Key Takeaways
- Small and medium-sized businesses (SMBs) are increasingly being targeted by Advanced persistent threat (APT) actors globally.
- Proofpoint researchers have identified three main trends of attacks targeting SMBs between 2022 and 2023, including the use of compromised SMB infrastructure in phishing campaigns; regional SMB targeting by state-aligned actors for financial theft; and vulnerable regional managed services providers (regional MSPs) being targeted via phishing and thereby introducing the threat of SMB supply chain attacks. Regional MSPs are small to midsize MSPs that service customers in a concentrated geographic area.
Overview
Proofpoint researchers conducted a retroactive analysis of small and medium businesses (SMBs) targeted by advanced persistent threat (APT) actors from Q1 2022 through Q1 2023. By leveraging the Proofpoint Essentials telemetry, which encompasses over 200,000+ small and medium business organizations, researchers were able to identify key trends in the APT landscape that pose unique threats to SMBs globally. By examining this data our researchers identified several APT actors specifically targeting SMBs including threat actors aligned with the Russian, Iranian, and North Korean state interests. This research seeks to highlight the threats facing SMBs today from apex level APT actors and provide the SMB community use cases of such targeting over the past year.
Understanding the Threat Landscape
Many organizations attempting to secure their network often focus on business email compromise (BEC), cybercriminal actors, ransomware, and commodity malware families that are commonly encountered in the emails received daily by millions of users worldwide. Less common, however, is a widespread understanding of advanced persistent threat actors and the targeted phishing campaigns they conduct. These skilled threat actors are well-funded entities associated with a particular strategic mission that can include espionage, intellectual property theft, destructive attacks, state-sponsored financial theft, and disinformation campaigns. While more rare and often much more targeted than cybercrime activity, Proofpoint data indicates that APT actors remain interested in SMB targets that align with their broader mandates as indicated above. This means that some of the most formidable cyber threat actors in the landscape maintain an interest in targeting businesses that are commonly under-protected against cyber security threats such as phishing campaigns.
Emerging APT Trends Impacting SMBs in the Cyber Threat Landscape
By examining a year’s worth of APT campaign data, Proofpoint researchers have identified APT actors from Russia, Iran, and North Korea targeting SMBs with phishing campaigns. These campaigns highlight three pertinent trends in the types of attacks and tactics being used against SMBs.
- APT actors using compromised SMB infrastructure in phishing campaigns
- APT actors engaging in targeted state aligned financially motivated attacks against SMB financial services
- APT actors targeting SMBs to initiate supply chain attacks
SMBs Used for Compromised Infrastructure in Threat Actor Campaigns
Proofpoint researchers observed more instances of impersonation or compromise of an SMB domain or email address over the past year. These occurrences often involved a threat actor successfully compromising an SMB web server or email account. These compromises may have been achieved through credential harvesting, or, in the case of a web server, through unpatched vulnerability exploitation. Once compromise was achieved, the email address was then used to send a malicious email to subsequent targets. If an actor compromised a web server hosting a domain, the threat actor then abused that legitimate infrastructure to host or deliver malicious malware to a third-party target.
Proofpoint researchers recently identified a prominent example of compromised SMB infrastructure being utilized by the APT actor TA473 (referred to in open-source intelligence as Winter Vivern) in phishing campaigns from November 2022 through February 2023. These campaigns targeted US and European government entities. In March 2023, Proofpoint published details about TA473’s transmission emails from compromised email addresses. In several instances, these emails originated from WordPress hosted domains that may have been unpatched or unsecure at the time of compromise. Additionally, unpatched Zimbra web mail servers have been exploited to compromise email accounts of government entities. In addition to sending emails via compromised SMB infrastructure, TA473 has also utilized compromised small and medium business domains to deliver malware payloads. Notably, this actor has compromised the domains of a Nepal-based artisanal clothing manufacturer and an orthopedist based in the US tri-state area to deliver malware via phishing campaigns.
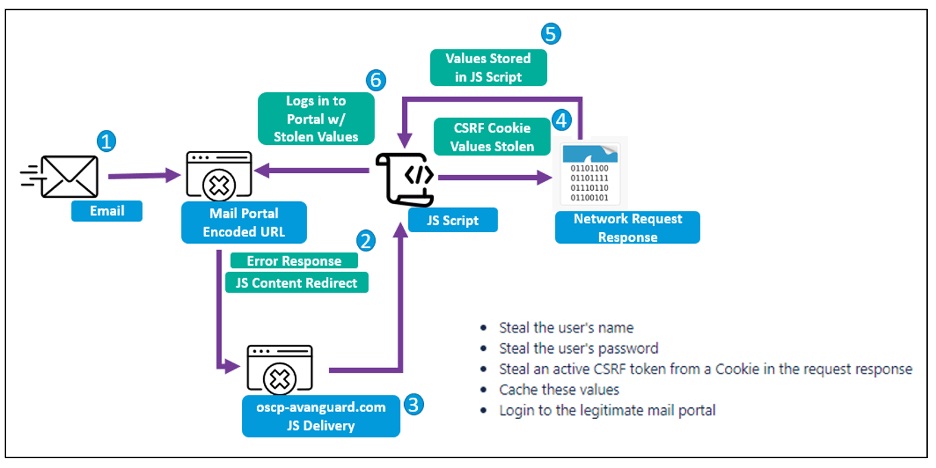
Figure 1. TA473 cross-site request forgery infection diagram.
