(Updated on10/29/2020)
This is the first of two posts addressing the risks inherent with Root User access. Make sure you check Part 2: Risky Scenarios Uncovered.
Customer data, employee records, financial files — admins need access to all of it to do their jobs. They have broad access to sensitive corporate data, as well as critical systems and servers. We trust admins with the keys to the IT kingdom, but are we doing enough to ensure the safety of our IT assets at the same time?
Whether intentionally or unintentionally, admins are often at the heart of enterprise security breaches. Their login accounts are prime targets for hackers: administrative credentials are gold. Not only do admins have access to some of the most sensitive information in the company, they often use a generic admin account to log in. Therefore, if a hacker compromises an admin account, it’s easy to steal data, cause damage, cover their tracks and leave without a trace.
But it isn’t only hackers we need to worry about. Within an enterprise, privileged users have been known to become disgruntled and vengeful, posing a huge threat to your organization if they choose to act maliciously or for profit. You don’t need to be a hacker to steal data, corrupt code or inflict harm on a server. Furthermore, there is plenty of opportunity for even loyal, non-malicious admins to make honest mistakes that expose data or harm systems.
The Unix/Linux Root User Danger
Because of the high risk associated with admins logging in as the root user (or changing identity to root after logging in during a session) in Unix/Linux systems, it is considered a best practice to restrict access to the root account. Instead, sudo is used to grant administrators root-level permissions to execute particular commands and scripts, when needed. This allows admin users to do their jobs without needing to know the root password or gain full root permissions.
There are, however, significant risks with the sudo approach: admins can abuse the root-level permissions they have received for one purpose to perform unrelated and nefarious activities that are very difficult to detect. For example, an admin might receive sudo permissions to edit a file in vi and then break out of vi to execute a destructive system command with root permissions, like this:
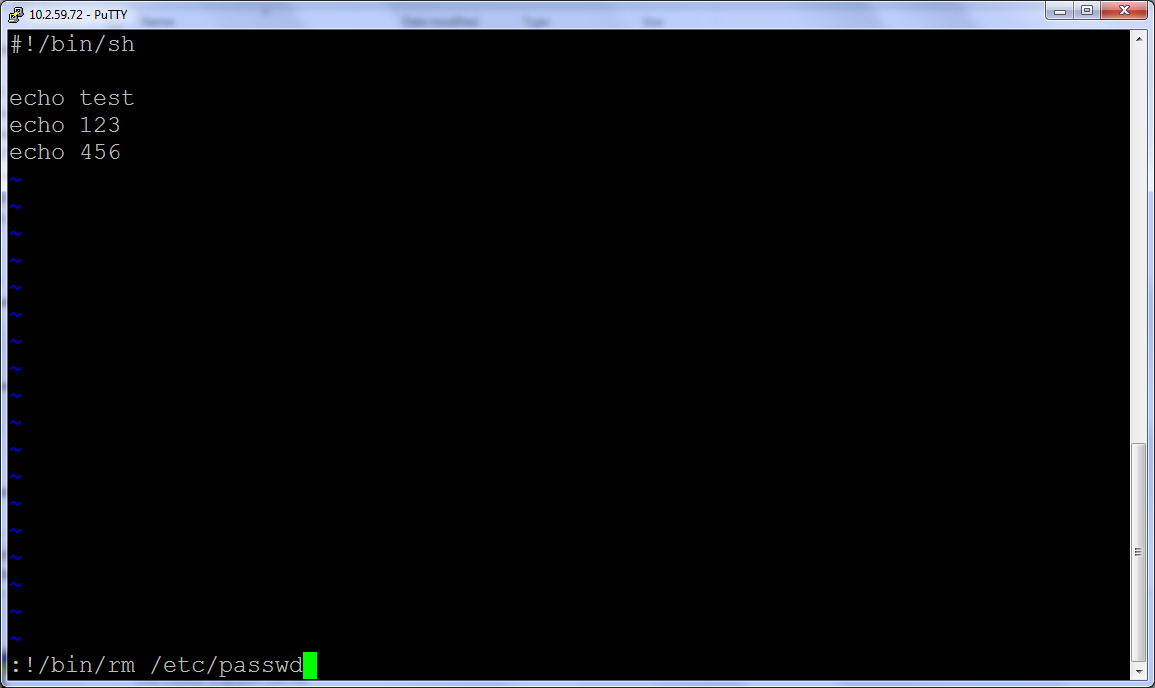
Other examples include being able to open a full shell with root-level permissions (allowing him to run unauthorized commands, scripts or applications without further obstacles), or when given permission to run a particular script, he could actually modify that script to perform actions which may harm systems or expose sensitive data.
