Proofpoint researchers have observed a new downloader in the wild that we and other researchers are calling “GuLoader.” Our researchers first observed GuLoader in late December 2019 being used to deliver Parallax RAT, which itself had recently been released. While we regularly observe new loaders, GuLoader has gained popularity quickly and is in active use by multiple threat actors. GuLoader is a downloader, written partly in VB6, which typically stores its encrypted payloads on Google Drive or Microsoft OneDrive (underscoring that threat actors continue to adopt the cloud just like legitimate businesses are).
GuLoader is a portable executable (PE) file that is often observed embedded in a container file such as an .iso or .rar file. We have also observed it being downloaded directly from various cloud hosting platforms. GuLoader is used predominantly to download remote access Trojans (RATs) and information stealers such as Agent Tesla/Origin Logger, FormBook, NanoCore RAT, Netwire RAT, Remcos RAT, Ave Maria/Warzone RAT and Parallax RAT.
Analysis
The GuLoader executable is a Visual Basic 6 wrapper which decrypts (XORing with a DWORD, 4-byte key) some shellcode containing the main functionality.
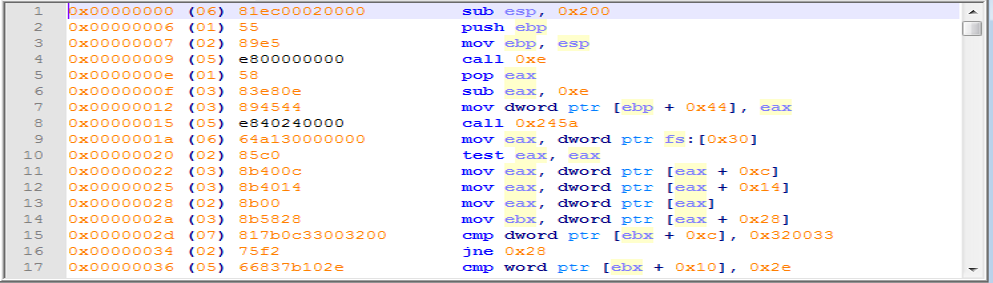
The loader uses sophisticated injection techniques to make analysis difficult. For example, it
- spawns a child process copy of itself (in suspended state)
- maps the image of a system DLL (typically "msvbvm60.dll" or "mstsc.exe") over the child at 0x400000 (instead of a normal high load address)
- injects the unpacking code into the child
