Introduction
What you see: a deluge of security alerts; support-desk calls; malware-infected machines; hints of external data transfers; the lingering digital detritus of cyber attacks within your network. These are trailing indicators of an attack, and they all unfold within the traditional network perimeter.
What you don’t see: malicious emails opened off your network; social media accounts impersonating your brand and surveilling your people; mobile apps that siphon sensitive data from workers’ personal devices on the go. As the way we work changes, these have become leading indicators of an attack—the stage where it is most effectively detected and blocked. And they all happen outside of your network, well beyond the sightline of traditional security tools.
This visibility gap has become one of cybersecurity’s most acute and fastest-growing problems. Even as organizations spend upwards of $100 billion per year [1] on the latest tools, cyber attackers keep getting through. Data continues to be stolen. Breaches keep appearing in the news. And the losses continue to mount.
Today’s business transcends the bounds of traditional network perimeters and connected endpoints. It transpires over email. It flows through social networks. It plays out across all types of mobile devices.
As the modern workforce has moved beyond the network, so have cyber attackers. That’s why today’s threats require seeing beyond the network—into every channel, every device, everywhere your people, data, and brand are.
Unfortunately, most security tools still focus on the parameter and endpoints. This approach may be somewhat useful for detecting threats already inside your environment. But it does little to stop them from getting there in the first place. And worse, it illuminates only the last stage of the attack, leaving you blind to most of the attack lifecycle. Without this insight, you can’t prevent attacks or respond effectively.
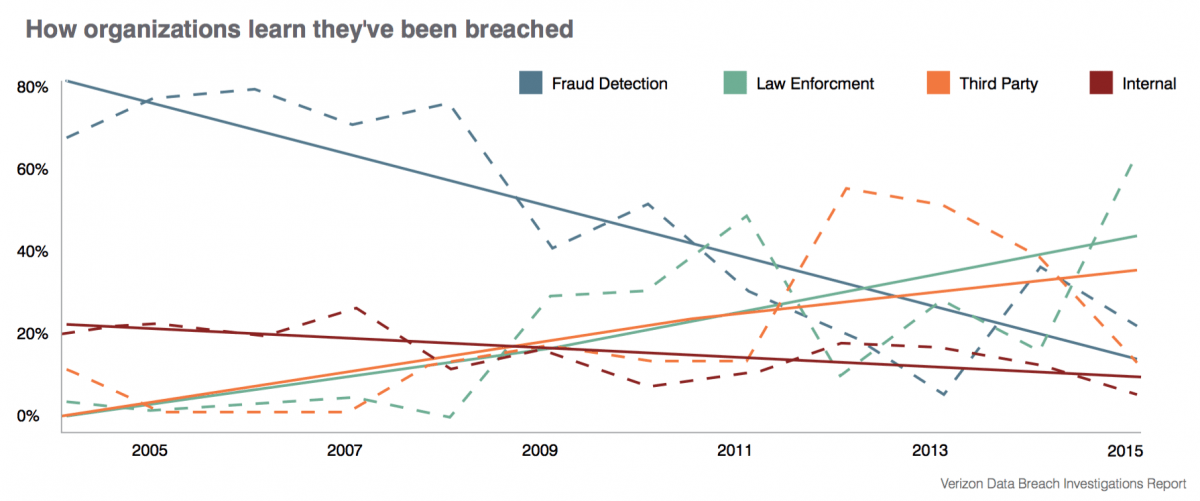
About three quarters of breached organizations learn that they’ve been attacked through an outside party [2]. A whopping 98% didn't discover the breach until a week after the fact [3]. And more than half aren't confident they found the root cause [4].
In other words, when it comes to one of the most catastrophic events that can happen to a company, most never see it coming. And many don’t know what happened even after the fact.
This paper examines the origins of this visibility gap, its consequences, and how to expand your field of view to better protect your people, data, and brand.
MOST ATTACKS BEGIN OUTSIDE YOUR NETWORK
Even when cyber attacks exploit a technical vulnerability, they usually involve people. The holiday 2013 data breach at Target—one of the highest-profile cyber attacks ever—started with a phishing email sent to an employee at the retail giant’s air-conditioning vendor [5].
