The Cybersecurity Stop of the Month blog series explores the ever-evolving tactics of today’s cybercriminals and how Proofpoint helps organizations better fortify their email defenses to protect people against today’s emerging threats.
Phishing attacks that use the adversary-in-the-middle (AiTM) technique have evolved significantly. Today they are some of the most advanced threats in the cybersecurity landscape. These attacks go beyond traditional phishing by actively intercepting and manipulating data that’s in transit. This makes them much harder to detect and defend against.
Unlike traditional credential harvesting attacks, AiTM threats use a reverse proxy to position themselves between victims and legitimate services they are trying to access. With these threats, threat actors can bypass multifactor authentication (MFA) in real time and perpetrate sophisticated attacks on organizations at a global level.
Background
AiTM attacks exploit fundamental flaws in security systems that rely on user credentials and legacy MFA. These attacks are a variant of the well-known man-in-the-middle (MitM) attack.
It is a form of data eavesdropping and theft where an attacker intercepts data from a sender to the recipient, and then from the recipient back to the sender. This allows attackers to intercept and manipulate the communication in real time, often stealing both login credentials and session cookies. It’s called a “adversary in the middle” because the attacker’s device sits between the sender and recipient and relays messages silently.
The Tycoon 2FA phishing-as-a-service (PhaaS) platform is one of the more notable examples of this threat. Tycoon enables attackers to build highly convincing phishing pages that mimic Microsoft 365 authentication screens. This includes custom branding from the organization’s Entra ID (formerly Azure Active Directory). With these phishing pages, cybercriminals steal usernames and passwords. They also grab 2FA tokens and session cookies, which are critical for bypassing MFA protections.
The scenario
In April 2025, Proofpoint detected multiple campaigns that targeted thousands of organizations worldwide, with an alarming increase in the use of Tycoon’s PhaaS platform. AiTM techniques were used to extract user credentials and bypass MFA.
These phishing campaigns used various evasion tactics, including invisible Unicode characters and custom CAPTCHAs. They also had anti-debugging features that were designed to frustrate automated defenses and slow analysis.
Notably, Proofpoint not only detected this threat within our own customer data, but we also identified it behind the defenses of six other email security vendors. (Three of those vendors are Leaders in the 2024 Gartner Magic Quadrant for Email Security Platforms report.) This shows how sophisticated the attack was—and how effective Proofpoint’s advanced threat detection capabilities are.
The threat: How did the attack happen?
Here’s what a typical attack flow looked like:
1. Sending the phishing lure. The victim receives an email with a URL that points to a fake Microsoft authentication page. This page is designed to look identical to a legitimate login page. This page is custom branded with the organization’s Entra AD logo, which makes it even more convincing.
