The abuse mailbox can be a huge pain point for information security teams. It can mean thousands of hours spent annually researching messages, identifying which ones are malicious, and then trying to remove all copies before threats are potentially activated by users. It also means a lot of time devoted to nonthreatening reported messages while serious attacks are potentially waiting in the wings.
According to The 2021 Cost of Phishing Study from Ponemon Institute, the average 10,000-person organisation spends thousands of hours remediating threats like business email compromise (BEC), malware infections, ransomware and credential theft, typically the primary drivers of email-based attacks. Credential phishing alone, one of the most popular types of threats for attackers, costs organisations about $700,000 annually responding to compromises.
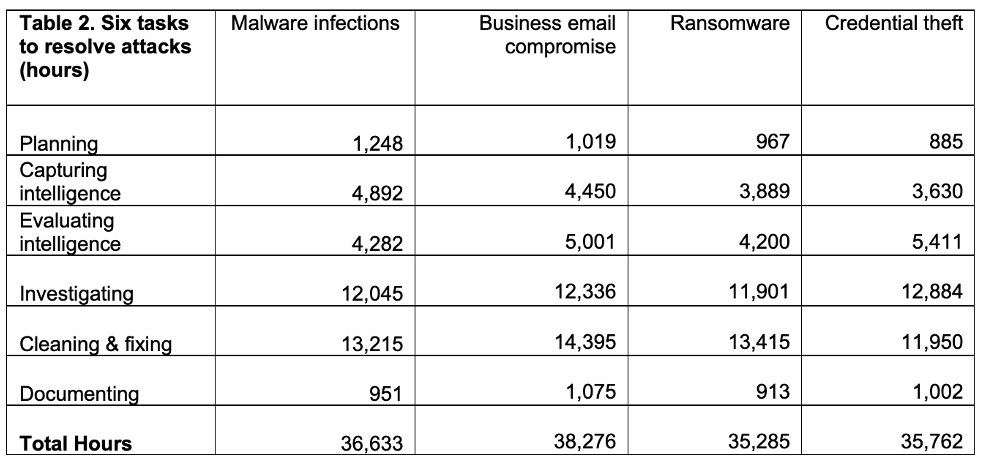
Figure 1. Research on the cost of phishing from Ponemon Institute shows the significant hours IT and information security teams spend remediating email-based threats (for a 10,000-person organisation, in this example)
To help solve this problem, Proofpoint suggests taking the following steps so you can manage your abuse mailbox successfully while also saving time and drastically reducing risk for your organisation.
Start with what’s already in your inbox—the good, bad and ugly
If you’re already overburdened with an influx of spam, phishing and other messages flooding your abuse mailbox, it’s important to go to the very core of the problem: messages getting delivered to your users in the first place. An advanced email security solution is necessary to reduce the risk of malicious messages in your inbox.
How much is your email security solution missing?
No matter how much automation you apply to investigating and responding to bad emails, if there are too many bad messages getting through, it’s a lose-lose for all parties. Think of a healthy email inbox like preventive care. It’s better to tackle the problem when it emerges rather than deal with the potentially worse downstream impacts later, echoing frameworks like the MITRE ATT&CK “Shift to the Left” towards PRE-ATT&CK.
We frequently see this problem in email security when conducting our Threat Assessments with potential customers. In the past month, for instance, in proof of concepts we conducted with Microsoft email gateways, over 12% of messages were condemned, with hundreds of thousands of credential, attachment and URL threats—and impostor and BEC messages—slipping through perimeter defences.
The net result is more incident response time and resources, creating a downstream impact of “good enough” email security. One example, shown below, is a large global consulting customer that was spending a lot of time remediating messages that had slipped through the perimeter. This was before they improved their email security posture and were able to achieve the protection and time-savings to SOC shown below.
