Proofpoint recently introduced a new capability that helps answer these types of questions:
- What threat actors are targeting my organization?
- How much activity do we see from a specific actor?
- Which of my users is the actor targeting?
- What techniques are they using?
- How is their activity changing over time?
- How is Proofpoint protecting us from these actors and threats?
Threat Actor Reporting is a free upgrade in Proofpoint Targeted Attack Protection (TAP). In short, it provides visibility into the tactics, techniques and procedures (TTPs) of threat actors and an understanding of their objectives. By coupling this information with details on who within your organization is being targeted, you can prioritize additional controls and actions you need to take.
Let’s take a look at how you might use Threat Actor Reporting. In the following example, we begin by clicking on the “Reports” button located on the left-hand side of the TAP dashboard and then, on the “Actors” tab at the top of the dashboard.
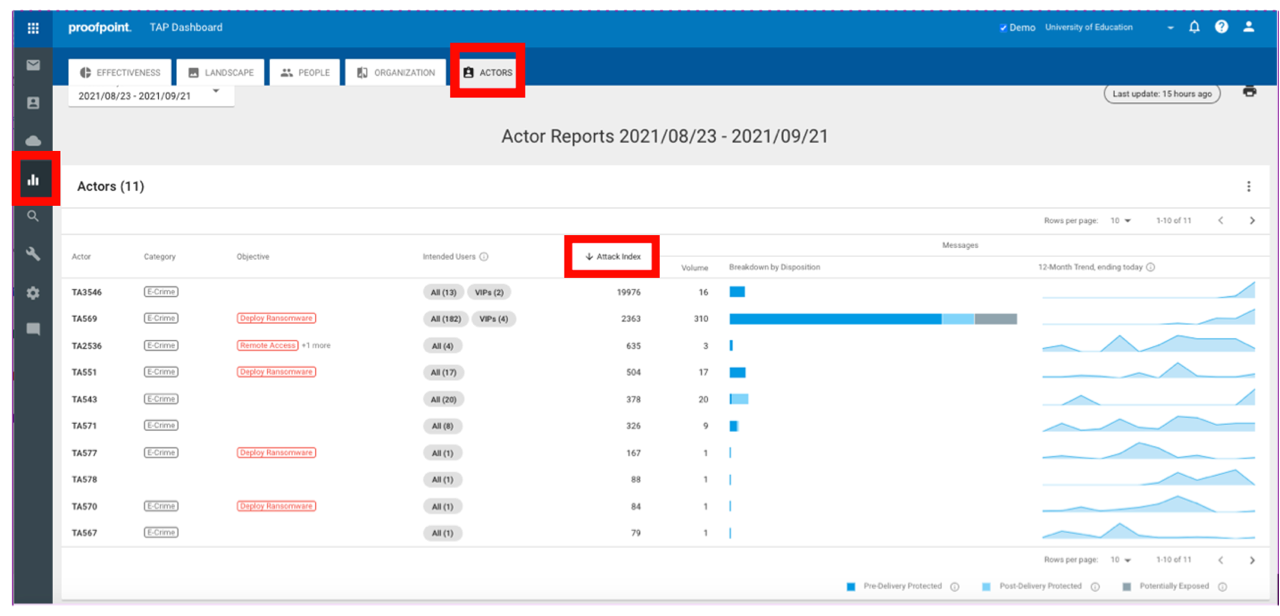
Figure 1: Threat Actor Report sorted by Attack Index quicky identifies the most significant threat actors
In this example, sorting is based on the Attack Index score, not by volume. Why? Volume unto itself is somewhat useless in telling us the true impact of an attack. A single, well-targeted, Remote Access Trojan (RAT) from a sophisticated state actor is much more concerning than a few hundred relatively innocuous spams from a somewhat pedestrian small crime gang.
The Attack Index reflects the relative impact of an attack by considering the actor’s sophistication, the “targetedness” and threat type, in addition to volume.
Figure 1 shows that the Attack Index is very high for TA3546, despite low volume, especially in comparison to the second actor listed, TA569. With this report, you can see, at a glance, that TA3546 has targeted two VIPs and has only very recently begun activity focused on the organization in the example. It’s worth noting that TA569’s objective is to deploy ransomware. This actor (and most others) will not typically deploy ransomware in the initial stage of the attack, but instead will deploy a type of malware that ultimately leads to ransomware. In the case of TA569, they usually deploy SocGholish malware that leads to WastedLocker ransomware. This visibility is extremely valuable for understanding which threat actors are targeting your organization and their involvement in a larger ransomware attack chain.