On the one hand, it is always going to be necessary to grant sudo permissions to admins so that they can do their jobs. On the other hand, we see that there are great risks associated with this. So how does the organization protect itself?
The Solution: User Activity Monitoring
The answer lies in monitoring all user activity on Unix/Linux machines, especially users with root or sudopermissions. When security staff has visibility into exactly what admins are doing with their privileged permissions, the organization is equipped to detect and prevent data breaches or system corruption in a timely manner. Additionally, the ability to review complete user activity logs and session videos after an incident is an unparalleled tool for fast root cause analysis and forensics investigations:
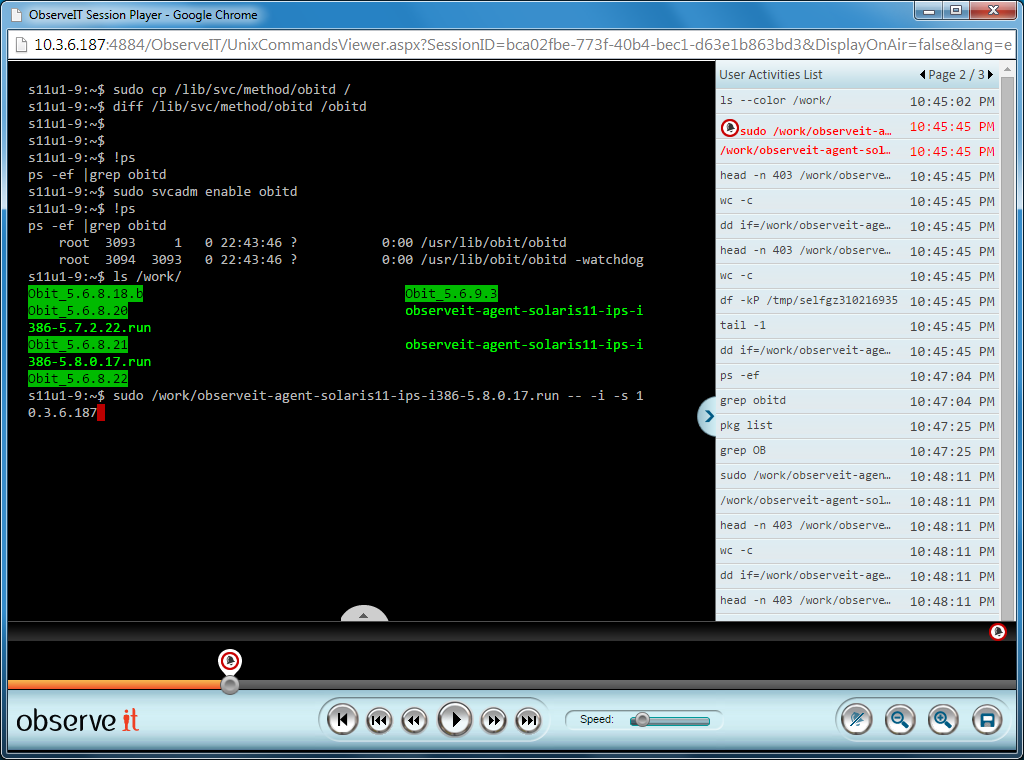
One of the challenges of this kind of monitoring in Unix/Linux systems is that many important and risky user actions are not run directly from the shell. Instead, they can be executed “behind the scenes,” as parts of scripts or aliases, for example. It is for this reason that it is critical to record both SSH input and output, as well as the actual commands executed, the resulting underlying system calls and even the specific resources affected.
Furthermore, all user actions must be tied back to the actual user who originally began the session, even if an su orsudo command was later invoked. It is critical to be able to follow the trail of users who logged in directly and then changed to root access later in the session.
(As a side note, this is one of the weaknesses of password vault solutions. While password vaults hide the root password from admins using them, they do not have any way to detect admins logging in with their own credentials and then subsequently gaining access to a root-level shell from within their session via sudo, a home-grown setuidprogram or the like.)
Real-time Alerts
Even with a fantastic user activity monitoring system in place, there is too much user activity to track manually. Most organizations do not have the resources to monitor every action of every user (even just admin users) on a daily basis. This is what makes it essential to deploy real-time alerts capability.
When such activities are detected, the system alerts security staff so that they can investigate. Instantaneous access to session video replay and plain-English logs of the commands and scripts run (including the underlying system commands executed by those commands/scripts and the system resources touched by them), enables a security officer to immediately determine if the user action that generated the alert was a normal administrative activity or one that represents a danger to the company.