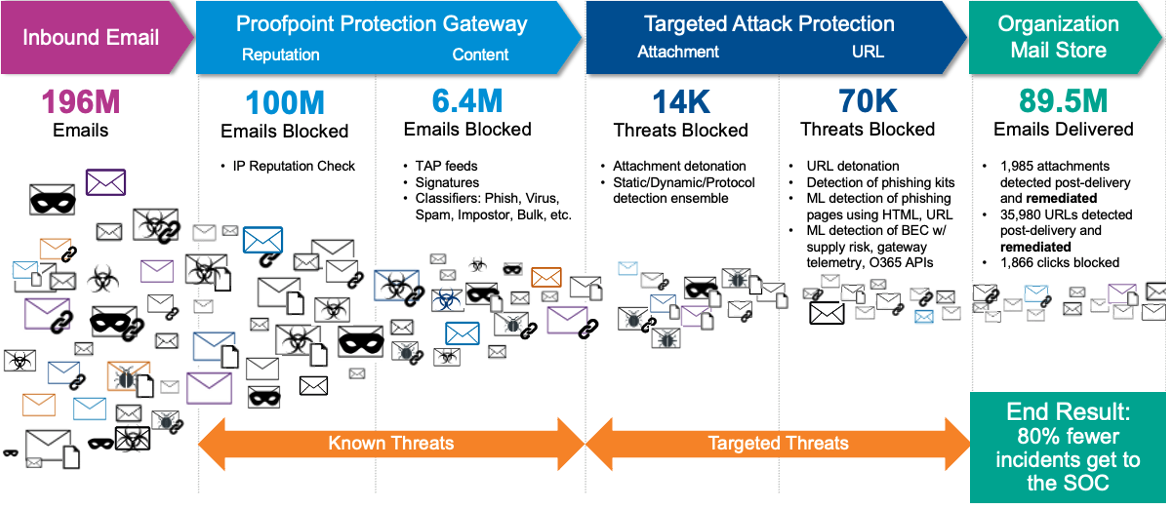
Figure 2. Example of mail flow, showing a large consulting firm using the Proofpoint Threat Protection Platform to reduce threats and spam getting through their existing gateway
And it’s not just threats and spam that cause pain for security operations centre (SOC) teams. False positives also play a role in increasing incident response workload, and we’ve seen many API-based Cloud Email Security Supplements (CESS) cause a high false positive rate for prospects during their proofs of concept. In one customer proof of concept, a CESS claimed 900 messages were malicious, but we found 68% of those malicious messages were false positives, meaning teams now have to go through those 600+ condemned messages to ensure they’re delivered.
In the case of the large consulting firm, the SOC team saw an 80% reduction in the number of incidents they received once the organisation improved its email security posture. This reduction drastically cut the need for SOC resources to be devoted to this area and also shortened overall response time.
Drive behavioural change for better email reporting accuracy
Once you improve your email security posture, the next step is to improve user phishing reporting habits and drive behaviour change.
As we noted in our last blog post [LINK], about two-thirds of user-reported messages, on average, aren’t malicious, suspicious or spam messages. Improving user email reporting accuracy can do wonders to reduce the number of false positive-reported messages. That said, we still suggest that users report anything they’re unsure about, as it’s better for your team to have visibility into the potential threats lurking in users’ inboxes.
Here are some other clear, actionable steps you can take to improve the accuracy of user phishing reporting:
1. Have a launch plan with onboarding education and ongoing reinforcement about your email reporting add-in that will complement your current phishing education initiatives.
By having a clear explanation of your email reporting button, what it’s for, when to use it, and how to access it on different devices, you’ll improve user reporting accuracy.
Consider making a video, including information in company newsletters, discussing the add-in in town halls, and incorporating information about it into your existing security awareness program’s content. Having a launch plan alongside a comprehensive phishing awareness training program that engages users with different mediums about spotting phish will help improve user reporting accuracy.
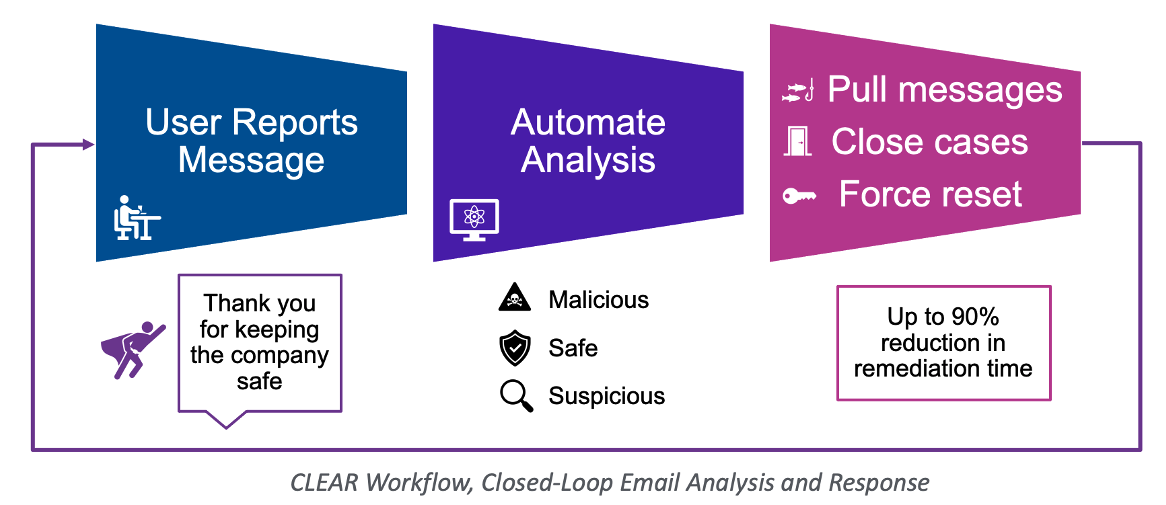
Figure 3. The automated solution for the abuse mailbox to reduce investigation and remediation time by up to 90% with the CLEAR workflow (Closed-loop email analysis and response)
