Microsoft — The Threat Actor’s Playground. A Blog Series.
This post is an ongoing series of blogs on different types of people-centric email attacks that Microsoft misses. These attacks cost organisations millions of dollars every year in losses and cause frustration for information security teams and users alike, due to easily evaded detection technologies and the inherent limitations of Microsoft email security.
In this series, you can expect to learn more about Microsoft missing several types of attacks, which we’ll explore in depth and provide recent examples of:
- Business Email Compromise (BEC) or email fraud
- Ransomware
- Supply chain risk
- Account compromise
- Weaponised file sharing
Subscribe to our blog at the bottom of this page to stay up to date on these misses that may impact your organisation. Also, use our Threat Assessment process to better understand your organisation’s risks.
Ransomware attacks missed by Microsoft
Ransomware attacks have accelerated dramatically in the past year. According to The 2021 Human Factor Report from Proofpoint, 2020 saw a 300% increase in ransomware attacks, based on U.S. government figures. Research by Ponemon Institute finds that these attacks are becoming increasingly more expensive, with an average 10,000-employee organisation spending close to $6 million annually on ransomware-associated costs.
Ransomware attackers have relied heavily on email as a point of initial access for years. More recently, ransomware actors have moved to a “big game hunting” strategy to encrypt as many systems and steal as much data as possible to increase their leverage in ransom negotiations. The ransomware itself is typically delivered as a second or even third payload following the installation of malware with downloader capability or theft of credentials (by multiple means). A number of prolific threat actors have become “initial access brokers”, having moved on from spreading banking trojans to selling their access to other groups. These groups will then typically escalate their privileges to administrative levels and more broadly compromise an environment before launching a coordinated attack using either their own ransomware or one of the many ransomware-as-a-service toolsets.
According to research by Unit 42 of Palo Alto Networks, email remains the top attack vector for ransomware accounting for more than 75% of attack origins. Many attacks are now multistage campaigns, with malware used first to infect systems with ransomware.
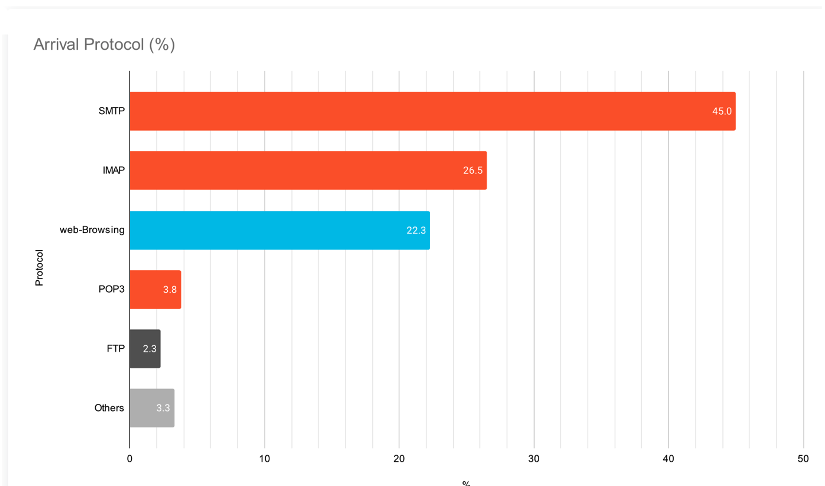
Figure 1. Research by Unit 42 of Palo Alto Networks finds email to be the origin of more than 75% of ransomware attacks
Proofpoint, in our analysis of data in our email security solutions, detected over 48 million malware samples last year that could have been used to launch ransomware. (We highlight this data in The 2021 Human Factor Report). Microsoft, in a limited set of threat assessments conducted in the last month, missed over 850 messages with confirmed first-stage ransomware and almost 8,000 messages with potential ransomware threats.
These misses are incredibly risky to defenders and valuable to actors, and a single downloader can easily escalate to an enterprise-wide compromise. With the average employee click rate of 11%, these Microsoft misses open the door to attacker code running on multiple machines in a typical enterprise environment. With threat actors adept at leveraging malicious macros and fileless malware, this puts substantial pressure on endpoint detection to not just find by respond to the foothold that attackers establish via email.
In one 4,000-employee health organisation, Microsoft missed over 1,800 messages with potential ransomware threats, which would result in dozens of compromises per month with a typical click rate. At a 10,000-employee higher education institution, there were over 850 messages with confirmed first-stage ransomware, and an additional 1,800 messages with potential ransomware threats that Microsoft missed. And, at a 24,000-employee manufacturing organisation, Microsoft missed 750 messages with potential ransomware threats.
Below, you’ll see a sample of ransomware attack types that Microsoft missed which recent Proofpoint Threat Assessments revealed.
