Proofpoint Security Awareness has long been at the forefront of innovative awareness strategies. In today’s complex threat landscape, a human-centric strategy has never been more important. And we have never been more dedicated to creating a program that helps users change their behavior.
In this post, we share a few enhancements that show how committed we are to helping users transform their behavior. We cover a key educational campaign and outline the benefits of several new functional enhancements within four focus areas.
1: Keeping users engaged
There are two recent and upcoming enhancements in this focus area.
We launched the Yearlong campaign: Cybersecurity Heroes
We released this pioneering, comprehensive educational program late last year. It provides an ongoing, curriculum-based approach to cybersecurity training. It is a testament to our belief in the power of continuous learning and helping users change their behavior.
The Cybersecurity Heroes campaign covers an array of key security topics in detail every month. Here are a few examples:
- Elements of data encryption
- Intricacies of strong password protocols
- Deceptive nature of ransomware
Long-term training schedules can be an administrative burden. That’s why we’ve made this training available through stand-alone monthly modules. This flexibility helps ease administrative workloads.

An article from the Cybersecurity Heroes campaign.
QR code phishing simulations will launch soon
In the second quarter of 2024, we will be releasing QR code phishing simulations. They are our proactive response to a novel and alarming trend. Recent intelligence from industry-leading analyses, including an eye-opening blog on QR code phishing from Tessian, underscores the urgent need for education. QR code phishing attacks are on the rise. Yet, 80% of end users perceive QR codes as safe. This highlights a dangerous gap in threat perception.
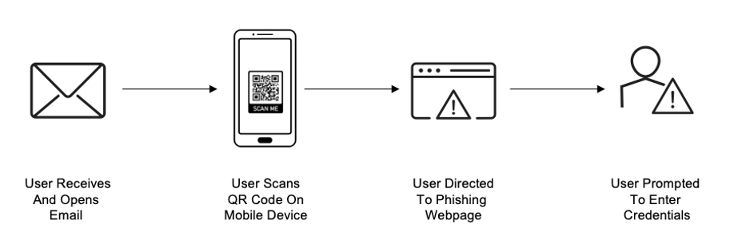
How a QR code phishing attack works.
