Users are ~7 Times More Likely to Click on Malicious SharePoint Online/OneDrive links
Threat actors have followed the enterprise migration to the cloud. They compromise and take over user accounts to move laterally inside an organisation, steal data, or communicate with your business partners or customers to request fraudulent wire transfers. They use your cloud and email infrastructure to host and distribute malicious content. Attackers leverage your users’ contacts and study their emails to understand trust relationships and map organisations. Exploiting the way modern employees work such as file sharing, attacks can be more effective than ever. In fact, Proofpoint research shows that users are seven times more likely to click on malicious OneDrive and SharePoint Online phishing links that are hosted on legitimate Microsoft domains.
In the first half of 2020, Proofpoint detected 5.9 million email messages with malicious SharePoint Online and OneDrive phishing links. While these messages made up about 1% of the total sample of messages with malicious URLs, they represented more than 13% of user clicks.
Phishing victims were:
- Four times more likely to click on malicious SharePoint links
- 11 times more likely to click on malicious OneDrive links
We also discovered that these messages were distributed from over 5,500 compromised tenants, which represent a large portion of Microsoft’s enterprise customer base. Such a wide-spread and effective form of cyberattack deserves a closer look.
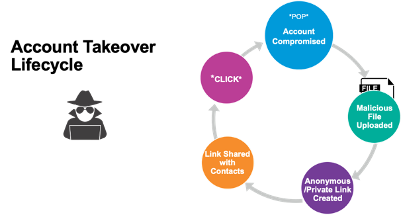
Malicious SharePoint/OneDrive Phishing Links and Account Takeover Lifecycle
SharePoint phishing usually starts with cloud account compromise. Once in control of the account, the attacker uploads a malicious file and then changes the sharing permissions of the file to “Public” so the new anonymous link can be shared with anyone. The attacker emails the link or shares the link with the user’s contacts or other targeted accounts, including external ones. When the recipients open the file and click on the embedded malicious link, they are phished, which starts the whole cycle again. These attacks can lead to data theft or wire fraud such as supply chain fraud.
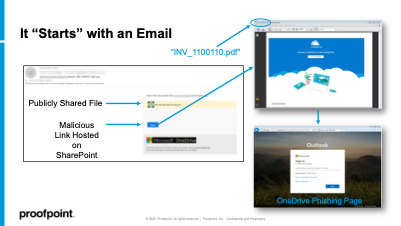
PDF Example:
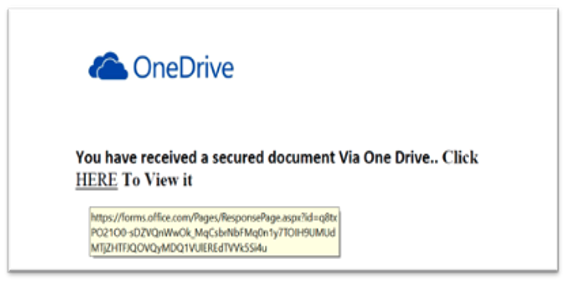
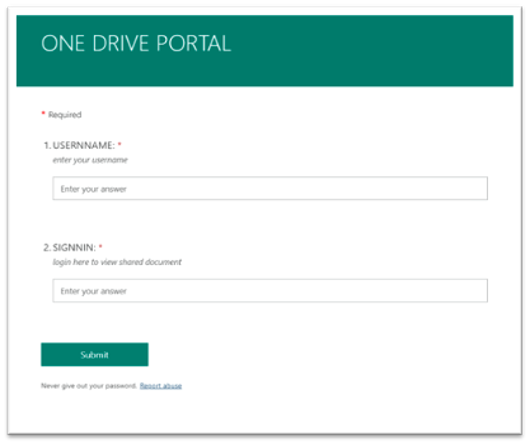
In the example below, a user receives an email with a shared link to a pdf file (INV_1100110.pdf) that looks like an invoice. When the user clicks on the link in the pdf file, he is directed to a phishing site that is a fake OneDrive sign-in page.
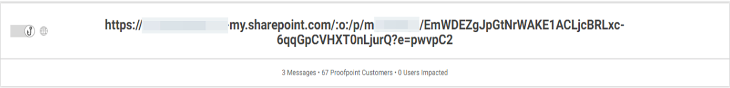
Sometimes the link in the shared document can be a redirect URL that is unique and hence can be difficult to detect, as it would not appear on any URL reputation repository.