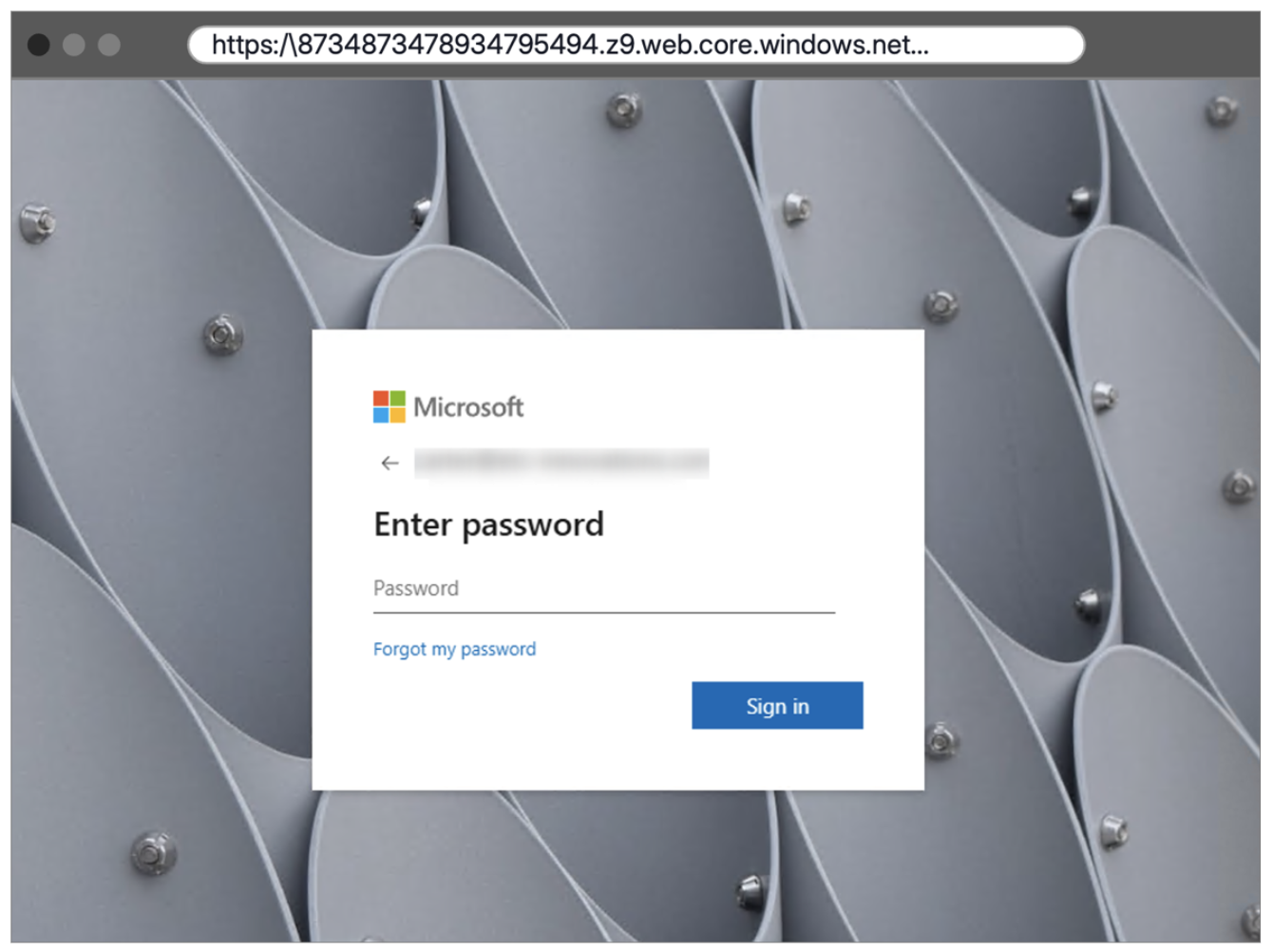
A fake Microsoft login page requesting the target’s password.
2. Harvesting credentials. Upon entering their username and password, the victim is then prompted to input their 2FA token, which is either generated by an authenticator app or sent via SMS. Both the login credentials and 2FA token are captured by the attacker in real time.
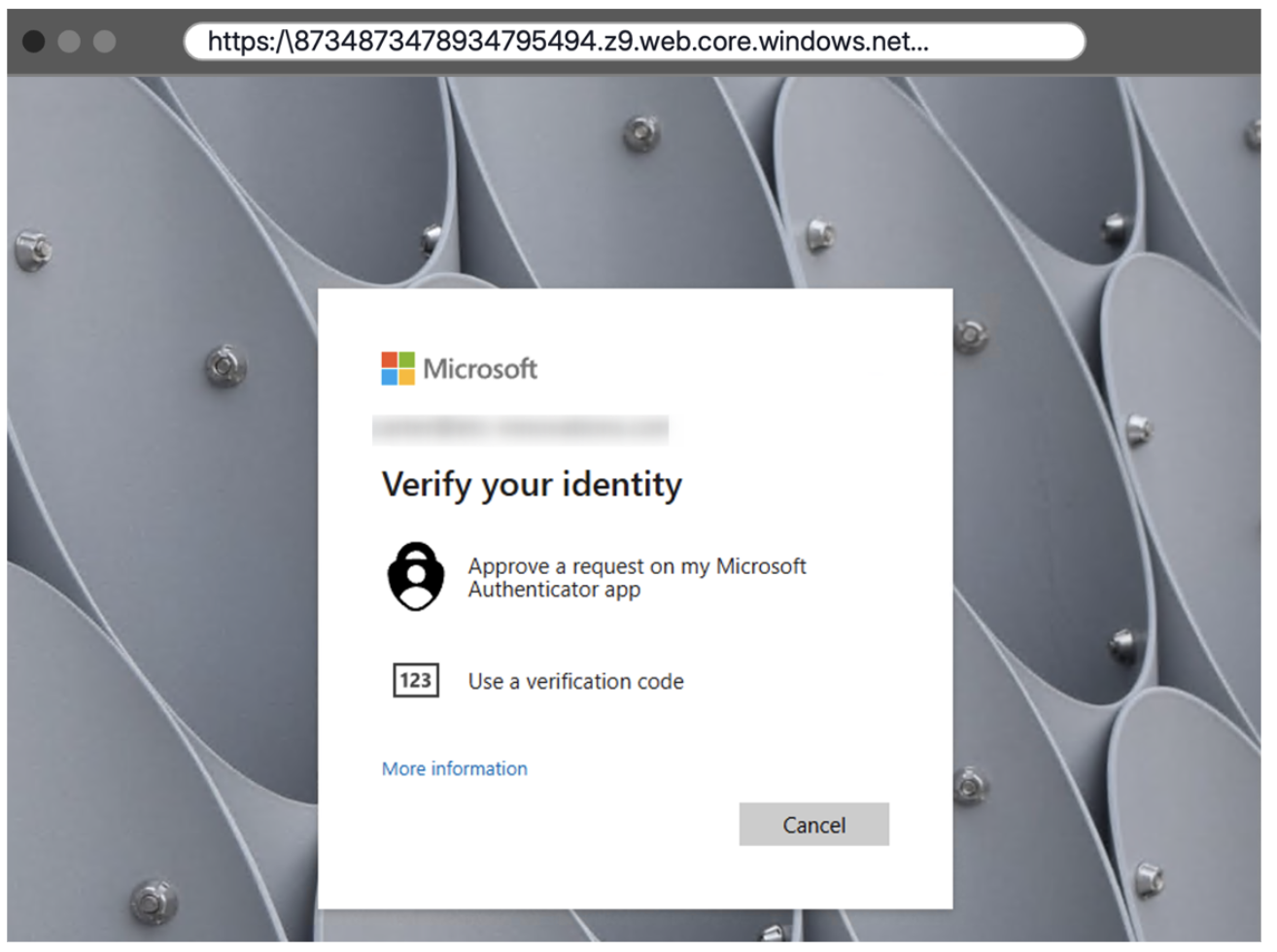
A fake Microsoft MFA page requesting a verification code.
3. Stealing session cookies. In addition to capturing credentials and 2FA tokens, AiTM attackers also steal the session cookies, which allow them to authenticate as the user without triggering MFA prompts.
4. Bypassing MFA. The attacker can now use the stolen session cookies to gain unauthorized access to the victim’s Microsoft 365 account or other critical cloud services. This is a serious vulnerability in legacy MFA systems. Cybercriminals can use it to maintain long-term access to sensitive accounts and systems.
The detection: How did Proofpoint identify this attack?
Proofpoint delivers a complete, human-centric solution to protect organizations from the widest variety of attacks today. Proofpoint Nexus AI is our multilayered detection stack. It combines semantic and behavioral AI, machine learning (ML) and curated threat intelligence from researchers. All these technologies work together to create a multilayered defense that can identify and mitigate malicious messages and content in emerging threats.
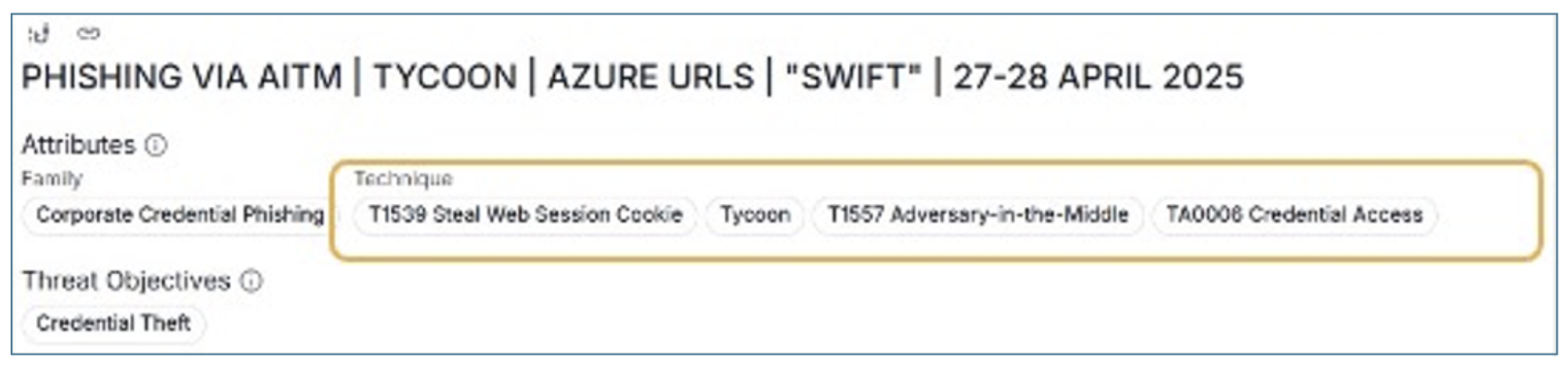
Phishing campaign shown in the Proofpoint Targeted Attack Protection (TAP) dashboard.
