As we approach the end of 2021, ransomware attacks continue to make global headlines and wreak havoc on organisations across the globe. (One incident even resulted in an alleged ransomware-related fatality). And unfortunately, we can expect ransomware to persist in 2022 and likely beyond as one of the primary threats facing organisations. That means if you don’t already have one, you’re going to need to create a ransomware defence strategy.
First, you’ll need a framework. During my time as a Gartner analyst, I spent a lot of time talking with clients about incident response strategies and how to get started or improve on their incident response processes. One question I’d often hear raised early on was, “Which framework should I follow?” or, worse yet, “Should I develop my own framework?”
Security frameworks are meant to be followed—not rewritten or revised. (Save that for your policies, guidelines and procedures—the specifics.) And whether you choose to follow ISO 27001 or the NIST Cybersecurity Framework, select one—and only one.
Please don’t try to cherry-pick the “best of” from multiple frameworks. Select exactly one framework. Then, tailor your organisation-specific policies, guidelines and procedures to match your needs. The same thing holds true for incident response frameworks. Both ISO 27035 and NIST 800-61 are foundational frameworks. Choose one of them and start building around it.
Get more insight into your users and the threats they face
Whether you choose NIST versus ISO, the next critical step toward creating your ransomware defence strategy is preparation and the need to “shift left”, meaning spending more time, money and effort on preparation activities.
The 2021 Unit 42 Ransomware Threat Report from Palo Alto Networks notes that about 75% of ransomware initial access begins with email protocols such as SMTP (45.0%), IMAP (26.5%) and POP3 (3.8%).

Figure 1. Research from Unit 42 finds most ransomware attacks begin with email phishing
There’s a lot that goes into preparation, some of which is certainly technology controls. Much more important, however, is understanding your organisation. The NIST Cybersecurity Framework can help on that front, as it “provides a common language for understanding, managing, and expressing cybersecurity risk to internal and external stakeholders”. The Framework Core (in Section 2) covers a method to map activities to achieve specific cybersecurity outcomes.
Ransomware operators “shifting left”, too
Ransomware attacks have already invested in “shifting left” and strengthening the relationships between threat actors, malware developers and ransomware operators.
In the past, ransomware operations had to be built from the ground up. Ransomware developers were known to write their own encryption code and now they rely on readily available options that are harder to crack. Their delivery methods have also advanced from traditional email phishing to more sophisticated spear-phishing campaigns.
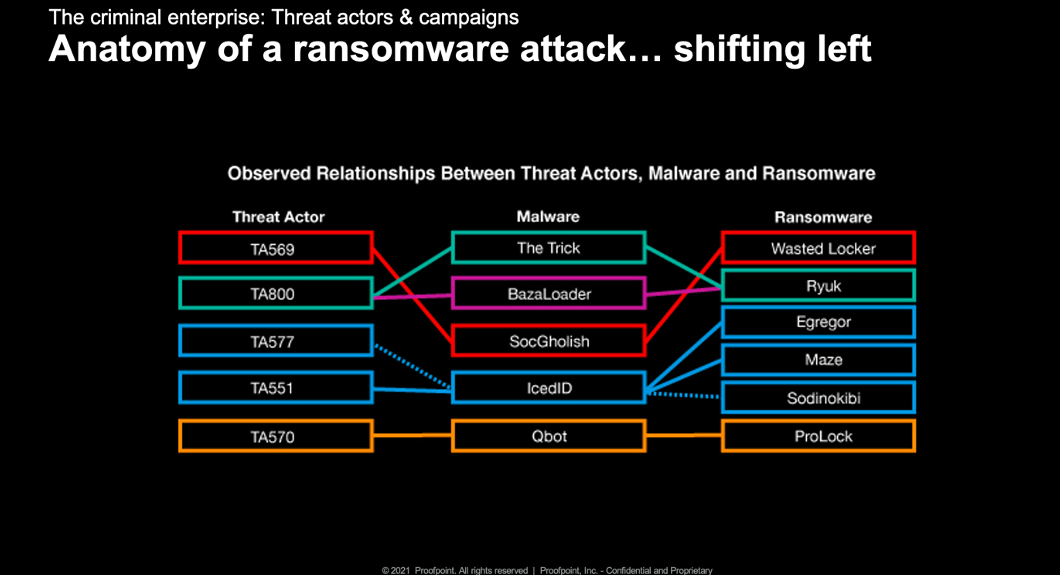
Figure 2. Observed relationships between threat actors, malware and ransomware
First stage malware like The Trick, Dridex and Buer Loader allows threat actors to gain initial access into an organisation. Once they have this access, they can sell it to ransomware operators, allowing for data theft and encryption operations. It’s common for ransomware operators to purchase this access from independent groups who infiltrate major targets.
Several threat actors have become initial access brokers, having moved from spreading banking Trojans to selling their access to other groups. These access facilitators distribute their backdoors via malicious links and attachments sent by email. These groups will typically escalate their privileges to administrative levels and more broadly compromise an environment before launching the ransomware.
Why is ransomware on the rise? Cybercriminals have created scale and are now able to offer programs like ransomware-as-a-service. Being able to pick services off the shelf like Locky, CryptoLocker, and TeslaCrypt have made it easier for groups to take up cybercrime.
Proofpoint tracks multiple threat actors who act as initial access facilitators or likely ransomware affiliates. In 2020, we identified 48 million messages within campaigns that would potentially lead to a ransomware outcome. Many threat actors have moved to more “selective” targeting, conducting reconnaissance before sending out their attacks.
Tools to support an effective ransomware defence strategy
Technologies like Nexus People Risk Explorer from Proofpoint can help you gain a better organisational understanding of your users, and explicitly show you which users, departments or groups are vulnerable, attacked or privileged. This improved organisational understanding can help you make fact-based security decisions. (Nexus People Risk Explorer is free to all Proofpoint customers who have one of our Proofpoint bundles.)
Also, Threat Actor Reporting is available as a free upgrade within Proofpoint Targeted Attack Protection (TAP). By combining Threat Actor Reporting with Nexus People Risk Explorer, you can begin to understand who within your organisation is under attack and why, and then plan a proactive mitigation strategy for those attacks.
Our CISO Dashboard, which is available to Proofpoint Security Awareness Training customers, provides an additional lens into your user community. It can help you identify users who may need additional layers of protection, such as a more stringent policy for web browser isolation to protect from malicious downloads like loaders and other malware components of complex, multistage ransomware attacks.
These key points of visibility and insights into users and the threats that they face are critical to helping you develop an effective ransomware defence strategy.
Learn More
For more information on ransomware, check out this Proofpoint blog post, “Ransomware on the Rise—Key Trends and Tips You Need to Know”.
Also, subscribe to the Proofpoint blog, so that you’ll never miss a post.