Let’s dive deeper into TA3546. (Note that clicking on any actor will launch a page where you can access all the types of information shown in Figures 2 - 5.)
First, we can see from Figure 2 that TA3546 is also known as FIN7, one of the most successful and dangerous financially motivated threat groups that’s been operating for the past half-dozen years.
You can get considerable background information on each actor, which sometimes includes details on indicators of compromise (IOC) and command-and-control information.
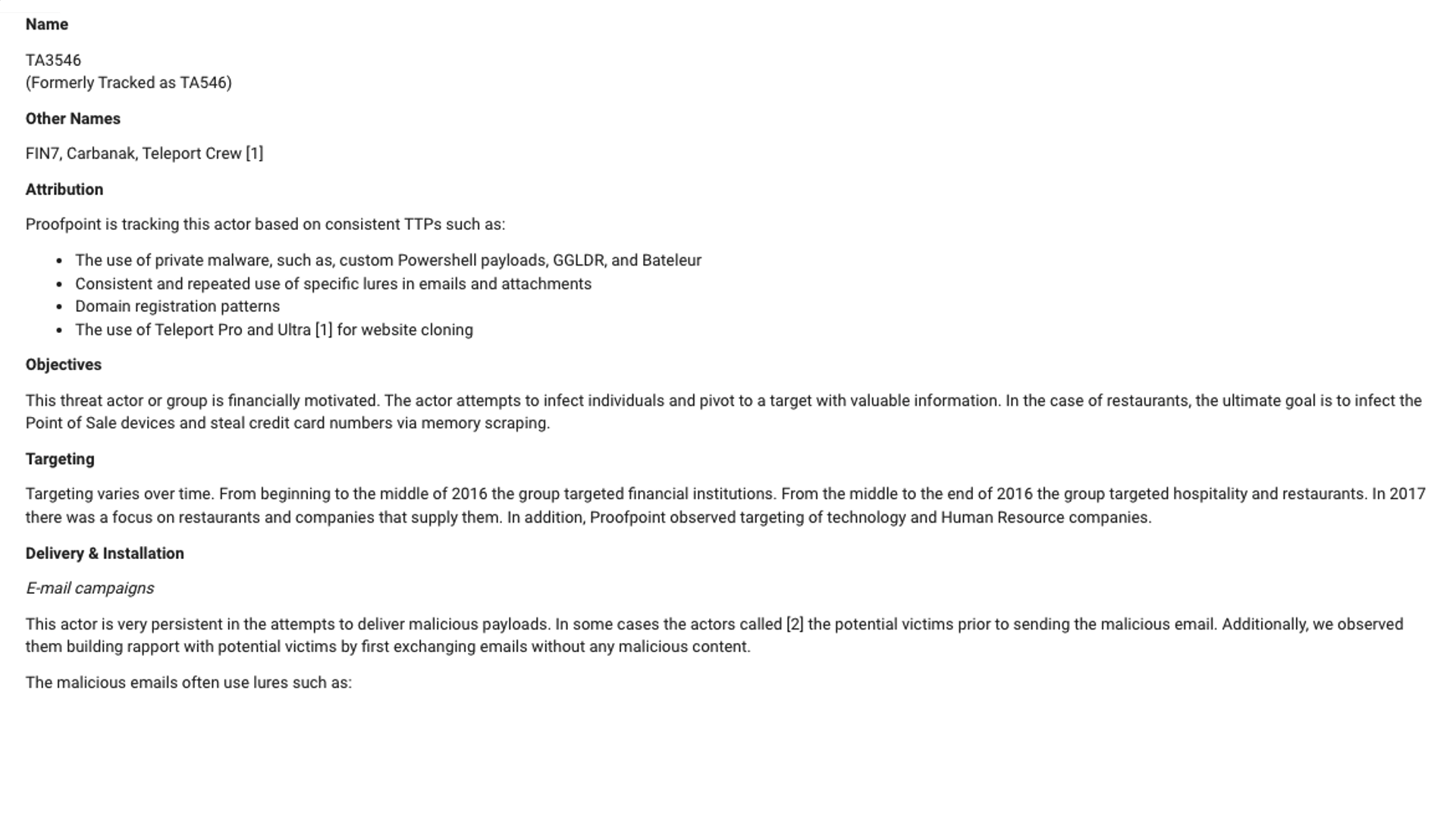
Figure 2: Detailed background information on threat actors curated by Proofpoint Threat Research
With a single click, you can see which users the attackers are focused on, such as the VIPs the attackers targeted in our example (see Figure 3).
