Last Time in the BEC Taxonomy Series…
Proofpoint researchers in the third of the Business Email Compromise (BEC) taxonomy series delved further into the Theme tier of the Email Fraud Taxonomy framework (Figure 1), focusing on payroll redirect schemes and how they can be some of the simplest, but still costly, email fraud attacks. Now we will explore another theme category, extortion, which has the potential to elicit the most fear, anxiety, and sense of urgency from victims out of all the email fraud themes addressed in our taxonomy.
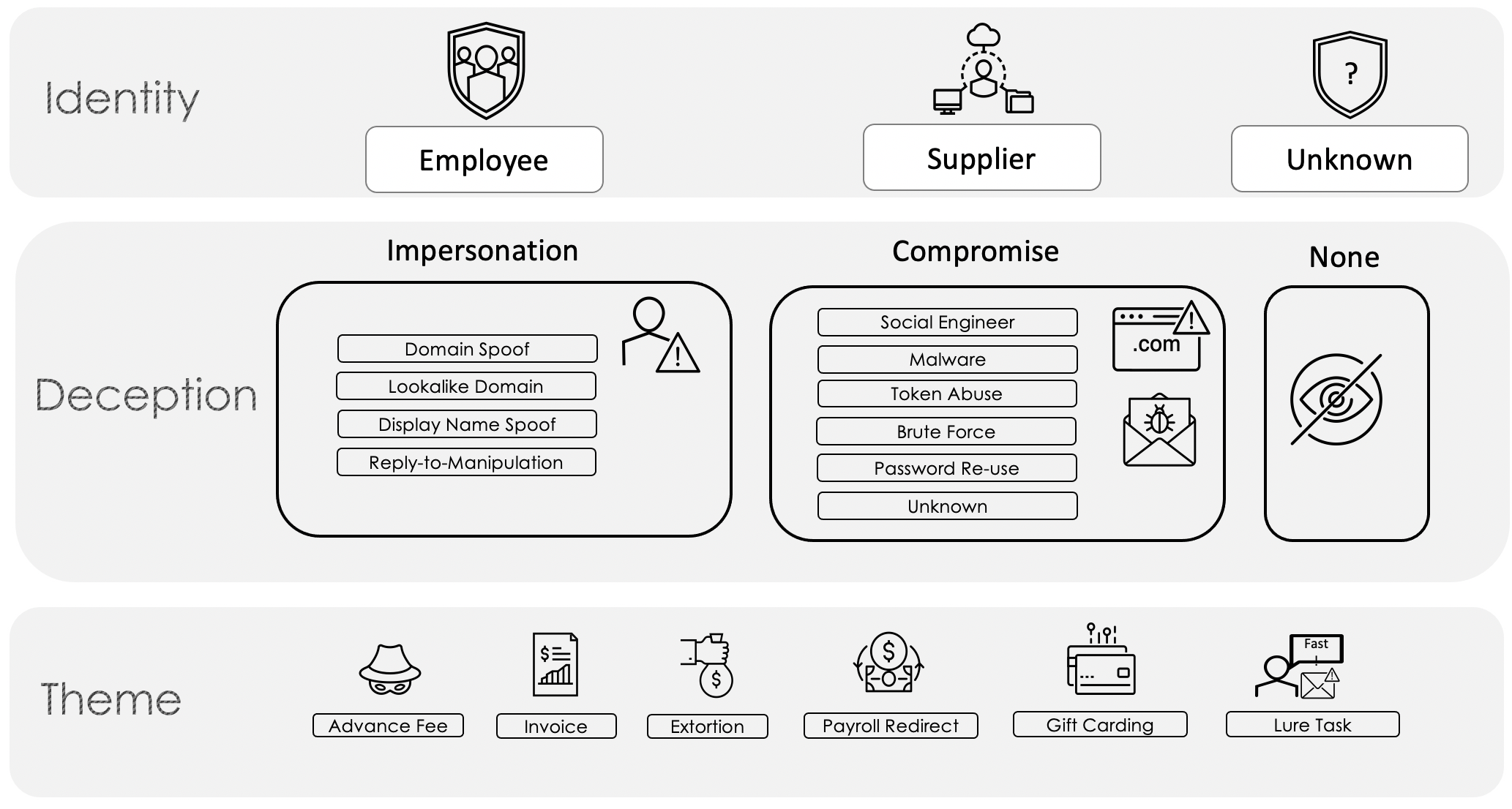
Figure 1. Email Fraud Taxonomy Framework.
What is Extortion?
Extortion as it relates to email fraud is any email-originated demand in which a good, service, or payment is requested to prevent destruction of property, violence, or release of confidential, embarrassing, or compromising information. Extortion has several subtypes, including:
-
Data Release: This is any attempt in which a threat actor has accessed or claims to have accessed sensitive data, customer information, or trade secrets. The threat actor essentially holds this valuable information hostage in return for a sum of money. The threat actor may threaten to make this information public if their demands are not met.
-
Distributed Denial of Service (DDoS): In this extortion attempt, a threat actor asks for money from a victim under the threat of launching a DDoS attack against the victim’s online assets. Such threats typically request payment in the form of cryptocurrency.
