When you hear the term “supply chain risk”, you might think of inventory shortages. But there’s a hidden risk that can have just as much financial impact—or perhaps even more.
That risk is bad actors weaponizing your trusted business partners. And once attackers gain a foothold in your organisation, they will in turn start gathering data they can later use for extortion or ransomware attacks. Or they will try to extract funds through business email compromise (BEC) fraud attacks.
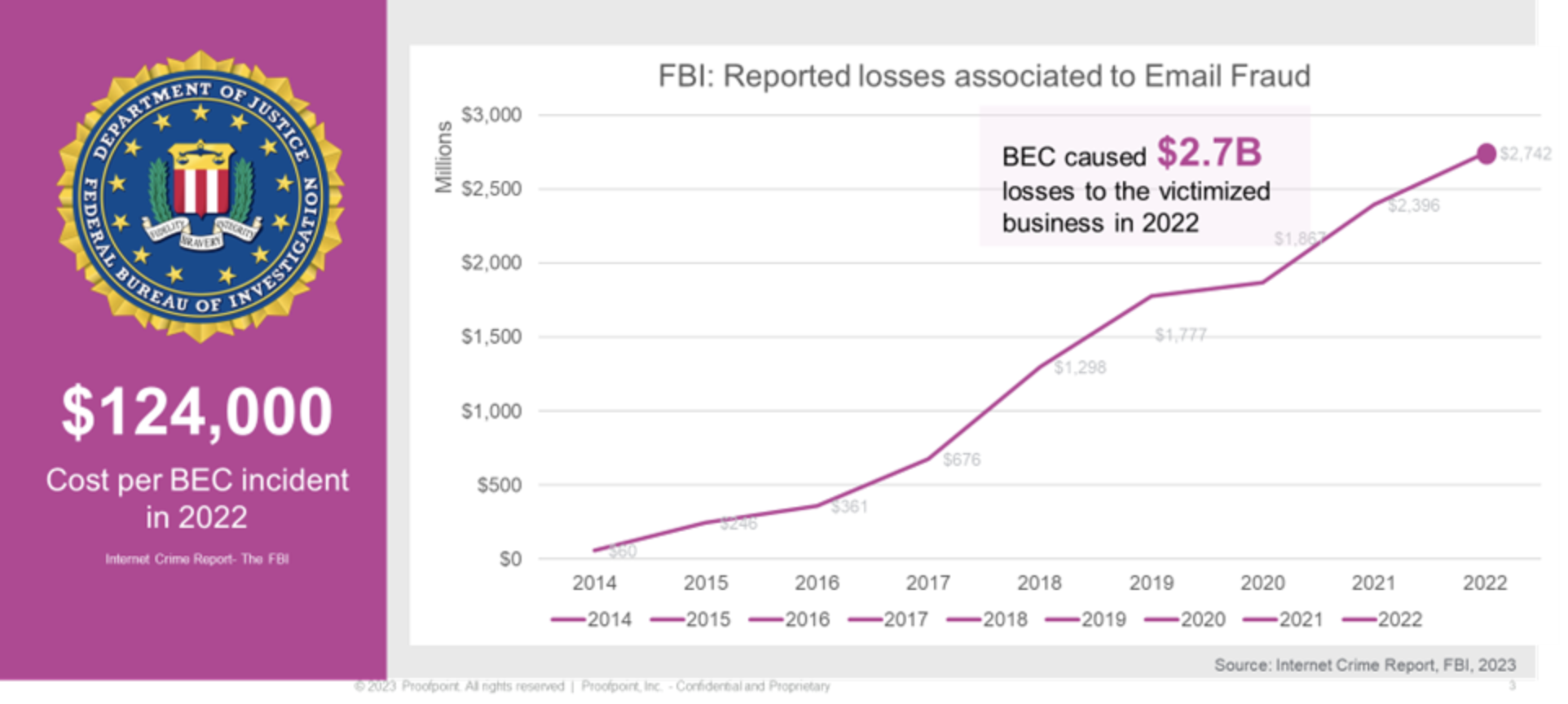
Figure 1. The $2.7 billion figure represents a 12.5% increase in losses in just one year. Source: FBI 2023 Internet Crimes Report.
Supplier-based attacks are on the rise. In fact, a recent Proofpoint analysis of nearly 4,600 organisations found that about 85% of them experienced supplier-based email attacks over a seven-day period ending January 31, 2023. Interestingly, these levels were consistent regardless of geographic location, industry or company size.
Let’s take a closer look at our findings. The most common tactics in supply chain attacks were phishing or impostor attacks (85%). More than three-quarters (78%) of these attacks were highly targeted. That means attackers weren’t casting a wide net, but they were very focused (less than five customers received the same threat).

Figure 2. Percentages of phishing and impostor threats and highly targeted threats. Source: Proofpoint
Here’s another concerning data point: Of the 4,577 organisations analysed, 96% were doing business with at least one supplier that had an active lookalike domain.
What does a supplier attack look like—and how can you better protect your organisation?
Threat actors take advantage of established financial relationships between businesses and their suppliers. It’s not out of the ordinary for suppliers to discuss terms or payments via email. If a bad actor can interject themselves at the right point in an email exchange or strike up an email conversation while impersonating someone, they can increase their odds of stealing payments or goods. This is especially true if they’re communicating from a legitimate account that has been compromised.
