This two-part blog series covers the latest innovations to Proofpoint Prime Threat Protection. Prime empowers security organisations with expanded defences and simplified operations to address today’s emerging human-centric cybersecurity challenges.
As digital workspaces continue to expand, attackers are increasingly targeting people across email and other digital channels, such as collaboration and messaging tools, social media platforms, cloud apps and file-sharing services. They’re also hijacking trusted business communications, disrupting relationships with suppliers and customers.
Today’s attackers are more sophisticated than ever before. They use phishing and other techniques, such as multifactor authentication (MFA) bypass, telephone-oriented attack delivery (TOAD), SocGholish and subscription email bombing, to compromise users. Many also pivot to third-party suppliers or business partners, compromising those accounts as a stepping stone to reach employees, with the ultimate goal of account takeover.
Proofpoint Prime takes a holistic approach to stopping these multichannel, multistage attacks and building human resilience across your organisation. It’s built to address both today’s and tomorrow’s evolving threat landscape.
In this blog post, we’ll highlight recent enhancements to Prime that help combat emerging human-centric threats.
Expanded phishing protection
Strong email protection is critical. But cybercriminals don’t simply give up just because their email-based attacks have been stopped. Recently, we’ve seen an increase in phishing attempts across collaboration tools, messaging apps, social media and other digital platforms.
To address this, the Proofpoint Prime solution has been enhanced. Now it provides phishing protection against malicious URLs delivered via any messaging, collaboration or social media platform. This is done in real time by inspecting URLs and blocking malicious URLs when they’re clicked, which is enforced in the browser. This means Prime can protect users anywhere, anytime—at click time, on any device, any network, anywhere users work.
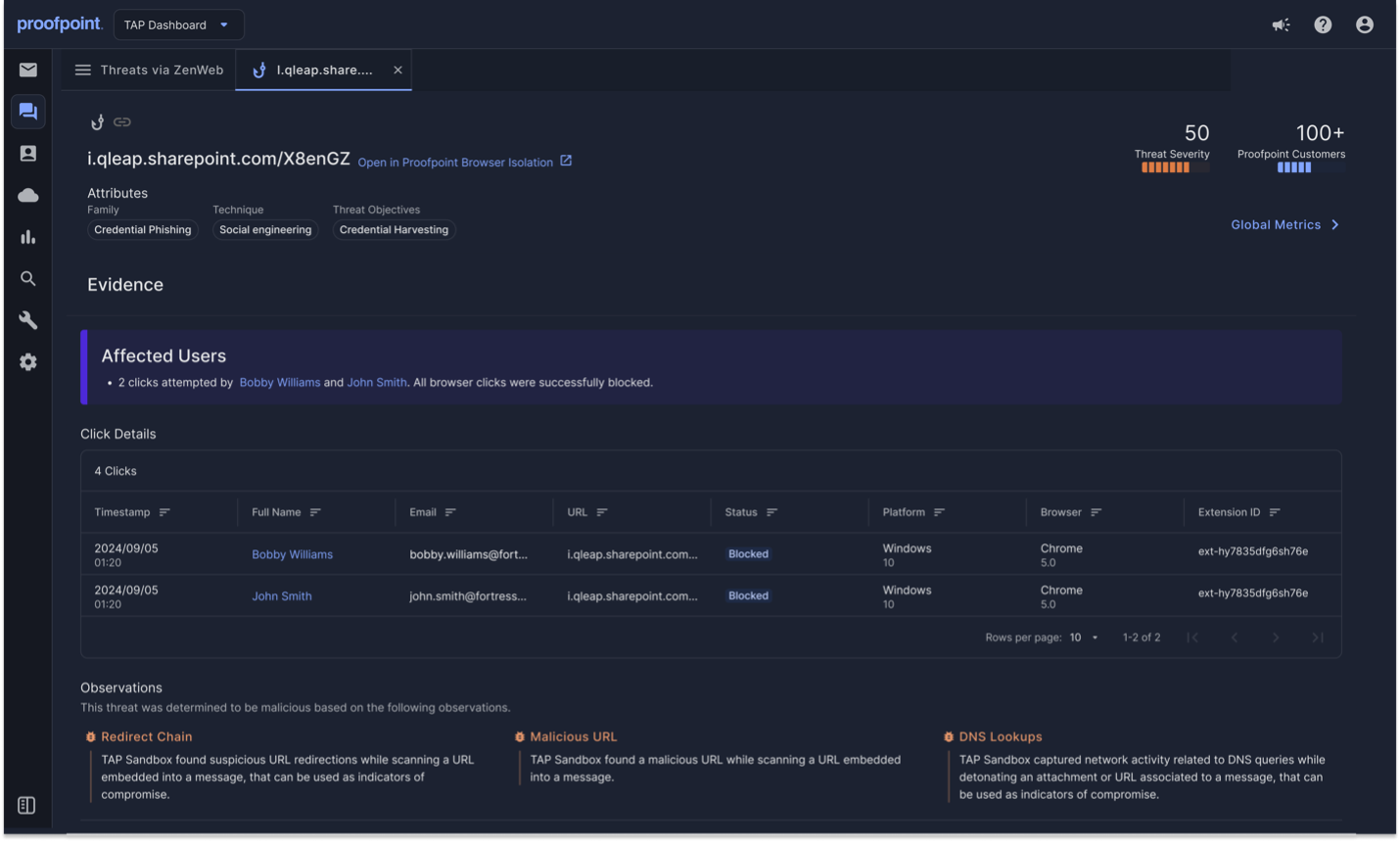
Malicious URL detection and isolation details in TAP Dashboard.
