A recent experiment involving 1,700 university students demonstrated that over half clicked through targeted malicious emails. The results weren't much better for malicious Facebook messages, even though the vast majority of the participants claimed they understood the risks associated with clicking links from unknown sources. As students head back to school or leave for college for the first time, the threats they face via email, social media, and on their ubiquitous mobile devices are more than just experiments - they are all too real.
In fact, not only do we regularly observe seasonal upticks in credential phishing related to learning management systems in August and September, but we see a wide variety of threats that span email, social media, and mobile apps of which college students must be particularly aware. Read on to learn the five things to do to ensure cyber safety for students as they return to school.
Beware of Credential Phishing
Credential phishing is a common practice among cyber attackers looking to gain access to banking sites, corporate networks, and other resources. For university students, learning management systems (LMSs) are a particularly common target. While cyber criminals use a number of techniques to steal login credentials for these systems, most craft a fake login page and embed the URL for this page in a phishing email. When users enter their credentials in the fraudulent login page, the credentials are sent to the attackers who use them to access the LMS, obtain additional personal information about the users, or access other services for which students might use the same credentials. After supplying their credentials to the fake page, students are frequently redirected to the real LMS login page so that it appears they simply logged in incorrectly. The image below shows a fake login page for one particular service that uses stolen branding and imagery to trick students.
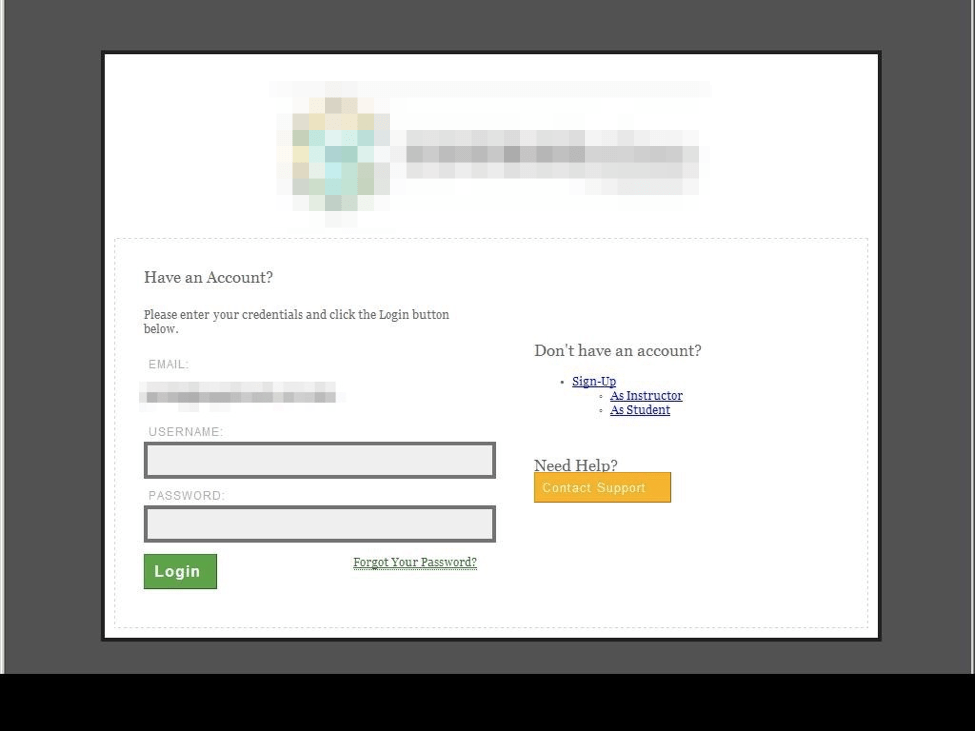
A fake login page using stolen branding to trick users into entering their login credentials
Credential phishing isn't limited to learning management systems. Other university-sanctioned communication and collaboration systems like Outlook Web Access and Google Apps are also frequent targets, as are banking sites in which students may be setting up their first accounts.
While universities can help introduce some internet safety for students with sophisticated email gateways and intelligent firewalls, most schools leave student systems fairly open. The onus thus falls on students to carefully evaluate emails and messages asking for credentials. In most cases, learning management, banking, and other systems will not legitimately request login credentials via email, instead opting for user-initiated actions.
Remember That Malware, Especially Ransomware, is Everywhere
Imagine pulling an all-nighter to finish a term paper then taking a moment to open an email, only to have a malicious attachment install ransomware on your computer, encrypting the term paper and the rest of your work from the semester. And then being asked to pay hundreds or thousands of dollars to get the documents -- as well as the rest of your document and media files -- back. This is a fairly common story with ransomware and college students are often poorly equipped to maintain regular backups or pay increasingly sizable ransoms. Proofpoint’s Second Quarter Threat Summary shows that ransomware is among the most pervasive malware varieties, reaching students via email, social media, and compromised websites – so-called "drive-by downloads" that install malicious software on computers without the user's knowledge as soon as they navigate to the site. At the same time, malvertising drives users to these compromised sites by the millions via ads on Facebook and popular websites with the promise of the latest kitten videos or the top-five ways to ace the next exam.
