Know Thy Enemy
Know thy enemy and know yourself; in a hundred battles, you will never be defeated. When you are ignorant of the enemy but know yourself, your chances of winning or losing are equal. If ignorant both of your enemy and of yourself, you are sure to be defeated in every battle.
— Sun Tzu, The Art of War
In cybersecurity, how well do you really know your enemy and yourself?
This is definitely a difficult task given the nature of the threat landscape and how organizations have adopted remote work and migrated to the cloud. Threat actors have many tactics and techniques they use to target people within the organization. And the accessibility of Google and LinkedIn makes it easy for them to conduct quick research on key people, people who might have privileges and their network.
Proofpoint Threat Research shows that threat actors are targeting people rather than infrastructure. Consider that more than 99% of threats need some sort of human interaction to trigger them. So, to build a successful security program today, you need to understand who is targeting you and your people, how, and what their objectives are.
Threat Actor Tracking in Targeted Attack Protection (TAP)
Proofpoint recently released a new feature within TAP called Threat Actor Tracking. It helps you understand the dynamics of threat actors, their objectives, techniques and tools, and the people they’re targeting. You can also see how specific threat actors’ behaviors change over time based on how they are targeting people within the organization.
This visibility can help organizations adhere to the advice given by Sun Tzu centuries ago by allowing them to know their enemy — and know themselves better, too. For example, if a threat actor targets a specific user or group of users in your organization, you would know who those users are and who the threat actor is. And you’d be able to understand the following, as well:
- Objectives (e.g., trying to gain access to endpoints, collect user credentials, deploy ransomware)
- Techniques (e.g., Office VBA Macro, HTML, PowerShell)
- Attack progression (e.g., whether that click was blocked or isolated, people targeted, who clicked, trends)
Now, let’s take a look how this feature appears in the TAP Dashboard.
To navigate to Threat Actor Tracking in the Targeted Attack Protection dashboard, simply go to threatinsight.proofpoint.com. From there, you can click the “Reports” button on the left-hand side and then click the “Threat Actor Tracking” tab inside the dashboard.
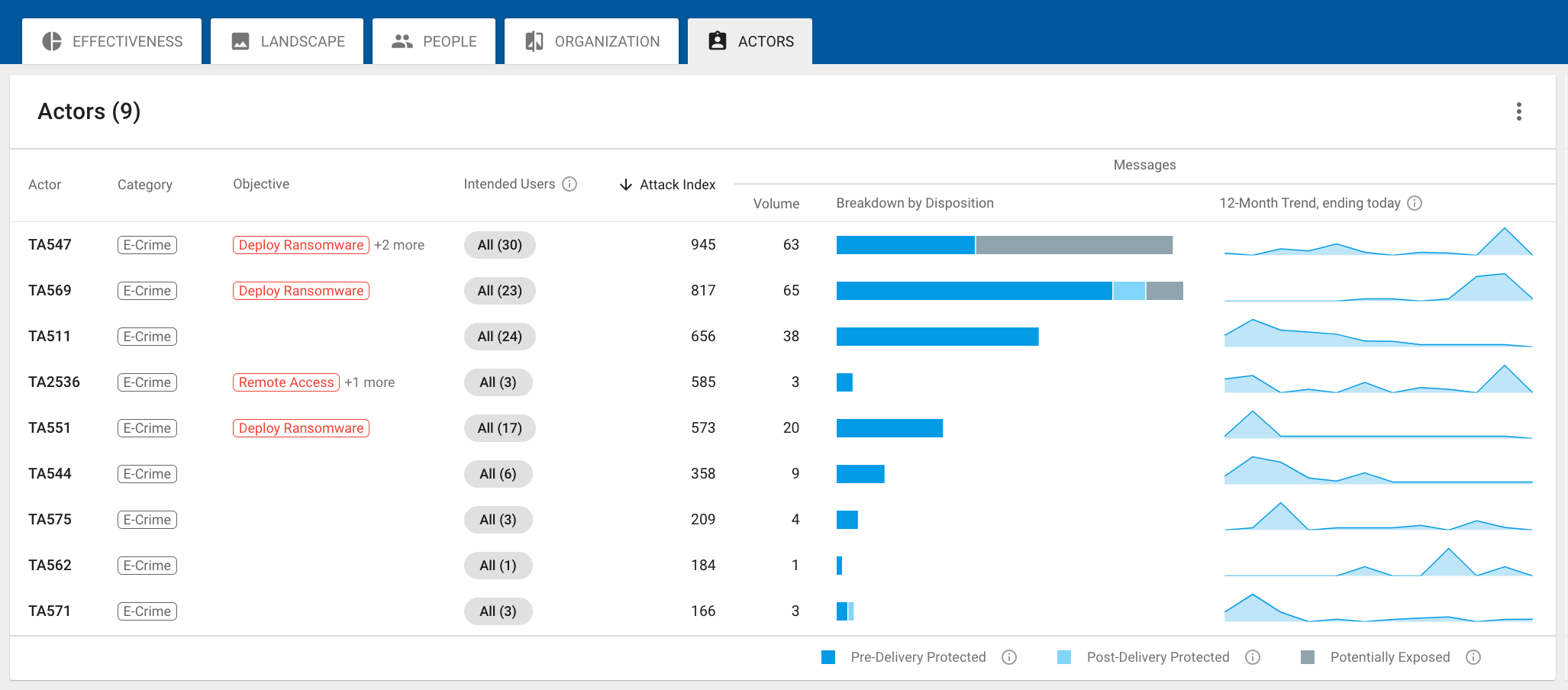
Figure 1. Threat Actor Tracking Dashboard
On the main page, you’ll be able to see all the threat actors targeting your organization. Each threat actor is assigned an attack index score based on the volume of threats, type of threats and severity of the threat actor. This is similar to how we calculate the Attack Index for Very Attacked People™ (VAPs).
