Proofpoint recommends a people-centric approach to security, where organisations are protecting their people, and their people are, in turn, helping to protect the business. But findings in the recent Notifiable Data Breaches (NDB) Report from the Office of the Australian Information Commissioner (OAIC) suggest that many organisations in Australia have some work to do to strengthen their “human firewall.”
The OAIC NDB Report, which was released in late August, says that nearly 30% of the data breaches reported in Australia during the period from January to June 2021 were the result of human error. And 30% of all the data breaches reported to the OAIC related to phishing (compromised credentials). More than half of cyber incidents (62%) during the reporting period involved malicious actors gaining access to accounts using compromised or stolen credentials, according to the OAIC NDB Report.
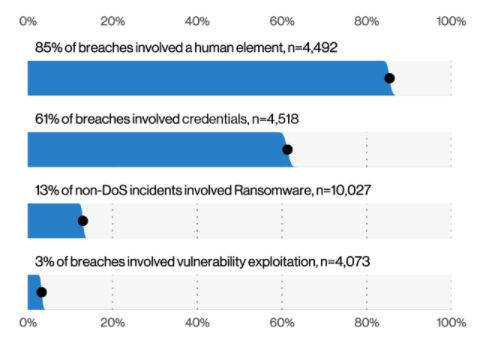
These are not just numbers we see in Australia. In the latest Verizon Data Breach Report, a global report, 85% of data breaches involved a human element and 61% of breaches involved credentials.
(source: 2021 Verizon Data Breach Report)
A silver lining: The 134 notifications of human error-related breaches that the OAIC received during the most recent reporting period represent a 34% drop from the prior period (July to December 2020), which saw 203 notifications. This decline may indicate that some organisations are doing a better job of increasing their employees’ awareness of cyber threats like phishing through targeted education.
Credential phishing remains a favorite tactic for attackers
The premise is basic: Cyber Attackers target people, they exploit people and ultimately, they are people. Since human error-related data breaches persist—and people remain the prime target for attackers regular and focused user training and awareness uplift is needed. The attackers are consistently pivoting the way they attack – it’s important to understand who the most at risk people are and redirect your priorities to accomadate. Addressing their training and awareness needs isn’t “one size fits all” it needs to be multi-faceted, as not all users respond to the same training. Gaining the desirable behaviour change needs tailoring.
Consider separate research conducted for the Proofpoint report, The Human Factor 2021, which found that credential phishing, both consumer and corporate, was by far the most common form of attack last year, accounting for nearly two-thirds of all malicious messages—and outpacing all other attacks combined. Also of note: Of all the phishing methods (attachment, data and link), attachments are the most successful, according to our research. One in five people fall victim to attachment-based phishing emails—a higher rate than the other two methods combined.
Credential phishing leads to account compromise, which can be used to execute other attacks, including data theft and business email compromise (BEC). But there is a new hope in the fight against phishing: the DMARC (Domain-based Message Authentication Reporting & Conformance) standard. The open email authentication protocol, which is built on SPF and DKIM standards, is a powerful, proactive tool for disrupting long-standing phishing strategies and forcing cybercriminals to abandon their preferred targets. (You can learn more about DMARC in this Proofpoint white paper.)
Email still playing the critical role in enabling ransomware attacks
Successful credential phishing can easily open the door to costly, disruptive ransomware attacks. According to the OAIC NDB Report, ransomware incidents increased 24% in the last reporting period, compared to the prior period. But that percentage is no doubt higher in reality.
In its report, the OAIC notes that, “During this reporting period, a number of entities assessed that a ransomware attack did not constitute an eligible data breach due to a ‘lack of evidence’ that access to or exfiltration of data had occurred.” The OAIC also states, “It is insufficient for an entity to rely on the absence of evidence of access to or exfiltration of data to conclusively determine that an eligible data breach has not occurred.” It further underscores that “given the prevalence or ransomware attacks,” organisations are expected to have appropriate internal practices, procedures, and systems in place to undertake a meaningful assessment under section 26WH of the Privacy Act.
Backups can help save the day when ransomware strikes, helping organisations to preserve critical data and get systems back online faster. But user training with a focus on email security can also help organisations meet the OAIC’s expectations and reduce their risk of exposure to a ransomware attack in the first place. The 2021 Human Factor report from Proofpoint says that while ransomware campaigns are becoming increasingly more sophisticated and operators are changing strategies, email remains a crucial part of laying the groundwork for these attacks.
Email, our report explains, is “the route through which much of the first-stage malware used to download ransomware is distributed.” Through our research for this report, we also found that 48 million email messages in 2020 contained malware capable of being used as an entry point for ransomware attacks. So, the takeaway is this: If you can avoid initial infections, you can also avoid ransomware attacks.
If organisations need even more incentive to step up their efforts to prevent ransomware attacks, the Australian House of Representatives has provided it in the form of the Ransomware Payments Bill 2021. Introduced in June, the bill seeks to establish a mandatory requirement for Australian corporations and partnerships to report to the Australian Cyber Security Centre ransoms paid in response to a ransomware attack. With this legislative move, the government is no doubt aiming to provide visibility into what it suspects is a large number of companies discretely paying hefty ransoms to cyber criminals rather than suffering the pain of an extended attack.
Repeating patterns underscore the need for change
The past 18+ months of COVID-19 pandemic-related disruption, which includes the rapid expansion of remote work, has created fertile ground for cyber criminal groups to amplify their efforts to target people. And findings in both the OAIC NDB Report and The Human Factor 2021 report make it abundantly clear that a people-centric approach to security is a must in today’s threat environment.
If you look back at prior OAIC NDB Reports, you can also see consistent patterns in data breach activity for organisations and industries in Australia. For example:
- Malicious or criminal attacks are the leading source of data breaches.
- Contact information, identity information and financial details continue to be the most common types of personal information involved in data breaches.
- And the two industries in Australia reporting breaches most often to the OAIC are the health sector and the finance sector—accounting for 19% and 13% of all breaches, respectively, in the latest OAIC NDB Report.
The question for every organisation that reported a breach to the OAIC in the past six months is this: What are you doing now?
Before the COVID-19 pandemic, many companies didn’t have the proper training in place to help their employees recognise and do their part to handle cyber threats. But even now, we continue to see end users not adequately trained to deal with cyber threats. Many Australians are still selecting basic passwords, and use the same credentials to log in to different online platforms and services, clicking on risky links they shouldn’t click on, and downloading attachments from suspicious senders.
User education isn’t the only way to combat cyber risks and threats. But without it, your organisation’s human firewall will never stand as an effective line of defence.
Learn how Proofpoint Security Awareness Training can help ensure the right response from your users when faced with sophisticated phishing and other attacks.