As with credential phishing, the openness of most student networks means that students are responsible to avoid compromised sites, avoid interacting with emails from unknown senders, and ignore the temptations of clickbait ads. Installing adblocking add-ons for web browsers, keeping antivirus software up to date, and regularly updating productivity and operating system software on their computers all add layer of student cybersecurity and protection against a range of threats.
Understand That Social Media Have Become Major Targets for Attackers
While we traditionally associate phishing attacks and malicious macros with delivery via email, cyber criminals have turned to social media now as well to distribute malware, phish for personal information, and impersonate or defame brands. For most college students, social media is a primary form of communication and the first place they turn for information. However, we regularly observe fraudulent accounts associated with major brands: for example, we recently reported that 167 fraudulent accounts relate just to Pokemon GO, many of which linked to malware or phishing sites.
As the European study of college student behaviour noted above uncovered, students clicked through 42% of anonymous, malicious Facebook messages they received. Every threat that students encounter via email can and has been replicated on social media. Unlike email, however, in which malicious messages are largely unsolicited, students often seek out connections on social channels, making it more difficult to distinguish unknown or malicious senders. Most recently, we have seen an uptick in so-called social media “angler phishing” – attacks in which criminals intercept social media communications with legitimate accounts and begin phishing for credentials or requesting payments by pretending to be associated with legitimate brands.
With cyber safety for students, the same caveats apply to social media as email and the open web:
- Do not interact with people or accounts you cannot verify are legitimate or known
- Avoid clicking through links or opening attachments from unknown accounts
- Ignore advertisements on social media as they may include malvertising
- Go first to corporate or school-based websites and follow links to verified social media accounts before interacting.
Think About Your First Job Interview When Posting Online
Although this seems like Social Media 101, bear in mind that very little that gets posted on social channels is truly private. Screenshots get captured and shared regardless of privacy settings and extended networks are difficult to monitor carefully. Pictures from the latest fraternity party or an extended rant about a professor are not guaranteed to stay within a small circle of friends. Particularly as students enter college, friend lists have a tendency to multiply rapidly as well with new acquaintances and classmates, compounding problems of trust and privacy.
However, it is not just the prospect of a future employer or mentor uncovering unsavoury images that should give students pause. Rather, both cyber criminals and physical attackers make use of social media to design sophisticated phishing attacks or track the location and habits of potential victims. The temptation to share new experiences with widening circles of friends is understandable but common sense should dictate what gets shared online versus what gets talked about in personal conversations.
Keep Mobile Devices Safe - Inside and Out
Mobile devices are a lifeline for students, connecting them to friends, learning management systems, parents, and more. These ubiquitous tools, though, are ready targets for attackers. Mobile malware continues to increase in variety and severity while the sheer amount of data we store in our pockets creates significant vulnerabilities. Phones and tablets now connect us to banking information, store credit cards, and connect to a wide range of services from healthcare to learning management systems. Keeping the devices safe physically as well as electronically is more important than ever.
On the electronic front, side-loading apps and jail-breaking phones open the devices to substantial amounts of malware. It is widely known that there are websites that will let you download any iPhone app or Android app for free, and that there are sites that will let students download all the business apps they might need for school for free. Despite the temptation to get a year’s worth of free games or productivity apps, the use of such sites and services simply is not worth the risk. These sites, whether free or paid, often distribute malicious apps that can steal passwords and personal data, regardless of the operating system running on a device.
In addition, students should be extremely careful about the Wi-Fi networks to which they connect. Whether returning to school or planning to visit parents at Thanksgiving, students should be especially wary of Wi-Fi networks at airports. Public Wi-Fi networks are often set up by criminals and thieves to intercept communications. If they steal email or PayPal passwords, for example, criminals can easily gain access to a wide range of other important accounts. In a mobile-first world, students should think about public Wi-Fi as a potential pick-pocket.
For most students entering or returning to university settings this fall, email is not their primary form of communication, meaning that email-based threats are often poorly understood. They often do not consider the medium relevant until they are required to interact with faculty and administrators via email.
At the same time, students are connecting via social media with new friends and distant friends back home, setting up online banking for the first time, installing new apps for both academic and personal purposes, and otherwise expanding their digital footprints. This presents real opportunities for cybercriminals looking to exploit naivete, inexperience, and new forays into everything from learning management systems to personal banking and online collaboration tools. College students must be extremely vigilant to online threats to avoid opening up personal and financial information to attackers.











