Today’s cyber-attacks target people, not infrastructure. Threats are constantly evolving to target the weakest point in an organization's attack surface–the end user. In fact, more than 90% of advanced threats target users through email. Not only that, but the growth of remote workers introduces more security risk than ever before as users migrate workflows and data to the cloud, access their personal email and applications from corporate devices, and log in to corporate properties from insecure Wi-Fi networks.
Safeguarding access without negatively impacting the user experience calls for adaptive security controls. Organizations need a comprehensive strategy to prevent and remediate phishing attacks.
Proofpoint and Okta combine leading email security and identity solutions to protect the tools you rely on: Microsoft 365, Google Workspace and your broader IT environment.
People-Centric Visibility for Adaptive Security Controls
Organizations need to protect all users, but not all users are considered equal by attackers. Some people within your organization are more likely than others to be targets of attack because they have access to sensitive information and/or high levels of access. And sometimes your most attacked people are not who you expect. Proofpoint Targeted Attack Defense (TAP) not only blocks threats, but also identifies your most attacked people, or VAPs, and shares that insight with Okta Identity Cloud and Workflows. You can automatically apply adaptive controls to secure those users’ accounts. These include authentication policies such as:
- Password Policy
- Factor Enrollment
- Application Access
- Application Sign-on
- User Roles/Entitlements
This enables you to provide proactive, granular protection when and where it’s needed most.
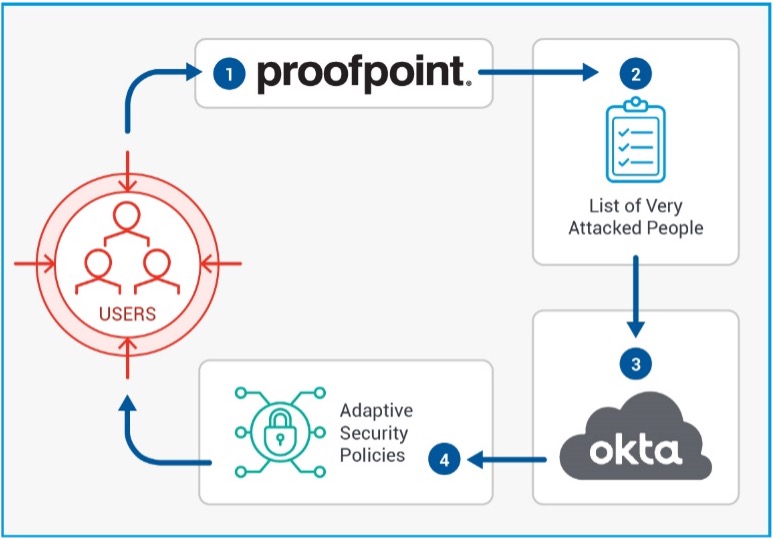
Figure 1 – Adaptive Security Controls for VAPs
Close the Security Loop
Threat actors are increasingly targeting users to gain access to enterprise assets, and security teams are scrambling to manage disparate tools to sift through a never-ending stream of security alerts. Strong email security and identity-centric remediation tools can help enterprises confidently automate incident response to reduce response time and help turn the tide against credential phishing attacks.
Knowing when a user clicks on a malicious link in an email is vital information, but it’s not enough to protect your organization. Proofpoint Threat Response Auto-pull (TRAP) removes the offending message to quarantine. In addition, TRAP follows forwarded mail and distribution lists, creating an auditable activity trail, granting your organization the power to pull back malicious messages after delivery. From there, TRAP alerts Okta. And Okta adds those users to a group subject to stricter multi-factor authentication. The integration automates remediation actions so the security team doest waste valuable time.
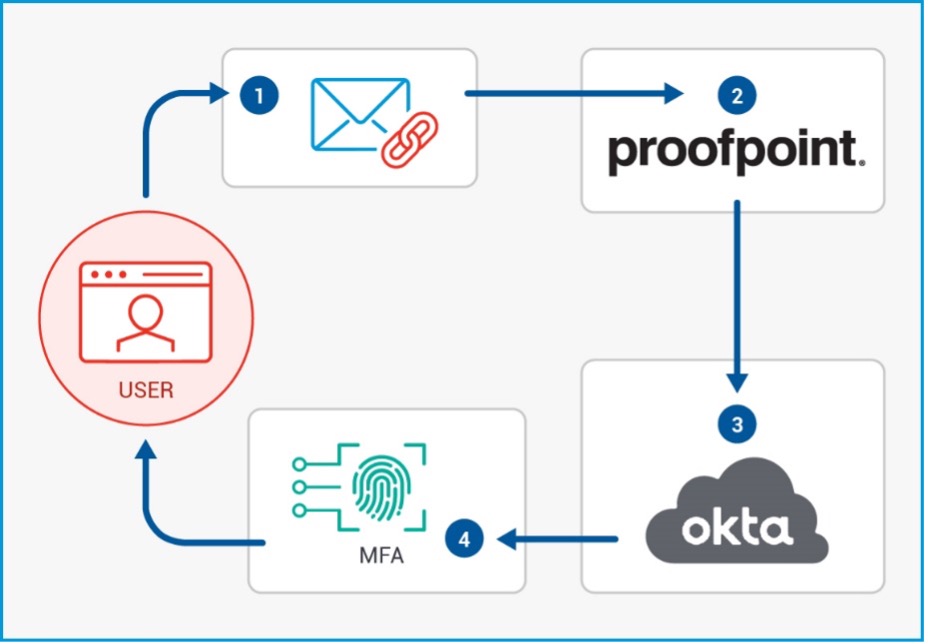
Figure 2 – Close the Security Loop with Proofpoint and Okta
These integrations are simple to implement and can be enabled at no-cost for joint Proofpoint and Okta customers.
We’re excited about our integration with Okta and are eager to discuss it more with you. Visit us at the Oktane21 booth.











