In recent weeks there has been an increase of reported Ryuk ransomware attacks across the healthcare industry. CISA, the FBI and HHS have warned against of “an increased and imminent cybercrime threat to U.S. hospitals and healthcare providers.”1 While ransomware actors have leveraged a number of different initial compromise vectors, the primary concern for the wave of recent activity is email threats.
Example Ryuk Ransomware Killchain:
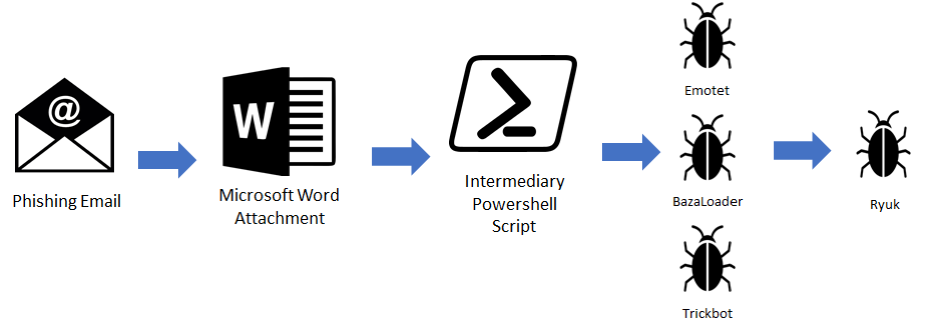
Threat actors send loaders, such as Emotet, BazaLoader and Trickbot/The Trick, through an email phishing campaign that contain links that host the malware or attachments with the malware. Loaders are used as first-stage downloader malware. Its primary purpose is to gain an initial foothold on a system and then download additional payloads as they send out system information to multiple command & control servers at the discretion of the threat actor. In this example, the final payload is Ryuk ransomware (although other variants have been seen, including Conti ransomware) with Cobalt Strike and other tools often being used to escalate privileges within the network as an intermediate step.
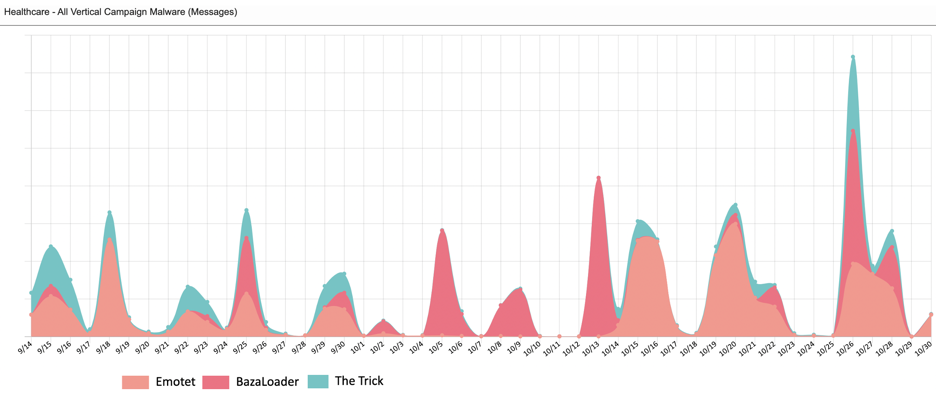
Proofpoint has seen a spike in the last month from Emotet, BazaLoader and The Trick campaigns across all our Healthcare customers, with campaigns sending tens of thousands of daily malicious messages.
Social Engineering Techniques and other TTPs
Several recent campaigns distributing Trickbot leverage common social engineering tricks to attempt to lure the recipient into running the macros that infect the targeted computer with malware. Two examples are below:
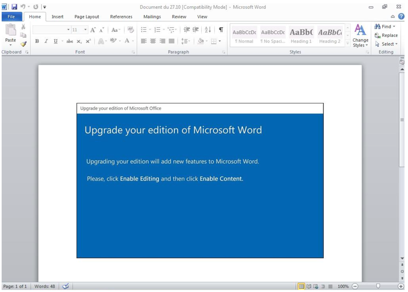
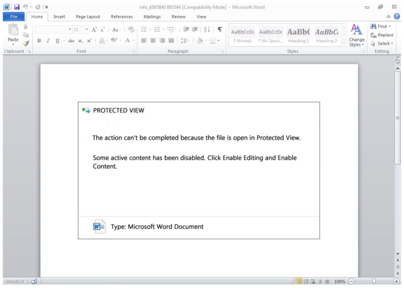
By contrast, BazaLoader campaigns have used messages that contain links to a landing page hosted on Google Docs or PDFs hosted on Constant Contact. The landing page or PDF contains a link to the download of BazaLoader, typically hosted on a compromised website. Recent lures have ranged from employee bonuses to customer complaints to Covid-19.