2. Provide users feedback about the messages they report.
The automated solution for the abuse mailbox to reduce investigation and remediation time by up to 90% also provides users feedback about the messages they report with the CLEAR workflow (Closed-loop email analysis and response). No user wants to submit a message to the security team and never receive a response. A broken feedback loop can also mean new tickets for the SOC team to respond to if users follow up about their original report.
It’s much easier to automate the feedback loop to users, letting them know the status of the message they reported. This feedback about reported messages will sharpen their skills and improve their reporting accuracy even more.
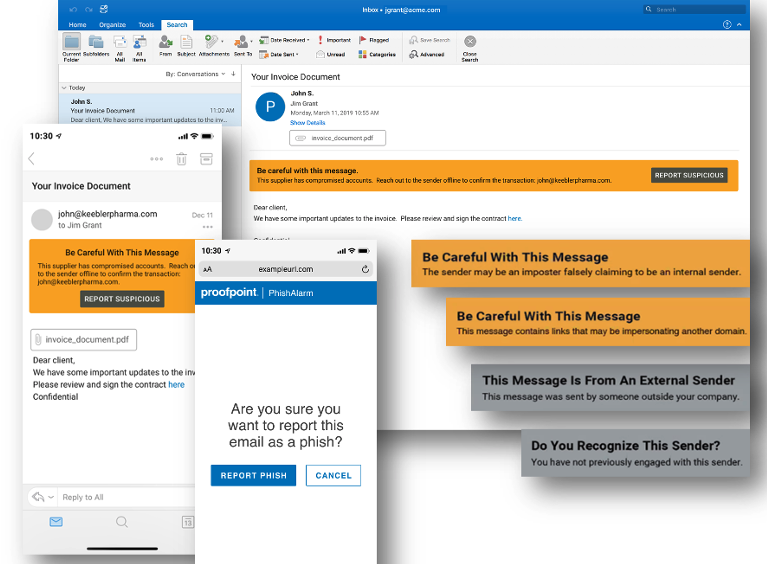
Figure 4. HTML-based Email Warning Tags provide users with contextual nudges to enhance their email reporting volume and accuracy.
3. Nudge your users about the messages they receive, and let them take action
HTML-based Email Warning Tags provide users with contextual nudges to enhance their email reporting volume and accuracy. Giving users context about the current message a user is reading is helpful for gauging risk in real time.
This is a new feature for Proofpoint customers; we’re excited to see what happens to user reporting rates and accuracy as customers adopt this tool.
Automate as much of the incident response process as possible, and consider reducing IT burden with professional services
If you’ve improved your overall security posture and provided users with tools and guidance to improve their phishing email reporting, the final step is to automate as much of the remaining incident response process as possible.
By automating the abuse mailbox, you can streamline workflows and drastically cut the time spent on manual tasks. Some of our customers have seen an up to 90% reduction in time spent on manual work.
But organisations are also strained for resources to manage email security. If that’s a painpoint in your business, organisations can choose an in-house best-of-breed managed email service to reduce IT burden and improve your email security posture.
Rather than piecing together threat intelligence and sandboxing data, or constantly updating YARA rules or playbooks to be as leading-edge as possible, use solutions that incorporate all of these things automatically. That will help you reduce manual work and free up your resources to focus on more important security tasks. (You can read case studies about how customers who have done this see significant ROI and save hundreds of thousands of dollars in remediation costs.)
By following the above strategies, you’ll improve your organisation’s overall security posture by creating a more streamlined abuse mailbox. And you’ll be able to focus your IT and information security resources on addressing more pertinent threats and tackling other essential security projects.