From January through March 2023, Proofpoint researchers observed regular impersonation of a medium-sized business based in Saudi Arabia within the auto-manufacturing sector as part of a phishing campaign. This credential harvesting phishing campaign, which targeted private email addresses in the United States and Ukraine, is attributable to TA422 (publicly known as APT28). This campaign represents ongoing targeting of Ukrainian entities by Russian GRU-related organizations, but interestingly spoofs an entity within the Middle East to target entities based in the US and Europe. The threat actor included the spoofed address within the “MailTo” field of the email header likely to augment social engineering efforts to appear as the impersonated entity. However, this impersonation via the “MailTo” field has the practical outcome of returning undelivered emails to the legitimate domain being impersonated by the threat actor. Therefore, the unintentional side effect of rejected emails provided Proofpoint researchers visibility into the credential harvesting pages of TA422 that leveraged the following subdomains to host credential phishing pages: 42web[.]io and frge[.]io.
Lastly, our researchers observed a prominent case of APT impersonation in May 2022 when TA499 (also known as Vovan and Lexus, which are personas selected by the threat actors), a Russia-based and state encouraged actor who solicits politically themed video conference calls from prominent pro-Ukraine figures, targeted a medium-sized business that represents major celebrity talent in the United States. TA499 sought to entice a major American celebrity into a video conference call about the conflict in Ukraine by impersonating Ukrainian President Volodymyr Zelensky. Proofpoint was able to attribute this campaign to TA499 based on a series of actor-controlled email addresses and domains that the group used consistently throughout 2022. More details on TA499 and its activity can be found in our recently published blog about the threat actor.
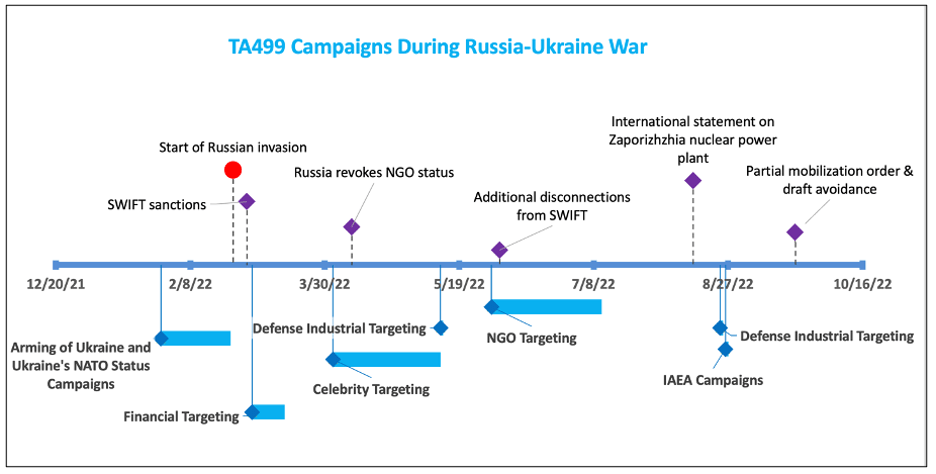
Figure 2. Timeline of TA499 activity in 2022.
An APT Would like to Make a Withdrawal – SMBs Targeted by State-Aligned Financial Theft
Apart from espionage, intellectual property theft, and destructive attacks, financially motivated attacks by state-aligned threat actors remain a persistent threat for the financial services sector. APT actors aligned with North Korea have in past years targeted financial services institutions, decentralized finance, and block chain technology with the goal of stealing funds and cryptocurrency. These funds are largely utilized to finance different aspects of North Korea’s governmental operations. In December 2022, Proofpoint observed a medium-sized digital banking institution in the United States receive a phishing campaign from the North Korea-aligned TA444. The email utilized an email sender address that impersonated ABF Capital to deliver a malicious URL that prompted an infection chain leading to the delivery of the CageyChameleon malware. Proofpoint recently published details on TA444 and its upstart mentality in the latter half of 2022.