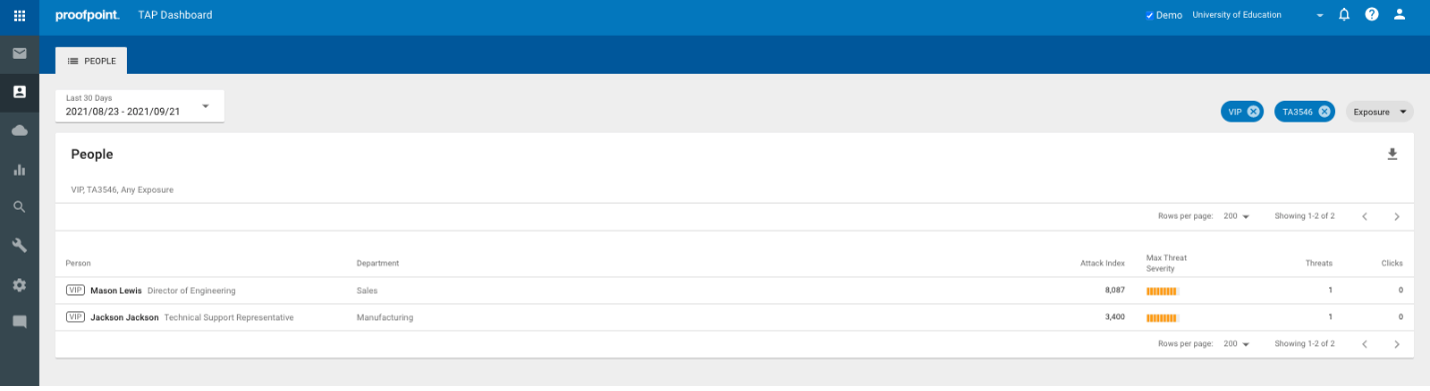
Figure 3: Detailed view of users the threat actor is targeting
The dashboard shown in Figure 4 also offers a wealth of information, ranging from threat type and category to the name of the malware used by the attacker.
All the bars shown are clickable and will provide additional details. For example, click on the bar under “Griffon” in the “Malware” section and you’ll learn that the malware is a JavaScript backdoor delivered via email that contains macro-laden Word documents. You’ll also find out that attackers used Griffon in five specific campaigns in the past year. (And, of course, all the campaign details are accessible, as well.)
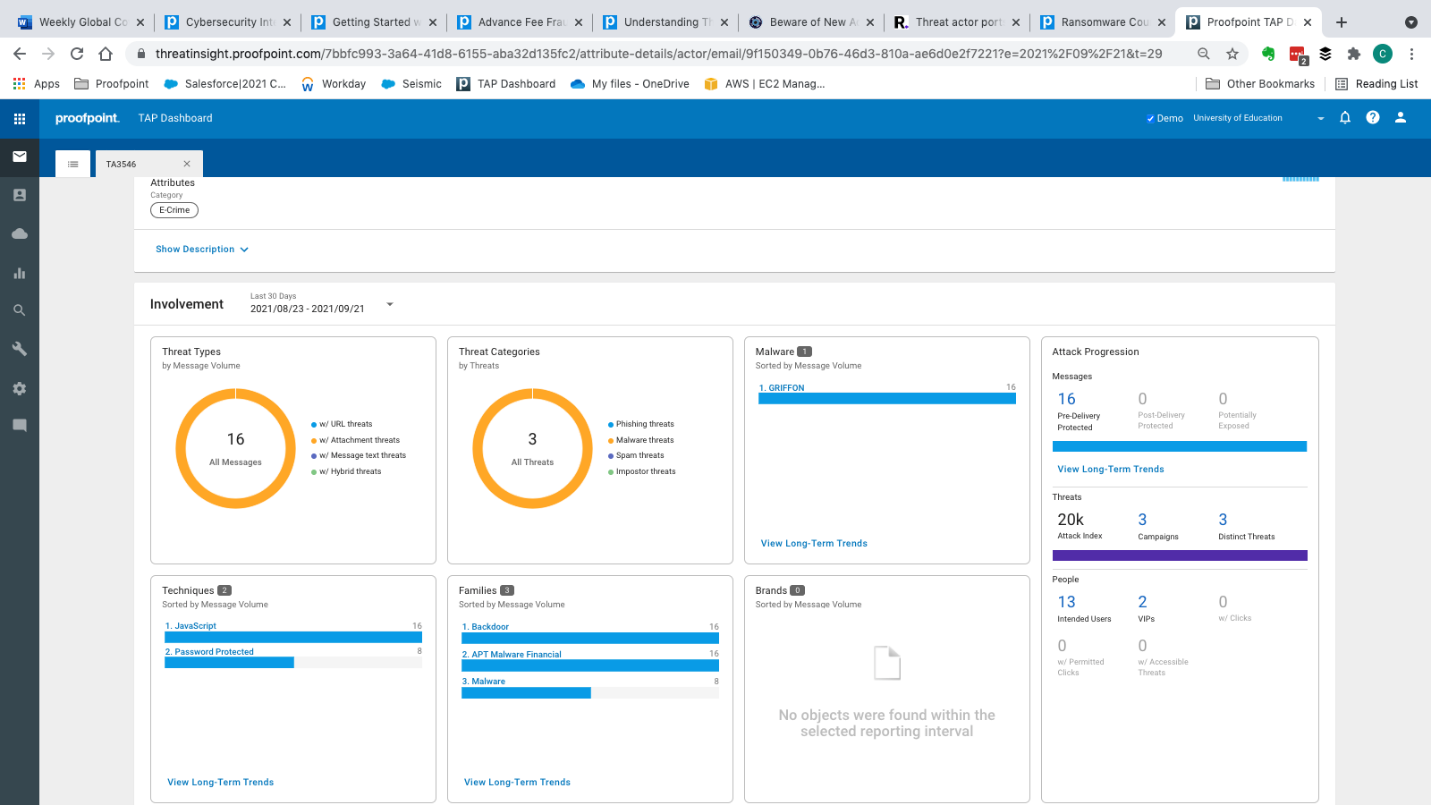
Figure 4: The threat actor dashboard provides an at-a-glance view of the threat types used and attackers’ tactics and techniques