Qbot Excel document attack overview:
- Environment: Microsoft 365
- Threat Category: Attachment Threat
- Attack Type: Keylogger as Initial Access Broker for Ransomware
- Target: Shared Mailbox
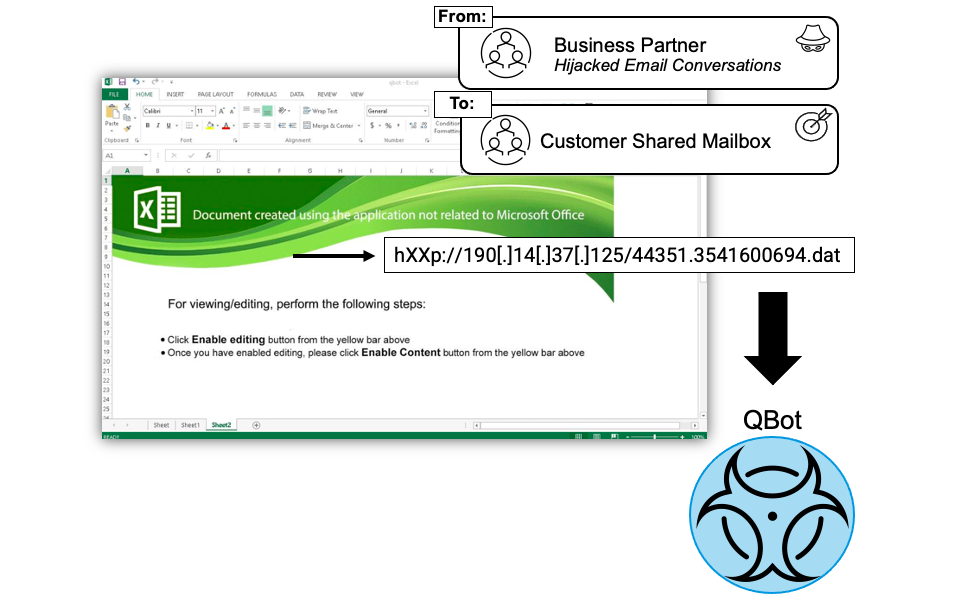
Figure 2. Qbot Excel document attack
The anatomy of the attack:
This ransomware attack employed a few disguises to circumvent defences, such as impersonation, file obfuscation and sandbox evasion techniques:
- The email makes it appear as though the message originated from a business partner with whom the target regularly communicates. Microsoft Spoof Intelligence provided no protection against this despite the obvious From address/Sender address mismatch.
- The file obfuscation tactic featured a zipped Excel attachment that uses macros to download and run Qbot, which Microsoft missed.
- The malicious payload uses sandbox evasion tactics also missed by Microsoft.
There are other examples of Microsoft missing ransomware using social engineering tactics to lure users into engaging.
Bandook Remote Access Trojan PDF document attack overview:
- Environment: Microsoft 365
- Threat Category: Attachment Threat
- Attack Type: Malware as Initial Access Broker for Ransomware
- Target: Customer Service Engineer
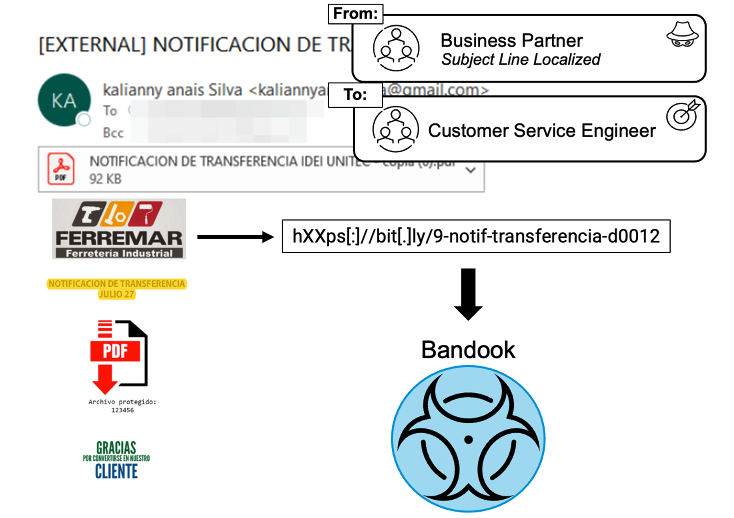
Figure 3. Bandook Remote Access Trojan PDF document attack
The anatomy of the attack:
This ransomware attack used a few disguises to circumvent defences, such as impersonation, social engineering, URL obfuscation and sandbox evasion techniques.
- The email makes it appear as though the message originated from a business partner with whom the target regularly communicates, with a localised subject line. Microsoft Spoof Intelligence provides no protection form these types of threats since it’s originating from a compromised account at the target’s business partner.
- The attachment itself was benign but contained an embedded URL.
- The URL obfuscation tactic, which was Microsoft missed, led to a URL with a password-protected and compressed executable leading to the Bandook remote access trojan.