This campaign was determined to be malicious by Proofpoint Nexus and our threat research team based on these attributes:
- Suspicious URL domain. The emails contained URLs with uncommon domains that are not often seen in Proofpoint traffic. The unusual domain was flagged as suspicious and quickly categorized as part of the AiTM attack.
- Uncommon sender. The email sender was unfamiliar and not typically seen in correspondence with the target organization. This raised a red flag, signaling the potential for a phishing attempt.
- Precision-validated phishing. AiTM attackers have also started using "precision-validated phishing," a technique where they validate whether the user is a likely target before launching the attack. This is part of a broader effort to increase the attack’s effectiveness by narrowing the scope of victims based on specific behaviors.
In addition to these identified attributes, the Proofpoint threat intelligence team detected several evasion tactics that further confirmed the attack's malicious nature. These included the use of invisible Unicode characters and custom-generated CAPTCHAs, designed to hinder automated analysis and frustrate defenders. The phishing kit also incorporated anti-debugging features that made it harder for traditional detection systems to flag the malicious content.
Suspicious behaviors also played a key role in detection. The reverse proxy technique employed by the attackers allowed them to intercept and relay communication between victims and the phishing kit, enabling real time theft of credentials and session cookies. The phishing page, crafted to mimic a legitimate Microsoft login page with custom branding, was a significant indicator of the attack’s sophistication.
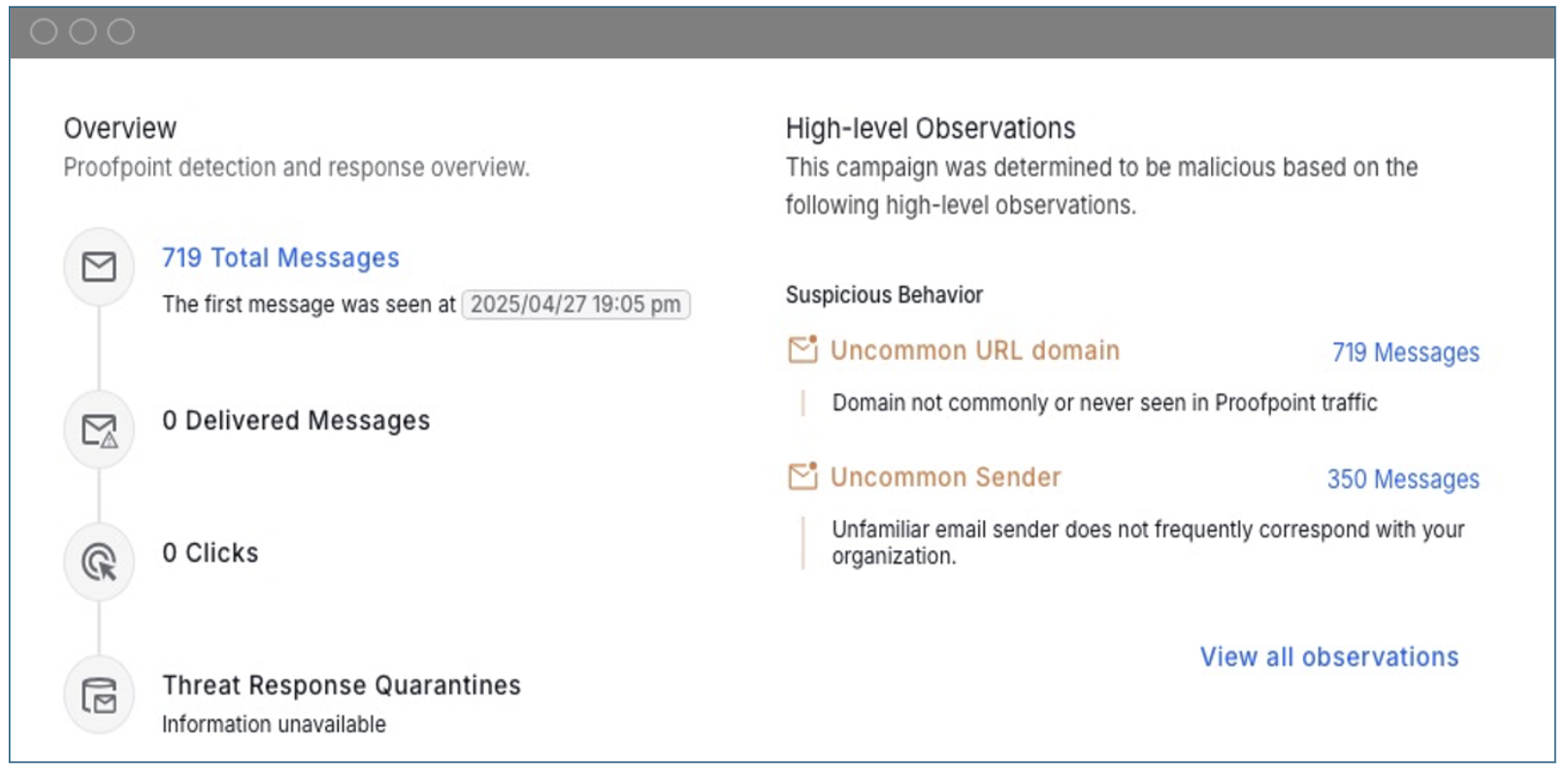
Condemnation summary of signals Proofpoint used to detect the campaign.
