In June 2025 Gartner® published “Overcome AI-Powered Attacks by Leveling Up Your Email Security Platform” by Nikul Patel, Deepak Mishra and Max Taggett. The paper emphasizes the continued importance of protecting organizations from phishing: “Phishing remains a significant attack vector, as demonstrated by its consistent year-over-year trend in the 2025 Verizon Data Breach Investigations [report].”
It also contains research that highlights the adoption of AI by attackers. Gartner found that “[attackers] are using large language models (LLMs) to cut attack costs by over 95%, increasing the ROI of phishing and leading to more sophisticated, varied and frequent attacks.”
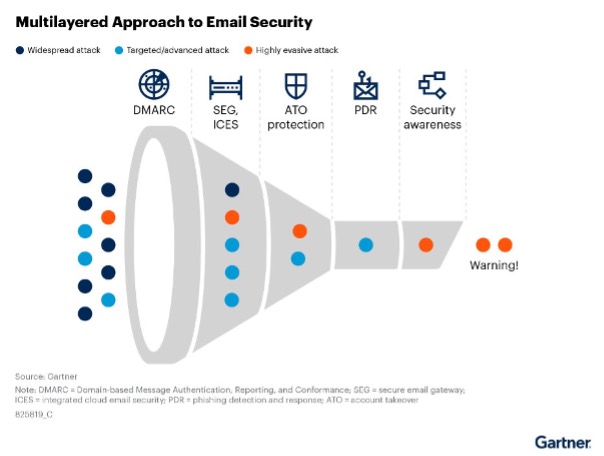
The research recommends: “Adopt a multilayered approach to reduce the overall attack surface. Focus on aspects such as Domain-based Message Authentication, Reporting, and Conformance (DMARC; I&O), security awareness training (security program management), and phishing detection and response (security operations).” The graphic below illustrates this advice.
Proofpoint goes beyond these recommendations
Proofpoint believes this approach is consistent with the Proofpoint platform and the integrated capabilities that are available through Proofpoint Prime Threat Protection.
DMARC and fraud protection
DMARC (domain-based message authentication, reporting and compliance) is important because it provides a mechanism to protect recipients and senders from fraudulent emails. Proofpoint Email Fraud Defense (EFD) goes beyond just implementing DMARC. It also includes the services required to successfully get organizations to “P=Reject” the highest level of protection DMARC can provide.
Flexible deployment
SEGs (secure email gateways) and ICES (integrated cloud email security) are the two ways of implementing email scanning capabilities. While an SEG sits in front of email servers, ICES relies on APIs that are provided by Microsoft to access emails. Both solutions have their own advantages.
Proofpoint is unique in providing both gateway protection and API-based ICES solutions, either separately or combined. Both have the same class leading threat protection capabilities including the use of AI to analyze not only the content of emails, but also the intent.
Protecting people and data
We believe Proofpoint goes beyond just the capabilities highlighted by Gartner to provide protection for other collaboration tools and data protection.
Proofpoint Account Takeover Protection provides identity hygiene to quickly detect, investigate and respond to account takeovers (ATOs).
Proofpoint Closed Loop Email Analysis and Response (CLEAR) uses AI to quickly and accurately inspect and remediate potentially malicious emails reported by users. Combined with Proofpoint Zenguide, it helps guide users to make the right choices when faced with threats. It also provides unique insights into who is the most targeted as well as the risky users in your organization.
The research also highlighted that “As email-based attacks increase, email telemetry becomes crucial for most XDR tools.” Proofpoint integrates with a wide range of technology partners including XDR.
Learn more
The Proofpoint platform provides a comprehensive approach to threat defense, closing security gaps and reducing the complexity caused by fragmented, disconnected solutions. It’s the only complete set of integrated solutions for human-centric security. Download the Proofpoint Prime Threat Protection solution brief. And to find out what Gartner recommends, download the new Gartner report.