Protection and Visibility into these Threats
Proofpoint has been protecting customers against email-delivered threats for years. Customers running Proofpoint’s Targeted Attack Protection (TAP) not only blocks single-stage threats (I.e. macros, executables, URLs) but also multi-stage threats (i.e. downloader / droppers like BazaLoader, Emotet and The Trick, which can pull in secondary/tertiary payloads like Ryuk).
While detection and blocking of these threats by TAP has been excellent, as a best practice, Proofpoint recommends careful inspection and remediation of delivered messages that associated with Emotet, BazaLoader and The Trick/Trickbot. Below is a simple three-step process to help you gain visibility into these first stage downloader malware targeting people in your organization:
1. Log in to the TAP Dashboard and go to the search page.
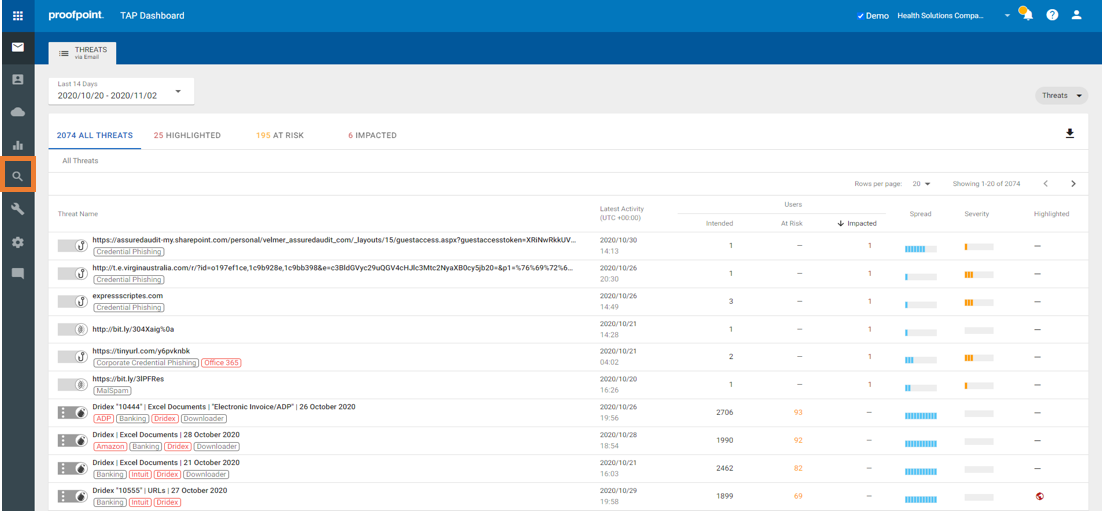
2. Type “Emotet” or “The Trick” or “BazaLoader” in the search bar and click the magnifying glass.
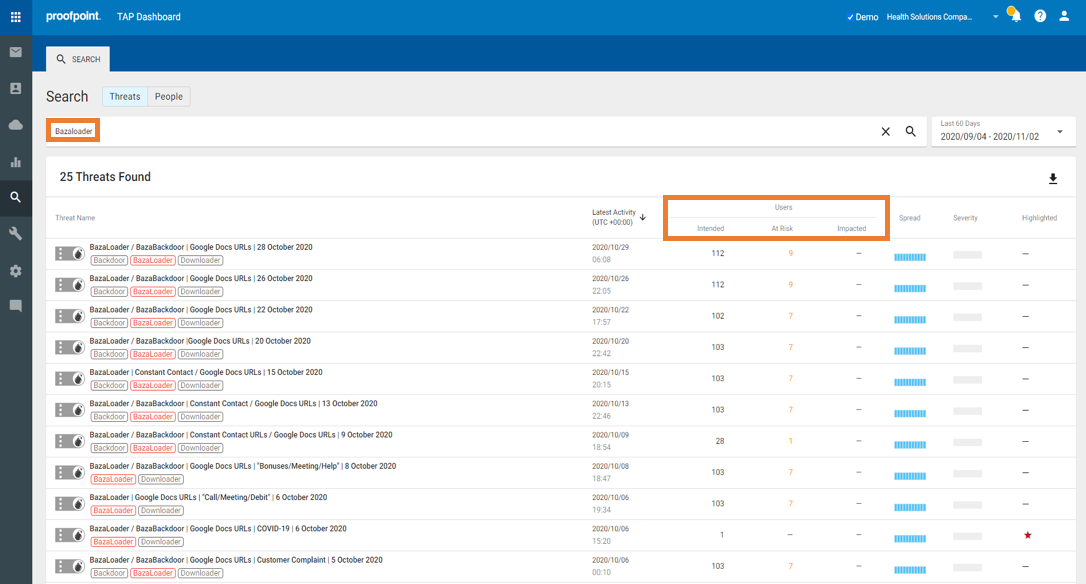
After searching for these malware families, the results provide an overview of all the campaigns that have targeted your organization for the timeframe you selected. It gives a snapshot into who was targeted, who is at risk, and who may have been impacted. This visibility gives great context to show to C-level Executives and the board how you are protecting your organization against these attacks. You can either download the results in a CSV file or simply take a screenshot.