OneNote Example:
Here is an example of an attack that uses SharePoint to host a malicious OneNote file impersonating voice mail:
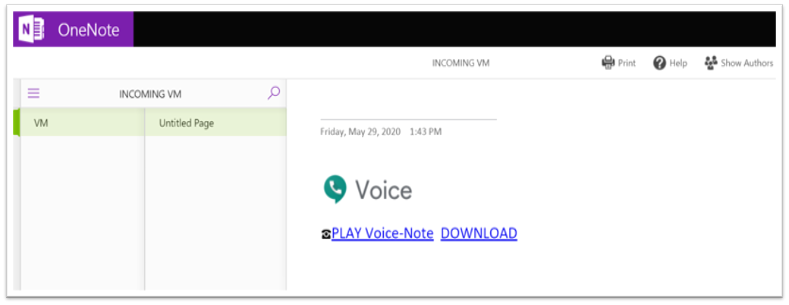
Malicious OneNote files can also be challenging since they cannot be downloaded and sandboxed. Detection requires an additional step—web-scraping before the embedded links can be analysed.
Microsoft Form Example
In this example, the cybercriminal shares a Word document with a link to a publicly shared Microsoft Forms file (the fake login page), which he uses to harvest Office 365 credentials. Given this attack utilises legitimate Microsoft services and is pure social engineering, it poses more of a challenge to detect and even harder to block/mitigate if you lack visibility into both email and cloud environments.
We have also observed some attackers hosting malicious content in one tenant while utilising a compromised account such as that of a VIP in a second tenant. Sharing the malicious link from the account of a more fitting user would increase the attackers’ chances of success. In addition, even if the compromised account in the second tenant is discovered, the malicious file hosted in the first tenant would not be taken down. And so, the attack would persist.
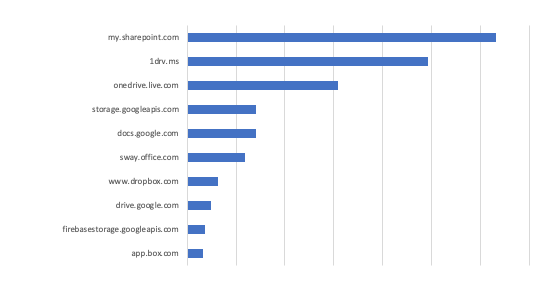
Top 10: Collaboration Services Domains with Clicked-On Malicious Links
SharePoint Online and OneDrive are not the only collaboration services domains that are abused by attackers. The graph below shows the top 10 list for such domains by clicks on malicious links hosted on those domains in the first half of the year. A notable one is Sway, the new Microsoft app for creating and sharing interactive content such as reports and newsletters. A second one is storage. Googleapis, which is a file (like a software patch) hosting service that attackers use for tech support scams and more.
Defending Against Hybrid Email and Cloud Threats
To defend against hybrid attacks like SharePoint and OneDrive phishing, organisations must gain visibility across email and cloud threat vectors and address the attack chain holistically. You need to understand your very attacked people (VAPs) and the risks they pose to your organisation:
- Who is being targeted with high-priority threats?
- What techniques are being used to attack users?
- Who has clicked on malicious attachments or links?
- Which users are prone to clicking?
- Which accounts are compromised?
- Which compromised accounts show suspicious file activity?
Proofpoint Targeted Attack Protection and CASB bring our people-centric approach to email and cloud security and defend cloud accounts against such attacks using advanced analytics such as:
- Predictive sandboxing of email messages with links from collaboration services such as SharePoint, OneDrive, Google Drive, Dropbox, etc.
- URLs are rewritten to protect users on any device or network as well as provide real-time sandboxing on every click
- Compromised account detection and remediation
- Adaptive access controls that prevent unauthorised logins or enforce multi-factor authentication for risky ones
- Post account takeover file and mailbox activity detection and mitigation
In addition, Proofpoint Security Awareness Training delivers targeted education driven by threat intelligence to ensure the right response from your users when faced with sophisticated attacks such as SharePoint and OneDrive phishing.
Learn More:
To learn how Proofpoint can protect your people and data with superior security, explore our Microsoft 365 compliance solutions. For more on CASB use cases, download our whitepaper, Getting Started with CASB.