Our new simulations will provide administrative visibility into which users are most vulnerable to an attack, as well as a dynamic environment for users to hone their threat detection abilities in alignment with real-world scenarios. They are based on our threat intelligence and designed to challenge and refine user reactions. With an understanding of who is most at risk and how users may react to a QR code phishing attack, administrators will be able to design a program that is tailored to each individual, resulting in maximum learning comprehension and retention.
QR code phishing simulations will be available in the second quarter of 2024.
2: Enhancing how people learn
We want to help businesses maximize their users’ learning comprehension and behavior change. One recent enhancement in this focus area is the integration of “Phish Hooks” into Teachable Moments. It was released in late 2023.
Here’s how it helps users learn better and retain what they’ve learned.
“Phish Hooks” is now integrated with Teachable Moments
This enhancement helps users understand why a phishing simulation would have been an actual threat. Users get immediate and clear feedback so that they know what to look out for next time.
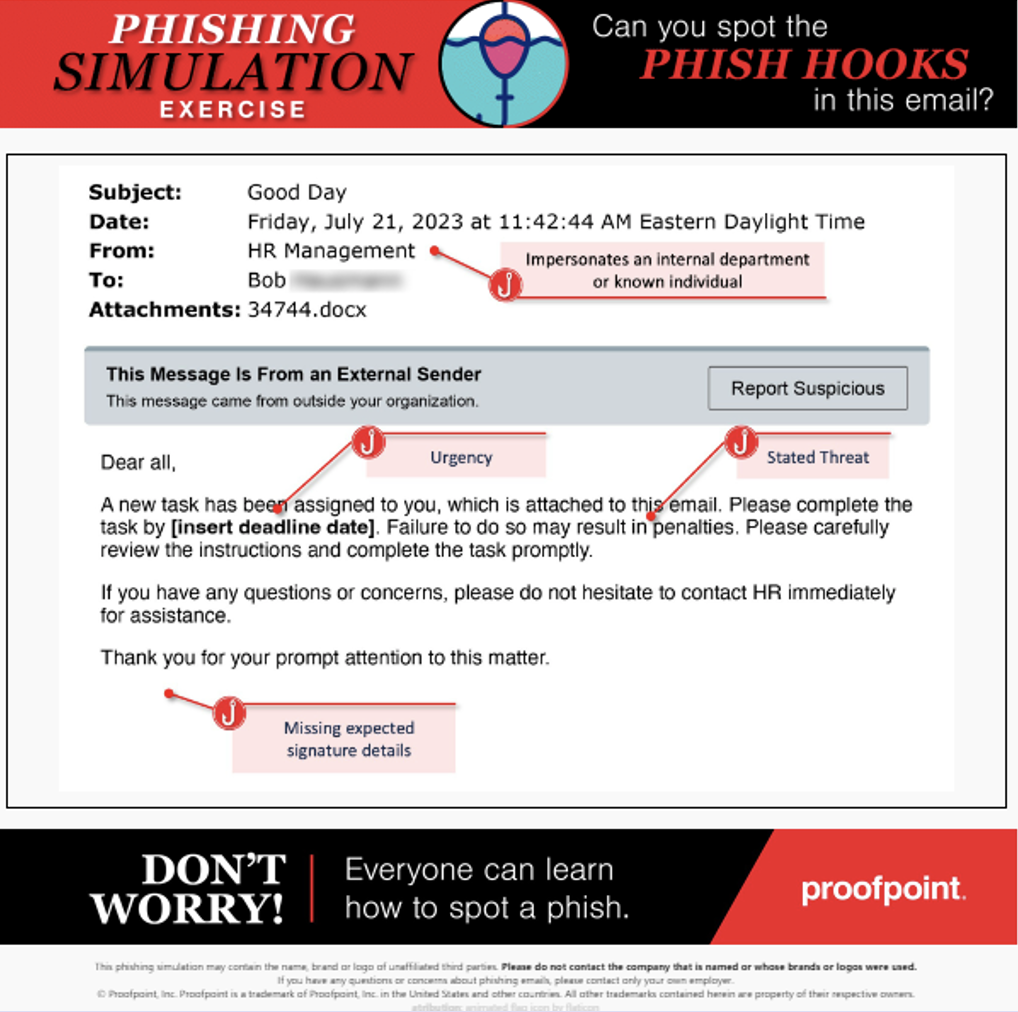
A view of Teachable Moments with “Phish Hooks.”
By dissecting the anatomy of a phishing attack, we can give a big boost to a user’s ability to critically assess an attack. That, in turn, helps them to improve their understanding and retention of safe cybersecurity behaviors.
3: Gaining visibility into vulnerable users
Proofpoint recognizes that security administrators play a critical role in orchestrating awareness efforts. That is why we refined our Repeat Behavior Report. It’s designed to help administrators identify the users who can benefit from targeted training about phishing risks. Here’s how.
The Repeat Behavior Report is more detailed
This enhancement gives you actionable insights that can help you identify vulnerability trends. To this end, the report now provides a more detailed view of how users engage with phishing simulations. For example, you can now see which users repeatedly click on links. You can also see which users repeatedly fail simulations by continually entering their credentials into the fake website that they are directed to.
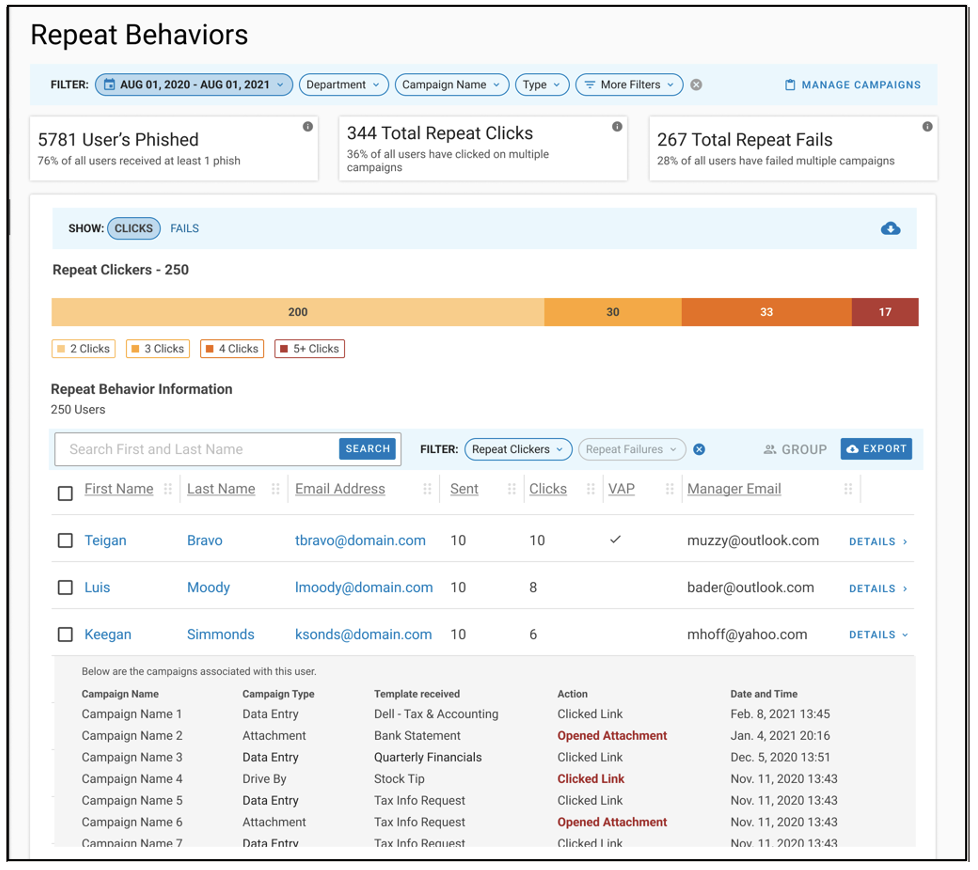
An example of the latest Repeat Behaviors Report.