The remediation: What are the lessons learned?
To safeguard against threats like the one described in this post, here’s what we recommend:
- Use enhanced authentication methods. MFA remains a key defense, but it’s not foolproof. Consider implementing additional authentication methods, such as hardware tokens, like FIDO2. These methods are resistant to session cookie theft and are harder for attackers to bypass.
- Educate users. Training employees to recognize phishing emails is crucial. Users should learn how to carefully inspect URLs in email messages. And they should be taught to verify the authenticity of login pages, especially those with custom branding.
- Improve your email filtering. Advanced email security solutions can detect suspicious behavior. They can also identify the use of uncommon domains that are used, unusual sender information, and other indicators of a phishing attack.
- Get advanced threat detection. The use of advanced threat detection tools is critical for defending against AiTM and other identity-based attacks. These tools not only prevent attackers from stealing credentials, but they also stop them from moving laterally across your environment and escalating the privileges of stolen accounts.
Protect your organization with human-centric protection
At Proofpoint, we recognize that the human layer is often the most vulnerable in cybersecurity. That’s why our solutions are designed to protect against the evolving landscape of threats. By combining cutting-edge technology with real-time threat detection, user education and advanced remediation capabilities, Proofpoint delivers comprehensive protection.
Proofpoint solutions to protect against AiTM attacks
Proofpoint Account Takeover Protection (ATO) can help you identify account takeovers in real-time by extending the power of Proofpoint Targeted Attack Protection (TAP). This provides the unique capability to identify and block most unauthorized login attempts, even when MFA is bypassed. This helps ensure that attackers cannot maintain access to compromised accounts.
Contact us to learn more about how Prime Threat Protection can help defend against AiTM and other emerging cybersecurity risks. Proofpoint experts are ready to guide you in securing your environment and ensuring your people remain safe from the latest phishing threats.
Read our Cybersecurity Stop of the Month series
To learn more about how Proofpoint stops advanced attacks, check out our other blogs in this series:
- Uncovering BEC and supply chain attacks (June 2023)
- Defending against EvilProxy phishing and cloud account takeover (July 2023)
- Detecting and analyzing a SocGholish Attack (August 2023)
- Preventing eSignature phishing (September 2023)
- QR code scams and phishing (October 2023)
- Telephone-oriented attack delivery sequence (November 2023)
- Using behavioral AI to squash payroll diversion (December 2023)
- Multifactor authentication manipulation (January 2024)
- Preventing supply chain compromise (February 2024)
- Detecting multilayered malicious QR code attacks (March 2024)
- Defeating malicious application creation attacks (April 2024)
- Stopping supply chain impersonation attacks (May 2024)
- CEO impersonation attacks (June 2024)
- DarkGate malware (July 2024)
- Credential Phishing Attack Targeting User Location Data (August 2024)
- Preventing Vendor Impersonation Scams (September 2024)
- SocGholish Haunts the Healthcare Industry (October 2024)
- Preventing Vendor Email Compromise in the Public Sector (November 2024)
- How Proofpoint Stopped a Dropbox Phishing Scam (December 2024)
- E-Signature Phishing Nearly Sparks Disaster for Electric Company (January 2025)
- Credential Phishing that Targets Financial Security (February 2025)
- Luring Victims with Free Crypto to Steal Credentials and Funds (April 2025)
- Stopping Phishing Attacks that Pivot from Email to SMS (May 2025)