Bidirectional integration with CrowdStrike Falcon
Proofpoint now supports CrowdStrike Falcon integration. This enables suspicious login activity and likely account takeover (ATO) information captured by Proofpoint to be accessible via CrowdStrike Watchlist. In addition, this integration enables CrowdStrike user risk insights to be seen within various Proofpoint interfaces, resulting in richer investigative insights for user accounts that are in question.
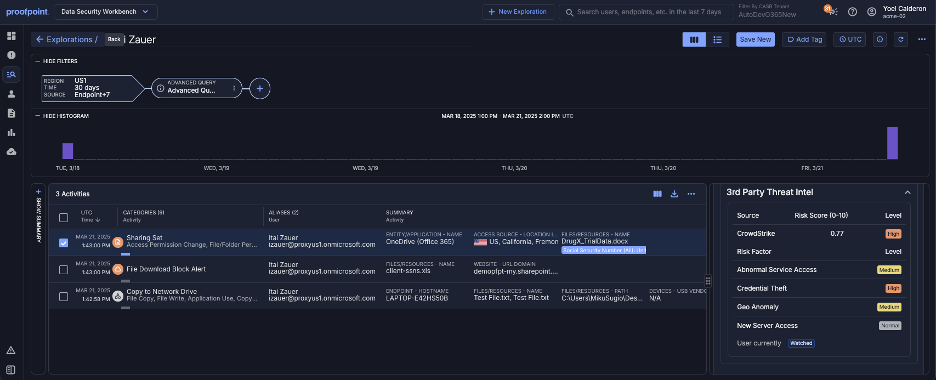
Shared threat intelligences between Proofpoint and CrowdStrike enhance endpoint control and improve investigation of active ATO incidents.
This integration shows why it’s so valuable to integrate an XDR platform like CrowdStrike Falcon with our human-centric platform.
Support for subscription email bombing
Subscription email bombing is a type of email attack where a victim’s email is used to sign up for hundreds or thousands of mailing lists, newsletters or other online services. The goal is to flood their inbox with spam, making it difficult to identify important emails or to help mask other fraudulent activities, like unauthorised transactions.
It can also lead to a frustrated recipient taking action to stop the bombing that instead ends up with their account being compromised. Proofpoint has observed attackers using subscription email bombing to distract their targets, then pivoting to digital channels, like Microsoft Teams, and posing as IT help desk personnel offering support. Believing they were interacting with legitimate IT, targets unknowingly handed over their credentials to the attackers.
