Prioritizing a strong defense against Business email compromise (BEC) and email account compromise (EAC)—a collective $26B problem—is more important than ever.
Our "Combatting BEC and EAC" blog series presents key things you can do at your organization to fight these cyber security threats. Each post in the series centers on one of seven key steps. In this post, we cover the seventh and final step: training your people.
A BEC attack from the target’s perspective
Imagine a day in the life of an ordinary user who doesn’t work in cybersecurity. They’re checking email while drinking coffee and see a message “from” a supplier who recently got acquired and needs to update their banking information for paying invoices. Seems like a simple request. The user logs into your organization’s payment system, updates account details and goes back to their normal routine for the day.
That user just fell for a business email compromise (BEC) attack.
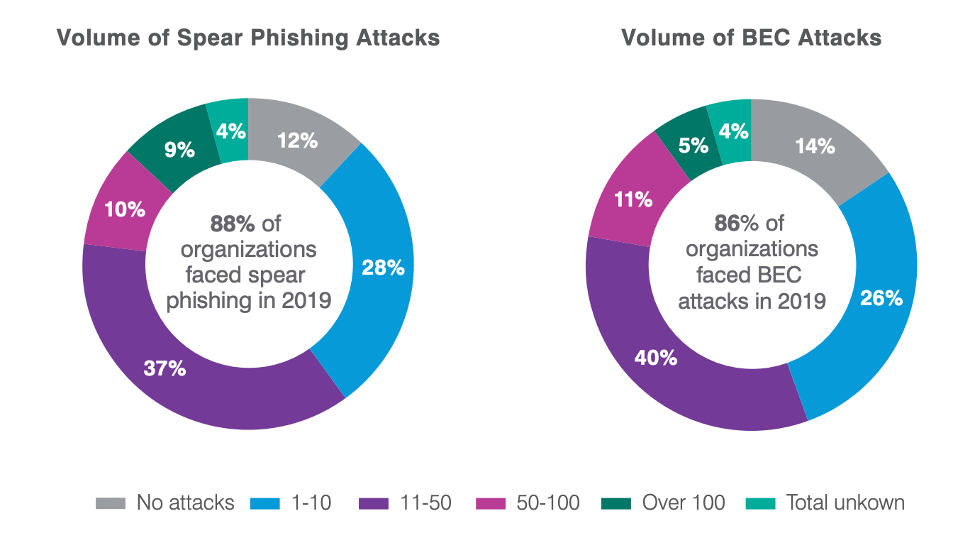
In 2019, according to the Proofpoint State of the Phish report, 86% of organizations reported experiencing business email compromise, with most organizations reporting multiple attacks. These attacks are getting more sophisticated each year—so how can you prepare your users for the potential attack that slips by perimeter defenses?
Plan specific—and ongoing—BEC education initiatives

Providing relevant security awareness training to your users is an ongoing process, not a one-time event. For BEC specifically, focus your education initiatives on vulnerable and targeted departments, including:
- Finance
- Accounting
- Human Resources
- Procurement
But don’t rush into BEC training without empowering your employees with some basic cyber security knowledge including the definitions of major threat tactics like BEC and how they work. Once this foundational knowledge is established, move on to more in-depth education on “how to do a double-take” around the specifics of spotting BEC attacks.
Out of band verification is another essential component of stopping successful BEC attacks. We’d recommend setting up meetings with department leaders and documenting or revising your verification processes for wire transfers, account changes, and related business processes. Don’t just rely on a single individual or communication channel, enhance this without of band verification. After you’ve agreed on the what, setting aside some time to educate these departments on processes will help you towards your ultimate goal of securing your environment and greatly reducing the likelihood of a successful attack.
Teaching the “why” of these processes and using stories to paint the picture will help users understand the needed extra steps to keep everyone safe and will be more impactful beyond just communication explaining the process.
If you’re interested in free materials and a campaign plan to educate your users on business email compromise, we have a free BEC kit you can use at your organization.
Give users an “out” when they’re unsure
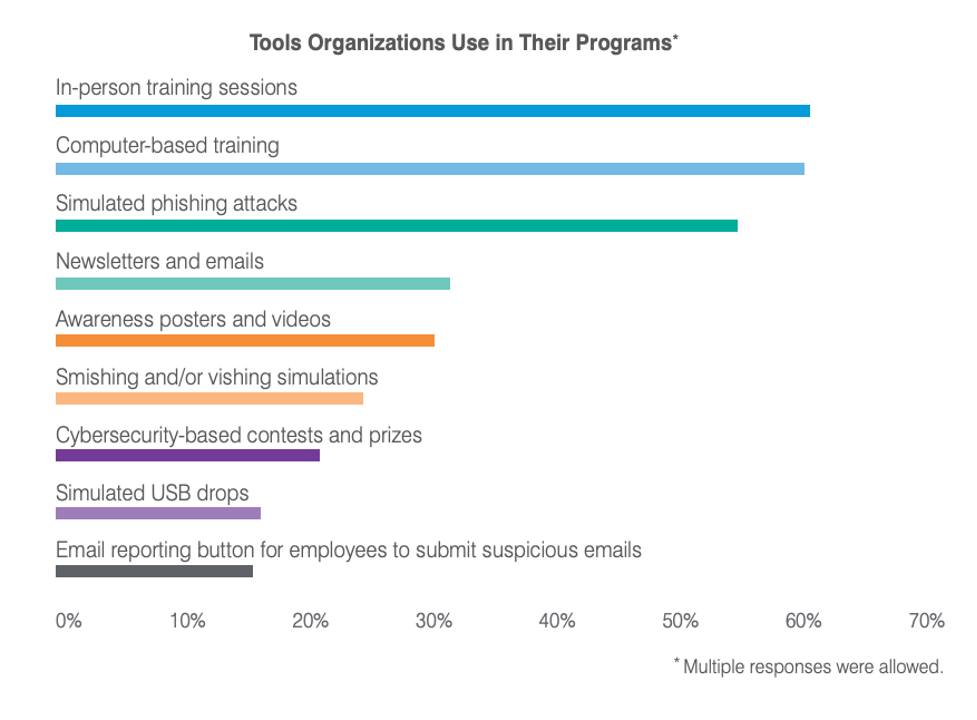
One of the most critical cyber security tools organizations can use in their program is an easy way to report suspicious messages such as using an email add-in. Only 15% of organizations have one in place today.
This approach is important for two reasons:
- It gives users an “easy out” whenever they have doubts about the message
- It helps reduce exposure within an organization
Though a lot of organizations have issues with an overflow of their abuse mailbox, we utilize advanced analysis using our threat intelligence and built-in sandboxing to tell administrators if the message is malicious, spam, safe, or otherwise. Our Closed-Loop Email Analysis and Response (CLEAR) solution can even automatically remove malicious reported messages and even send users feedback about the message they reported. Together this workflow helps reduce exposure and make users an important layer of cyber security for the organization. Clients who have impactful, ongoing security awareness efforts are able to consistently have 70%+ of users reporting suspicious messages.
Learn More About Stopping Business Email Compromise Attacks
BEC attacks are becoming more sophisticated, and the equation for stopping BEC attacks is becoming more complex. Proofpoint offers a layered approach to address the multitude of tactics bad actors are using every day against businesses like yours. Get the information you need to protect your organization with our complimentary BEC readiness assessment.