It’s also useful to understand a malicious actor’s activity over time. Figure 5 shows one of five different ways to view the long-term trends associated with FIN7. Here, we see that the attacks started to ramp in July 2021 and have been increasing since. We could also view how other trends shift, for example, if the attacker moved to/from other malware types (that is, used something other than Griffon), or if they mixed up the techniques, using something other than JavaScript.
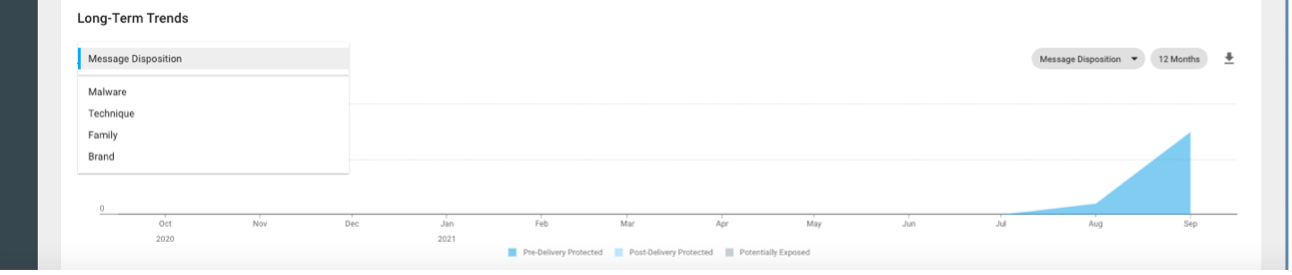
Figure 5: Long-term trends identify changes in threat actor behavior
This was a quick overview of how you can use the Threat Actor Reporting capability in TAP to gain more visibility into threat actors, what their objectives might be, who they’re attacking and what techniques they’re using, among other things. You can use this information to gain new insights, act more proactively and implement additional security controls to help you get in front of adversaries.
Request a free trial here.











