The first quarter of 2017 stood in stark contrast to much of 2016. Where high-volume Dridex and Locky attacks dominated in 2016, threats in Q1 2017 were marked more by their diversity, targeting, and variety than by sheer volume. The quarter ended with a bang, however, when large Dridex campaigns marked the return of high-volume attacks as well as ongoing smaller campaigns that exposed users to threats ranging from information stealers to ransomware to sophisticated SMS phishing.
Our latest threat report reviews the top security trends, techniques, and recommendations for the first quarter of 2017. In the post below, we review our top findings.
Email Trends
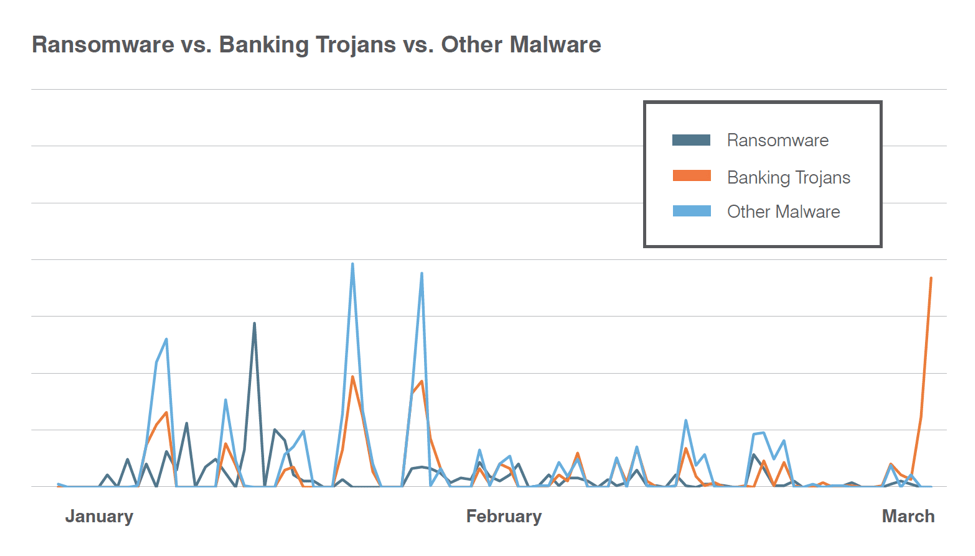
Email is still one of the most common vectors cybercriminals use to attack organizations and individuals, distributing a wide range of malware via URLs, attached documents, and attached archive files. This quarter, we observed a shift in attack types, with 60-70% of daily mail volume containing malicious URLs, oftentimes in hybrid approaches that combined the malicious attachments favored in the last half of 2016. Payloads also shifted: without the massive Locky campaigns of 2016, payloads were much more evenly divided among ransomware, banking Trojans, and other types of malware (Figure 1).
Figure 1: Indexed malicious message volume by malware type
Exploit Kits and Web-based Attacks
Exploit kit activity remains at less than 10% of its Q1 2016 peak. However, we observed social engineering schemes added to both Magnitude EK and the EITest infection chain, suggesting that attackers are looking at new ways to leverage the technology without relying on zero-days and exploits.
Ransomware
Even with Locky ransomware only appearing in smaller, less frequent campaigns, ransomware remains a widespread threat that continues to grow rapidly. New variants are now appearing daily. Despite the dominance of established strains like Cerber and TorrentLocker in large email campaigns, over four times as many new ransomware variants appeared in Q1 versus the year-ago quarter.
BEC
Reply-to and display name spoofing remained the dominant techniques in Q1, but BEC actors moved still closer to an even split between the two approaches. Reply-to spoofing decreased by 6 percentage points from Q4 2016 to 56% of total BEC attacks. Display name spoofing increased 7% to 43% of total BEC. DMARC adoption, which can address many types of spoofing appearing in both BEC and other types of phishing, continued to grow slowly, as did adoption of more sophisticated policies.
Mobile and Social Media
On the mobile front this quarter, we identified 16,000 publishers across vendor-sanctioned and third-party app stores that were distributing malware. Many of these apps were masquerading as legitimate applications. SMS phishing increased and became more sophisticated. At the same time, fraud and cybercrime continued to thrive on social media channels. In particular, support fraud - also known as angler phishing - took advantage of our growing reliance on social media for interacting with brands and businesses.
Proofpoint Recommendations
This report provides insight into the shifting threat landscape that can inform your cybersecurity strategy. Here are our top recommendations for how you can protect your company and brand in the coming months.
Assume users will click. Social engineering is increasingly the most popular way to launch email attacks and criminals continue to find new ways to exploit the human factor. Deploy a solution that identifies and quarantines both inbound email threats targeting employees and outbound threats targeting customers before they reach the inbox.
Build a robust BEC defense. Highly-targeted, low volume BEC scams often have no payload at all and are thus difficult to detect. Invest in a solution that has dynamic classification capabilities that you can use to build quarantine and blocking policies. At the same time, adopt authentication practices to stop supply chain and partner payment fraud.
Protect your brand reputation and customers. Fight attacks targeting your customers over social media, email, and mobile—especially fraudulent accounts that piggyback on your brand. Look for a comprehensive social media security solution that scans all social networks and reports fraudulent activity.
Lock down mobile app environments. Mobile environments increase the risk of rogue apps that can steal critical corporate information. Invest in a data-driven solution that works with your mobile device management (MDM) to reveal the behavior of apps in your environment, including what data they are accessing.
Partner with a threat intelligence vendor. Smaller, more targeted attacks call for sophisticated threat intelligence. Deploy a solution that combines static and dynamic techniques to detect new attack tools, tactics, and targets—and then learns from them.
For a deeper dive into the threat landscape in the first quarter of 2017, download our full report here.