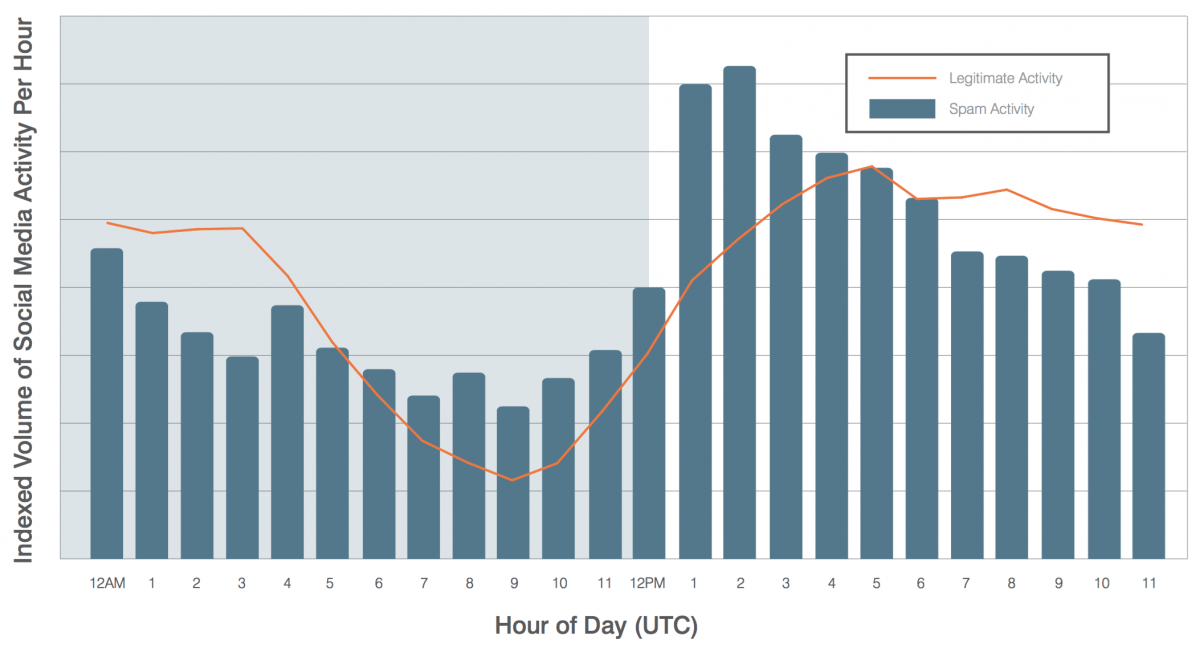
While most attacks still occur via email, social networks and mobile devices are fast becoming popular threat vectors [6]. More than one in every five clicks to a malicious URL takes place off the corporate network through email, social networks, or on mobile devices [7].
The already-massive volume of malicious messages continues to rise. In the first quarter of 2016, malicious email message volume (emails that contain harmful URLs and file attachments) increased by 66% over the fourth quarter 2015—and more than 800% vs. the year-ago quarter [8].
At the same time, brands are using social media more than ever to interact with their audiences. But many of those interactions are hijacked by attackers using similar-looking accounts to spread malware, promote fraud, and steal credentials.
On the mobile front, dangerous apps downloaded from rogue marketplaces affect two in five enterprises [9]. Lured in by free clones of popular games and banned apps, users who download apps from rogue marketplaces—and bypass multiple security warnings in the process—are four times more likely to download an app that is malicious. These apps steal personal information, passwords, and data.
LOOKING FOR THREATS IN ALL THE WRONG PLACES
Conventional cyber defenses focus on hardening the network perimeter, defending the edge of your environment to keep attackers out. This might have made sense in an earlier era, when work took place on company-owned machines, always connected to your network, and inside the four walls of your office.
Today, there’s no “edge” to defend. People work from everywhere, through many channels, and on a range of mobile devices.
Network visibility is important. But a myopic focus on network-based threats gives you only a partial view of the complete threat landscape.
Most attacks start with people, well beyond the control and safety of your network. By the time signs of the attack appear on the network, the attack is well underway and may have already succeeded. The best defenses stop attacks where they start: email, social media, and mobile devices.
Email threats
More than 90% of targeted attacks are launched through email, exploiting the weakest link in the security chain: people.
Nearly a third of people who receive a malicious email will open it—on or off the network. And about 12% click the malicious attachment or link [10].
Someone clicks the malicious file or link within the first four minutes of a typical phishing campaign [11]. Once that click occurs, the user is usually infected within seconds. So if you can’t see attacks that arrive through email, you’re missing most of them.