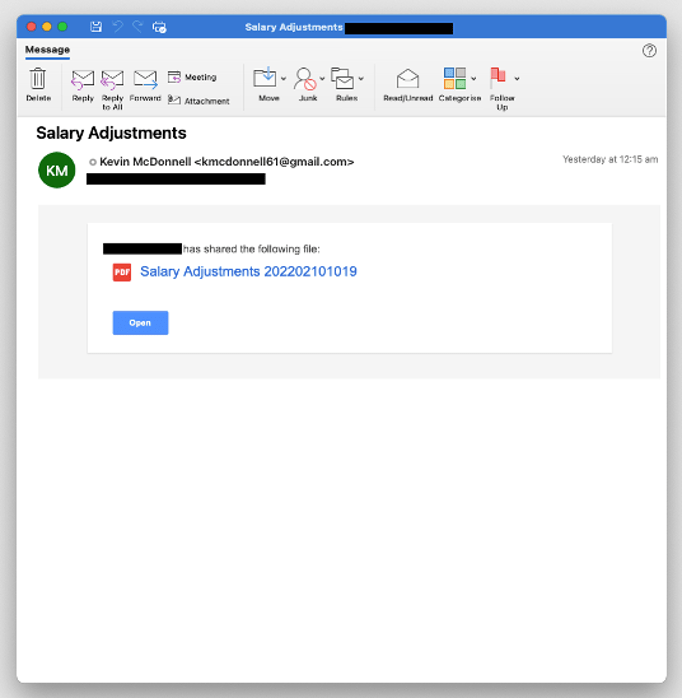
Figure 3. Example TA444 email lure using salary adjustment themes.
Regional Managed Service Providers Increasingly Targeted by Phishing in APT Supply Chain Attacks
The final emergent trend observed between 2022 and 2023 is the increased level of APT targeting of vulnerable regional managed service providers (MSPs) as a means of initiating supply chain attacks. Regional MSPs often protect hundreds of SMBs that are local to their geography and a number of these maintain limited and often non-enterprise grade cyber security defenses. APT actors appear to have noticed this disparity between the levels of defense provided and the potential opportunities to gain access to desirable end user environments. Accordingly, Proofpoint has observed instances of regional MSPs being targeted in phishing campaigns within geographies that align with the strategic collection requirements of APT actors.
In mid-January 2023, Proofpoint researchers observed TA450—publicly known as Muddywater and attributed to Iran’s Ministry of Intelligence and Security—targeting two Israeli regional MSPs and IT support businesses via a phishing email campaign. These emails originated from a compromised email address at an Israeli medium-sized financial services business and included a URL for the cloud hosting provider OneHub. If clicked, this URL delivered a Zip archive that contained a legitimate installer executable file for the remote administration tool Syncro. While Syncro is a legitimate remote administration tool used in businesses, in this context, once installed on the target host, threat actors would be able to utilize the remote administration tool like a remote access trojan and conduct additional intrusion activities, likely through both native tools and proprietary malware.
The targeting of regional MSPs within Israel aligns with TA450’s historic geographic target set. Further this recent campaign indicates TA450 maintains an interest in targeting regional technology providers to gain access to downstream SMB users via supply chain attacks originating against vulnerable regional MSPs.
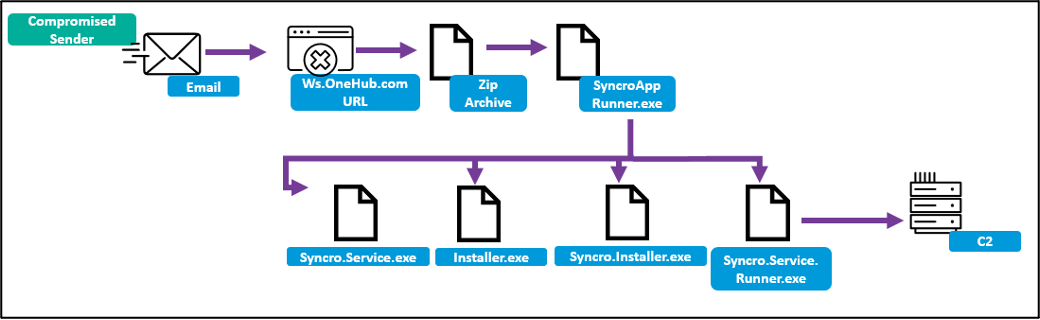
Figure 4. Example TA450 Syncro infection chain circa January 2023.
Conclusion
An increasingly complex APT phishing landscape, at a glance, indicates that threat actors are avidly looking to target vulnerable SMBs and regional MSPs as part of their state-aligned collections requirements. Proofpoint data over the past year indicates that several nations and well-known APT threat actors are focusing on small and medium businesses alongside governments, militaries, and major corporate entities. Through the compromise of small and medium business infrastructure for use against secondary targets, state-aligned financial theft, and regional MSP supply chain attacks, APT actors pose a tangible risk to SMBs operating today. This research supports business proprietors and regional MSP efforts to acquire agile email phishing protection like Proofpoint Essentials, which have an eye towards detecting targeted attacks as well as preventing spam and discarding high volume threats from cybercrime actors.











