At Proofpoint, we talk a lot about the value of identifying the very attacked people, or VAPs, in your organization. Those most “at-risk” might surprise you—they aren’t always the VIPs we often assume attackers prioritize.
Our latest cybersecurity threat report presets data gathered between January and June of 2019. In it, we examine which employees, departments and industries are most at risk, why they are targeted and how.
Here are three key findings from our research. To get the full report, and recommendations for how you can start identifying VAPs at your organization, click here.
1) Education and food/beverage organizations were the most vulnerable to cloud-based attacks.
The education and food and beverage sectors were most vulnerable to cloud account attacks, with more than 7 in 10 attack campaigns resulting in a successful compromise.
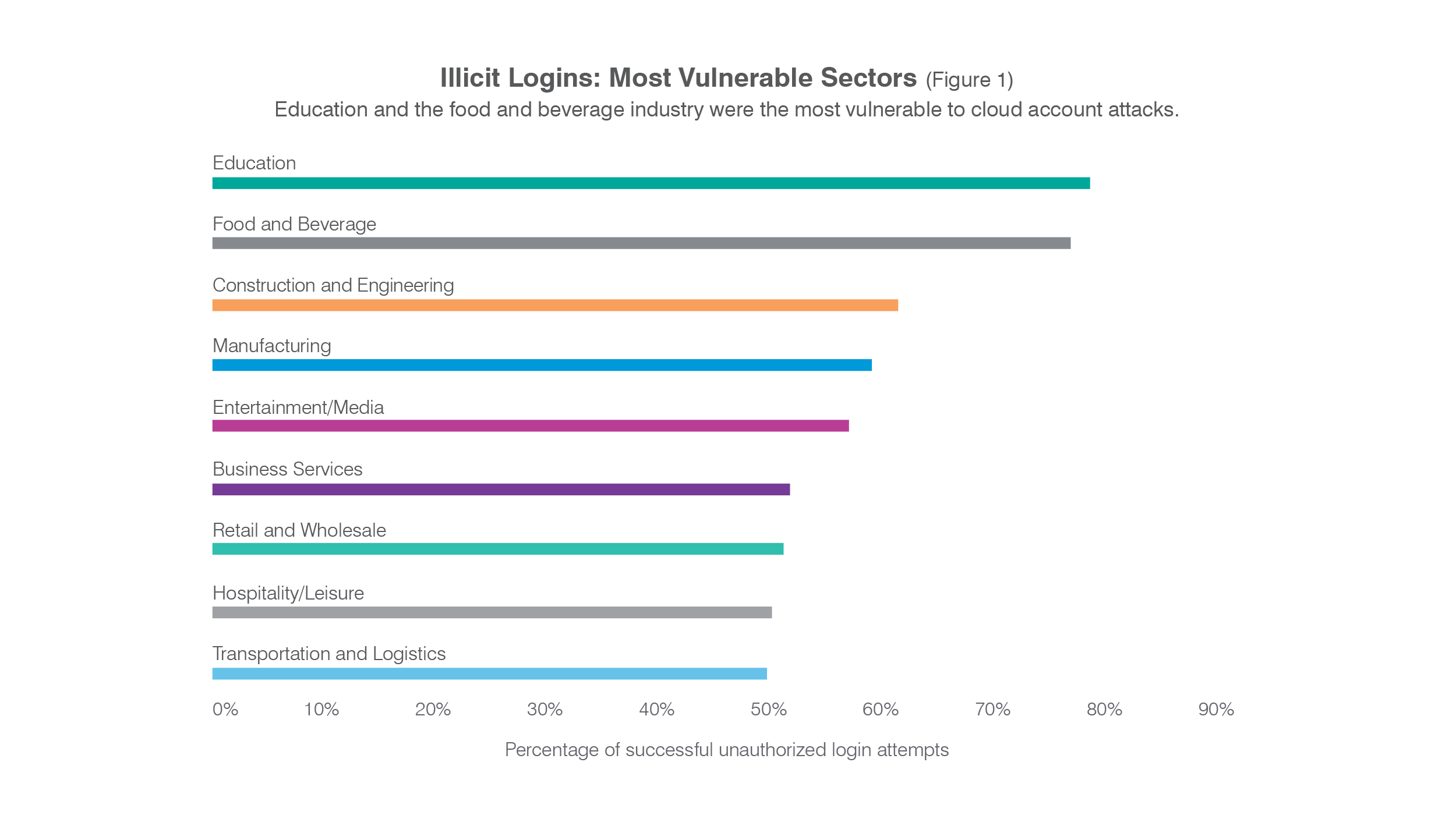
For cyber criminals, school districts, colleges and universities were easy prey. Possible reasons include large numbers of users (such as students) and decentralized security operations. Cloud accounts that go largely unused, such as those provided to a school’s alumni, represent ideal targets for brute-force password attacks.
