australia’s tax season runs from July 1 to October 31, it didn’t stop threat actors from already trying to trick recipients in manufacturing, technology, and IT industries into revealing their credentials. Below is an example of a low volume Australian-focused campaign from January 2021 that fraudulently used the Australian Taxation Office branding and promised a tax refund notification. If the URL within the email is clicked, it leads to a fake myGov authentication page designed to harvest user credentials.
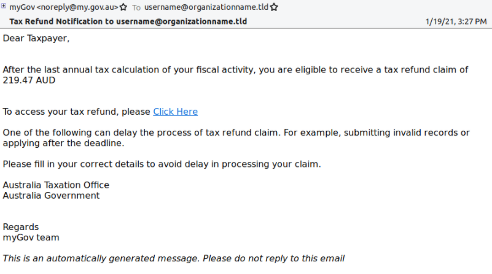
Image 1: Fraudulent Australian tax refund phishing email example
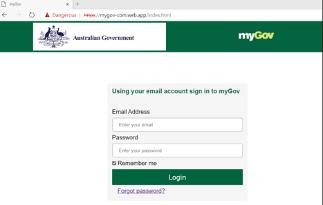
Image 2: Fake myGov landing page designed to trick recipients into revealing their credentials
In January 2021, we also observed threat actor TA2102 targeting Australian citizens with a series of ransomware campaigns, including one leveraging the promise of tax refunds. The campaign sends messages with subjects including:
- Tax Invoice 2101996
- Payment GC328034
- Tax Invoice 2101321
- invoice GC382528
- Payment 2101549
These messages contain Microsoft Excel documents that use XL4 macros to download Thanos Ransomware. Thanos ransomware encrypts file extensions and uses a 2048-bit RSA public key to encrypt files. After encrypting the file’s contents, Thanos will add the file extension “.locked” to the file on disk.
Please see a sample of the message below:
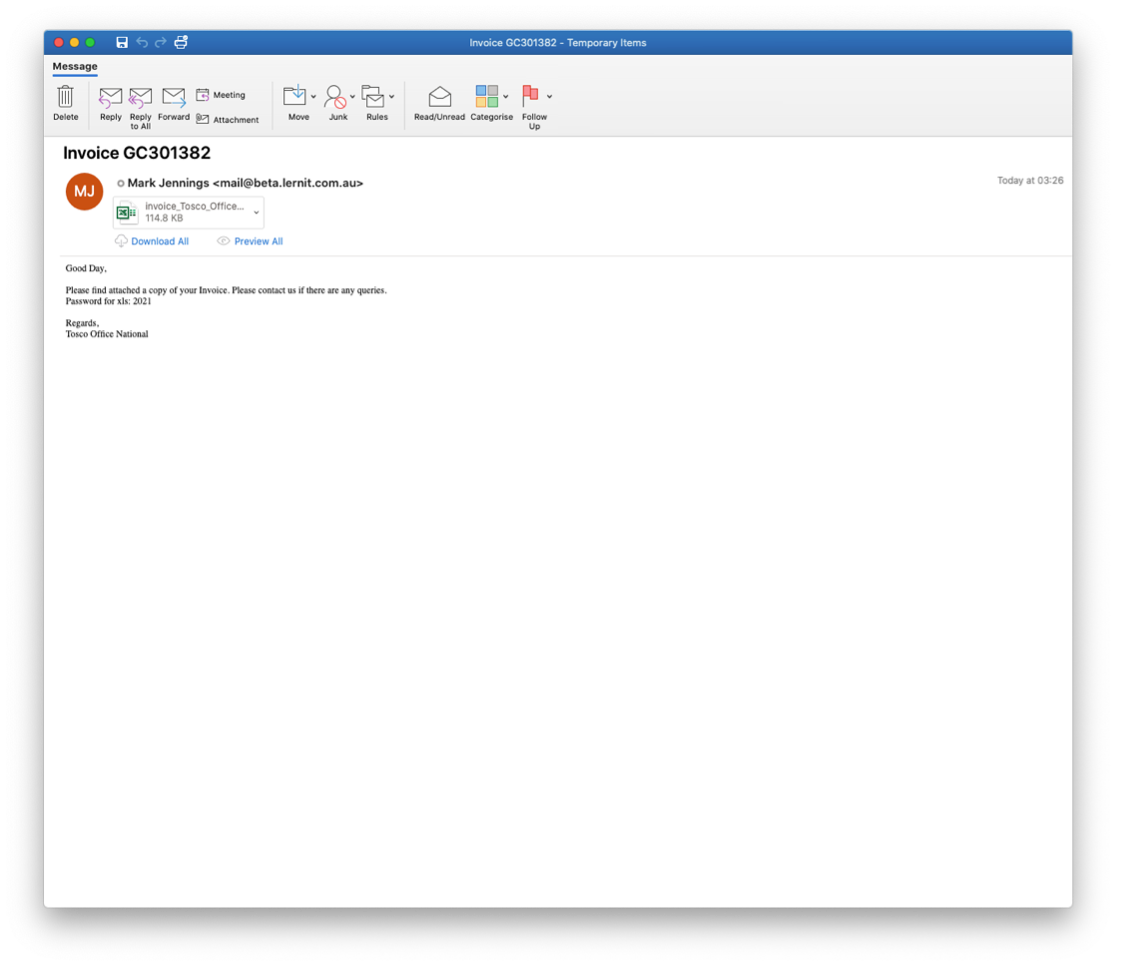
Image 3: Message containing Microsoft Excel Document
Conclusion
Tax season is a popular time for threat actors to conduct email-based attack campaigns designed to steal sensitive information for financial gain. In 2021, threat actors are often combining current events such as COVID-19 or healthcare themes alongside typical tax lures to further entice victims.
To reduce the risk of successful exploitation, Proofpoint recommends the following:
- Train users to spot and report malicious email. Regular training and simulated attacks can stop many threats and help identify people who are especially vulnerable. The best simulations mimic real-world attack techniques. Look for solutions that tie into real-world attack trends and the latest threat intelligence.
- At the same time, assume that users will eventually click some threats. Attackers will always find new ways to exploit human nature. Find a solution that spots and blocks inbound email threats targeting employees before they reach the inbox. Invest in a solution that can manage the entire spectrum of email threats, not just malware-based threats. Some threats—including business email compromise (BEC) and other forms of email fraud—can be hard to detect with conventional security tools. Your solution should analyse both external and internal email—attackers may use compromised accounts to trick users within the same organization. Web isolation can be a critical safeguard for unknown and risky URLs.
- Manage access to sensitive data and insider threats. A cloud access security broker can secure cloud accounts and help you grant the right levels of access to users and third-party add-on apps based on the risk factors that matter to you. Insider risk management platforms can help protect against insider threats, including users compromised by external attacks.
- Partner with a threat intelligence vendor. Focused, targeted attacks call for advanced threat intelligence. Leverage a solution that combines static and dynamic techniques at scale to detect new attack tools, tactics, and targets—and then learn from them.