With these insights, you can customize curriculums for users who are more likely to take risky actions. This approach ensures that each user has an educational journey that is relevant and impactful and addresses their unique areas for growth.
4: Saving administrative time and resources
There are four recent and upcoming enhancements to this focus area. We’ve grouped them together into two themes because they are interlinked.
Program customization is now more efficient
Security practitioners often deal with a lot of manual work. We wanted to streamline their processes. These strategic enhancements are designed to minimize the time and resources that are required to build and adapt educational programs within our solution.
Adaptive Groups and Adaptive Assignments let you automate the process of user group creation, user enrollment and curriculum allocation.
Adaptive Groups
Now, you can automatically build groups based on user-specific attributes that are pre-defined within your Identity Management directory. Departmental affiliations, organizational roles or date of hire are some examples you might use.
Let’s say you create an Adaptive Group based on an attribute like department. When you add a new user to the corresponding department, that user will be added to the Adaptive Group automatically. Manual management of group membership is no longer necessary. So you are free to focus on more strategic work.
And here’s a teaser. Looking ahead, Proofpoint plans to further enhance Adaptive Groups so that you can build groups automatically based on user risk. You will be able to derive user risk profiles from integrations with Proofpoint Targeted Attack Protection (TAP) and the Nexus People Risk Explorer. And within these integrations, you can create groups automatically based on:
- Very Attacked People™ or Top Clicker groups tracked within TAP
- Risk Profile or Target Group within Nexus People Risk Explorer
Adaptive Assignments
You can now add users automatically to a training assignment for immediate enrollment. Say that you create an assignment, and you enroll an Adaptive Group—such as a predefined group like “Accounting and Finance”—to the assignment. When you add a new user to this group, they are automatically enrolled into the assignment. There is no need for you to take any manual action.
You can count on maximum user engagement, too, because the audiences you want to target will automatically receive the education that is most relevant to them.
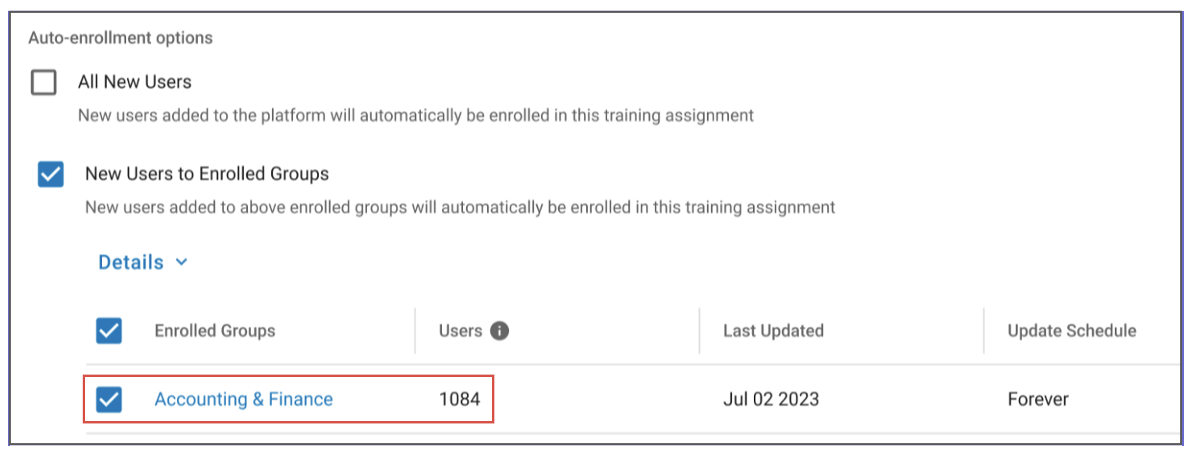
A view of the integration between Adaptive Groups and Adaptive Assignments.