- modifies a register within the context of the suspended child thread to redirect execution into the injected code
- resumes the child
- the child overwrites the system DLL image at 0x400000 with the unpacked code
The downloaded files consist of 64 hex digits followed by a PE executable encoded with XOR, where the XOR key is stored in the shellcode.
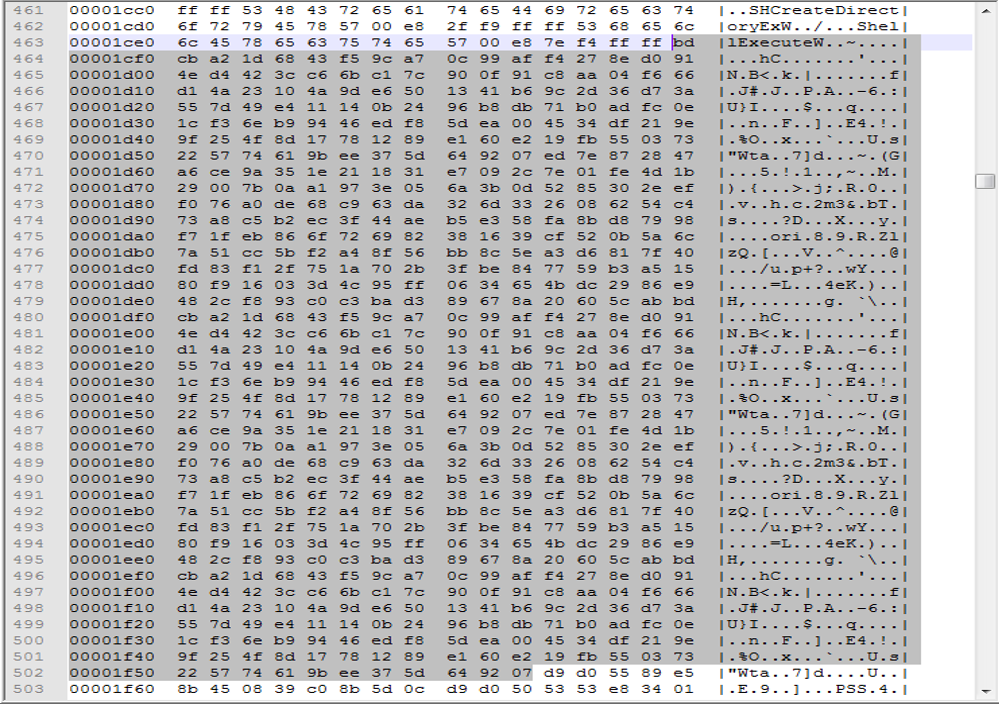
Payload Encoding
The payload URI paths (other than Google Drive or OneDrive ones) and downloaded filename frequently have the form "<something>_encrypted_XXXXXX.bin" where "XXXXXXX" are hexadecimal digits.
The downloaded payloads consist of
* 64 lower-case hex digits
* the XORed PE binary
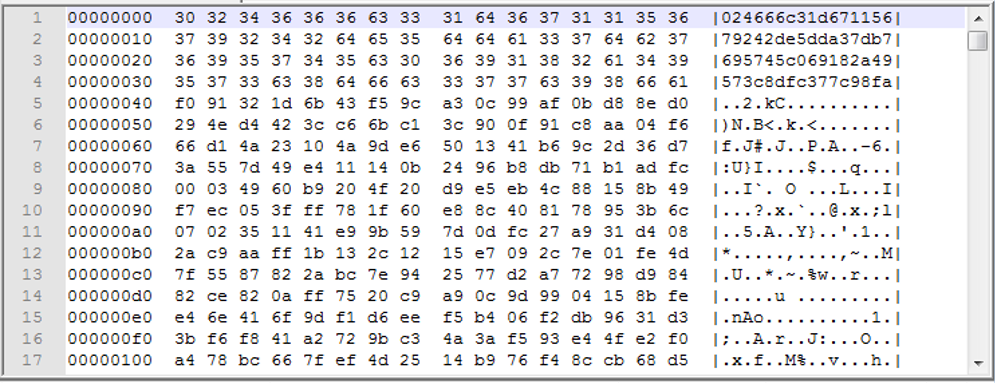
The XOR key was fixed at 96 bytes in early versions of the loader
Later versions have longer keys, typically 512-768 bytes long, usually consisting of a 256-byte key repeated to give the required length. The key is stored completely in the decoded shellcode.
IOCs
Parallax Sample - 2019-12-23
SHA256: e8f8cc178425c55c03c76d0a2a11918371bba8f2d6f400752ca1cea5e663da2e
URLs: hxxps://drive.google[.]com/uc?export=download&id=1dtlMCyozUPBepc-AtEdirGENZBpWesAi
C2: 185.140.53[.]134:7776
Remcos Sample - 2020-02-20
SHA256: 26f7bfe041a3d8a2b620d0ed2af4e2ef54b004202ec479362939b9154b1c8758
URLS: hxxps://drive.google[.]com/uc?export=download&id=1N8gVOM5p8Ubm1HwolChxHidT7YoN29EE
C2: droptop1[.]com:2500
C2: droptop2[.]com:2500
C2: droptop3[.]com:2500
C2: droptop4[.]com:2500
C2: droptop5[.]com:2500
C2: droptop6[.]com:2500
C2: droptop7[.]com:2500
C2: droptop8[.]com:2500
C2: droptop9[.]com:2500
C2: droptop10[.]com:2500