3. Optionally, you can click each campaign that you’d like more details for. In this campaign, you can see that almost 150 messages targeting the organization were blocked. The threat actor used a URL that led to a malicious Microsoft Word Doc for the targets to open and run. The target geography for this campaign was spread across several countries.
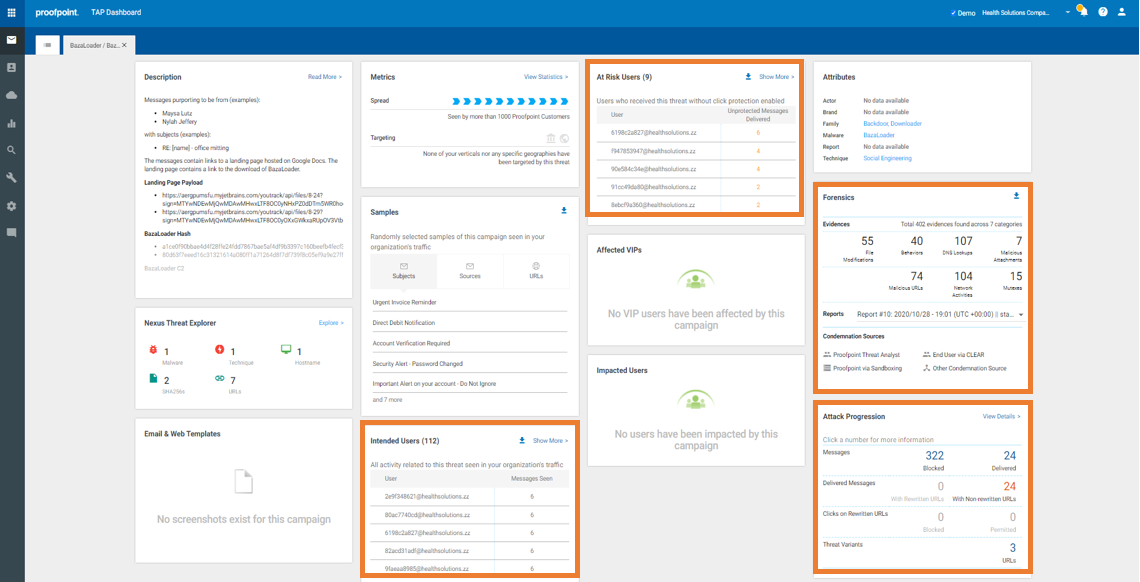
You can also see detailed forensics associated with this campaign, as well as the targeted individuals and any targeted VIP users. Security teams could then reach out to these users, warn them to be extra vigilant and report suspicious messages to their abuse mailbox via forwarding the message or a reporting button. We also recommended providing Security Awareness Training regarding ransomware and the aforementioned tactics of these actors to help end users recognize these threats.
Proofpoint threat researchers continue to closely track these actors and campaigns, and publish frequent updates via the TAP dashboard, TAP APIs, and our Threat Insight blog/social media feeds.
Sources - 1: https://us-cert.cisa.gov/ncas/alerts/aa20-302a