Social
Social media accounts are easy to set up and rarely policed. It’s no wonder that 40% of Facebook accounts and 20% of Twitter accounts related to Fortune 100 brands are fake [12]. These accounts are designed to steal customer data, damage the brand, manipulate markets, and commit fraud.
In early 2016, Dutch attackers stole account credentials of about 100 Instagram users in Europe who had large followings. Using those credentials, the attacks impersonated the account holders and contacted various advertisers with offers to promote their brand through the Instagram account. Many companies fell for it, giving the attackers tens of thousands of euros [13].
Mobile
Bring-your-own device (BYOD) policies have become the norm in many workplaces. And in those that don’t have a formal BYOD policy, people are bringing their mobile devices anyway.
Mobile-device-management (MDM) vendors have rushed in to help plug this new security risk. These tools help enforce security policies, but on their own, they don’t determine which mobile apps are safe and which ones pose risk. These mobile risks can include:
- Account takeover
- Leaked data
- Hijacked devices
- Privacy violations
- Adware
- Risk to your brand
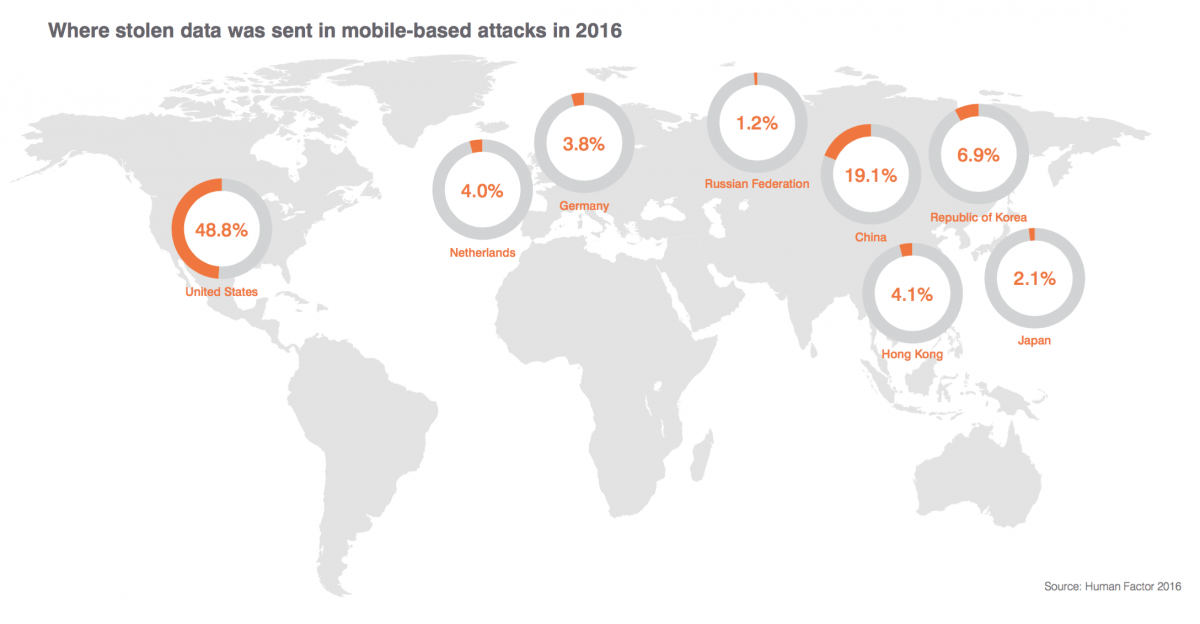
Our analysis of authorized Android app stores discovered more than 12,000 malicious mobile apps— capable of stealing information, creating backdoors, and other functions—accounting for more than 2 billion downloads. Malicious apps send data to servers in 56 countries outside the U.S.; China is the top overseas destination [14].
Malicious apps are an attractive vector for attackers. Unlike email-based campaigns, which rely on spam messages to millions of users, an app placed in a single store can reach millions of potential users.
Another mobile threat is riskware. These are apps that, while not always overtly malicious, engage in risky behavior. Riskware is invisible to mobile device management tools, which is why they’re found on so many employee- and company-owned mobile devices. These apps exhibit a wide range of dangerous behavior that leads to leaked sensitive enterprise data, stolen credentials, or ex ltrated data—often used to target employees in future attacks.
THE COST OF TUNNEL VISION
This lack of visibility increases your risk, makes security incidents more difficult to resolve, and leads to more costly cleanups.