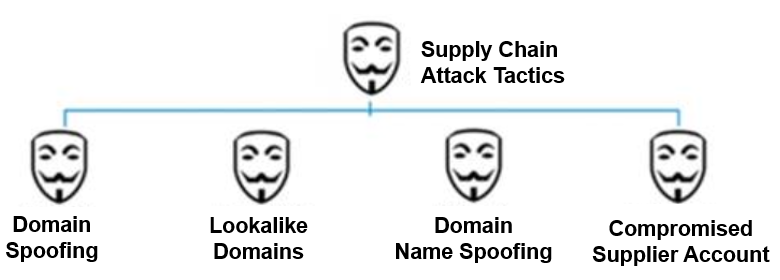
Figure 3. Common tactics used in supply chain attacks.
Here are some tactics to look out for:
- Email spoofing. Attackers will forge an email address to trick recipients into thinking a message came from a trusted person or entity. If your system isn’t checking the authenticity of email sources, email spoofing can go undetected.
- Lookalike domains. These domains appear very similar to legitimate domains to fool users who aren’t carefully inspecting addresses. For example, a bad actor could create a lookalike domain of goodomain.com or goodddomain.com to target customers of gooddomain.com.
- Display name spoofing. This is another way attackers impersonate trusted people. In this case, the email display name is changed so the message appears to be coming from a trusted source. Creating an account that has a spoofed display name is relatively simple. Spotting this tactic can be especially challenging for mobile users because most mobile device mail clients only show the display name—not the full “from” address.
- Compromised supplier accounts. Bad actors use compromised partner and supplier accounts for BEC, phishing and malware attacks. Security teams typically can’t see which supplier accounts are compromised and often rely on partner notification. This can lead to an investigation that’s highly manual and time-consuming.
Ransomware, payment requests and redirects
Attackers often seek financial payouts, either through ransomware or by convincing an unsuspecting target to send them money directly. Bad actors will send fraudulent invoices or request rerouting of payments to a bank account controlled by them.
When you consider the large amounts associated with supplier invoices, these scams are often the costliest for victim organisations. Any requests for payments or changes to payment routing should be highly scrutinised and confirmed by phone.
The need for proactive monitoring
Even with the best user training, it’s unrealistic to expect users to defend against every possible supplier email attack. This is where technology can help.
- Supplier Threat Protection. This solution from Proofpoint provides an added layer of protection by monitoring third-party entities and your suppliers to detect when an account has been compromised. Using advanced behavioural artificial intelligence (AI) and machine learning, compromised accounts can be detected early and acted on, even if the supply chain attacks haven’t been directed at your company yet.
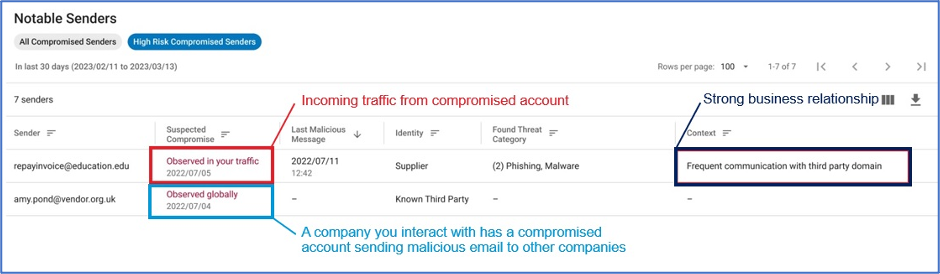
Figure 4. Compromised account information provided through the Proofpoint Supplier Threat Protection dashboard.
- Proofpoint Domain Discover. This detection system continually analyses newly registered domains, helping you identify domain lookalikes and respond to the domains attackers used to defraud your employees, customers and partners. Data gathered from Domain Discover can help support your virtual takedown submissions and get malicious domains added to blocklists.
- Nexus Supplier Risk Explorer. The Proofpoint Nexus supplier risk solution automatically identifies your suppliers and the domains they use to email your users. It assesses the risk level of these supplier domains by evaluating several dimensions, including:
- Threats sent to your organisation
- Threats sent to other Proofpoint customers
- The lookalikes of supplier domains
- Whether a domain is recently registered
- Whether a domain has a DMARC reject policy
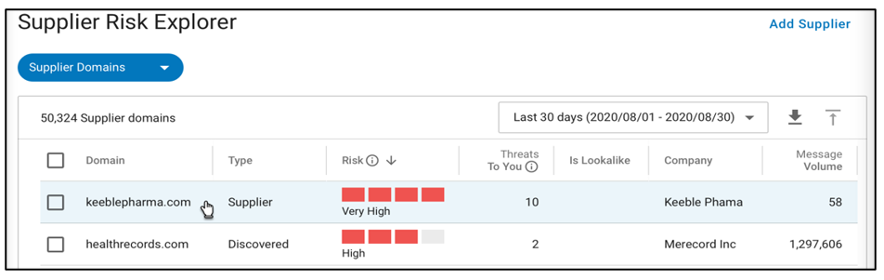
Figure 5. Proofpoint Supplier Risk Explorer dashboard showing domain details and risk levels.
Supplier domains actively sending your users malicious emails will rise to the top of the list. That helps your security team focus their efforts on the highest risk suppliers.
Fortify your defences against supply chain attacks
Supply chain attacks are getting more frequent and sophisticated. To defend against them, your organisation needs to invest in technology and training.
Consider partnering with an industry leader that has the experience and expertise to detect and block most attacks before they ever reach a user’s inbox. Then, make sure your employees are trained to spot messages that don’t get blocked.
The Proofpoint Threat Protection Platform, which includes Advanced Threat Protection, Security Awareness Training, Email Fraud Defense and Supplier Threat Protection can help you strengthen your defences against supply chain attacks.