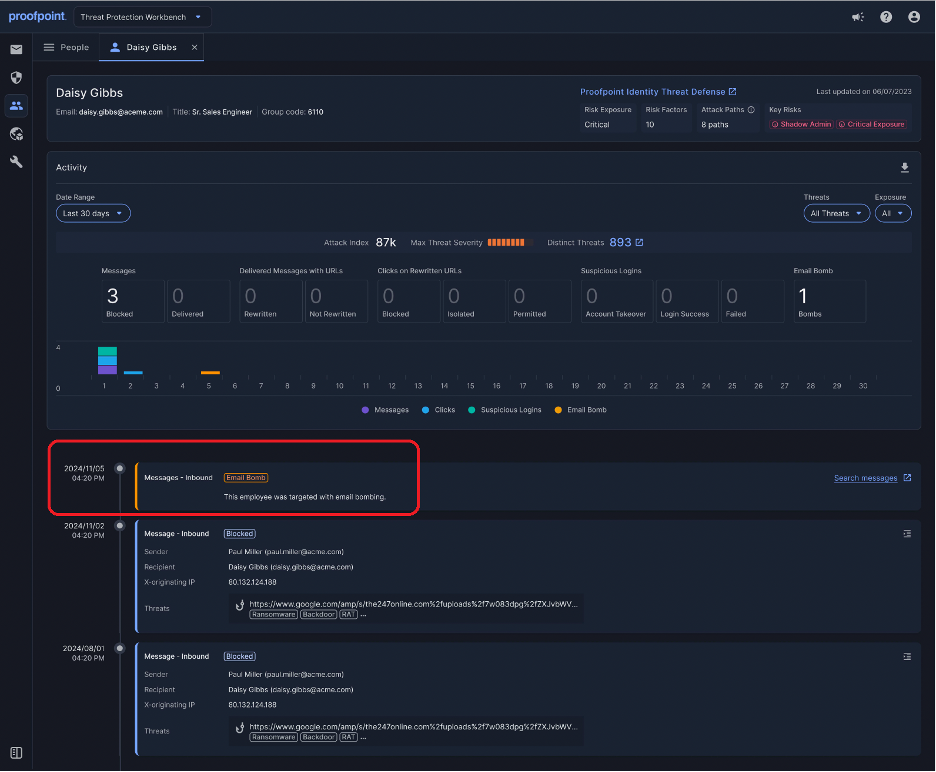
Proofpoint Prime detects and remediates subscription email bombing attacks.
Thanks to threat intelligence and machine learning, Proofpoint Prime is now able to detect and remediate subscription email bombing attacks.
Takedown services for malicious domains and URLs
Proofpoint Prime now gives organisations the ability to mitigate malicious activity from look-alike and non-look-alike domains and URLs that are used in attacks targeting their company.
As part of these takedown services, the Proofpoint takedown team uses internal threat intelligence, email traffic data and open-source intelligence (OSINT) to investigate each submission and collect supporting evidence. The team then works directly with a range of partners to mitigate the attack effectively and quickly. This includes popular blocklist providers, registrars, hosting companies and top-level domain (TLD) providers.
Takedown requests can be submitted through the Prime Takedown portal. There, you can also get easy access to submission details and track the status of your requests.
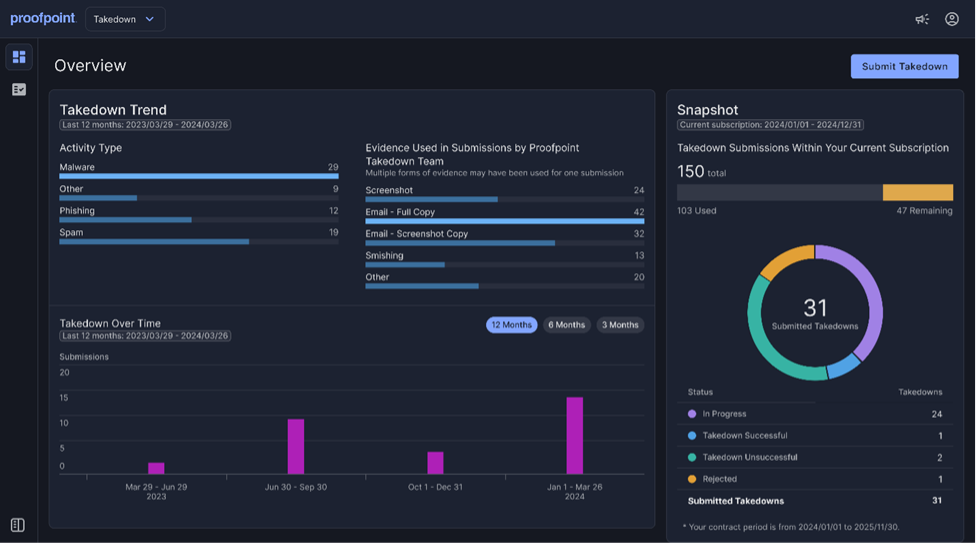
The malicious domain takedown services included in Proofpoint Prime allows security teams to proactively combat impersonation risk.
Struggling to protect your modern workspace? Proofpoint can help
Proofpoint delivers the only human-centric cybersecurity platform with a comprehensive, adaptive approach to protecting your greatest assets and biggest risks: your people. That’s why almost 2 million customers of all sizes, including 85 of the Fortune 100, rely on Proofpoint.
To learn more about these recent enhancements, join our Post-RSA chat on 7 May. And for more information on our holistic approach towards human-centric threats, visit us at Proofpoint.com or contact us today.