-
Physical Harm: This encompasses any attempt to extort a payment, also commonly in the form of cryptocurrency, in exchange for not physically harming the victim or their organization. Common threats under this type include bomb threats, hitmen, and murder plots.
-
Sextortion: This is probably the most commonplace of the extortion subtypes and includes deceitful attempts to extort a payment, likely in cryptocurrency, by threatening to release sexually related photographs or videos of the victim.
Extortion and the Email Fraud Taxonomy Framework
Extortion email fraud is the first of our themes that regularly does not use deception as a tactic or leverages just one, impersonation (per the Proofpoint Email Fraud Taxonomy Framework in Figure 1 above). In this social engineering scenario, making the email look as if it originated from the victim’s mailbox. An example of this begins with an email message from the threat actor claiming that they had hacked your computer and recorded you visiting adult content. The portions of the email with sensitive content would be made to look like they came from your mailbox. Unless you meet their ransom demands, the threat actor would threaten to release this information to your coworkers and family. Such a scenario would be mapped to the Proofpoint framework as depicted in Figure 2.
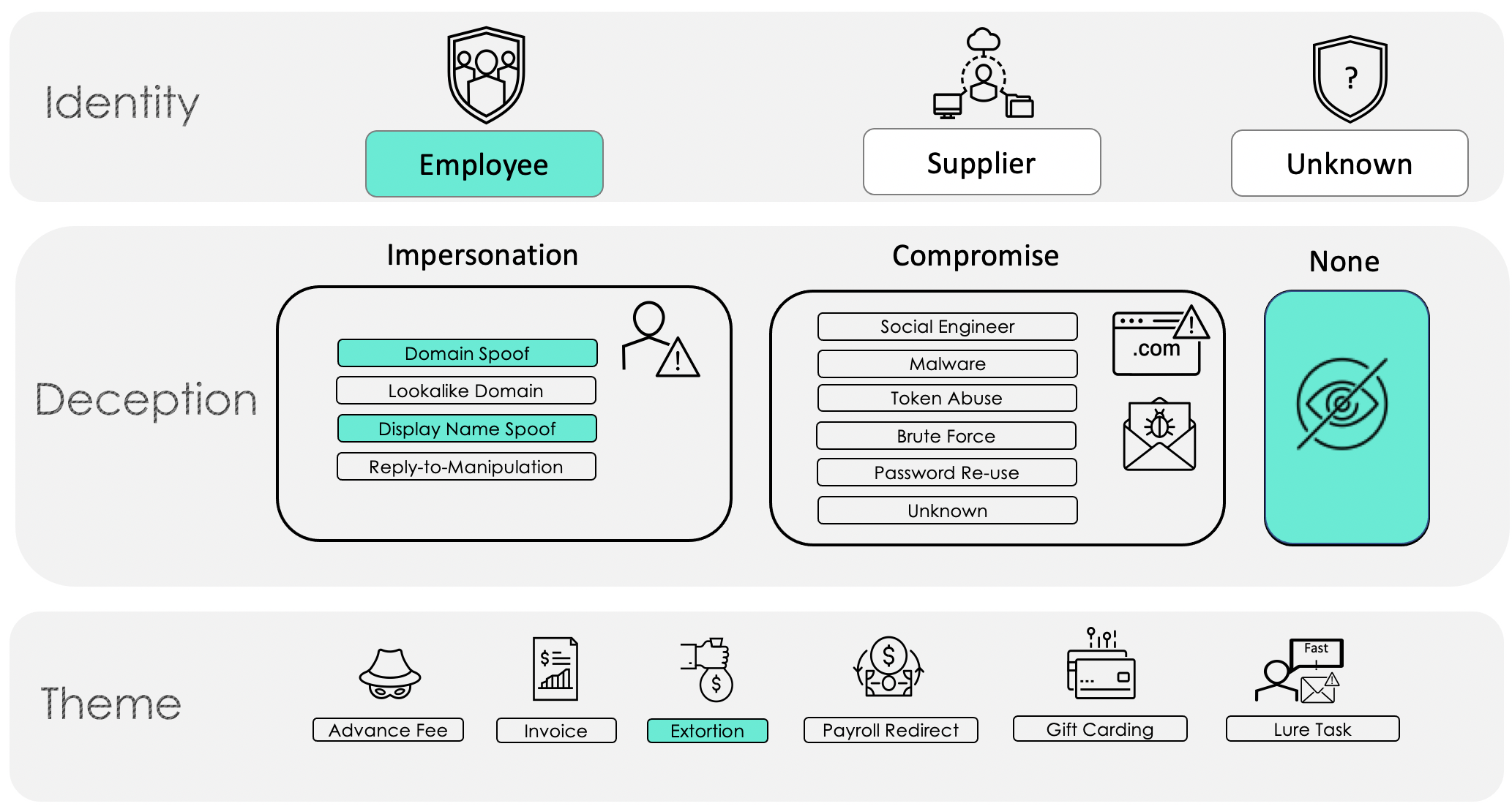 Figure 2.
Figure 2.