Many account owners don’t use the account often enough to notice anything amiss. Once attackers gain control over the account, they can use it for spam, malware and phishing campaigns—especially against other users within the school’s domain.
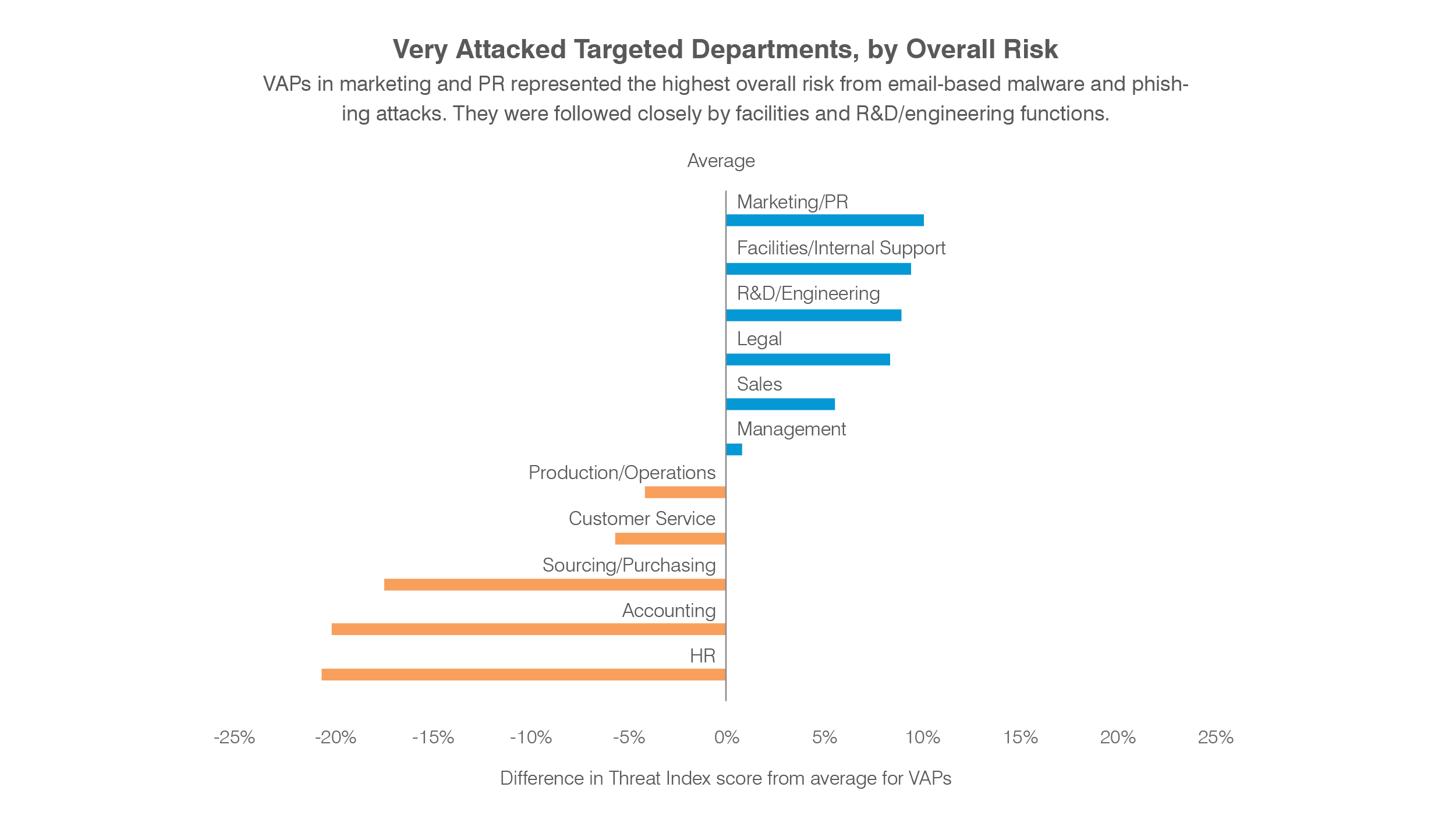
2) Marketing/PR represented the highest overall risk from malware and phishing
By department, workers in marketing/public relations functions represented the highest overall risk from malware and phishing, followed closely by facilities/internal support (which includes IT workers) and R&D/engineering.