- The malicious payload uses sandbox evasion tactics missed by Microsoft.
This type of attack is dangerous because it’s personalised and received by a single user. However, attacks that prey on shared mailboxes have a higher likelihood of prompting user engagement.
The Trick Excel document attack overview:
- Environment: Microsoft 365
- Threat Category: Attachment Threat
- Attack Type: Malware as Initial Access Broker for Ransomware
- Target: Public-Facing Mail List
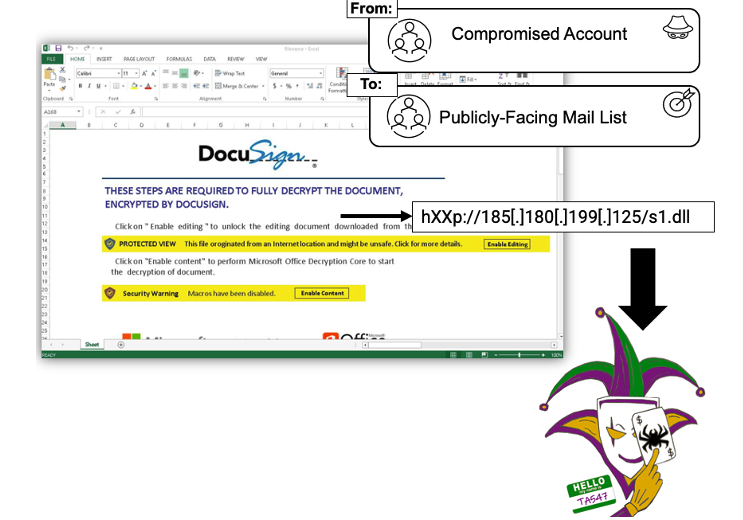
Figure 4. The Trick Excel document attack
The anatomy of the attack:
This ransomware attack relied on a few disguises to circumvent defences, such as passing reputation scans and SPF and DKIM checks. It also used file obfuscation and sandbox evasion tactics.
- The email came from a compromised account, passing SPF and DKIM checks and increasing perceived legitimacy. Microsoft reputation scans only detect known threats. Since this email was sent to a mail list, it improved the likelihood of users engaging with the message.
- Microsoft missed the file obfuscation tactic, which was embedded in the Excel document that uses Excel 4.0 macros (a thirty year-old document format that is still supported by Microsoft and easy to use as a vehicle for malware) to download The Trick.
- The malicious payload uses sandbox evasion tactics missed by Microsoft.
Going with “good enough” email security can mean more ransomware is likely to be activated on your network.
How Proofpoint stops ransomware
It’s important to note that Proofpoint would have detected and blocked the messages shown above from delivery.
Proofpoint is the only vendor that provides an end-to-end, integrated solution to combat ransomware. We’ve built multilayered detection techniques to defend against constantly evolving threats. Known malicious documents are blocked automatically, while unknown attachments are analysed and sandboxed, overcoming attempted evasions like password-protected documents, attachments with embedded URLs and zip files.
The machine learning components of URL and attachment protection are trained by our unmatched data set that comes from global scale and our deployments protecting the number one threat vector at more of the Fortune 100, Fortune 1000 and Global 2000 than any other security provider.
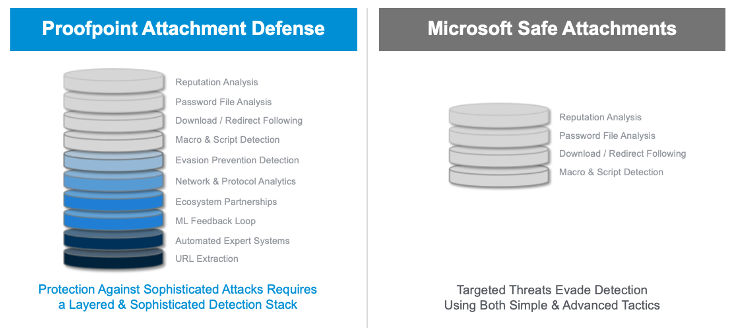
Figure 5: Proofpoint Attachment Defense vs. Microsoft Attachments
Recommendations to prevent ransomware attacks
Proofpoint takes a layered approach to stopping ransomware attacks with our Threat Protection Platform, so there are more layers to protect organisation. Some layers include our leading detection, isolation, authentication, education and automated remediation capabilities.
There’s no silver bullet to stop the ever-increasing phishing threat, which is why a layered, integrated threat protection solution is necessary. Proofpoint also uses machine learning and advanced sandboxing technology to stop BEC, phishing, account takeover and more, in addition to ransomware.
To learn more about how we can stop these threats and more in your environment with the Proofpoint Threat Protection Platform, see this page. Also, consider scheduling a free Email Threat Discover Assessment.