In other instances, in which a threat actor does not use impersonation in an extortion scheme, free email providers are typically leveraged with no spoofing. Such a scenario would map to the framework as follows (Figure 3):
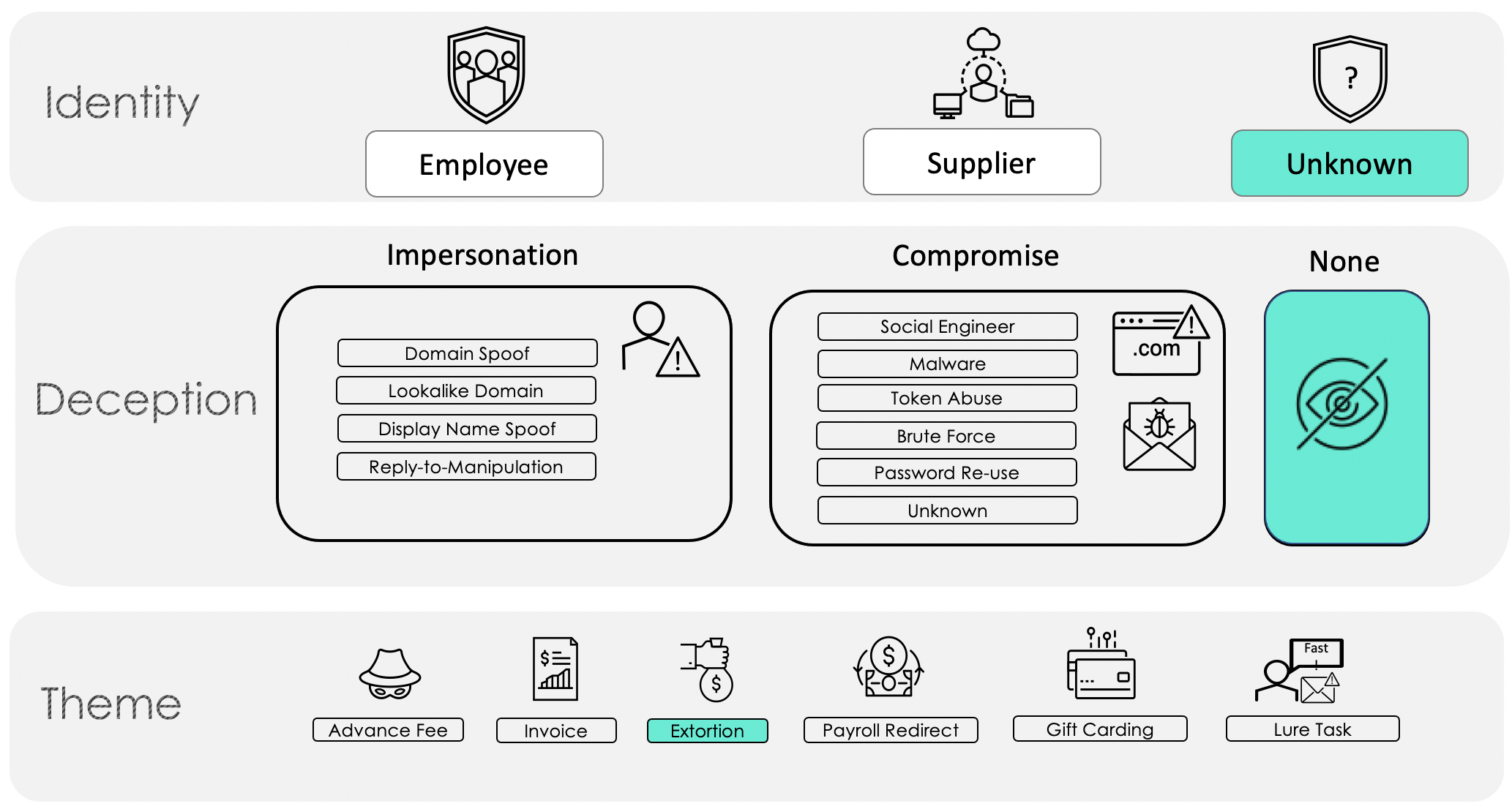
Figure 3.
Real World Examples
By far the extortion type most seen in Proofpoint data is sextortion. These fraudulent emails tend to be quite lengthy in their efforts to convince the victim that they are in a precarious position and need to meet the threat actor’s demands.
In the sample below (Figure 4), the threat actor not only includes details on how they captured the sensitive content they claim to have in their possession but informs the victim that they have their contact list with phone numbers, emails, and social media. The threat actor also provides their Bitcoin address for payment, which they expect in a week’s time.
Figure 4.
Another type of extortion less commonly seen by Proofpoint analysts but that can be quite alarming to receive is physical harm. As seen in Figures 5 and 6, these emails attempt to scare the victims into thinking their lives are in grave danger and that the only way to keep themselves safe from harm is by paying the threat actors. Some key attributes to these kinds of emails include a sense of urgency and limited time for the victims to decide what to do, as well as strong discouragement from contacting law enforcement.
Figure 5.
Figure 6.
Keep Reading…
In our next BEC blog post we will tackle another category in the Theme tier, lures and tasks.