Learning modules and phishing simulations are now easier to access
With these enhancements, you can now enjoy quicker and more intuitive access to the wealth of our educational resources.
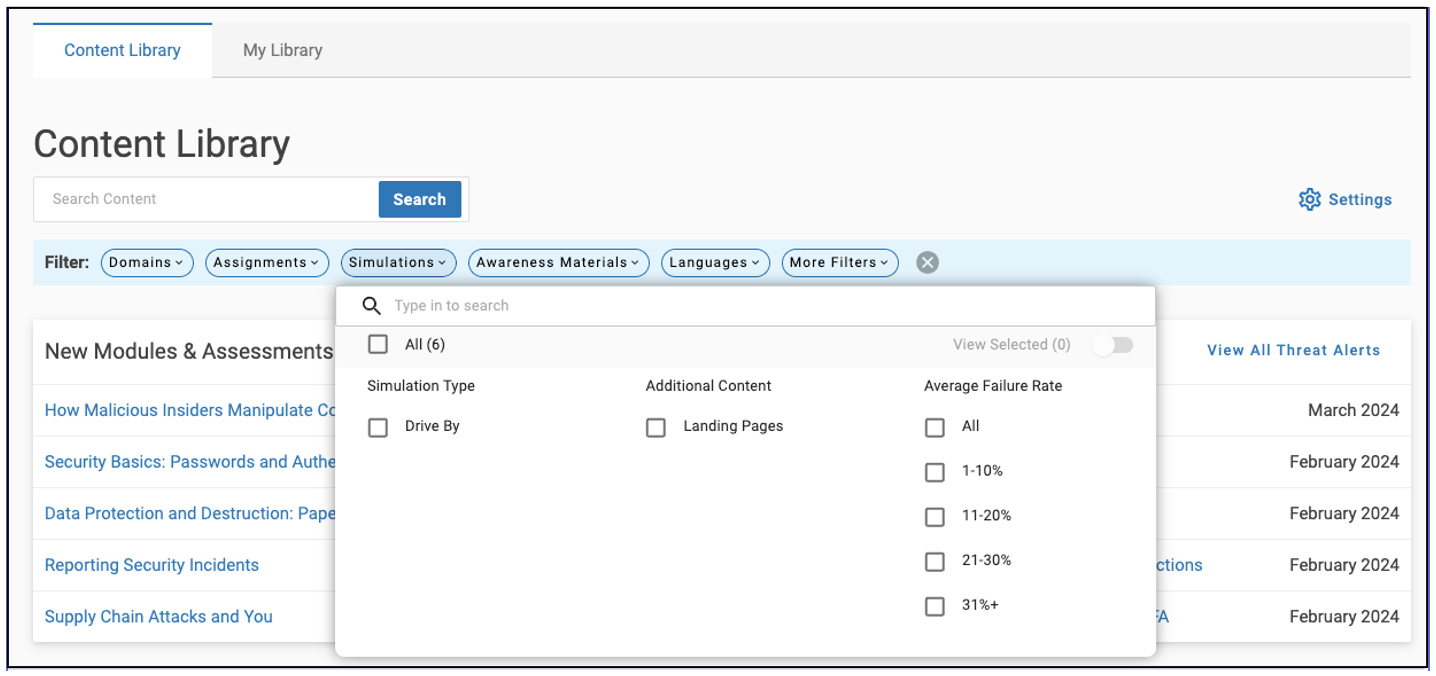
Rearchitected Content Library filter
We overhauled the Content Library Filter to streamline the administrator experience further. We expanded the primary filters so that you can conduct searches based on:
- Domains
- Assignments
- Simulations
- Awareness materials
- Languages
You can also do a deeper search within each filter via a simple checkbox or manual entry.
Phishing simulation templates integration
We also integrated phishing simulation templates into the Content Library. That means you can now rapidly develop and deploy a phishing simulation campaign that aligns to a target group’s comprehension level as well as your expected failure rate goals.
A view of phishing simulation templates integrated into the Content Library.
Learn more
These enhancements to Proofpoint Security Awareness prove how committed we are to delivering sophisticated, user-focused training. Our platform not only teaches users what they need to know, but it also helps create a culture of proactive cybersecurity vigilance.
We encourage you to take advantage of these enhancements. If you need help with or want to learn more, contact us.