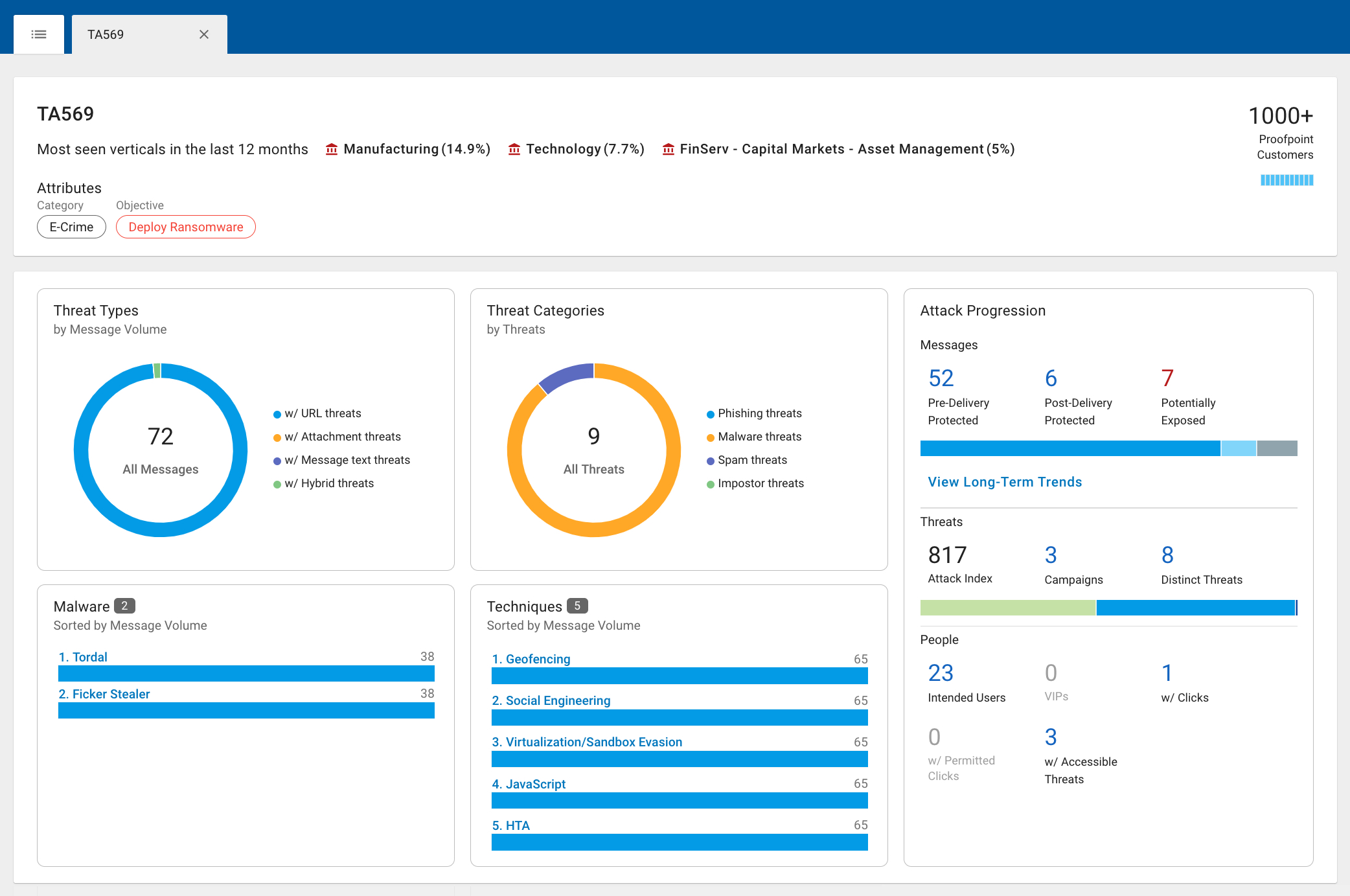
Figure 2. Threat Actor Profile Dashboard
Next, you can click on each threat actor profile to get a detailed description of the actor, the tactics and techniques they use, their motivations, the attack progression, the long-term trends, and the people in your organization they’re targeting.
We’re very excited about this new feature release and the additional visibility it will provide to our customers. Threat Actor Tracking will help them prioritize additional remediation steps. Some of these steps could include but aren’t limited to:
- Creating isolated web browsing policies for threat actor targets
- Enrolling targeted users into relevant training based on how they’re being targeted by threat actors
- Incorporating intelligence into other parts of your security program
Learn more
Want to use our unique insights to improve your organization’s security? Learn more about Proofpoint TAP here.