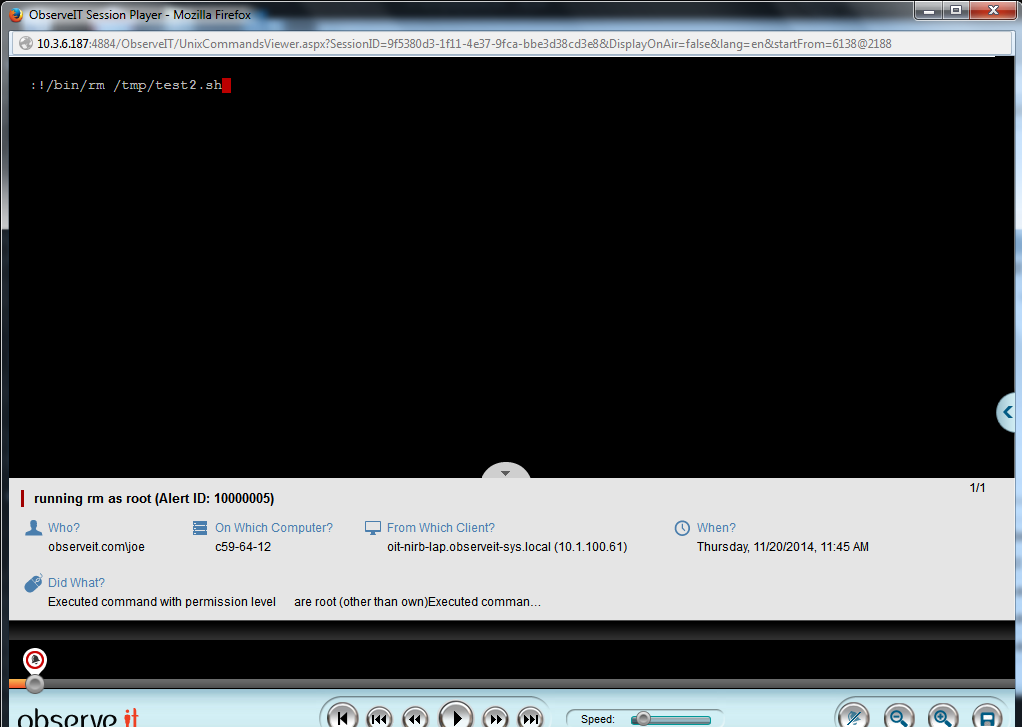
Let’s look at an example: the user activity monitoring system is configured to generate an alert anytime someone who initially logged in to a session without root permissions runs the rm command with root permissions. This is how this alert rule appears in our Proofpoint ITM user activity monitoring system:
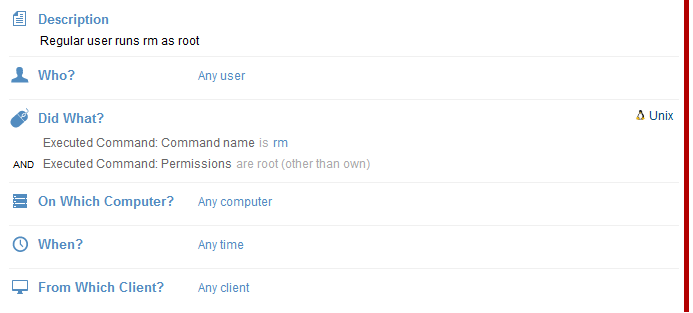
Whenever an alert based on this rule is generated, the security officer can review the session in real-time (or anytime afterwards) to understand exactly what the user was doing and if the action was appropriate or not. This is what the generated alert looks like, presenting the key details of the action:
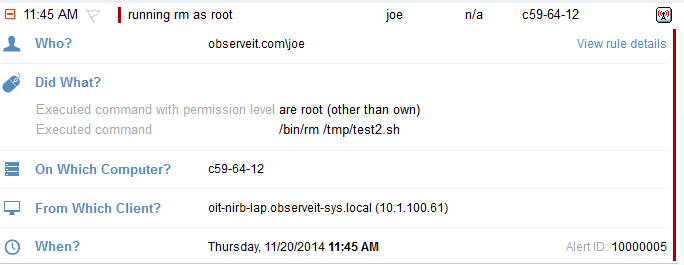
If the security officer wants to watch the session recording, he can click the video icon (seen at the top-right in the above image) which launches the session video from the moment this action was performed:
Companies don’t have many options – they must give Root User access to certain individuals. This level of control puts critical systems at risk. User activity monitoring is a critical solution that reduces the chance of a breach by providing transparency to IT managers.
Check back next Tuesday for Part 2: Uncovering Risky Scenarios.
In 2015, the biggest security risk to your company will be your users. Understanding this risk and making sure your security solutions are equipped to meet it will be vitally important. If you are looking to improve how your company meets user based threats, check out an EMA report: Mitigating User-Based Risks.