Email addresses in the marketing/PR category may be bigger targets simply because they are more readily accessible. Public relations professionals often include their full name, email address and other contact information in press releases and newsroom sections of company websites. And marketing professionals often promote themselves on social media and other digital channels.
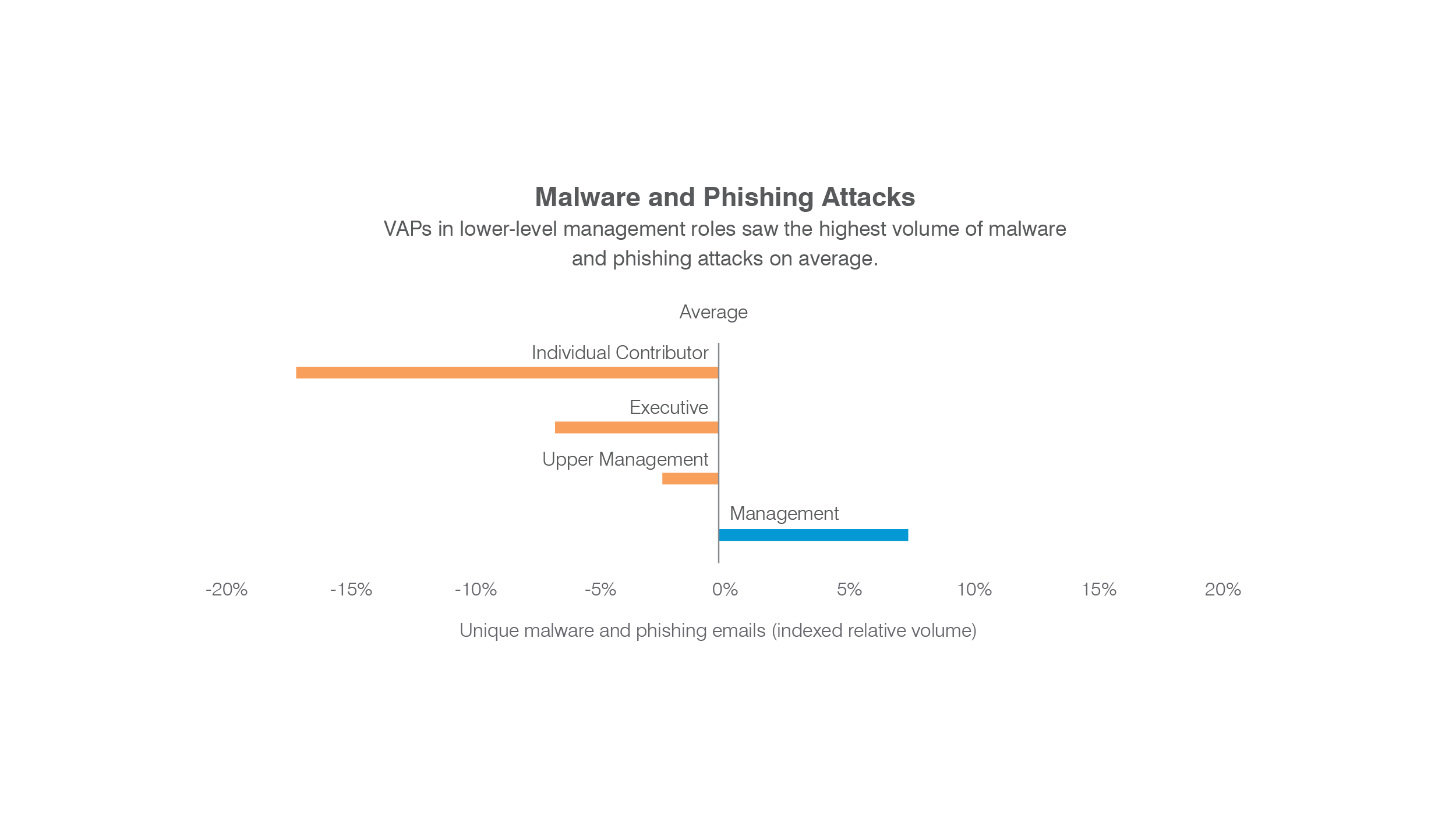
3) Your VAPs aren’t always your VIPs
Overall, VAPs at every rung of the corporate ladder are at roughly equal risk from email-based malware and phishing attacks.
Across the board, Attack Index scores fell within one or two percentage points of the overall VAP average. But VAPs in lower-management roles saw nearly 8% more phishing and malware attacks than the average VAP. The split suggests that attacks targeting these VAPs were higher volume but lower risk than those targeting both higher- and lower-level VAPs.
To learn more about attack trends in the first half of 2019 and to get recommendations on how to fight back, download the full report here.