Greater risk
You can’t secure what you can’t see. As more attacks originate off your network, a network-fixated defense will miss an ever-growing percentage of them. Network-based detection tools see only the final stages of cyber attacks, when the attacker already has a foothold in your environment.
By the time the threat is detected on the network, the attack may have already succeeded.
Delayed detection
Attackers can access compromised systems for months before their victim detects the attack. Financial firms, which deploy some of the most advanced network tools available, take an average of 98 days to discover an attack [15]. The retail sector fairs even worse, at 197 days [16].
Delayed detection means the attacker has more time to spread laterally across your environment, steal more data, and cause more damage.
Costlier cleanup
Network-only visibility slows the process—and in turn raises the costs—of resolving security incidents. Most attacks begin outside of the network perimeter. Without visibility beyond the network, tracing them to their source and knowing their full scope is difficult.
Cleaning up and remediating a cyber attack takes an average of 31 days at a cost of $20,000 per day [17]. The more PCs the attack has had time to infect, the costlier they become.
Ponemon Institute outlined six factors that contribute to the costs of a data breach beyond the value of lost data [18]:
- Investigating the root cause of the data breach
- Determining the probable victims
- Organizing the incident response team
- Building a communications and public-relations strategy about the breach
- Preparing notice documents and other required disclosures to victims and regulators
- Rolling out call center procedures and specialized training
All of these are more difficult and expensive without the forensics and insight you get only when you look beyond the network.
CONCLUSION AND RECOMMENDATIONS
Aware of today’s cyber threats, organizations are investing millions into new technologies to detect, block, and resolve attacks. Unfortunately, most of these tools are looking in the wrong places.
Organizations must look beyond the network. We recommend a three-pronged approach to bridging the visibility gap:
-
Identify key blind spots. Determine whether your current defense is in the flow of today’s attacks. That means email, social media, and mobile devices.
-
Create a plan to close the gaps. The specifics of this plan will hinge on the size of your organization and security team. It may include modeling your return on investment and potential impact to your security operation.
-
Consider solutions to improve visibility. The best tools will not only detect threats beyond the network but tie into your incident response tools. Visibility into today’s threat vectors enhances your ability to respond to current threats and makes the next one even easier to stop.
To learn more about the risks you may not be seeing, schedule a free Proofpoint threat assessment. Our simple, non-invasive process will help you assess your security posture. You’ll get a clearer picture of threats and vulnerabilities in your environment.
Our email risk assessment shows you who is being targeted and how (ransomware, credential phishing, BEC, and so on).
Mobile
Our mobile defense risk assessment shows you what mobile applications your users have on their phones and what each of those apps is doing.
Social
Our social risk assessment provides a snapshot of all accounts associated with your brands — corporate, unauthorized, and fraudulent.
Data Discover
A Data Discover risk assessment shows you where sensitive data lives within your environment.
Click here to schedule an assessment.
[1] Steve Morgan (Forbes). “Worldwide Cybersecurity Spending Increasing to $170 Billion by 2020.” March 2016.
[2] Verizon. “Data Breach Investigations Report.” April 2016.
[3] Ponemon Institute. "The Post Breach Boom." February 2013.
[4] Ibid.
[5] Krebs on Security. “Email Attack on Vendor Set Up Breach at Target.” February 2014.
[6] Proofpoint. “Quarterly Threat Summary: Jan-Mar 2016.” April 2016.
[7] Proofpoint. “The Human Factor 2016.” February 2016.
[8] Proofpoint. “Quarterly Threat Summary: Jan-Mar 2016.” April 2016.
[9] Ibid.
[10] Verizon. “2016 Data Breach Investigations Report.” April 2016.
[11] Ibid.
[12] Proofpoint. “The State of Social Media Infrastructure.” 2014.
[13] Proofpoint. “Instagram Attack Spotlights Blended Social Media and Email Trend.” March 2016.
[14] Proofpoint. “The Human Factor 2016.” February 2016.
[15] Ponemon Institute. “Advanced Threats in Financial Services—A Study of North America and EMEA.” May 2015.
[16] Ponemon Institute. “Advanced Threats in Retail—A Study of North America and EMEA.” May 2015.
[17] Kelly Jackson Higgins (InformationWeek). "Cost of a Data Breach Jumps By 23%." October 2014.
[18] Ponemon Institute. “2015 Cost of Data Breach Study: Global Analysis.” May 2015.